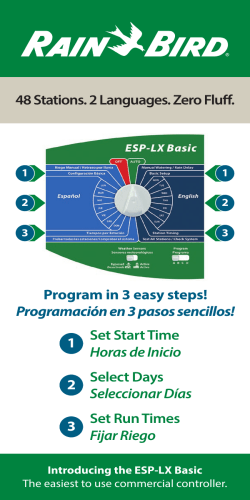
Panzura Admin Guide
TM Panzura Storage Controller Administration Guide Release 6.0 May 2015 Copyright © 2015 Panzura, Inc. All rights reserved. The information in this manual is subject to change without notice. Originated in the USA. Any other trademarks appearing in this guide are the property of their respective companies. 5/19/2015 695 Campbell Technology Parkway Suite 225 San Jose, CA 95008 [email protected] 1‐855‐PANZURA (1‐855‐726‐9872) +1 (408) 578‐8888 www.panzura.com Panzura Storage Controller | Administration Guide 2 Contents Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5 1 Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Panzura Storage Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Panzura Storage Controller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7 Controller Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8 Description of Key Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Panzura Unified Namespace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 File Locking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Data Mobility and Snapshots . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 User‐Managed Snapshots . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Data Locality . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Extended File System ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Scale‐out Global Deduplication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Intelligent Read/Write Cache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Enhanced Cloud Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 Configurable Mesh . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 Intelligent Symantec NetBackup Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 DR Cloud Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 10GbE and 1GbE NIC Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Unified Storage. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Enterprise AntiVirus Plugin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Configuring the Controller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Accessing the Web UI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 Navigating the Web UI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13 Dashboard. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13 2 System Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 Basic Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 System (Basic). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 Time. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 Encryption and Certificates (Basic) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27 CloudFS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32 Active Directory (Basic) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34 AMI Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36 NFS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36 CIFS (Basic) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40 Snapshot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42 Panzura Storage Controller | Administration Guide 3 Contents License Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43 Advanced Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50 System (Advanced) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50 KMIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52 High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54 Encryption and Certificates (Advanced). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56 Mesh . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58 Active Directory (Advanced) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61 CIFS (Advanced) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63 Snapshot Manager. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64 Cache. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 Data Locality Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66 Bandwidth Limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71 SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73 Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75 3 Maintenance Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77 Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77 High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83 CIFS Dashboard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85 CIFS Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86 Secure Erase . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87 CIoudFS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87 Cloud Metrics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87 NFS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90 Master Snapshot. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90 Cloud Delete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90 Image Upgrade . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91 Reboot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92 Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92 Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93 Advanced. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94 A Setting Up Gray‐X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95 B Antivirus and Malware Scanning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96 McAfee VirusScan Enterprise 8.8 with VirusScan Enterprise for Storage . . . . . . . . . . . . . . . . 96 Symantec Protection Engine for Network Attached Storage 7.5 . . . . . . . . . . . . . . . . . . . . . . . 97 C Creating A Microsoft Azure Storage Container . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98 Panzura Storage Controller | Administration Guide 4 Preface Welcome to the Panzura Storage Controller (controller). The preface contains the following information: “About this Guide” on page 5 “Document Conventions” on page 5 “Related Documents and Resources” on page 5 About this Guide This guide describes how to deploy and manage the controller. It is designed for experienced storage administrators who are responsible for configuration and maintenance. It assumes that you are familiar with NFS and CIFS network storage operations. For installation information, see the Panzura Storage Controller Installation Guide. Document Conventions This document uses the following conventions. Convention Bold font Description Actions, command names. Example: Choose One Arm (default) or Inline. Example: Use the show‐interface command. Command examples and output. Example (sample output): Fixed width font Running test on Cloud License: CSP-Google, 44454C4C-4600-1047-8051C6C04F4C4D31.1330968255.954850 Running connectivity test Resolve DNS commondatastorage.googleapis.com : 74.125.224.106 74.125.224.107 74.125.224.108 ... Related Documents and Resources For related documentation and other information, go to the Panzura web site at http://www.panzura.com. The documentation may be accessed on the Support page (Support > Docs & Information). Access requires a user login and password. Panzura Storage Controller | Administration Guide 5 1 Overview This chapter provides an overview of the Panzura architecture and the Panzura Storage Controller (controller) features. “Panzura Storage Architecture” on page 6 “Panzura Storage Controller” on page 7 “Controller Features” on page 8 “Unified Storage” on page 12 “Configuring the Controller” on page 12 Panzura Storage Architecture The Panzura OS (PZOS) provides a highly scalable, high performance global file system called CloudFS that is natively integrated with object‐based cloud storage systems. CloudFS allows clients from multi‐site locations to interact with and lock files within a single global file system address space, known as the unified namespace. Within the Panzura architecture, global shared file read operations are serviced locally at LAN speeds. File write permissions are managed by the Panzura's Global Read Write file locking technology. Within the Panzura network architecture (Figure 1), all controllers share access to a common storage cloud. The cloud is the authoritative source of data for all controllers. Because cloud storage is effectively infinite in capacity and elastic in scale, cloud storage is always larger than the local physical storage that is available in any particular controller (at any particular site). The Panzura architecture includes technologies to leverage this difference in capacity and manage the aspects of deploying a NAS storage system that operates under this paradigm. Each Panzura controller provides LAN speed access to CloudFS. Locally, each controller caches data while presenting a complete metadata view of the entire CloudFS that spans all connected sites. Panzura Storage Controller | Administration Guide 6 Chapter 1 | Overview Figure 1 Panzura Network Topology Panzura Storage Controller The Panzura Storage Controller (controller) is the core of the Panzura storage architecture. The controller is a reliable, high performance, optimized cloud storage appliance that can manage massive data densities within its scalable file system. The resilient storage subsystem protects data using military grade encryption, multiple RAID parity protection schemes, efficient user managed snapshots, and cloud storage. The controller provides local and cloud storage for widely‐used file storage protocols, file management technologies, and directory services integration. Network File System (NFS), used by Unix/Linux clients and servers Common Internet File System (CIFS), used by Microsoft Windows clients and servers Microsoft Active Directory (AD) Panzura Storage Controller | Administration Guide 7 Chapter 1 | Overview The controller can virtualize multiple disk media types within the same file system. Supported media include spinning hard disk drives (HDDs), solid state drives (SSD), networked WAN‐addressable cloud storage, and LAN‐addressable NAS filer volumes. PZOS serves data to clients with CIFS and NFS protocols. Controller Features The Panzura Storage Controller provides the following features: Highly scalable 128‐bit transactional object file system Intelligent read & write caching In‐band file system Policy Engine User managed snapshots Extended file system ACLs RAID data protection Globally distributed file sharing & locking for CIFS High availability Microsoft Active Directory integration Kerberos authentication Key Management Interoperability Protocol (KMIP) support Global namespace Scalable live global deduplication Policy defined variable length deduplication Multi‐protocol CIFS SMBv1, SMBv2, and NFSv3 file services CIFS load balancing Military grade encryption Unified SSD, HDD, and cloud storage Intelligent LAN and WAN bandwidth management Intelligent NetBackup support for multi‐site backup, recovery, and archive Tivoli TSM support for multi‐site backup, recovery and archive SNMPv3 monitoring, traps, and alerting Online remote monitoring and support High speed parallelized WAN‐optimized cloud I/O Multiple cloud topologies (public, hybrid, private) Real‐time cloud storage diagnostics Full system recovery from the cloud 1GbE and 10GbE NIC support (optical and copper) Bandwidth shaping and connection tuning Panzura Storage Controller | Administration Guide 8 Chapter 1 | Overview Description of Key Features This section describes the key features in detail. Panzura Unified Namespace The Panzura unified namespace is an in‐band file system fabric that consists of multiple physical file system instances converged into a single file system metaspace and mounted locally on each node with the root label “CloudFS.” The Panzura unified namespace does not rely on underlying distributed databases and thereby avoids common global namespace limitations that can affect speed, transactional data coherence, write order fidelity, open files, atomic precision, in‐band operation, and global snapshots. By contrast, other global namespace architectures require a database process on each storage system and changes to file metadata require complex out‐of‐band operations. File Locking PZOS and CloudFS support several file locking mechanisms. A traditional file lock is a lock issued against a file by a file system, a server or an application. The lock can consist of extensive application specific meta‐ information and be written into parts of the file payload and/or its file system metadata. File coherency locks are file system locks that are issued by applications to arbitrate guaranteed consistency between applications writing/reading to a single file, for example, MSFT Office Application locks. Opportunistic caching locks are delegated rights that are issued by a file server protocol engine for a remote client to cache a file locally to increase client‐side performance. This is not necessarily a guaranteed write lock, because the delegation can be revoked by a file server at anytime. Example: Microsoft CIFS OPLOCKS. Data Mobility and Snapshots When the controller is operating, it actively takes the configured file system snapshots. Snapshots can occur at the granularity of one per second and are virtually unlimited with respect to data address space and number of entities. The snapshot process captures and manages the user data state, individual file system state, and total system data. All snapshots are independent and able to be moved between systems. Snapshots capture the state of the global file system address‐space in a single operation with guaranteed data coherence at byte‐level granularity. Snapshots never overwrite data blocks. If a new data block is written, then the next snapshot contains a pointer to the new block. If an existing block is modified, a new block is written, while the old block is retained within the active file system for the previous snapshot. User‐Managed Snapshots User managed snapshots provide point‐in‐time copies to protect data with no performance impact and minimal consumption of storage space. Panzura Storage Controller | Administration Guide 9 Chapter 1 | Overview You can take user‐managed snapshots while applications are running to create copies in less than one second, regardless of size of your file system, the data set, or the level of activity on the system. You can schedule automatic snapshot creation or take snapshots on demand. Snapshots are visible on the desktop explorer environment for CIFS and NFS protocols. You can access and retrieve older snapshots from CIFS/NFS mounts without involving IT administration. Each controller has been tested for up to 10,000 user managed snapshots with its global file system. The total number of addressable snapshots is a function of the number of controllers in the entire unified namespace. For example, for a unified namespace with 16 nodes, the maximum tested capacity is 160,000 snapshots. See “Master Snapshot” on page 90. Data Locality Data locality (caching and pinning) governs what data is cached locally on the controller. PZOS provides fine‐grained configuration control over caching through the use of policies, rules and actions that result in improved performance and enhanced cloud storage availability for users. When configuring data locality, Panzura recommends using the auto cache action with prepopulate enabled. This ensures that files are available in disk cache for end users. Prepopulating makes the data available without forcing a reduction in cache. Pinning allows an administrator to forcefully localize (pin) data in the cache within a controller to provide guaranteed LAN speed performance. Because pinning consumes cache space, it should be considered only if needed for performance, with the trade‐off between performance and cache space kept in mind. Note that data is always protected in the cloud, irrespective of polices rules and pinning. See “Data Locality Settings” on page 66. Extended File System ACLs The Panzura file system supports extended file system access control lists (ACLs) with full POSIX semantic compliance. For NFSv3, the system supports read and write ACL operations through an SSH shell or application layer. Clients can dynamically use any supported ACL mode for setting and getting ACLs. For CIFS, clients use a native Microsoft method with the Server Message Block (SMB) protocol for reading and writing extended ACLs. PZOS provides the ability to turn SMB signing on or off. See “CIFS (Basic)” on page 40. Scale‐out Global Deduplication The controller supports enhanced data deduplication within the global file system with high performance, scalability, and system‐wide efficiency. The deduplication data architecture and physical layout on disk is optimized for local and global write performance and data addressability. See “System (Advanced)” on page 50. Intelligent Read/Write Cache PZOS supports an intelligent read/write disk‐based cache (IRC) that reserves a percentage of local storage to intelligently track hot, warm, and cold file block structures as they are accessed. The cache dramatically increases data availability and I/O performance, because file data‐blocks reads have a higher probability of being serviced from local disk than directly from external cloud storage. The cache also Panzura Storage Controller | Administration Guide 10 Chapter 1 | Overview increases overall data availability by masking variations in cloud availability. This allows the file system to continue serving I/O and cache‐resident data‐block reads even when the WAN link to the cloud storage slows or is unavailable, or if the cloud itself is down. See the Panzura technical white paper TWP‐3002 for an in‐depth description of IRC. Enhanced Cloud Diagnostics The controller provides a robust set of diagnostic and measurement tools for monitoring and understanding the health, status, and performance of the Panzura cloud storage infrastructure and interactions. The cloud diagnostics features include tools to analyze the cloud, while the cloud metrics features present a detailed set of trended graphs to visually display metrics about cloud reads and writes. The system also generates alerts if the cloud becomes unavailable. See “Diagnostics” on page 77. Configurable Mesh Configurable Mesh allows an administrator to reduce the metadata that is synchronized with any particular controller, thus reducing the synchronization overhead, bandwidth requirements for synchronization events, and visibility to excluded controller. Each controller can be configured to synchronize only select metadata from other configured controllers within the same CloudFS. Sync relationships can be defined as unidirectional or bidirectional. With configurable mesh, the scope of deduplicated information is restricted to the metadata that is visible to a given controller. Intelligent Symantec NetBackup Integration PZOS supports intelligent integration with Symantec NetBackup, including awareness of the NetBackup data format stream. The system efficiently deduplicates the data stream inline with high optimization ratios. Tivoli TSM, Microsoft Robocopy and Symantec Backup Exec are also supported as cloud backup and cloud archive applications. High Availability The Panzura High Availability (HA) solution consists of two configuration options, HA‐Dedicated and HA‐ Distributed. HA‐Dedicated is similar to the methods used by legacy enterprise storage products. In this configuration, an active controller is protected by a dedicated, passive standby. When the active controller fails, the passive standby assumes its identity and takes over operation. The innovative HA‐Distributed configuration provides a more cost effective and flexible solution. This implementation makes it possible to protect many controllers with a single passive standby that can significantly reduce the cost of HA. When a failure occurs, the standby assumes the identity of the failed controller and takes over operation. If a greater level of protection is required, multiple standby controllers can be deployed to protect against multiple controller failures. And the standby controllers can be geographically distributed from the controllers they protect to provide greater flexibility. See “High Availability” on page 54. DR Cloud Recovery Full cloud disaster recovery (DR) allows rebuilding and recovery of an entire controller from the cloud after a disaster has occurred. In this highly optimized and efficient process, the file system is brought Panzura Storage Controller | Administration Guide 11 Chapter 1 | Overview online and established as active from its cloud metadata instances as soon as possible following the disaster. A minimal set of data blocks are recovered from the cloud to bring the system to a state where clients can start using the controller, with remaining data downloaded in priority order. 10GbE and 1GbE NIC Support PZOS provides support for high‐performance multi‐media network interface cards (NICs). 10GbE NIC options are available along with continued support for 1GbE NIC copper options. Optical and copper NIC SFP+SR media support are also available on 2U systems with the 10GbE NICs options. Unified Storage Each controller provides RAM, SSD, and HDD media that are homogeneously converged and managed as a single physical local storage pool. The physical configuration and number varies depending on the controller model. For larger systems, the number of SSD and HDD media can be expanded by adding disk expansion shelves (up to a total of 324TB RAW) which becomes available to the system's storage services, including IRC. Enterprise AntiVirus Plugin Protecting file servers from viruses is an important part of an overall security strategy, and products such as McAfee VirusScan Enterprise 8.8 with VirusScan Enterprise for Storage 1.1 address this need well. With the Panzura Enterprise Virus Scanning (VSE) license, you can use McAfee VSE to automatically scan files with the latest virus definitions based on Internet Content Adaptation Protocol (ICAP). McAfee VSE controls the actions taken in the event a virus is detected. These actions include the ability to block the file from being accessed, logging the detection event, and quarantining the file. If a file was previously scanned, it is not rescanned unless the virus signature information has changed, the cloud controller has rebooted, or the filename, contents or path have changed. Configuring the Controller The controller installation process includes initial configuration steps. See the Panzura Storage Controller Installation Guide for instructions. After the controller is installed, use the web UI for all additional configuration and management. Accessing the Web UI To access the controller Web UI, enter the controller’s IP address into your web browser and log in using the following default credentials: Account = admin Password = admin Panzura Storage Controller | Administration Guide 12 Chapter 1 | Overview Navigating the Web UI The web UI contains the following areas (see Figure 2): Top information area — Displays the hostname of the controller, software version, user name, and link to log out. Tabs — Allows you to access the Dashboard, Configuration, or Maintenance pages. The Dashboard is selected when you first open the web UI. Left side menu — Allows you to navigate to individual configuration and maintenance pages. Visible only when you click the Configuration or Maintenance tab. The contents of the side menu depends on what license are active and can also depend on configuration settings. For example, the CIFS Settings page is visible on the side menu only if a CIFS license is active and CIFS is selected as an option on the CloudFS page. Alert area—Presents current alert information. Shown only if there is are current alerts. Figure 2 Web UI Tabs Top information area Alert area Left side menu Dashboard The Dashboard page opens when you log in to the controller and is accessible at any time by clicking the Dashboard tab. Panzura Storage Controller | Administration Guide 13 Chapter 1 | Overview Figure 3 Dashboard The Dashboard page shows the following information: Network Throughput – Shows ingress and egress bytes (bytes per second) for the selected time period. (See “Data Interval and Refresh Rate” on page 16.) Bandwidth Summary (Last Week) – Shows a summary of bandwidth use over the last week, in 3‐ hour increments. Bandwidth is shown for traffic from the controller to clients. Disk and RAID – Shows the status of the local storage disks on this controller. Data storage availability counters are provided for all local disks plus cloud storage. Note In Unified Management deployments, this counter does not include storage for disks on other controllers in the group. On a new controller, the storage statistics are for the local device only. When you install a license for cloud storage, the storage statistics are immediately updated to include the storage available in the cloud. Panzura Storage Controller | Administration Guide 14 Chapter 1 | Overview Multi‐Site Topology (CloudFS) – Shows status information for each controller (see the following section). Multi‐Site Topology The Multi‐site Topology (CloudFS) section of the Dashboard now includes detailed information about the synchronization state of all controllers. This information can help a Panzura administrator identify when the controllers within a CloudFS are not in sync. In some extreme cases, controllers not being in sync can cause end users to report not being able to see recently created files or folders. Panzura controllers use system level snapshots behind the scenes to communicate local filesystem changes to all other controllers. These are unrelated to the user snapshots that can be scheduled within the Web UI. When a controller takes a system level snapshot, it is sent to the cloud. All other controllers download and apply this snapshot. This makes it possible for the users accessing the other controllers to have a view of the non‐local portion of the filesystem. In some extreme cases, a controller might fall behind in uploading its latest system level snapshots, or a controller might fall behind in downloading its peers' latest system level snapshots from the cloud. If either of these occurs, the CloudFS becomes out of sync. This can lead to end users reporting that they cannot see newly created files or folders. The Snapshot Generated column contains the reference number for the most current system level snapshot that the controller has created, while the Snapshot Uploaded column contains the reference number for the latest system level snapshot that the controller has successfully uploaded to the cloud. For example in the following figure, the most current system level snapshot generated by cc1‐blr has a reference number of 2026. The latest snapshot cc1‐blr has uploaded to the cloud is also 2026. Because these match, it is clear that the controller is not falling behind with uploading system level snapshots. Had the Snapshot Generated reference number been 2036 or higher and the Snapshot Uploaded reference number been 2026, that would indicate that the 10 most recent system level snapshots had not yet been uploaded to the cloud. In this scenario, the network connection from cc1‐blr to the cloud should be checked. The last column to the right is titled Snapshot Received Locally. It contains the reference number of the latest system level snapshot from the controller that has been downloaded and applied to the controller from which the admin is currently viewing the Dashboard. In the following figure, the data indicates that the cc1‐NVA system level snapshot 1743 has been received from the cloud and applied to controller cc1‐ca. So controller cc1‐ca is in sync with cc1‐NVA. Panzura Storage Controller | Administration Guide 15 Chapter 1 | Overview Had the Snapshot Received Locally reference number been 1733 and the Snapshot Uploaded number been 1743, that would indicate a problem. Users connected to cc1‐ca would have an old view of cc1‐ NVA. In this scenario, the network connection between cc1‐ca and the cloud should be checked. In general, all controllers should be within several snapshots of each other. When controllers are out of sync by five or more or more snapshots, end users will begin to notice problems. To see the exact date and time of the latest received snapshot, hover over the Snapshot Received Locally reference number. Data Interval and Refresh Rate By default, statistics are shown for the most recent 1‐hour period, and are refreshed once a minute. You can change the data interval and refresh rate. Data interval – The data interval can be one of the following: — 5 minutes — 30 minutes — 1 hour — 24 hours — 7 days — 30 days Refresh interval – The refresh interval can be one of the following: — — — — Off (no automatic refresh) 30 seconds 1 minute 5 minutes Panzura Storage Controller | Administration Guide 16 Chapter 1 | Overview You also can refresh the data at any time by clicking Update Now. Redisplaying the Dashboard If you navigate away from the Dashboard, you can easily display it again by clicking the Dashboard tab. Configuration Pages The Configuration pages are divided into Basic Settings and Advanced Settings. The Basic Settings pages are listed when you click the Configuration tab. To list the Advanced Settings pages, click Advanced Settings. For information on configuration tasks, see Chapter 2, “System Setup.” Click the Maintenance tab to display the Maintenance pages. For information on maintenance tasks, see Chapter 3, “Maintenance Operations.” Panzura Storage Controller | Administration Guide 17 2 System Setup This chapter describes the settings on the Configuration pages for the Panzura Storage Controller (controller). See the Panzura Storage Controller Installation Guide for instructions on installation and initial setup. Basic Settings “System (Basic)” on page 19 “Network” on page 21 “Time” on page 26 “Encryption and Certificates (Basic)” on page 27 “CloudFS” on page 32 “Active Directory (Basic)” on page 34 “AMI Hosts” on page 36 “NFS” on page 36 “CIFS (Basic)” on page 40 “Snapshot” on page 42 “License Manager” on page 43 Advanced Settings “System (Advanced)” on page 50 “KMIP” on page 52 “High Availability” on page 54 “Encryption and Certificates (Advanced)” on page 56 “Active Directory (Advanced)” on page 61 “CIFS (Advanced)” on page 63 “Snapshot Manager” on page 64 “Cache” on page 65 “Data Locality Settings” on page 66 “Bandwidth Limit” on page 71 “SNMP” on page 73 “Logging” on page 75 Panzura Storage Controller | Administration Guide 18 Chapter 2 | System Setup Basic Settings The following sections describe how to configure basic settings. System (Basic) X Configuration > Basic Settings > System Use this page (Figure 4) to set the controller hostname, enter location and contact information, and assign a configuration mode. Configuration modes: Master – This controller is the master for a group of distributed controllers. The other controllers are subordinates. All licenses and configuration settings are added to the master controller and automatically propagate to the subordinate controllers. Subordinate – This controller is a subordinate that is managed by a master. By default, all controllers are set as subordinates. Each deployment must have at least one master. By default, all controllers are masters and maintain their own security and configuration. When you add a subordinate, you must specify the master that will manage it. All configuration settings on the master are automatically propagated to the subordinates. After setting up the hostname and IP address information during installation, you do not need to configure any additional settings on the subordinates. If you have two masters in the same CloudFS list, ensure that their encryption certificates are the same at all times, as all systems in the same CloudFS list must have same encryption certificates. Caution Every time a subordinate is rebooted or the master configuration changes, the configuration of the subordinate is updated. If you change a controller from a master to a subordinate, the current configuration is overwritten with the configuration from the master. This can cause loss of user access to CIFS shares. Panzura Storage Controller | Administration Guide 19 Chapter 2 | System Setup Figure 4 System Settings (Basic) This field is visible only if Subordinate mode is selected After setting values, click Save. Caution Select the hostname carefully. Hostname changes can only be performed with assistance from Panzura Support. Table 1 System Settings (Basic) Item Description Hostname Set the controller hostname. The name must be unique within the CloudFS (no other controllers within the same CloudFS can have the same name). This simplifies administration and access to the managed controllers. Use the local DNS server at each site to return the IP address of the local controller. You can rename the controller without affecting the filesystem name. After renaming you must rejoin the domain. Location Location of the controller. Allows you to identify the location of the con‐ troller in the support emails. Contact Enter the contact email for the person responsible for controller administration. Configuration Mode Select whether the controller is a master or subordinate. Default is Master. When you select Subordinate, a field appears for you to add the hostname of the associated master. Panzura Storage Controller | Administration Guide 20 Chapter 2 | System Setup Network X Configuration > Basic Settings > Network Use this page to set the network parameters. Network ports are defined as follows: GB1 = ix0 = A = LAN: This port is for CIFS/NFS connections to clients. GB2 = ix1 = B = Object Store (could be WAN): This port is used to connect to the object store in the cloud. See the Panzura Storage Controller Installation Guide for locations of the controller ports. Note If you use the Command Line Interface (CLI) to perform initial configuration, some IP settings are already configured. You can use this page to change them if necessary. The controller can be deployed in the network in either of the following modes: One‐Arm – The controller is connected to the network through a single interface, GB1. The controller is not directly in the traffic path between the internal and external networks. Figure 5 One‐Arm Deployment Panzura Storage Controller | Administration Guide 21 Chapter 2 | System Setup Inline – The controller is connected to the network by separate LAN (GB1) and WAN (GB2) interfaces. This option requires at least one static route, to enable the controller to forward traffic to the WAN. When using inline mode, make sure that the two networks, GB1 and GB2, are on different subnets and that the DNS server is not on the GB2 (WAN network). Because GB2 is intended only for cloud traffic, if the DNS server is on the WAN network, the internal firewall blocks the DNS traffic. Figure 6 Inline Deployment Figure 7 shows the page and Table 2 describes the settings. After setting values, click Save. Note If you change the IP address of the interface through which you logged onto the Web UI, your management session is terminated as soon as you click Save. Panzura Storage Controller | Administration Guide 22 Chapter 2 | System Setup Figure 7 Network Settings (One‐Arm) Panzura Storage Controller | Administration Guide 23 Chapter 2 | System Setup Table 2 Network Settings Item Description Network Deployment Mode Choose One Arm (default) or Inline. If you choose Inline, the page displays additional settings for the GB2 interface and static route table. See the description at the beginning of this section for details. The Inline option requires at least one static route to enable the controller to forward traffic to the WAN. Network Hosts Click Add a Host to add a host to the local hostname file for address resolution without the use of an external DNS server. A host can be another controller, a Windows domain controller, or another system on the network. Specify the following for each host, and click Add: • Host name (fully qualified domain name [FQDN]) • IP Address Add or remove additional entries as needed. To remove an entry, select its checkbox and click Delete Selected. If you need to modify an entry, delete the existing entry and then add a new one. Cloud Controller GB1 Inter‐ Set the configuration for the GB1 interface. One‐arm deployments use GB1 face Configuration for both client access and connecting to the object storage. GB1 is the only interface that needs to be configured. Inline deployments use both the GB1 and GB2 interfaces. In this case, GB1 will be dedicated to client access to the controller. • Use DHCP—Select this checkbox to have addresses assigned automati‐ cally by an external Dynamic Host Configuration Protocol (DHCP) server. If you select this checkbox, other settings in this section are disabled. • Use Static IP Address—Assign the following settings for static IP addressing: — IP Address—IP address assigned to the interface. — Subnet Mask—Subnet mask assigned to the interface (format x.x.x.x). — Gateway IP—IP address of the network gateway. — Primary DNS Server IP—IP address of a the preferred server to pro‐ vide DNS. — Secondary DNS Server IP—Optional IP address of a the preferred server to provide Domain Name Service (DNS). — DNS Domain Name—Name of the domain where the controller is installed. — Jumbo Frame—Disable or enable jumbo frames. Enabling jumbo frames can improve performance in high‐speed (gigabit Ethernet or higher speed) networks; however, they only work if fully supported on network devices and they increase CPU and memory load on the controller. Make sure that you understand the use of jumbo frames before enabling this feature. Panzura Storage Controller | Administration Guide 24 Chapter 2 | System Setup Table 2 Network Settings (continued) Item Description WAN bandwidth limit Set bandwidth limits for WAN traffic: • Enable bandwidth limit—Enable or disable bandwidth limits. • Max. Upload (Mbps)—Maximum bandwidth for file upload (Mbps). Default is 8. • Max. Download (Mbps)—Maximum bandwidth for file download (Mbps). Default is 8. Note: If your site is provisioned with less WAN bandwidth than these limits, the controller will fully consume the capacity. Panzura recommends that you set these limits under your upload and download bandwidths. On the Bandwidth Limit Settings page (see “Bandwidth Limit” on page 71), it is possible to configure bandwidth limits to conform to a schedule. If bandwidth limits that are set on the Network Settings page conflict with scheduled bandwidth limits, the schedule bandwidth limits take prece‐ dence. GB2 Interface Configura‐ tion (Inline configurations only) Inline deployments use the GB2 interface to connect to object storage in the cloud. • IP Address—IP address assigned to the interface. • Subnet Mask—Subnet mask assigned to the interface (format x.x.x.x). • Gateway IP—IP address of the network gateway. • Jumbo Frame—Disabled or enabled jumbo frames. Static Route Table This menu item is visible only when you select the Inline network configu‐ ration. Enter static routes for the GB2 interface. You must enter at least one static route to allow the controller to forward traffic to the WAN. To add a route, click Add Static Route and enter the following information: • IP Address—IP address for the route table entry. To configure a default route, enter 0.0.0.0. • Netmask—Subnet mask assigned to the interface (format x.x.x.x). To configure a default route, enter 0.0.0.0. • Gateway IP—IP address of the network gateway. Then click Add to add the entry to the static routes table displayed on the page. To remove an entry, select its checkbox and click Delete Selected. Add or remove additional entries as needed. Panzura Storage Controller | Administration Guide 25 Chapter 2 | System Setup Time X Configuration > Basic Settings > Time Use this page (Figure 8) to set the date and time on the controller. CloudFS deployments require that all controllers and Active Directory servers have their clocks synchronized. For the most accurate time synchronization, use the Network Time Protocol (NTP) option and specify the same NTP server for all controllers and the Active Directory server. Note For multi‐site deployments, it is a requirement to have all controllers and Active Directory servers synchronize their time from the same NTP source (for example, pool.ntg.org). If the times are not synchronized, CIFS users will not be able to log in and obtain access to their CIFS shares. Table 3 describes the settings on the page. Figure 8 Time Settings After setting values, click Save. Table 3 Time Settings Item Description Use NTP Select to obtain time settings from a Network Time Protocol (NTP) server. Enter the fully‐qualified hostname or IP address of the NTP server. Set Time Manually Select to enter the time directly. This option is not recommended, because accurate time synchronization is critical for CIFS users and it is difficult to maintain accurate time synchronization manually. If you must specify manual time entries, enter the date in dd/mm/yyyy format and the time in hh:mm:ss format using a 24‐hour clock. Panzura Storage Controller | Administration Guide 26 Chapter 2 | System Setup Table 3 Time Settings (continued) Item Description Time Zone Select the time zone from the dropdown list. Encryption and Certificates (Basic) X Configuration > Basic Settings > Encryption & Certs Use this page (Figure 9) to upload pre‐created data encryption and web HTTPS certificates. Data encryption certificates are created, and KMIP certificates are retrieved, using the Advanced Settings > Encryption & Certs page. See “Encryption and Certificates (Advanced)” on page 56. Encryption certificate: The encryption certificate is used to encrypt data that is sent to the cloud and decrypt data that is received from the cloud. You can use the default encryption certificate or install a replacement certificate. By default, no certificate is active. To use the controller, you must activate the temporary certificate (not recommended) or use a custom certificate. When a custom certificate is loaded, it is visible in the list of encryption certificates. You can activate the custom certificate by clicking Activate in the Action column. Web certificate: The web certificate is presented when an administrator accesses the controller web interface. You can upload multiple certificates and then activate one of them to replace the default x509 PEM web authentication certificate. The next subsections provide additional information about how certificates are used. System Management Web certificates are used when the administrator manages the controller via a Web browser. This is a normal HTTPS security mechanism for guaranteeing the authenticity of a remote system, in this case the controller. The controller ships with a default X509 PEM web certificate issued and signed by Panzura, Inc. You can install a new replacement certificate via the Web UI. Rules on using Web certificates: You can have only one Web certificate You can never delete the default Panzura certificate Only one Web certificate can be active Panzura Storage Controller | Administration Guide 27 Chapter 2 | System Setup Data Encryption The encryption certificate is used to encrypt data sent to the cloud and decrypt data that is read from the cloud. Each controller ships with a default data encryption certificate (P12 formatted) that is issued and signed by Panzura, Inc. The security Web UI provides administrators with the ability to manage encryption certificates with flexibility, but care must be taken when doing this because controllers are fundamentally designed to share cloud data across multiple controllers, geographies, locations, and groups of users. The pre‐ installed Panzura issued encryption certificate can be used or can be easily replaced with a customer owned/issued certificate. By default, no certificate is active. To use the controller, you must activate either the temporary certificate (not recommended) or a custom certificate. After a customer‐issued certificate is loaded, it is displayed in the certificate list. You can select and activate any certificate, as described in this section. The following restrictions apply. All cloud controllers operating in a common single CloudFS must use the same encryption certificate for global read‐write collaboration to operate successfully. Unpredictable data access and client I/O experiences can occur if this certificate topology is not implemented. Although multiple encryption certificates can be loaded, each Panzura controller uses one active certificate for all data operations. Multiple certificates cannot be active. When a different certificate is activated, the system uses the new active certificate to encrypt all new data while using older certificates, no longer active, to decrypt data that was encrypted with those certificates. You can delete a certificate only if it has never been activated. If the certificate has ever been used it must remain on the controller. Panzura Storage Controller | Administration Guide 28 Chapter 2 | System Setup Figure 9 Security (Basic) Panzura Storage Controller | Administration Guide 29 Chapter 2 | System Setup The next table describes the actions on the page. Use the following procedures if you need to generate a self‐signed web and/or encryption certificate: “To generate a self‐signed web certificate” on page 30 “To generate a self‐signed encryption certificate” on page 30 Table 4 Web Certificates Settings Item Description Change Active Certificate Select the radio button for the certificate to activate, and click Apply. To remove a previously uploaded certificate, click Delete. You cannot delete the temporary web certificate that is shipped with the controller. Upload New Web Certificate To use a new x509 PEM certificate, enter a name to identify the certificate in the certificate list and click Browse to find and select the certificate file. Click Upload Certificate to make the certificate available for selection. Fol‐ lowing upload, the name of the new certificate is shown. Upload New Encryption Certificate Enter a name to identify the certificate, and click Browse to find and select the certificate file. Enter and confirm a passphrase. This is the export password that is assigned when creating the encryption certificate from OpenSSL. Click Upload Certificate to make the certificate available for selection. Click Reset to clear any settings entered in this section but not yet saved. To generate a self‐signed web certificate 1. You can download openssl binaries from http://www.openssl.org/ and install them on Windows or Linux. For Linux, check the distribution for the install package. 2. Open a command prompt (or terminal if you are using Linux) and issue the following command. # openssl req -x509 -nodes -days 365 -newkey rsa:1024 -keyout cc1.pem -out cc1.pem This will create a certificate named cc1.pem that will be used to upload from the Web UI. When the certificates is uploaded and activated, the Web UI will refresh with the self‐signing certificate. 3. Click Apply to activate the certificate and deactivate the previously active certificate. If you already have a third part signed certificate to convert to x509 PEM, open a text editor and paste the keys from the certificates for the certificate chain in the following order and save as a PEM file. 1. Private.key 2. Domain.crt: For domain certificate 3. Intermediate.crt: For the Intermediate certificate 4. Root.crt: For the Root certificate To generate a self‐signed encryption certificate 1. You can download openssl binaries from http://www.openssl.org/ and install them on Windows or Linux. For Linux, check the distribution for the install package. 2. Use the following command to generate a private key if one doesn’t exist. Panzura Storage Controller | Administration Guide 30 Chapter 2 | System Setup # openssl genrsa -des3 -out cloudfs.key 2048 The command example uses DES as the encryption algorithm. Because keys are sensitive information, make sure you store them carefully and encrypt them using a strong passphrase and cipher. You can use the DES, Triple DES, IDEA, or 128, 192, or 256‐bit AES symmetric ciphers by adding des, des3, idea, aes128, aes192, or aes256 flag to the command line. The default is triple DES (des3). 3. Use the following command to create a CSR from the private key you created. The CSR file contains your certificate application information, including your public key. # openssl req -new -key cloudfs.key -out cloudfs.csr 4. The process prompts you for details for the CSR file to create a Distinguished Name (DN). Some fields have a default value, which you can change as needed. If you enter a period (.), the field is left blank. The default values are read from the openssl.cfg file. For Common Name, specify the fully qualified domain name (FQDN) of the controller, for example, cc.panzura.com. You can leave the email address, optional company name and challenge password fields blank. Country Name (2 letter code) [US]: US State or Province Name (full name) []: California Locality Name (eg, city) []: San Jose Organization Name (eg, company) []: Panzura Inc Organizational Unit Name (eg, section) []: Support Common Name (eg, YOUR name) []: cc.panzura.com Email Address []: 5. In addition to setting values for the existing parameters, add the following additional attributes to the file. A challenge password []: An optional company name []: 6. To generate a pair of private key and public CSR for a controller, CC1, use the following command, which creates two files; cloudfs.key and cloudfs.csr. The file cloudfs.key contains a private key; do not disclose this file to anyone. Carefully protect the private key in case of disaster recovery and be sure to back it up, as there is no way to recover if it is lost. The private key is used as input in the command to generate a CSR. # openssl req -new -nodes -keyout cloudfs.key -out cloudfs.csr -newkey rsa:2048 7. To create a self‐signed certificate from the private key and CSR that you generated, use the following command: # openssl x509 -req -days 365 -in cloudfs.csr -signkey cloudfs.key -out CC1.crt 8. Issue the next command to bundle the p12. The command reads the encoded certificate and key and exports to a single PKCS#12 file. By default, the key will be encrypted with triple DES and you will be prompted for an export password (which may be blank). # openssl pkcs12 -export -in CC1.crt -inkey cloudfs.key -out CC1.p12 -name "Friendly Name" Note You can concatenate the root certificate and any other certificates in the chain into a single file (for example, root.crt) and included in the PKCS#12 file as follows: # openssl pkcs12 -export -in CC1.crt -inkey input.key -certfile root.crt -out CC1.p12 9. In the controller web UI, click Browse under Encryption Certificates to upload the CC1.p12 file, and then select it. Click Apply to activate the certificate and deactivate the previously active certificate. Panzura Storage Controller | Administration Guide 31 Chapter 2 | System Setup CloudFS X Configuration > Basic Settings > CloudFS Use this page (Figure 10) to configure settings for file storage into the cloud, provided that you have installed a cloud storage license. For information on adding a cloud storage license, see “License Manager” on page 43. Table 5 describes the settings on the page. Figure 10 CloudFS Settings Panzura Storage Controller | Administration Guide 32 Chapter 2 | System Setup After setting values, click Save. Table 5 CloudFS Settings Item Operation Mode Description Note: You can select the CIFS and NFS options only if those licenses are installed. You must activate the CIFS and/or NFS options for them to be displayed on the side menu, Choose the file sharing protocols supported by the controller: CIFS‐only—Supports storage of files accessed using CIFS. CIFS is commonly used within Microsoft Windows network domains to access files. (This file system is also known as Server Message Block or SMB). NFS‐only—Supports storage of files accessed using NFS. NFS is used by Unix/Linux‐based systems. CIFS‐NFS‐mix—Supports storage of files accessed by either CIFS or NFS. This option is not recommended because it may make it difficult to determine which protocol the specific files belong to and could result in access or permissions issues. If you must include CIFS and NFS, make sure that the two types of files are stored in separate directories. Configured Cloud Control‐ Specify the list of controllers that are subordinate to this controller. This lers in CloudFS option is configurable only on an controller that is a master. Click Add a Cloud Controller to add a subordinate controller to the distrib‐ uted controller group. • Enter the hostname of the subordinate controller. The hostname must be an FQDN. • Enter the domain name. The domain name must be a valid DNS domain. • If you are configuring HA‐Distributed, indicate whether this controller will be an active or standby system. Set the mode to Active, unless you are configuring an HA standby controller. See “High Availability” on page 54 for instructions on configuring a standby controller. • Click Add. CAUTION: Deletion or modification of a controller could result in loss of data. For this reason, deletion and editing are not supported in the Web UI. Be careful when adding a controller. If you enter incorrect information (or need to delete a controller), you must work with Panzura Support to correct the information or perform the delete operation. Panzura Storage Controller | Administration Guide 33 Chapter 2 | System Setup Active Directory (Basic) X Configuration > Basic Settings > Active Directory Use this page (Figure 11) to specify Active Directory settings for user access to the controller. For security reasons, the controller does not store admin name and password. When the controller joins the Active Directory domain, it uses the shared secret password provided by the Active Directory for future connections. CIFS File system security CloudFS file system security is compatible with and adheres to the Microsoft CIFS architecture. Files and directories can have user permissions or group permissions known as Active Directory security ACLs. The security ACL information is made available via Microsoft Active Directory network queries between the client, the Active Directory forest, and the controller. This relationship is established and initiated during the client login to the controller. Joining a Microsoft Active Directory domain The controller is designed to participate in Microsoft Active Directory Enterprise Forest topologies and therefore does not support a CIFS workgroup‐only authentication model (a CIFS network with no Active Directory Domain controller). An internal DNS server should be accessible to the controller during the Active Directory join process. The controller will try to understand the Active Directory topology during the join process and locate many Active Directory servers within the domain. These servers will be used as potential candidates during the join process. The process of joining a controller to an Active Directory domain will populate key domain security ACLs within the default BUILTIN groups. This facilitates global read‐write CIFS file sharing access throughout the Panzura unified namespace for each node in CloudFS (such as ..\cloudfs\cc1, ..\cloudfs\cc2, ..\cloudfs\cc3). By default the Active Directory groups 'Domain Admins' and 'Domain Users' are members of the Active Directory BUILTIN groups. If additional domain ACL security is needed, these can be modified after successfully joining the Active Directory domain. Web UI Authentication Using Active Directory If the controller has joined an Active Directory domain, you can set up your AD domain controller to allow authentication to the Panzura controller using Active Directory credentials without additional setup in the Panzura controller. To use this feature, add the following two groups to the AD domain controller: priv_panzura_admins , priv_panzura_users Set the group scope to Global and group type to Security. Users assigned to either of these groups can then log in to the Panzura controller using their AD credentials. Both of the following user name formats are accepted: username@domainname and domainname\username. Panzura Storage Controller | Administration Guide 34 Chapter 2 | System Setup Figure 11 Active Directory Settings (Basic) To join the Active Directory domain that you configured, specify the information in Table 6 and click Join Domain. The page displays the name of the domain controller (if configured) and the current Active Directory domain status. Note If you are joining an Active Directory Read Only Domain Controller, refer to “Joining an Active Directory Read Only Domain Controller” on page 62 To remove the controller from an Active Directory Domain, click Detach from Domain. Domain Administrator credentials are required to perform this operation. Table 6 Active Directory Settings Item Description Active Directory Domain Name Enter the Active Directory domain name and click Save. Active Directory Domain Administrator Enter the user name of the Active Directory administrator. Active Directory Adminis‐ trator Domain Password Enter the password for the Active Directory administrator. Panzura Storage Controller | Administration Guide 35 Chapter 2 | System Setup AMI Hosts X Configuration > Basic Settings > AMI Hosts Note The AMI Hosts page is displayed on the side menu only in a configuration that includes both physical and AMI controllers. The AMI hosts settings simplify management of CloudFS configurations that include both physical and AMI controllers. On a master EC2 Cloud Controller, use this page (Figure 12) to accept or reject subordinate controllers. The pages lists any controllers that are configured as subordinate EC2 controllers. Select a controller and click Accept an AMI Host to add the controller to the CloudFS. The subordinate will add its information to the master bucket, and the master will check the bucket for updates every minute. You can also reject a subordinate controller by selecting it and clicking Reject an AMI Host. For more information about setting up an EC2 Cloud Controller, see the EC2 Cloud Controller Setup Guide. Figure 12 AMI Hosts Settings NFS X Configuration > Basic Settings > NFS Use this page (Figure 13) to select which clients or subnets can access the data stored on the controller. Clients use NFS to mount storage on the controller. In addition to the host access control settings, the file system on the client is used to determine which users have permission to access individual files and directories in CloudFS. Table 7 describes the settings on this page. After setting values, click Save. Note The NFS Settings page is displayed on the side menu only if NFS is licensed and one of the NFS options is selected on the CloudFS page. See “CloudFS” on page 32. Panzura Storage Controller | Administration Guide 36 Chapter 2 | System Setup Figure 13 NFS Settings These fields are displayed for Add Host or Add Subnet Host(s) or subnet(s) Host(s) or group(s) Panzura Storage Controller | Administration Guide The Directory field is displayed only if a local or remote (not global) file system is selected These fields are displayed for Add Group of Hosts or Add Group of Groups 37 Chapter 2 | System Setup Table 7 NFS Settings Item Description Add host Click Add Host to include hosts for which the controller will provide data storage. Specify the following: • File system—Select a file system from the dropdown list. • Directory(s)—This field is displayed only if specific local or remote (not CloudFS) file system is selected. You can optionally select one or more directories within the file system to be mount points. • Host(s)—Specify one or more host IP addresses, machine names, net‐ group names, or combination of group names (separated by a space). • Permission — Read‐only—Allows read‐only access to files. — Read‐Write—Allows the read‐write access to files. — No‐root‐Squash—Allows root users on the NFS clients to access all files that are available on the NFS server. • Alldirs Mount — Yes—The client is allowed to mount any directory under the selected directory. — No—The client can mount only at the specified directory level. • Root Access — Yes—Root access is provided to the specified directory. — No—Root access is not provided to the specified directory. • Description—Enter a text description (optional). To delete a host, select it and click Delete Selected. If you need to modify a host entry, you must remove it, save, and then add the host again with the changes. Example (one host, one directory) Filesystem: /cloudfs/cc1‐ca Directory: NFS1 The path /cloudfs/cc1‐ca/NFS1 will be exported. Host(s): 10.11.12.12 Permission: Read‐write Alldirs Mount: No Root Access: No Example (multiple directories, multiple hosts, Alldirs, and root access in one entry) Filesystem: /cloudfs/cc1‐ca Directory: NFS1/dir1/dirA NFS1/dir1/dirB The paths /cloudfs/cc1‐ca/NFS1/dir1/dirA and /cloudfs/cc1‐ca/NFS1/ dir1/dirB will be exported. Host(s): 10.11.12.12 10.11.12.13 Permission: Read‐write Alldirs Mount: Yes Root Access: Yes Panzura Storage Controller | Administration Guide 38 Chapter 2 | System Setup Table 7 NFS Settings (continued) Item Description Add subnet Click Add Subnet to include all hosts on a specified subnet. Enter the sub‐ net address and netmask, choose a permission option, and click Add. Repeat to add additional subnets. Permission options include: • Read‐only—Allows read‐only access to files. • Read‐Write—Allows the read‐write access to files. • No‐root‐Squash—Allows root users on the NFS clients to access all files that are available on the NFS server. To delete a subnet, select it and click Delete Selected. Add group of hosts Click Add Group of Hosts to add a set of hosts as a netgroup. The hosts in the netgroup must be local (not synchronized throughout CloudFS). Specify a name for the group and enter a set of hosts using hostnames or IP addresses or a combination of both. Use a space to separate the entries. Examples: 10.1.1.1 10.1.1.2 10.1.1.3 host1 host2.example.com 10.1.1.1 host1 host2.example.com A netgroup functions as a unit when checking permissions for operations such as remote mounts, remote logins, and remote shell sessions. For remote mounts, the netgroup identifies and classifies machines. For remote login and remote shell sessions, the netgroup identifies users. Add group of groups Click Add Group of Groups to create a netgroup that consists of a set of netgroups. Specify a name for the group and enter a set of groups. Use a space to separate the entries. Example: NETGRP1 NETGRP2 Manually restart NFS ser‐ vice Click Manually Restart NFS Service to restart services after changing the NFS configuration. Panzura Storage Controller | Administration Guide 39 Chapter 2 | System Setup CIFS (Basic) X Configuration > Basic Settings > CIFS Note The CIFS Settings page is displayed on the side menu only if CIFS is licensed and one of the CIFS options is selected on the CloudFS page (see “CloudFS” on page 32). For additional CIFS settings, see “CIFS (Advanced)” on page 63. Follow these steps to create a CIFS share: 1. Log in to a client computer using an Active Directory administrator account. 2. Connect to the share \\<cc‐name>\cloudfs, where <cc‐name> is the hostname of your controller. Refer to the documentation for the client operating system if you need the specific steps to accomplish this step. As an example, on Windows 7 select Start > Run and type the path to the share in the entry field. 3. When you are connected to the cloudfs share, create the share folder: a. In the controller web UI, select Configuration > Basic Settings > CIFS. See (Figure 15). b. Click Add a CIFS Share. c. Specify the share name and path (Table 8). d. Click Add and then click Save. The CIFS share is now created. Verify that the permissions of the share provide the appropriate user level access. Table 8 CIFS Settings Item Description Name Name to identify the share. Example: projects Path Path to the share, in the form /cloudfs/<cc‐name>/<folder name> where <cc‐name> is the hostname of the controller and <folder name> is a location you specify. Example: /cloudfs/star‐01/projects where star‐01 is the hostname of the controller. Note: The cloud controller uses "/" in the path name. Windows uses "\" instead. Panzura Storage Controller | Administration Guide 40 Chapter 2 | System Setup Figure 14 CIFS Settings Panzura Storage Controller | Administration Guide 41 Chapter 2 | System Setup Snapshot X Configuration > Basic Settings > Snapshot Use this page (Figure 15) to configure the timing of snapshots. Table 9 describes the settings on the page. Figure 15 Snapshot Settings After setting values, click Save. Table 9 Snapshot Settings Item Description Enabled User Managed Scheduled Snapshots Select to enable the snapshot feature. Number of Yearly Snapshots to Keep Enter the number of yearly snapshots to keep (default 1). Number of Monthly Snapshots to Keep Enter the number of monthly snapshots to keep (default 11). Panzura Storage Controller | Administration Guide 42 Chapter 2 | System Setup Table 9 Snapshot Settings (continued) Item Description Number of Weekly Snapshots to Keep Enter the number of weekly snapshots to keep (default 3). Number of Nightly Snapshots to Keep Enter the number of nightly snapshots to keep (default 6). Number of Hourly Snapshots to Keep Enter the total number of hourly snapshots to keep (default 24) and use the hourly checkboxes to specify a schedule. The system saves snapshots according to the schedule up to the total specified num‐ ber of snapshots. For example, if you specify 20 for the number of hourly snapshots to keep and select 4 times from the hourly snapshot schedule, then the system saves 5 snapshots taken at each time, for a total of 4 x 5 = 20. License Manager X Configuration > Basic Settings > License Manager Note In a group of distributed controllers, set the CIFS configuration only on the master controller. Use this page (Figure 16) to add, activate, or deactivate other licenses on the controller. The system identifier shown near the top of the page is unique to each controller and is used to generate and request licenses. Table 10 shows the actions on this page. This page allows you to configure the connection between the controller and object storage in the cloud. The cloud license plays a critical role in establishing the connection with the common storage for the CloudFS file system. Table 11 shows the information that needs to be obtained from the cloud storage provider. The configurations are vendor specific, therefore all can be obtained from the cloud account administration Web portal provided by your cloud storage provider. You can also specify settings for file access auditing, as described in “File Access Auditing” on page 47, and Enterprise AntiVirus Plugin (EAP), as described in “Enterprise AntiVirus Plugin Settings” on page 49. Panzura Storage Controller | Administration Guide 43 Chapter 2 | System Setup Figure 16 License Manager Panzura Storage Controller | Administration Guide 44 Chapter 2 | System Setup Table 10 License Manager Tasks and Settings Item Description Add a license Uploads a license to the controller. Click Browse to locate the license file and then click Add License to make the license available for activation. NOTE: All licenses are keyed to the system identifier of a specific controller and cannot be used for any other controller. If the credentials you enter for a cloud license are not correct, the controller cannot connect to the cloud, and multiple retires could lockout the cloud account. Activate selected Activates the licenses that have checkboxes selected. Deactivate selected Deactivates the licenses that have checkboxes selected. Delete selected Removes the licenses that have checkboxes selected from the License Manager list. PZOS provides support for many cloud storage providers. The following table Table 11 can help you to translate the unique configuration fields of each provider to the fields on the Cloud Connector Settings page. Note Every cloud controller within a CloudFS must specify the same name for "Path" within the Cloud Connector Settings. This field is case‐sensitive. Activate licenses by selecting the checkbox next to each license and clicking Activate Selected. Table 11 Configuration Information for Cloud Storage Providers Cloud storage provider Amazon Simple Storage service (S3) Panzura connector CSP‐Amazon Panzura license field Amazon S3 parameter Path Not applicable to the Amazon web Enter a folder name services settings Access Key ID Secret Access Key Bucket Region Endpoint See Amazon AWS docs link: http://docs.amazonwebsevices.com/general/latest/gr/ rande.html#s3_region User name Password Bucket Hostname Panzura Storage Controller | Administration Guide Notes 45 Chapter 2 | System Setup Cloud storage provider AT&T StaaS Panzura connector CSP‐Atmos Panzura license field EMC Atmos parameter Path Not applicable to the EMC web ser‐ Enter a folder name vices settings UID Subtenant ID:serviceclass=Policy Policy can be policy1 or policy2. Example: Subtenant ID:serviceclass=Policy Refer to A&T for information regarding policy1 and policy2. Shared secret Atmos node name Your Atmos (RMG) Resource Mgmt Group site node name UID Subtenant ID Shared secret Hostname Notes Cloud storage provider EMC Atmos Panzura connector CSP‐Atmos Panzura license field EMC Atmos parameter Path Not applicable to the EMC web ser‐ Enter a folder name vices settings UID Subtenant ID Shared secret Atmos node name Your Atmos (RMG) Resource Mgmt Group site node name UID Subtenant ID Shared secret Hostname Notes Cloud storage provider Google cloud storage Panzura connector CSP‐Google Panzura license field Google cloud storage parameter Path Not applicable to the Google web Enter a folder name services settings Access Key Secret Bucket Google cloud storage host address Currently Google requires this to be commondatastorage.googlea‐ pis.com User name Password Bucket Hostname Panzura Storage Controller | Administration Guide Notes 46 Chapter 2 | System Setup Cloud storage provider HP Cloud Storage Panzura connector CSP‐HP Panzura license field HP Cloud parameter Notes Path Enter a folder name User name Not applicable to the HP web ser‐ vices settings Access Key: Tennant ID Password Bucket Auth Path Secret Key Container Service Endpoint Identity Hostname Service Endpoint Object Storage A combination of the 2 parame‐ ters joined by a ‘:’ The end part of the Identity Server (starting at the ‘:’) with the string ‘/v2.0/tokens’ added Only the FQDN hostname part of Object Storage string (ending at ‘.com’) Note For HP Cloud configurations, enable port 35357 on your firewall for HTTPS traffic. Cloud storage provider Microsoft Azure Cloud Storage Panzura connector CSP‐Microsoft Panzura license field Microsoft Azure Parameter Notes Hostname Path Storage Account Name windows.net ‐‐‐ Storage Account Name Enter a folder name Primary Access Key Container PRIMARY ACCESS KEY CONTAINER From manage access keys Container needs to be created before license activation File Access Auditing The license manager options include file access auditing, which allows you to audit changes to file access across your organization. To set up file access auditing, configure the following settings under AS‐Audit on the License Manager page. Table 12 File Access Auditing Settings on the License Manager Page Item Description Sysloghost IP address or FQDN of the host to receive the audit log. Panzura Storage Controller | Administration Guide 47 Chapter 2 | System Setup Table 12 File Access Auditing Settings on the License Manager Page (continued) Item Description Include Files Files to include in the audit, specified as a comma‐separated list of glob matches (such as *.exe). Exclude Files Files to exclude from the audit, specified as a comma‐separated list of glob matches (such as *temp*). Access Operations to include in the audit. • General operations. open, close, write, read, create, remove, rename, mkdir, rmdir, readdir, access, fsync, link, symlink, readlink • Attributes. setattr, getattr • Extended attributes. getxattr, setxattr, delxattr, listxattr, • ACLs: aclset, aclget, aclcheck • CIFS. sendfile, recvfile, chmod, chown, trunc, lock, unlock, search, chflags, mknod, streaminfo, connect, disconnect, The following is a sample of an audit log as it appears in the syslog server. In the output, the [host] column is the Panzura controller, [uid/sid] is the user identifier, and [err] is one of the following error codes. Code Description 0 No error. 1 Operation permission/capability issue 2 Item does not exist 5 I/O error 6 Device not available 13 Access permissions issue 16 Resource busy 17 File already exists 28 No space left on device 30 Read‐only file system 35 Try again ‐ cloud likely not available Panzura Storage Controller | Administration Guide 48 Chapter 2 | System Setup Enterprise AntiVirus Plugin Settings The Panzura Enterprise AntiVirus Plugin (EAP) license allows you to use McAfee VSE to automatically scan files with the latest virus definitions based on Internet Content Adaptation Protocol (ICAP). EAP actions include the ability to block the file from being accessed, logging the detection event, and quarantining the file. If a file was previously scanned, it is not rescanned unless the virus signature information has changed, the cloud controller has rebooted, or the filename, contents or path have changed. To view the logs associated with EAP, select Maintenance > Diagnostics, and use the show‐log‐tail command, as described on page 81. Table 13 shows the Application Services ‐ ICAP settings on the License Manager page. Table 13 Application Services ‐ ICAP Settings on License Manager Page Item Description Hostname Specify the IP address of the anti‐virus scanner, using commas to separate multiple scanners. The controller load balances across the scanners in a round‐robin fashion. All scanners must be synchronized with identical virus definitions and configured identically. Port Specify the port number used by the antivirus scanners. All scanners must use the same port. The industry standard port assignment for ICAP assigned by IANA is 1344 (default). Service Specify the antivirus scanner ICAP service name. Most scanners ignore this parameter. avscan is the recommended default. Include Files Specify patterns to identify the files to be scanned. The default is '*' which indicates that all files are scanned. Example: Enter *.exe, *.docx to scan only files with the exe or docx suffix. Exclude Files Specify patterns to explicitly identify files not to be scanned. Example: Enter *.pdf to exclude files with the pdf suffix from the scans. scan‐on‐read Specify whether to scan files when they are open for reading (default no). scan‐on‐write Specify whether to scan files when they are saved or closed (default no). Deny on Error Specify whether to assume content is suspicious and deny access if the av scanner is non‐responsive for any reason and no other scanners are avail‐ able (default yes). allow206 Not currently supported. Panzura Storage Controller | Administration Guide 49 Chapter 2 | System Setup Advanced Settings The following sections describe how to configure advanced settings. System (Advanced) X Configuration > Advanced Settings > System Use this page (Figure 17) to set the consistency schedule, data compression, deduplication, and SSD cache. Table 14 describes the settings on the page. Figure 17 System Settings (Advanced) After setting values, click Save. Table 14 System Settings (Advanced) Item Description Consistency interval Specify the interval at which all controllers within the CloudFS attempt to synchronize changes. Panzura Storage Controller | Administration Guide 50 Chapter 2 | System Setup Table 14 System Settings (Advanced) (continued) Item Description Data Compression Select whether to enable or disable data compression for files that are moved to the cloud for storage. Default is enabled. Data compression can provide more efficient use of local and cloud stor‐ age and more efficient data transfers; however, if data compression is dis‐ abled, performance might increase slightly and the system might use slightly less memory. The trade‐off is between efficient use of resources and performance. We recommend that you enable data compression globally on this page. If you have some specific data files that you do not want to compress (because they are already compressed). You can override data compres‐ sion for specific data sets on the Data Locality page. See “Data Locality Set‐ tings” on page 66. Data Deduplication Note: This field is visible only if the data deduplication license is installed. Select whether to enable or disable data deduplication for files that are moved into the cloud for storage. Data deduplication provides improved use of local disk storage (cache) and long term (cloud storage). Default is enabled. Enabling data deduplication on a controller benefits other controllers as well because the results of data deduplication are shared across all the systems. Results of data deduplication are data‐specific and require the use of CPU, memory, and disk I/O. It is not recommended for data sets that are already optimized and for those where appropriate duplication patterns cannot be detected (mpg, audio files, encrypted files, or files that are already dedu‐ plicated). You can override data deduplication for specific data sets on the Data Locality page. See “Data Locality Settings” on page 66. Cloud Upload Order Specify the order in which data is uploaded to the cloud storage. Permission options include: • Data then Metadata—Upload data first and then metadata. (Default) • Metadata—Upload metadata first and then data. Note: This setting should be changed only with guidance from Panzura technical support (professional services?). Panzura Storage Controller | Administration Guide 51 Chapter 2 | System Setup Table 14 System Settings (Advanced) (continued) Item Description Configurable Mesh The use of the Configurable Mesh option requires specific deployment steps and preparation. If you plan to deploy systems with this option, work with your Systems Engineer and Panzura support to design your deploy‐ ment before configuring your systems. Note: This field is visible only if the configurable mesh license is installed. By default, all controllers within a CloudFS receive file system updates for all of the CloudFS filesystem. This means that all systems have a complete, up to date view of the file data and the filesystem metadata. The configurable mesh option allows you to limit updates to specific con‐ trollers. The storage and bandwidth requirements for a site can be reduced by limiting these updates. Drive File Size Specify the drive file size from the dropdown list. Modifying the drive file size provides the ability to accommodate sites that may have less than the recommended 10Mbps network connection. This setting should be changed only with guidance from Panzura Support. SDD Cache Show Settings Do not change this setting unless directed to by Panzura Support. KMIP X Configuration > Advanced Settings > KMIP Use this page (Figure 18) to configure connection to a Key Management Interoperability Protocol (KMIP) server and to manage KMIP certificates. Table 15 describes the actions on the page. Communication with the KMIP server requires a mutually authenticated SSL session. You must upload the certificate authority (CA) certificate (the one that signed the KMIP server's server certificate) and client certificate for a KMIP server. Only one certificate of each type can be uploaded. To upload another certificate, you must delete the certificate of that type that was previously uploaded. After uploading the KMIP related certificates, you can register encryption certificates. See “Encryption and Certificates (Advanced)” on page 56. Note Only master controllers can interact with a KMIP server. Panzura Storage Controller | Administration Guide 52 Chapter 2 | System Setup Figure 18 KMIP Settings Panzura Storage Controller | Administration Guide 53 Chapter 2 | System Setup Table 15 KMIP Settings Item Description KMIP Server Specify the following for connection to a KMIP server, and click Save: • KMIP Server Host Name—Specify the IP address or hostname of the KMIP server. • KMIP Server Port—Specify the port for communication with the KMIP server. IANA.org has assigned port 5696 for use by KMIP servers and clients. Your KMIP server documentation will state if it uses a different port number. The EMC RSA Data Protection Manager uses port 443 for KMIP communication. • KMIP Protocol Type—Select one of the following: — binary TTLV (standard KMIP). — HTTP TTLV (RSA DPM). If you select this option, a Security Class field is displayed. Enter the appropriate security class. • Security Class—Copy the security class specified in the EMC RSA Data Protection Manager product and paste it into this field. Note: If you change to a new KMIP server, you need to register all certificates with the new server. KMIP Certificates The Delete button becomes active after a KMIP Client or KMIP Server CA Certificate has been uploaded. If necessary, click Delete to remove the appropriate certificate. If a certificate is not currently uploaded, the KMIP Certificates area shows "No KMIP Server CA Certificate" or "No KMIP Client Certificate." Upload new KMIP certifi‐ cates Use this section to upload CA and client certificates (X.509 PEM format). Select the certificate type (CA or Client) and click Browse to specify the file. Click Upload Certificate. Following upload, the certificate is listed in the KMIP Certificates area as "KMIP Server CA Certificate" or "KMIP Client Certificate." High Availability X Configuration > Advanced Settings > High Availability Note This section applies to HA standby controllers. See the Panzura Storage Controller Installation Guide for information. The High Availability page is visible only if HA is activated. This page is visible only on controllers that have been configured as a standby, and after the controller has been rebooted. See “CloudFS” on page 32 for information on specifying standby mode. The controller supports HA‐Distributed and HA‐Dedicated modes for high availability. For a general overview of the high availability feature, see “High Availability” on page 11, and for instructions on initiating a high availability takeover, see “High Availability” on page 83. Panzura Storage Controller | Administration Guide 54 Chapter 2 | System Setup The High Availability configuration page (Figure 19) is visible on standby controllers. When a controller is configured as a standby controller, this page is used to select the active controllers for which this controller serves as a standby. Table 16 describes the settings on the High Availability page. Figure 19 High Availability This section appears when you click Add Controller The added controllers are listed in the table After setting values, click Save. Table 16 High Availability Settings Item Description Add Controller Click to add one or more controllers for which this controller will serve as standby, and click Add. The controller is added to the table. The table includes a search box, dropdown list to select the number of controllers to list on each page, and paging controls. Delete Controller Panzura Storage Controller | Administration Guide Select the checkbox for the controller in the table, and click Delete Con‐ troller. Use the checkbox in the column header to select all of the control‐ lers. 55 Chapter 2 | System Setup Best Practices for High Availability CIFS Environments The following best practices apply to high availability takeover and restoration: HA‐Dedicated is supported for use when needing to fail over a system to perform maintenance. When bringing a repaired controller back online in an HA‐Distributed environment, use a new hostname and CCID. This requires that you request a replacement license from Panzura. When bringing a repaired controller back online in an HA‐Dedicated configuration, it will automatically become the standby for the current active controller. Use Microsoft DFS namespace. This will handle the redirection of clients as part of the takeover. In Active Directory, configure folder targets using the IP address of an active controller. Add folder targets that point to standby controllers prior to failover with care. When configuring a folder target that will point to a standby prior to a takeover event, set the referral ordering to Last among all targets in the Properties > Advanced tab of the folder target. NFS Environments The following notes apply specifically to NFS environments: Specify the intr option each time an NFS export is mounted. Allow NFS requests to be interrupted if the server goes down. After performing a takeover, go to the client machines and manually unmount the exports from the failed controller and mount the same exports for the now active controller. Encryption and Certificates (Advanced) X Configuration > Advanced Settings > Encryption & Certs Use this page (Figure 20) to create and register data encryption certificates, and to retrieve encryption certificates from a KMIP server. For information on uploading pre‐created data encryption and web HTTPS certificates, see “Encryption and Certificates (Basic)” on page 27. If you are using a KMIP server, you can also use this page to register a certificate with the KMIP server, retrieve a certificate from the KMIP server, and create an encryption certificate. For instructions on configuring connection to a KMIP server, see “KMIP” on page 52. Panzura Storage Controller | Administration Guide 56 Chapter 2 | System Setup Figure 20 Security (Advanced) Table 17 Encryption and Certificate Actions (Advanced) Item Description Delete a certificate Click the Delete button for the certificate in the Encryption Certificates list. Register a certificate with Click the Register button for the certificate in the Encryption Certificates the KMIP server list. The registration process copies the certificates to the KMIP server. PZOS stores both the certificate and private key in one file. When a certificate is copied to the KMIP server, it is split into two parts: a certificate and a private key. These are stored as KMIP secret data objects. For example, if you register a certificate, mycert, the KMIP server stores the registered certificate as: mycert‐cert and mycert‐key. Create a self‐signed encryption certificate Specify a name for the certificate and click Create & Register. This creates a self‐signed certificate that lasts for five years (RSA 2048‐bit encryption). The full certificate name is hostname of the cloud controller with the cre‐ ation date appended. The created certificate will be registered on the KMIP server. To view the full certificate name, select Basic Settings > Encryption and Certs, and click View for the certificate. Panzura Storage Controller | Administration Guide 57 Chapter 2 | System Setup Table 17 Encryption and Certificate Actions (Advanced) (continued) Item Description Retrieve a certificate from Specify the certificate and private key name, and click Retrieve Certificate the KMIP server to retrieve the certificate from the KMIP server. The certificate is added to the Encryption Certificates list on this page. For example, if you previous registered the certificate mycert, enter mycert‐cert and my‐cert‐key and click Retrieve Certificate. NOTE: If you have a master‐master configuration, any retrieve operation should be done to all masters. Mesh X Configuration > Advanced Settings > Mesh Note The use of the Configurable Mesh option requires specific deployment steps and preparation. If you plan to deploy systems with Configurable Mesh, work with your Systems Engineer and Panzura support to design your deployment before configuring your systems. This page is visible after the Configurable Mesh license is installed. When combining multiple controllers within a CloudFS, you might want to select which controllers synchronize data. By default, the Global Read Write license synchronizes all controllers within the CloudFS. Configurable mesh allows you to control the file system synchronization relationships among controllers. Configurable Mesh allows you to reduce the metadata that is synchronized with any particular controller, thus reducing the synchronization overhead, bandwidth requirements for synchronization events, and visibility to excluded controller. To use Configurable Mesh all of the cloud controllers must first be properly installed, be members of the same CloudFS, be configured as master or subordinate as desired, and have the Configurable Mesh license activated. Following the initial setup, enable Configurable Mesh on all masters, as described in “System (Advanced)” on page 50. Subordinate controllers are automatically enabled for Configurable Mesh when their master is enabled and the setting are propagated to it. This should happen within a few minutes (the exact timing depends on network latency). You can now use the Mesh page (Figure 21) on the master controllers to create the synchronization relationships among all controllers. The synchronization relationships can be either of the following: Uni‐directional, from one controller to another only. Bi‐directional, where both controllers share their filesystems with the other. New synchronization relationships are created as uni‐directional. In order to create a bi‐directional synchronization relationship you must create two uni‐directional relationships. Panzura Storage Controller | Administration Guide 58 Chapter 2 | System Setup Create a uni‐directional synchronization relationship as follows: 1. Start by selecting the desired controller from the Select Controller to Configure list. This controller will be the source of the filesystem to be synchronized with another controller. 2. From the list of controllers in the Doesn’t Sync filesystems of box, select the controller that you want to be synchronized with the source. 3. Click <<< to move the controllers to the Syncs filesystems of box. 4. Verify that this is the desired sync relationship. 5. If the relationship is as desired, click Save. If it is not, click Reset Configuration. A configuration cannot be saved after it is reset. To make the uni‐directional relationship into a bi‐directional relationship, follow these additional steps. 1. Repeat the process starting with the controller that was previously the target of the synchronization for Select controller to configure. This makes it the source. 2. Select the previous controller in the Doesn’t Sync filesystems of, making it the target. 3. Click <<< to move the controller to the Syncs filesystems of box. 4. Click Save. The combination of the two uni‐directional configurations has now created a bi‐directional relationship. Note Configurable Mesh can be used to create a wide variety of filesystem synchronization relationships. It is recommended that customers create only the synchronization relationships that are needed. Panzura Storage Controller | Administration Guide 59 Chapter 2 | System Setup Use this page (Figure 21) to specify cloud controllers for global and local mesh configuration. Figure 21 Mesh Settings Panzura Storage Controller | Administration Guide 60 Chapter 2 | System Setup Active Directory (Advanced) X Configuration > Advanced Settings > Active Directory Use this page (Figure 22) to specify the Active Directory NETBIOS domain and domain controller. Figure 22 Active Directory Settings (Advanced) To set the Active Directory configuration, specify the following settings and click Save. Table 18 Active Directory Settings Item Description NETBIOS Domain Enter the short Active Directory (NetBIOS) name used when logging in with Active Directory credentials. The NetBIOS name is most often used when deploying the Panzura controller on a LAN. The NetBIOS name is limited to 15 characters. Example: NIMBUS‐9 is the NetBIOS name of the Active Directory domain. Domain Controller (optional) Enter the name of the preferred domain controller on your network. Example: ad2.panzura.com To see a list of available controllers, click the magnifying glass icon. As a best practice, leave this field blank. This optional setting allows you to choose a preferred domain controller. However, configuring this optional field pins the Active Directory server selection. This can result in a scenario where an alternate Active Directory server will not be used when the pinned Active Directory server goes offline. Panzura Storage Controller | Administration Guide 61 Chapter 2 | System Setup Joining an Active Directory Read Only Domain Controller The Active Directory Read Only Domain Controller (RODC) deployment mode is a common approach for providing remote site AD services. As the name suggests, the controller is read only and provides a level of security and protection against unauthorized changes. Adding any device, such as a cloud controller, to an RODC requires the use of a Read Write Domain Controller (RWDC). The following steps add the cloud controller to the RODC. 1. From the cloud controller, join the RWDC. See “Active Directory (Basic)” on page 34. 2. From the RWDC: — Use the following command to obtain the fully qualified domain name (FQDN) of the controller. dsquery computer -name <cloud controller hostname> — Use the following command to force replication of the cloud controllers account credentials to the RODC. REPADMIN /RODCPWDREPL <RODC-HOSTNAME> <FQDN of controller from previous command> 3. Verify that the machine name appears in the AD User and Computers list on both the RWDC and RODC. 4. On the RWDC, use the following command to allow the RODC to authenticate the cloud controller. net localgroup "Allowed RODC Password Replication Group" name>$ /add <cloud controller NetBios This completes the process of adding a cloud controller to an Active DIrectory RODC. Select Configuration > Basic > Active Directory page in the Web UI to display the name of the RODC the controller has joined. Note Sometimes samba (winbindd) keeps the connection to RWDC (used for domain join) for a brief period. Eventually at the next winbindd discovery, the Cloud Controller will establish connection with its site local RODC. Panzura Storage Controller | Administration Guide 62 Chapter 2 | System Setup CIFS (Advanced) X Configuration > Advanced Settings > CIFS Use this page (Figure 23) to specify the Server Message Block (SMB) signing setting for CIFS and to enable Access‐Based Enumeration (ABE). Table 19 describes the settings on the page. Note For additional information on CIFS settings, see “CIFS (Basic)” on page 40 and “Snapshot Manager” on page 64. This page is visible only if the CIFS license is installed. Figure 23 CIFS Settings (Advanced) After setting values, click Save. Table 19 CIFS Settings Item Description SMB Signing Select an option for Server Message Block (SMB) signing. SMB signing is a security signature mechanism that can improve the security of the SMB protocol for Windows systems. The SMB options are: • Off—SMB signing is not supported between the client and controller. The controller will reject signed session requests from clients. • Auto—By default, the controller expects clients to use signed SMB ses‐ sions. If the client does not support SMB signing, the client responds with a message to that effect and the controller allows a non‐signed SMB session for that client. If your company enforces SMB signing at the client, and you are having connectivity issues, consider setting SMB signing to Auto. Panzura Storage Controller | Administration Guide 63 Chapter 2 | System Setup Table 19 CIFS Settings (continued) Item Description Access‐based enumeration Select whether to enable Access‐Based Enumeration (ABE). ABE is an administrative capability available to environments using Microsoft clients with shared files and folders. When enabled, users see only the files and folders they have permission to access. If a user does not have read per‐ mission for a specific folder, Windows hides the folder from the user's view. For example, ABE allows you to limit users to see only their personal home directory when they access the home directories shared folder. Hide CloudFS Share Hides the CloudFS share from end users. Snapshot Manager X Configuration > Advanced Settings > Snapshot Manager Use this page (Figure 24) to view the list of user snapshots that have been created and to create a single, unscheduled snapshot manually. Table 20 describes the settings on the page. Figure 24 Snapshot Manager Table 20 Snapshot Manager Item Description Create Snapshot Click Create Snapshot. Enter a name to identify the snapshot, and click Add. To remove a snapshot, select it and click Delete Selected. Panzura Storage Controller | Administration Guide 64 Chapter 2 | System Setup Cache X Configuration > Advanced Settings > Cache This page (Figure 25) contains settings intelligent read cache. Table 21 describes the settings on the page. Work with Panzura support before you consider modifying these settings from the system defaults. See the Panzura technical white paper TWP‐3002 for an in‐depth description of the Intelligent Read Cache settings. Figure 25 Cache Settings After setting values, click Save. Table 21 Cache Settings Item Description Intelligent Read Cache Enable or disable the intelligent read cache. Percent of Storage for Cache Enter the percentage of storage that is reserved for cache. The default is 40%, which is the maximum recommended value. Work with Panzura Support before changing this value. Cache all on Cloud Read Select whether to enable or disable caching for read operations. Default is disabled. When a client requests to read a block of data, the controller fetches the drive file, selects the block, and returns it to the client. Typically the entire drive file is kept in memory cache for a few seconds or minutes before being flushed. When the cache all on cloud read option is enabled, the entire drive file will persist in the cache until it is forced out, possibly for days or weeks. This feature can reduce the number of cloud reads required for files that are being frequently accessed by clients. The only potential downside is that other data in the cache will be flushed more frequently. Panzura Storage Controller | Administration Guide 65 Chapter 2 | System Setup Table 21 Cache Settings (continued) Item Description Prefetch on Directory Select whether to enable or disable. Default is disabled. When enabled, Prefetch on Directory will prefetch all drive files from the cloud when a directory is listed or opened. This is useful only in environ‐ ments that meet both of the following characteristics: • The vast majority of files are less than 128k in size. • The vast majority of files are read nearly immediately after a directory is opened or its contents listed. Enabling this option in directories with large files will cause performance to decrease. Data Locality Settings X Configuration > Advanced Settings > Data Locality Settings Note This page is visible only if the data locality license is installed. Use this page to create policies to govern what data is cached locally on the controller. The controller includes Intelligent Read Cache (IRC), which is designed to provide LAN speed access to data stored in the cloud. Data locality further enhances IRC by allowing you to select specific files and data blocks to be continuously cached locally in the controller. See the Panzura technical white paper TWP‐3002 for an in‐depth description of IRC and pinning. Cache settings must be specified before configuring data locality. See “Cache” on page 65. Data Locality Settings consist of policies and rules within a policy. Policies can act on local or remote file systems and provide automated caching, or pinning, of file data. You can create one data locality policy for each file system and each policy can have multiple rules within the policy. Panzura recommends using the auto cache action with prepopulate enabled. This ensures that files are available in disk cache for end users. Prepopulating makes the data available without forcing a reduction in cache. Pinning allows an administrator to forcefully localize (pin) data in the cache within a controller to provide guaranteed LAN speed performance. Because pinning consumes cache space, it should be considered only if needed for performance, with the trade‐off between performance and cache space kept in mind. For more information, see the Panzura white paper 3002, "Next Generation Intelligent Read Cache and Smart Data Pinning for Cloud Storage." Local and Remote File Systems A controller can have a local file system and multiple remote file systems. The local file system on this page refers to the controller name in CloudFS. When file systems are synchronized in CloudFS, a copy of the metadata for each local file system on a controller is copied to the other controllers (Figure 26). The metadata stored on the other controllers is Panzura Storage Controller | Administration Guide 66 Chapter 2 | System Setup called the remote file system. Remote file system synchronization causes the controller to receive the metadata updates in CloudFS. Figure 26 Local and Remote File System Synchronization Controller cc-b Controller cc-a cc-a Local cc-b Remote cc-a Remote cc-b Local Because a local file system has the same name as the controller name, you can tell if a file system is local by comparing its name with the controller name shown at the top of the page (Figure 27). Figure 27 Local File System Panzura Storage Controller | Administration Guide 67 Chapter 2 | System Setup Setting Up Data Locality Figure 28 shows the Data Locality page and Table 22 describes the tasks and settings on the page. If the system is running and policies are operating, the table at the bottom of the page provides statistics on the rules. For example, the Data Hits column shows the frequency at which the policies are triggered. Figure 28 Data Locality Settings These fields are displayed for Add a Policy These fields are displayed for Add a Rule Panzura Storage Controller | Administration Guide 68 Chapter 2 | System Setup After setting values, click Save to activate the settings. Table 22 Data Locality Tasks Item Description Add a policy Click Add a Policy, specify the new policy in one of the following ways, and click Add: • Enter a policy name in the Add a New Policy Name field, and select a default action (Auto cached or Pinned). If you choose pinned as the default action, the only way to unpin is to specify the auto cache in a rule. Note: We recommend that you keep the default action as auto cache and then use rules to assign pinning. For more information, see the Panzura White Paper 3002, “Next Generation Intelligent Read Cache and Smart Data Pinning for Cloud Storage.” • Select a file system on which to base the policy from the Filesystem dropdown list, and select a policy from the Select a Policy dropdown list. This option allows you to reuse the rules from another policy when creating a new one. If you have multiple controllers in the cloud file system, the Filesystem dropdown list has multiple entries. In this case, you must decide where to apply the policy: to the local controller’s file system, or to a remote controller’s file system on this local controller. See Figure 26. For example, assume that you have nodes at site A and B. You are working from site A, but the data of interest is on site B. For the policy, select the controller B file system from the dropdown. Then when data is written to the remote file system, it is also localized on controller A. Edit a policy After a data locality policy is created, you can edit the default action by selecting from the Action dropdown list . Remove a policy Click the Delete icon to delete a policy. Panzura Storage Controller | Administration Guide 69 Chapter 2 | System Setup Table 22 Data Locality Tasks Item Description Add a rule 1. Click Add a rule. 2. Enter a rule expression. The rule syntax is based on glob programming, with the available actions or auto cache or pinning added to a glob expression. The rules are case sensitive. The controller supports the following types of glob expressions (examples are included): — Match a directory path, which always begins with the filesystem. If the filesystem for the policy is \cloudfs\cc1‐ca, then homedir/sampledir/* matches anything in the sampledir directory under /cloudfs/cc1‐ca/homedir — Match anything in a specified directory from any directory path. */sampledir/* matches any path that includes a sampledir directory, such as ../homedir/sampledir/*, ../temp/sampledir/*, or ../Dept/Sales/sampledir/* — Match one unknown character. ?at matches Cat, cat, Bat or bat. — Match any number of unknown characters. Sys* matches Sys or System — Match a characters as part of a group of characters. [CB]at matches Cat or Bat but not cat or bat — Escape character. Sys\* matches Sys*, does not match Sys\* For example, if you enter *.mp3 and the select Pinned as the action, the rule pins all files with a .mp3 extension. Panzura Storage Controller | Administration Guide 3. Choose a rule action from the dropdown list (Auto cache or Pinned). Auto cache is recommended. 4. Indicate whether to prepopulate the specified files into the IRC whenever the rule is triggered. If you choose Prepopulate (which is recommended), files are cached but not pinned, so they can be evicted by the system if needed. This option is useful for performance optimization for reads when you don't want to forcefully consume cache space with pinning. 5. Indicate whether to apply deduplication to the data. This option controls deduplication for files that match the rule expression. If you specify No, deduplication is disabled for those files. Setting this option overrides the global deduplication setting and allows you to optimize deduplication at a fine‐grained level. For example, If you enabled deduplication globally on the Cloud FS page (“CloudFS” on page 32), you can override that setting for mp3 files by specifying a rule for mp3 files and setting dedup to No. 70 Chapter 2 | System Setup Table 22 Data Locality Tasks Item Description Add a rule (continued) 6. Modify the block size, if needed. Default is 128KB. This option is active only if dedup is set to Yes. It applies deduplication only at the selected block size. This option is useful if you have some data sets with a known block size, such an Oracle database or VMDK file with that block size. If you are backing up the database or file, you can deduplicate at that level to increase efficiency. 7. Click Add to save the rule and display it in the rule list. Because rules are considered in the listed order, you might want to change the rule order. Click the arrow in the Move column to move an entry up or down in the list. To remove a rule, select it and click Delete Selected. Bandwidth Limit X Configuration > Advanced Settings > Bandwidth Limit Settings Use this page (Figure 29) to set policies that limit bandwidth during specified periods. Using bandwidth limits can ensure that the controller does not affect network availability for other users when the controller is communicating with the cloud to store or retrieve data. Panzura recommends that you set a bandwidth value for optimal cloud performance that the controller can use for automatic tuning. Bandwidth limits apply to WAN Cloud Storage write operations (egress packets written to the cloud). to WAN Cloud Storage read operations (ingress packets read from the cloud). for an inline deployment, bandwidth limits apply only to the GB2 (WAN) network interface. Table 23 describes the settings on the page. Panzura Storage Controller | Administration Guide 71 Chapter 2 | System Setup Figure 29 Bandwidth Limit Settings After setting values, click Save. Table 23 Bandwidth Limit Settings Item Description Enable Select the checkbox to activate that policy. You can specify and activate up to five policies. If the conditions for a specific policy are met, then all of the following policies are ignored. From Day To Day Select the days of the week to start and end the rate restriction. For example, if you specify the range Monday through Thursday, then on Monday, Tuesday, Wednesday, and Thursday, the specified limit applies for the specific time period. Hour Select the hour of the day start and end the rate restriction. Bandwidth (Mbps) Enter the maximum bandwidth that is permitted during the period. Maxi‐ mum is 1000 Mbps (default). Panzura Storage Controller | Administration Guide 72 Chapter 2 | System Setup SNMP X Configuration > Advanced Settings > SNMP Settings Use this page to specify the SNMP community string and trap settings. Figure 30 shows the page, and Figure 31 shows the additional settings for SNMPv3, which support an encrypted authentication channel. Table 24 describes the settings on the page. In addition to the SNMP settings on this page, the controller supports the UC Davis MIB objects, which are available at: http://www.net‐snmp.org/docs/mibs/ucdavis.html Figure 30 SNMP Settings Panzura Storage Controller | Administration Guide 73 Chapter 2 | System Setup Figure 31 SNMP Settings (SNMPv3) After setting values, click Save. Table 24 SNMP Settings Item Description Read Community String Enter the community string for communication between the controller and the trap receiver. If you specify a custom community string, the public community string is disabled. SNMP Trap Enter the IP address and community string for up to two trap receivers. Trap Threshold Settings Enter the usage thresholds (percent) that will trigger SNMP trap messages of particular types: CPU usage, memory usage, disk usage, and Cloud usage. The controller generates SNMP traps of the specified type if the usage meets or exceeds the threshold. The thresholds are useful to alert network administrators that additional capacity might be needed soon. For example, if you have 10 TB storage capacity in the cloud, you might want to set a threshold at 7.5 TB so that an SNMP trap is sent when that level is reached. Panzura Storage Controller | Administration Guide 74 Chapter 2 | System Setup Logging X Configuration > Advanced Settings > Logging Settings Use this page (Figure 32) to specify a remote server to receive syslog messages from the controller event log. Table 25 describes the settings on the page. Figure 32 Syslog Settings Panzura Storage Controller | Administration Guide 75 Chapter 2 | System Setup After setting values, click Save. Table 25 Syslog Settings Item Description Syslog Server Enter the IP address or hostname of the syslog server. Logging Level Select the minimum level of messages to send to the server. The selected level and all higher levels are sent. For example, if you specify Error, then messages of type Error, Critical, Alert, and Emergency are sent. Trace Log Select the minimum level of messages to send to the server. The selected level and all higher levels are sent. For example, if you specify Error, then messages of type Error, Critical, Alert, and Emergency are sent. Add an Application Click Add an Application to specify the services to be logged in addition to the standard syslog logging. Select a service and a trace level, and click Add. Add additional entries as needed. To delete an entry, select it and click Delete Selected. Panzura Storage Controller | Administration Guide 76 3 Maintenance Operations This chapter describes Maintenance operations and includes instructions for performing maintenance operations on the Panzura controller. See the following sections: “Diagnostics” on page 77 “High Availability” on page 83 “CIFS Dashboard” on page 85 “Secure Erase” on page 87 “CIoudFS” on page 87 “Cloud Metrics” on page 87 “NFS” on page 90 “Master Snapshot” on page 90 “Cloud Delete” on page 90 “Image Upgrade” on page 91 “Reboot” on page 92 “Support” on page 92 “Password” on page 93 “Advanced” on page 94 Diagnostics X Maintenance > Diagnostics Use this page to use packet capture tools and run diagnostic commands. Packet capture tools—Capture packets on the Ethernet ports. You can select to capture all packets or restrict the capture to TCP or UDP packets. The captured packets are saved into a file that you can download and send to Technical Support. Diagnostic tools—Execute network, controller‐specific , and cloud diagnostic commands. Performance Test tools—Execute Iperf commands to test network performance. Packet Capture X Maintenance > Diagnostics To capture packets: 1. Select the type of packet capture from the dropdown list. 2. Select the interface (gb1 or gb2). 3. Click Start to start packet capture. Panzura Storage Controller | Administration Guide 77 Chapter 3 | Maintenance Operations 4. Click Stop to stop packet capture. To download the captured packets in a file, select Maintenance > Support and click Download Support Log. Table 26 Packet Capture Operations Item Description pkt‐capture Capture TCP and UDP headers and packet. pkt‐capture‐tcp Capture TCP headers and packet. pkt‐capture‐udp Capture UDP headers and packet. pkt‐capture‐header‐only Capture TCP and UDP headers. pkt‐capture‐tcp‐header‐only Capture TCP headers. pkt‐capture‐udp‐header‐only Capture UDP headers. Diagnostic Tools X Maintenance > Diagnostics To use the diagnostics tools: 1. Select a command from the dropdown list (see the following table for a list of commands, with some example options and output). 2. Click Run to display the command output, or show the available options, if the command includes options. For example, in the following figure, clicking Run for the cdiag‐switch command displays the options. Figure 33 Sample Diagnostics Tools Output Panzura Storage Controller | Administration Guide 78 Chapter 3 | Maintenance Operations In the following figure, including the on option for the cdiag‐switch command executes the command. Figure 34 Sample Diagnostics Tools Output Table 27 Diagnostics Tools Commands Item Description cdiag‐report Displays data dump (same as data dump on the Cloud Metrics page). See “Cloud Metrics” on page 87. Example: cdiag‐report tail cdiag‐switch Turns cloud diagnostics on or off. Enter on or off. Diagnostics must be on to use the cloud metrics tools. See “Cloud Metrics” on page 87. This set‐ ting does not survive a reboot. Example: cdiag‐switch on cifs‐add‐gcfg Panzura support use only. cifs‐clr‐gcfg Panzura support use only. cifs‐debug Panzura support use only. cifs‐dsp‐gcfg Panzura support use only. cifs‐regen‐machine‐secret Panzura support use only. cloud‐connect‐test Displays license and connection information based on the cloud license that is loaded, including success, failure, and what ports are open or closed. If the cloud connect is successful, you can perform cloud‐upload‐ test. cloud‐runtime‐stat Displays runtime statistics. Useful mainly for uploads. The statistics for download are not as useful because pre‐fetch is used. For download, you may see failures occur even if status is OK, because the system is looking for future snapshots that do not exist. cloud‐upload‐test Tests the connection to the cloud. diag‐ad‐config Displays the status of the Active Directory connection (joined or not). Panzura Storage Controller | Administration Guide 79 Chapter 3 | Maintenance Operations Table 27 Diagnostics Tools Commands (continued) Item Description layer‐four‐traceroute Sends a Layer 4 traceroute command to the specified IP address and optional port number. Example: layer‐four‐traceroute‐gb2 10.3.3.3:443 layer‐four‐traceroute‐gb2 Sends a Layer 4 traceroute command to the specified IP address and optional port over the GB2 interface (cloud facing). Example: layer‐four‐traceroute 10.3.3.3:443 mark‐remote‐disable Disables remote file marking. mark‐remote‐display Displays the current setting for remote file marking. mark‐remote‐enable Enables remote file marking. nslookup Obtains information about a host. Example: nslookup host5 pchar Displays information on bandwidth latency and loss between the control‐ ler and the specified system. Example: pchar 10.3.4.5 ping Sends an ICMP ping command to the specified IP address. Example: ping 10.3.4.5 ping‐gb2 Sends an ICMP ping command to the specified IP address over the GB2 interface (cloud facing). Example: ping‐gb2 10.3.4.5 repair‐ad‐config Reinitialize the CIFS services. Note that issuing this command results in connection loss. This command does not provide any output. restart‐cifs‐service Restarts the CIFS service. restart‐grw Panzura support use only. run‐cmd Executes a CLI support‐level command. CAUTION: These commands should be executed only under the direction of Panzura support. Any misuse could void your warranty. search‐log Allows you to search the system log for the specified keyword. Example: search‐log AUDIT show‐cfg‐error Displays configuration errors. show‐dp‐data Panzura support use only. show‐dp‐list Panzura support use only. show‐dp‐stats Panzura support use only. show‐fs‐list Lists all of the local and remote CloudFS file systems. show‐fs‐snapshot Lists information about current snapshots. show‐interface Displays interface information. show‐inventory Displays information about the installed Panzura product. show‐log‐config Displays information about config changes. Panzura Storage Controller | Administration Guide 80 Chapter 3 | Maintenance Operations Table 27 Diagnostics Tools Commands (continued) Item Description show‐log‐tail Displays contents of system message logs. If you are using the EAP capability, you can display the logs by using the command: show‐log‐tail /var/log/avquarantine show‐malloc‐stats Displays virtual memory allocation. show‐pktcap‐list Displays results of any previous packet capture. show‐pktcap Displays the contents of pcap file for the most recent packet capture. show‐pktcap‐hex Displays the hex dump of the pcap files for the most recent packet cap‐ ture. show‐pktcap‐host Displays the host information for the most recent packet capture. show‐pktcap‐icmp Displays the ICMP information for the most recent packet capture. show‐pktcap‐list Displays the list of existing packet captures. show‐pktcap‐tcp Displays the TCP information for the most recent packet capture. show‐pktcap‐udp Displays the UDP information for the most recent packet capture. show‐pool‐iostat Shows current file system stats for read and write IO operations and band‐ width usage. show‐pool‐list Displays information about used and free space. Information is the same as in the Dashboard, but in raw form. show‐pool‐status Displays information about drive availability and cloud license. show‐route Displays route table information. show‐system Displays system and file information. show‐vm‐stats Displays virtual memory status. show‐zfs‐properties Panzura support use only. show‐zone‐stats Panzura support use only. show‐system Shows a snapshot of the system resources, including load, CPU, and mem‐ ory usage and the top running processes. traceroute Sends a traceroute command to the specified IP address. Example: traceroute 10.3.3.3 traceroute‐gb2 Sends a traceroute command to the specified IP address over the GB2 interface (cloud facing). Example: traceroute‐gb2 10.3.3.3 Panzura Storage Controller | Administration Guide 81 Chapter 3 | Maintenance Operations Performance Test Tools X Maintenance > Diagnostics The performance test tools measure bandwidth and link quality for the connection between the controller and the cloud. The controller is treated as a client when you specify another server or controller. To measure performance: 1. Select the type of performance tool from the dropdown list. 2. Specify details for the test in the text area. — To run a test with the controller as a server, select iperf‐server‐tcp‐start to start the test and iperf‐server‐stop to stop the test. — To run a test with the controller as a client, select iperf‐client‐tcp and enter the hostname or IP address of another server or controller. 3. Click Run. 4. Click Stop when you are ready to stop the packet capture. Results are displayed in the Diagnostics Output area. Figure 35 Sample Performance Tools Output Output examples This example shows output from client controller vmcc92. Diagnostics[57529]: Firewall is temporarily disabled to allow diagnostics operation and shall be enabled when operation is completed automatically. -----------------------------------------------------------Client connecting to vmcc94, TCP port 5001 TCP window size: 65.0 KByte (default) -----------------------------------------------------------[ 4] local 10.199.10.92 port 45867 connected with 10.199.10.94 port 5001 [ ID] Interval Transfer Bandwidth Panzura Storage Controller | Administration Guide 82 Chapter 3 | Maintenance Operations [ [ [ [ [ [ [ [ [ [ [ [ [ 4] ID] 4] ID] 4] ID] 4] ID] 4] ID] 4] ID] 4] 0.0- 5.0 Interval 5.0-10.0 Interval 10.0-15.0 Interval 15.0-20.0 Interval 20.0-25.0 Interval 25.0-30.0 Interval 30.0-35.0 sec sec sec sec sec sec sec 436 MBytes Transfer 416 MBytes Transfer 369 MBytes Transfer 312 MBytes Transfer 401 MBytes Transfer 359 MBytes Transfer 433 MBytes 731 Mbits/sec Bandwidth 698 Mbits/sec Bandwidth 619 Mbits/sec Bandwidth 524 Mbits/sec Bandwidth 673 Mbits/sec Bandwidth 603 Mbits/sec Bandwidth 727 Mbits/sec This example shows output with the vmcc94, controller acting as the server. Diagnostics[46450]: Firewall is temporarily disabled to allow diagnostics operation and shall be enabled when operation is completed automatically. -----------------------------------------------------------Server listening on TCP port 5001 TCP window size: 64.0 KByte (default) -----------------------------------------------------------[ 5] local 10.199.10.94 port 5001 connected with 10.199.10.92 port 33313 [ ID] Interval Transfer Bandwidth [ 5] 0.0-120.2 sec 9.09 GBytes 650 Mbits/sec [ 6] local 10.199.10.94 port 5001 connected with 10.199.10.92 port 45867 [ ID] Interval Transfer Bandwidth [ 6] 0.0-120.0 sec 9.46 GBytes 677 Mbits/sec High Availability X Maintenance > High Availability Note This menu item is only visible on standby systems where High Availability has been previously configured. On a standby controller, use the High Availability maintenance page to view synchronization status and to initiate a takeover for an active controller that is down. Panzura Storage Controller | Administration Guide 83 Chapter 3 | Maintenance Operations Figure 36 Sample Performance Tools Output Viewing Synchronization Status The Sync Status section lists filesystems and associated snapshot activity, which you can use to assess conditions prior to takeover. For each filesystem, the table shows the ID for the last generated and last received snapshots, along with the timestamp of the last received snapshot and the current filesystem status. If there is a discrepancy between the last generated snapshot and the last received snapshot, it might take a longer time to synchronize following takeover, or some data might become orphaned. If you observe any discrepancy, you can obtain additional information by referring to the Multi‐Site Topology section of the Dashboard (see “Multi‐Site Topology” on page 15). In addition to snapshots generated and received, the Multi‐Site Topology section also reports on snapshots uploaded. If there is a significant difference (> 50) between the values of uploaded and received snapshots, it will take longer for the standby controller to synchronize and become active. If there is a difference of more than 1 or 2 between the generated and uploaded snapshots, some data might become orphaned as a result of the takeover. Takeover The takeover process applies to HA‐Dedicated and HA‐Distributed configurations. The process works as follows. For the example, assume that the active controller is star‐01 (IP address 10.16.0.111) and that the standby controller is star‐03 (IP address 10.16.0.113). 1. The active controller (star‐01) is determined to be down. 2. Open the High Availability maintenance page for the standby controller (star‐03). In the figure, notice that the hostname is star‐03 and that the IP address is 10.16.0.113. After the takeover, the hostname will change to star‐01, while the IP address will still be 10.16.0.113. Panzura Storage Controller | Administration Guide 84 Chapter 3 | Maintenance Operations 3. Click Takeover and click OK to confirm. A takeover status window opens. As part of the takeover process, to ensure that the standby controller has the latest view of the file system, the process attempts to catch up on any file system snapshot downloads. The controller will continue to download file system snapshots in sequence until it encounters a failure. When this happens, the controller will retry the download a total of 10 times, pausing 30 seconds between attempts. After 10 attempts, the controller assumes it has caught up with all file system snapshot downloads and the takeover process continues. The controller performs these actions to work around any network issues that might interfere with the process of downloading consistency snapshots from the cloud. 4. When the takeover is complete, a popup window opens. Click OK. 5. Assuming that you have previously set up the Windows Server DFS‐N namespaces correctly, the Microsoft DFS namespace must be redirected to look at the standby controller that is now active. If this is not done, clients will see an error message when they attempt to access a share. In DFS, add a new folder target with the IP address of the standby controller (10.16.0.113), and delete the path to the failed controller (10.16.0.111). Once this is done, clients have access to the share as if they were still connected to the original controller. CIFS Dashboard X Maintenance > CIFS Dashboard The CIFS Dashboard page displays charts on CIFS activity: Metadata read cache performance Data read cache performance CIFS scaling and performance By default, statistics are shown for the most recent 30 minutes. You can change the time scale to any of the following: 5 minutes 30 minutes 1 hour 12 hours 1 day All (all available statistics) The graphs are dynamic, and each includes multiple data point categories such as metadata reads and memory cache hits. You can show or hide any categories for a specific graph by clicking or hiding the category in the legend for that graph. For example, to focus only on the total metadata reads in the Metadata Read Cache Performance graph, click each of the other categories in the legend so that only that category remains. You can zoom to a pre‐set period of time by using the Zoom button or set a custom zoom level by using the zoom controls below the legend. To zoom into a particular period, slide the zoom control to the left. As you do this, the data to the right of the zoom control is revealed in detail in the larger graph. Panzura Storage Controller | Administration Guide 85 Chapter 3 | Maintenance Operations Figure 37 Maintenance > CIFS Dashboard (excerpt) Legend Zoom control CIFS Users X Maintenance > CIFS Users The CIFS Dashboard page displays a list of the current CIFS users. You can search the list, choose the number of entries to display per page, and use the paging controls to page through the list. Panzura Storage Controller | Administration Guide 86 Chapter 3 | Maintenance Operations Secure Erase X Maintenance > Secure Erase Secure Erase allows you to delete a file or folder in such a way that the contents cannot be restored, even using the most advanced technology available. Secure Erase removes all versions of specified files and folders, including the associated objects stored in the cloud. User managed snapshots containing copies of the files and folders are explicitly noted in the Secure Erase output and not erased. This enables the administrator to take the appropriate action for the snapshots within the context of their environment. The snapshots will age out according to the settings defined in User Managed Snapshot settings (see “Master Snapshot” on page 90). Use the Secure Erase page to manage secure erase operations. 1. Specify the file or directory name to remove. 2. Select a date for deletion, or click Now for immediate deletion. 3. Click Erase to activate the delete operation. The Schedule Files/Directories list shows when scheduled items will be deleted, and the table at the bottom of the page lists the files that have already been deleted. Click Download Report to download a report of the actions taken by secure erase. After the report is downloaded, click Clear Entry to erase all the report contents from the system. CIoudFS X Maintenance > CIoudFS The CloudFS page displays a list of the current CloudFS hosts and allows you to pause or resume remote FS sync. Click Pause in the Remote FS Sync column to suspend sync operation and click Resume to restart. Click Save to implement the change. You can search the list, choose the number of entries to display per page, and use the paging controls to page through the list. Cloud Metrics X Maintenance > Cloud Metrics The graphs on this page provide detailed information on the communication links between the controller and the cloud. The cloud metrics are collected from the controller diagnostic database in five‐minute intervals. The graphs include information only on controller‐to‐cloud communications, not on file system, local storage, or LAN communications. The graphs are dynamic. You can show or hide any categories for a specific graph by clicking or hiding the category in the legend for that graph. For example, to focus only on the total WAN output in the Write Throughput graph, click each of the other categories in the legend so that only that category remains. To enable Cloud Metrics 1. Choose Maintenance > Diagnostics. Panzura Storage Controller | Administration Guide 87 Chapter 3 | Maintenance Operations 2. Under Diagnostic Tools select cdiag‐switch and add on as a parameter. 3. Click Run. After five minutes you can open the Cloud Metrics page to view the graphs for the following metrics. To view the log entries used to generate the data for the past two hours, click the Show Cloud Call Log (last 2 hours) link at the bottom of the page. Throughput Write Throughput: Throughput for all upload (PUT) operations to the cloud. Read Throughput: Throughput all download (GET) operations from the cloud. Duration Average Write Duration: Average time in seconds for upload (PUT) operations to the cloud. Average Read Duration: Average time in seconds for download (GET) operations from the cloud. Panzura Storage Controller | Administration Guide 88 Chapter 3 | Maintenance Operations Statistics Cloud Write Statistics: Statistics for upload (PUT) operations to the cloud. Cloud Read Statistics: Statistics for download (GET) operations from the cloud. Snapshot throughput Statistics on the automatic filesystem consistency checkpoint snapshots that the controller takes during general operation. These are data consistency checkpoints that queue locally on the local file system and then are efficiently uploaded to the cloud as needed. This chart describes the frequency of snapshots and the depth of the queue of waiting uploads relative to the number of successful uploads to the cloud. Panzura Storage Controller | Administration Guide 89 Chapter 3 | Maintenance Operations NFS X Maintenance > NFS Use this page to restart the NFS service. Doing so terminates all NFS sessions. Master Snapshot X Maintenance > Master Snapshot A master snapshot is a consistency point snapshot for the entire local file system on a controller. By default, master snapshots are taken once per week. Because master snapshots can consume significant I/ O resources, Panzura provides the ability to modify the master snapshot schedule. Use this page to modify the schedule for the master snapshot. You can set the date, time, and recurrence interval. To modify the schedule for a master snapshot: 1. Select a day of the week and time from the dropdown lists. 2. Select a recurrence interval (from 1‐4 weeks). 3. Choose one of the following actions: — Save to save the configuration and start the snapshot schedule. — Generate a Master Snapshot Now to order a snapshot on demand. Cloud Delete X Maintenance > Cloud Delete Note This page is visible only on data protection controller models that are deployed exclusively for back‐ up using Symantec NetBackup. When a user deletes a file the objects that comprise the file are placed in a delete queue for 14 days. At the end of 14 days: The objects are deleted from the object store provided. The objects are not required to maintain the integrity of a snapshot or required to re‐hydrate a deduplicated file. This helps to ensure a more orderly delete process from all of the cloud controllers within a CloudFS. If you need to purge objects more quickly than that, contact Panzura Support. The Cloud Delete schedule applies only to Symantec NetBackup images. After deleting a NetBackup image, an administrator can schedule the deletion of the related cloud objects in advance of the 14 day expiration period. This makes it possible to reclaim storage space within the object store, and in some cases lower the related expense. Use the Cloud Delete page to schedule cloud deletions. Panzura Storage Controller | Administration Guide 90 Chapter 3 | Maintenance Operations To schedule cloud deletions: 1. Select checkboxes for days of the week and time of day. 2. Choose one of the following actions: — Apply to save the configuration and start the deletion schedule. — Save to save without starting the schedule. Image Upgrade X Maintenance > Image Upgrade Use this page to upgrade the controller manually to a specific image. New OS images are available from Panzura support. For information on enabling automated updates, see “Support” on page 92. To manually upgrade the system image: 1. Download the image from Panzura to your local network. 2. Click Browse and navigate to the image file. 3. Click Open or Save (depending on your browser). 4. Click Upgrade. Panzura Storage Controller | Administration Guide 91 Chapter 3 | Maintenance Operations Reboot X Maintenance > Reboot Use this page to reboot the controller. When you reboot the controller you have the option to specify a particular software image to use on subsequent reboots of the system. If you have a new version of PZOS that you want to use, make sure that you select it before rebooting. To reboot the system: 1. Select the image to use upon reboot. 2. Click Reboot. Support X Maintenance > Support Use this page to perform the following operations: Enable automated system image updates. (To manually upgrade the controller, see “Image Upgrade” on page 91.) Enable automated event log export to Panzura. Export packet capture files. Table 28 Support Operations Item Description Automatically Send Logs to If you enable this option and click Save, then each night the controller Panzura Support and Check sends the event log to Panzura for analysis . for New Operating System When there is an operating system update, the new version is automati‐ Upgrades cally downloaded to the controller. When you are ready to install the upgrade, choose Maintenance > Reboot, specify the new version, and click Reboot. Download support log If you generated a packet capture on the Maintenance > Diagnostics page, click Download Support Log to download and save a copy of the logfile to your desktop (file name panzura.support). If requested, send this logfile to Panzura Support. click this button to save the capture and then click Save to save the file to your local system so you can send it to Panzura. See “Diagnostics” on page 77 for instructions on taking packet captures. Panzura Storage Controller | Administration Guide 92 Chapter 3 | Maintenance Operations Table 28 Support Operations (continued) Item Description Support access Select a support assistance option and click Save to enable automated remote network support and monitoring. Options include: • Disabled—Remote support access is not permitted. • Limited Access—Panzura support staff has limited remote access to the system and ability to perform a reduced set of remote diagnostic functions. The Panzura staff cannot see any user data, file systems, or the full CLI command set. • Full Access—Panzura support staff has full remote access to the system to perform the needed maintenance and troubleshooting operations using the full set of CLI and shell tools in the system, all alert informa‐ tion, error logs, and system logs. The file system and all data is accessi‐ ble and Panzura support can even remotely access the WebUI, console and Dashboard if approval is given by the customer. Password X Maintenance > Password The controller supports the following types of administrator accounts: Admin—Full read‐write access to the Panzura controller and all Web UI pages. Restricted user— Read‐only access. Can view only the Dashboard tab. Panzura recommends changing the passwords to prevent unauthorized access. Use the Password page to reset the passwords. Table 29 Password Settings Item Description Change Password for Admin Enter and confirm the new password for the administrative user, and click Save Password. Default is admin. Change Password for Restricted Users Enter and confirm the new password for the user account, and click Save Password. Default is user. Panzura Storage Controller | Administration Guide 93 Chapter 3 | Maintenance Operations Advanced X Maintenance > Advanced Use this page to reset and clean up the system, take snapshots, and recover using snapshots. Caution Contact Panzura Support before performing any of the operations on this page. Table 30 Advanced Operations Item Description Reset Configuration to Fac‐ Resets all system values to factory defaults. Stops all read/write operations tory Defaults on the controller, purges all data from the controller, clears all reporting statistics, deletes the configuration information, and resets the system to factory defaults. Delete all Storage and Clear Stops all read/write operations on the controller, purges all data from the Stats controller, and clears all reporting statistics. The system reboots, stopping all read‐write operations. Power Off Halts the controller and turns the power off. Restore local file system Restores the file system on this controller with the file system in the cloud storage. The controller reboots and then recovers the metadata from the cloud storage backend. You can choose to recover to the most current state of the file system, or to recover to the state of the file system as captured in a specific snapshot. See “Snapshot Manager” on page 64 for snapshot names. Generate configuration file Causes the master controller to create a new configuration file that the for master‐subordinate subordinate controllers can synchronize to. configuration sync Remove cloud controller Use this option to remove a controller if an error was made when the con‐ troller was added to CloudFS. Use this option only if the controller to be removed has never been active. Select the controller and click Remove. If you need to remove a controller under any other circumstances, contact Panzura Technical Support. Panzura Storage Controller | Administration Guide 94 A Setting Up Gray‐X The Gray‐X feature allows Windows users to determine if a file is not stored in their local controller’s disk cache, and therefore will take some time to open. This feature is especially useful if the user is working with large files that are not frequently accessed and therefore might not be in the local disk cache. This feature is available only on Windows. When you open a folder in Windows File Explorer, the Panzura Storage Controller determines whether all file blocks are resident locally in cache. If any blocks are missing from cache, a gray X is displayed in the File Explorer window. Gray‐X is disabled by default. When enabled, the Gray‐X status is displayed in the Window Explorer file listing. Figure 38 Gray‐X Indicators Enable or disable the Gray‐X feature 1. Log in to the admin UI to the controller, and open the Maintenance tab. 2. Under Diagnostic Tools, select cifs‐add‐gcfg and do either of the following: — To enable the Gray‐x feature, enter the value pz_replock check blocks = yes and click Run. — To disable the Gray‐X feature, enter the value pz_replock check blocks = no and click Run. Reboot is not required. Panzura Storage Controller | Administration Guide 95 B Antivirus and Malware Scanning This appendix describes how to configure McAfee VirusScan Enterprise and Symantec Protection Engine for antivirus and malware scanning. McAfee VirusScan Enterprise 8.8 with VirusScan Enterprise for Storage You can configure a controller to use McAfee VirusScan Enterprise (VSE) 8.8 for antivirus and malware scanning. When installing the ICAP license on the controller, you are prompted for configuration information, as shown in the following figure. Figure 39 Panzura ICAP Settings for McAfee VSE 8.8 with VirusScan Enterprise for Storage 1.1 Enter the IP address of the McAfee scanner into the Hostname setting of the ICAP license. No other setting changes are required. If you have multiple scanners and want to load balance between them, enter the IP addresses in the Hostname setting as a comma‐separated list. By default, the ICAP license scans files when a read or write occurs. If you do not want to scan on writes, enter no for Scan on Write. After the settings are configured, select the checkbox for the ICAP license and then activate the license at the top of the License Manager page. This will enable virus scanning immediately. If you need to change the settings later, enter new values and click Activate Selected at the top of the License Manager page. It is not necessary to deactivate the license to make configuration changes. Panzura Storage Controller | Administration Guide 96 Appendix B | Symantec Protection Engine for Network Attached Storage 7.5 You can configure a controller to use Symantec Protection Engine for antivirus and malware scanning. When installing the ICAP license on the controller, you are prompted for configuration information, as shown in the following figure. Figure 40 Panzura ICAP Settings for Symantec Protection Engine for Network Attached Storage 7.5 Enter the IP address of the Symantec scanner into the Hostname setting of the ICAP license and verify that Deny on Error is set to no. If you have multiple scanners and want to load balance between them, enter the IP addresses in the Hostname setting as a comma‐separated list. By default, the ICAP license scans files when a read or write occurs. If you do not want to scan on writes, enter no for Scan on Write. After the settings are configured, select the checkbox for the ICAP license and then activate the license at the top of the License Manager page. This will enable virus scanning immediately. If you need to change the settings later, enter new values and click Activate Selected at the top of the License Manager page. It is not necessary to deactivate the license to make configuration changes. Panzura Storage Controller | Administration Guide 97 C Creating A Microsoft Azure Storage Container This appendix shows how to create a storage container for Microsoft Azure. Set up a Microsoft Azure account 1. To sign up for Microsoft Azure, go to http://azure.microsoft.com/en‐us/ and follow the instructions for a free trial. 2. Sign in and click MY ACCOUNT at the top of the page. 3. Select Management portal and click Storage on the left. Follow the instructions to create a storage account. When the account is created, the status will be online. 4. Click the name of the storage account you created. 5. Select Containers > Create a Container. 6. After creating the container, select Manage Access Keys. The primary access key is needed for the Panzura Licensing. Set up the Panzura License Open the License Manager page in the Panzura controller Web UI and specify the following settings: Hostname: Always use Windows.net Path: User‐specified path. Storage Account Name: User‐specified name to identify the account. Primary Access Key: Get from Manage Access Keys – Use Primary Access Key. Container: User‐specified container name. Panzura Storage Controller | Administration Guide 98 Appendix C | Test Connectivity Open the Maintenance > Diagnostics page in the Web UI and use the cloud‐connect‐test command to check connectivity to Microsoft Azure. Panzura Storage Controller | Administration Guide 99
© Copyright 2026