A law firm concern - Claremont Graduate University
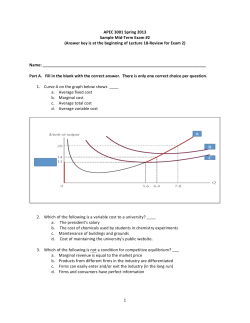
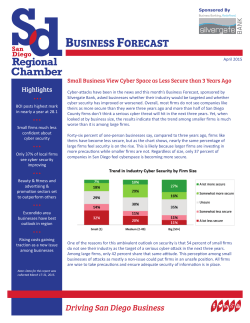
CYBERSECURITY: A LAW FIRM CONCERN Allan Mugambi and Noopur Kore Claremont Graduate University, Center For Information Systems and Technology. WHY SHOULD LAW FIRMS CARE EXAMPLES OF LAW FIRM INTRUSION Law firms are having a fast digital evolution. HIGH VALUE TARGET • Law firms have aggregated / summarized data from organizations. • Law firm clients such as banks and hospitals have their data secured but law firms are the weak link. • If a law firm is attacked, the attack will spread laterally to other networks and their data get compromised too. SENSITIVE DATA • Law firms have volumes of sensitive information. • They have information on deals, intellectual property, mergers and acquisitions. • Personal bank, hospital, business or insurance information could be here. VULNERABILITY • Law firms have worse security than their clients. • Some law firms outsource IT capabilities. • Connectedness and lawyer culture. RESEARCH POSTER PRESENTATION DESIGN © 2012 www.PosterPresentations.com POTASH HACK • China based hackers targeted the law offices of the lawyers working on a deal to have an Australian company acquire the world’s largest producer of potash. • The acquisition was by an Australian company looking to pay $40 billion for the Canadian firm. • The attack spread to several law firms and Canadian treasury ministry. • It started at a law firm. PITTSBURGH HACK • A fired law firm worker retaliated against his employer by using one password provided to him to get through to the law firm's VPN. • The hacker installed malware that enabled him to capture passwords of anyone on the firm’s network. • The hacker, identified himself as anonymous, later informed the law firm of the security breach stating that their backup files had been copied and deleted. Furthermore, they would use the data accessed in any way against the law firm. • The hacker was arrested and convicted to a two year probation, community service, and requirement to notify his employer of the conviction. PROBLEMS Lawyers are susceptible to having valid business correspondence with people they do not know. Lawyers, by nature do business with criminals. Lawyers, by trade are in the business of “responding quickly” and be easily lured by phishing emails. Lawyers give a high value to confidentiality. Lawyers access their information mostly over insecure mobile devices. SOLUTIONS Increase security by segmenting the network Be careful what data is outsourced. Keeping sensitive data off line Save important files on computers not connected to the Internet where possible. Develop a cyber security policy Determine on one centered on people or one centered on policy. Instill a culture of security among lawyers Watch out for common errors that could render data insecure. WHAT SHOULD CHANGE • As law firms see a digital transformation they also need to keep in step with cyber security. • Digitization of law firms coupled with digital communication such as rampant use of email are some of the factors contributing to information insecurity for law firm data. It should be curbed or find an alternative. • Clients will continue to demand that law firms improve on information security on the cyberspace. Hence, law firms should develop infrastructure for security or outsource it. • Access to sensitive information on wireless devices over insecure connections means greater vulnerability for sensitive information. Law firm employees having access to this sensitive information should be educated about the vulnerabilities. REFERENCES • Ames, J. (2013). Cyber security: Lawyers are the weakest link. Lawyer, 27(44), 1. • Conte, A. (2014). Unprepared law firms vulnerable to hackers. Retrieved from – http://triblive.com/news/allegheny/6721544-74/lawfirms-information#axzz3Ji9kuMrl • Ezekiel, A. W. (2013). Hackers, spies, and stolen secrets: protecting law firms from data theft. Harvard Journal of Law & Technology, 26(2), 649-668. • Finkel, E. (2010, 11). CYBER SPACE UNDER SIEGE. ABA Journal, 96, 39-43. Retrieved – From http://search.proquest.com/docview/805121605?acco untid=10141 • Google Images • McNerney, M., & Papadopoulos, E. (2013). HACKER'S DELIGHT: LAW FIRM RISK AND – LIABILITY IN THE CYBER AGE. American University Law Review, 62(5), 1243-1269. Retrieved from http://search.proquest.com/docview/1443695077?acc ountid=10141 • The White House (2015). FACT SHEET: Cyber Threat Intelligence Integration Center. – Retrieved from https://www.whitehouse.gov/the-pressoffice/2015/02/25/fact-sheet-cyber-threat-intelligenceintegration-center CONTACT INFORMATION Noopur Kore – [email protected] Allan Mugambi – [email protected]
© Copyright 2026