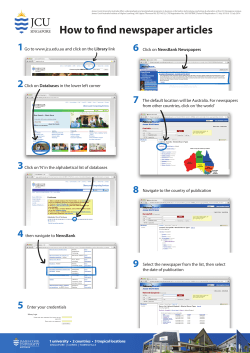
Sample Report Database Security Sample
Sa Database Security Sample le mp Re Note : This sample report does not contain actual data. The data is fictional and fictional names are used throughout this report. po COPIES AND COPYRIGHT • As always, the IgniteiConsult users are welcome to an unlimited number of copies of the materials contained within this sample. Furthermore, the IgniteiConsult users may copy any graphic herein for their own internal purpose. Ignite Intelligence requests only that IgniteiConsult users retain the copyright mark on all pages produced unless you have purchased IgniteiConsult product or SaaS usage time. Please contact the Support Center at +61 466 392 338 for any help we may provide. • The pages herein are the property of Ignite Intelligence. Beyond the samples, no copyrighted materials of Ignite Intelligence may be reproduced without prior approval, unless you have purchased IgniteiConsult product or SaaS usage time. rt LEGAL CAVEAT • Ignite Intelligence has worked to ensure the accuracy of the information it provides to the users of IgniteiConsult. This report relies upon data obtained from many sources, however, Ignite Intelligence cannot guarantee the accuracy of the information or its analysis in all cases. • Furthermore, Ignite Intelligence is not engaged in rendering legal, accounting, or other professional services, unless paid for. Its reports should not be construed as professional advice on any particular set of facts or circumstances. Members requiring such services are advised to consult an appropriate professional in Ignite Intelligence. • Neither Ignite Intelligence nor its software/programs are responsible for any claims or losses that may arise from a) any errors or omissions in their reports, whether caused by Ignite Intelligence by its sources, or b) reliance upon any recommendation made by IgniteiConsult. ROADMAP FOR THIS SAMPLE Sa OVERVIEW OF DATABASE SECURITY DIAGNOSTIC mp About the Diagnostic The Database (DB) Security Diagnostic benchmarks the key competencies of an organization that characterize the best DB security experts. The results provide a baseline for measuring team performance, identify areas for development, and link development opportunities to the corresponding resources to drive team performance improvement. Participants A comprehensive team effectiveness evaluation is based on the feedback from a team of DB security experts and their Group Leader who completed the assessment. le What you will find in this Report: 1. An evaluation of DB security skill maturity in terms of Key Performance Indicators (KPI’s). 2. The areas of largest priority misalignment between the desired and actuals in terms of Performance Spots (PS’s). 3. The areas where the DB group could change involvement at an atomic level in terms of Performance Factors (PF’s). 4. Process measures and health report and implementation guidelines in terms of Recommendations to support DB security skills development. Efficiency Effectiveness Adaptability Re Process Metrics Error Index Process Metrics 76.76% 63.0% 64.13% 82.94% Benchmarks 90% 97% 88% 99% rt po Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence Page 2 of 13 ROADMAP FOR THIS SAMPLE Sa DATABASE SECURITY HIGH-LEVEL PROCESS HEALTH REPORT Strategic Drivers mp Aggregate Access Rights - An electronic payment processor was auditing their database for PCI compliance and discovered that ATM and PIN numbers were being stolen. Detailed logs from Imperva Secure Database Activity Monitoring helped track down and apprehend the criminals. The company now generates alerts on suspicious database access to sensitive data. Scan for Vulnerabilities - Failing to safeguard databases that store sensitive data can cripple your operations, result in regulatory violations, and destroy your brand. Understanding the top database threats and implementing the solutions outlined in IgniteiConsult will enable you to recognize when you’re vulnerable or being attacked, maintain security best practices, and ensure that your most valuable assets are protected. Discover Database Servers - Databases have the highest rate of breaches among all business assets, according to the 2012 Verizon Data Breach Report. Verizon reported that 96% of records breached are from databases, and the Open Security Foundation revealed that 242.6 million records were potentially compromised in 2012. le Detect unusual access activity - The reason databases are targeted is quite simple; databases are at the heart of any organization,storing customer records and other confidential business data. But why are databases so vulnerable to breaches. One reason is that organizations are not protecting these assets well enough. According to IDC, less than 5% of the $27 billion spent in 2011 on security products directly addressed data center security. When hackers and malicious insiders gain access to sensitive data, they can quickly extract value,inflict damage, or impact business operations. In addition to financial loss or reputation damage, breaches can result in regulatory violations, fines, and legal fees. However, the good news is that the vast majority of incidents – more than 97% according to the Online Trust Alliance (OTA) in 2013 – could have been prevented by implementing simple steps and following best practices and internal controls. High-level Process Health Measures Benchmarks Discovery and Assessment locate where database vulnerabilities and critical data reside. 9.00 9.0 User Rights Management identifies excessive rights over sensitive data. 7.19 9.0 Monitoring and Blocking protect databases from attacks, data loss and theft. 6.65 9.0 Auditing - helps demonstrate compliance with industry regulations. 7.10 9.0 Data Protection - ensures data integrity and confidentiality. 9.90 9.0 Non-Technical Security - instills and reinforces a culture of security awareness and preparedness. 5.80 9.0 Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence rt Key Performance Indicators po Re Key Performance Indicators Health Measures Page 3 of 13 DATABASE SECURITY DETAILED PROCESS HEALTH REPORT Key Performance Spots Health Measures Key Performance Indicators Sa High-level Performance Benchma User-set Process Health rks values Spots Measures Analyze Discovery Results. 10.70 9.0 6.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Analyze Risk and Prioritize Remediation Efforts. 12.00 9.0 9.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Calculate Risk Scores. 9.80 9.0 7.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Discover Database Servers. 12.00 9.0 9.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Identify Compromised Endpoints. 6.00 9.0 4.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Identify and Classify Sensitive Data. 5.00 9.0 8.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Mitigate Vulnerabilities. 6.33 9.0 9.0 Discovery and Assessment - locate where database vulnerabilities and critical data reside. Scan for Vulnerabilities. 10.20 9.0 User Rights Management identifies excessive rights over sensitive data. Aggregate Access Rights. 1.60 9.0 User Rights Management identifies excessive rights over sensitive data. Enrich Access Rights Information. 5.00 9.0 User Rights Management identifies excessive rights over sensitive data. Extract Real User Identity. 11.60 9.0 5.0 User Rights Management identifies excessive rights over sensitive data. Identify and Remove Excessive Rights. 6.17 9.0 4.0 User Rights Management identifies excessive rights over sensitive data. Review and Approve/Reject Individual User Rights. 11.60 9.0 5.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Block Malicious Web Requests. 3.00 9.0 9.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Detect Unusual Access Activity. 6.12 9.0 5.0 1.0 8.0 7.0 © 2013-14 | Ignite Intelligence rt po 28/03/2014 2.03 PM Re Report generated date & time: le mp Discovery and Assessment - locate where database vulnerabilities and critical data reside. Page 4 of 13 Key Performance Indicators High-level Performance Benchma User-set Process Health rks values Spots Measures Impose Connection Controls. 2.00 9.0 9.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Monitor Local Database Activity. 8.40 9.0 3.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Real-Time Alerting and Blocking. 4.33 9.0 9.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Response Timing. 11.90 9.0 8.0 Monitoring and Blocking - protect databases from attacks, data loss and theft. Validate Database Protocols. 10.80 9.0 7.0 Auditing - helps demonstrate compliance with industry regulations. Automate Auditing with a DAP Platform. 10.50 9.0 4.0 Auditing - helps demonstrate compliance with industry regulations. Capture Detailed Transactions. 8.80 9.0 7.0 Auditing - helps demonstrate compliance with industry regulations. Generate Reports for Compliance and Forensics. 2.00 9.0 9.0 Data Protection ensures data integrity and confidentiality. Archive External Data. 8.00 9.0 9.0 Data Protection ensures data integrity and confidentiality. Encrypt Databases. 11.80 9.0 7.0 Non-Technical Security - instills and reinforces a culture of security awareness and preparedness. Cultivate Experienced Security Professionals. 1.00 9.0 Non-Technical Security - instills and reinforces a culture of security awareness and preparedness. Educate Your Workforce. 10.60 9.0 Sa Monitoring and Blocking - protect databases from attacks, data loss and theft. le mp Re 9.0 5.0 po DATABASE SECURITY PROCESS KEY CHALLENGES rt Key Challenges 1 DB administrator has only a rudimentary understanding of the security measures offered by your DBMS. 2 SQL Injection attacks pose tremendous risks to web applications that depend upon a database backend. 3 Organization trusts employees with protecting sensitive information. On the contrary, industry analysts say 'never'. 4 Security issues are often neglected in the implementation of data warehouses. Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence Page 5 of 13 ROADMAP FOR THIS SAMPLE Sa mp DATABASE SECURITY PROCESS GAPS & RECOMMENDATIONS Process Recommendations List for the Report Key Performance Indicators Discovery and Assessment - locate where database vulnerabilities and critical data reside. Process Gaps Recommendations le Organization is struggling to maintain an accurate inventory of their databases and the critical data objects contained within them. Forgotten databases may contain sensitive information, and new databases can emerge e.g., in application testing environments without visibility to the security team.. 1.Sensitive data in the databases will be exposed to threats if the required controls and permissions are not implemented. Hence an inventory of all databases with data objects should be maintained. 2. Invalid or forgotten database inventory also should be maintained.. Discovery and Assessment - locate where database vulnerabilities and critical data reside. It is common in this organization to find vulnerable and un-patched databases, or discover databases that still have default accounts and configuration parameters. Attackers may know how to exploit these vulnerabilities to launch attacks against your organization. According to the 2012 Independent Oracle User Group (IOUG), 28 percent of Oracle users have never applied a Critical Patch Update or don't know whether they've done so. Another 10 percent take a year or longer to apply their patches.. 1.Stay on-top of maintaining database configurations even when patches are available.It generally takes months to patch databases once a patch is available. During the time your databases are un-patched,they remain vulnerable. Discovery and Assessment - locate where database vulnerabilities and critical data reside. It is common in this organization to find vulnerable and un-patched databases, or discover databases that still have default accounts and configuration parameters. Attackers may know how to exploit these vulnerabilities to launch attacks against your organization. According to the 2012 Independent Oracle User Group (IOUG), 28 percent of Oracle users have never applied a Critical Patch Update or don't know whether they've done so. Another 10 percent take a year or longer to apply their patches.. 1.Stay on-top of maintaining database configurations even when patches are available.It generally takes months to patch databases once a patch is available. During the time your databases are un-patched,they remain vulnerable. Discovery and Assessment - locate where database vulnerabilities and critical data reside. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. Re Discovery and Assessment - locate where database vulnerabilities and critical data reside. Cybercriminals, state-sponsored hackers, and spies use advanced attacks that blend multiple tactics such as spear phishing emails and malware to penetrate your organization and steal sensitive data. You could be unaware that malware has infected your device, so legitimate users become a conduit for these groups to access your networks and sensitive data. Discovery and Assessment - locate where database vulnerabilities and critical data reside. It is common in this organization to find vulnerable and un-patched databases, or discover databases that still have default accounts and configuration parameters. Attackers may know how to exploit these vulnerabilities to launch attacks against your organization. According to the 2012 Independent Oracle User Group (IOUG), 28 percent of Oracle users have never applied a Critical Patch Update or don't know whether they've done so. Another 10 percent take a year or longer to 28/03/2014 2.03 PM 1. Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. 1.Sensitive data in the databases will be exposed to threats if the required controls and permissions are not implemented. Hence an inventory of all databases with data objects should be maintained. 2. Invalid or forgotten database inventory also should be maintained.. rt Organization is struggling to maintain an accurate inventory of their databases and the critical data objects contained within them. Forgotten databases may contain sensitive information, and new databases can emerge e.g., in application testing environments without visibility to the security team.. 2.If a vulnerability is discovered and the database vendor hasn't released a patch, a virtual patching solution should be used. Applying virtual patches will block attempts to exploit vulnerabilities without requiring actual patches or changes to the current configuration of the server.Virtual patching will protect the database from exploit attempts until the patch is deployed.Again,focus on patching highrisk vulnerabilities that can facilitate DoS and SQL injection attacks. po Discovery and Assessment - locate where database vulnerabilities and critical data reside. Report generated date & time: 2.If a vulnerability is discovered and the database vendor hasn't released a patch, a virtual patching solution should be used. Applying virtual patches will block attempts to exploit vulnerabilities without requiring actual patches or changes to the current configuration of the server.Virtual patching will protect the database from exploit attempts until the patch is deployed.Again,focus on patching highrisk vulnerabilities that can facilitate DoS and SQL injection attacks. Identify malware-infected hosts so that you can prevent these devices from accessing sensitive information in databases as well as unstructured data stores. Once you identify compromised devices, you should apply controls to sensitive data to restrict those devices from accessing and exfiltrating data. 1.Stay on-top of maintaining database configurations even when patches are available.It generally takes months to patch databases once a patch is available. During the time your databases are un-patched,they remain vulnerable. 2.If a vulnerability is discovered and the database vendor hasn't released a patch, a virtual patching solution should be used. Applying virtual patches will block attempts to exploit vulnerabilities without requiring actual patches or changes to the current configuration of the server.Virtual patching will protect the database from exploit attempts until the patch is deployed.Again,focus on patching high- © 2013-14 | Ignite Intelligence Page 6 of 13 Key Performance Indicators Process Gaps Discovery and Assessment - locate where database vulnerabilities and critical data reside. Recommendations apply their patches.. risk vulnerabilities that can facilitate DoS and SQL injection attacks. Organization is struggling to maintain an accurate inventory of their databases and the critical data objects contained within them. Forgotten databases may contain sensitive information, and new databases can emerge e.g., in application testing environments without visibility to the security team.. Analysis records to be created based on data stakeholder and application stakeholder perspective. Sa Organization is struggling to maintain an accurate inventory of their databases and the critical data objects contained within them. Forgotten databases may contain sensitive information, and new databases can emerge e.g., in application testing environments without visibility to the security team. Discovery and Assessment - locate where database vulnerabilities and critical data reside. It is common in this organization to find vulnerable and un-patched databases, or discover databases that still have default accounts and configuration parameters. Attackers may know how to exploit these vulnerabilities to launch attacks against your organization. According to the 2012 Independent Oracle User Group (IOUG), 28 percent of Oracle users have never applied a Critical Patch Update or don't know whether they've done so. Another 10 percent take a year or longer to apply their patches.. Discovery and Assessment - locate where database vulnerabilities and critical data reside. Discovery and Assessment - locate where database vulnerabilities and critical data reside. mp Discovery and Assessment - locate where database vulnerabilities and critical data reside. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. 1.Sensitive data in the databases will be exposed to threats if the required controls and permissions are not implemented. Hence an inventory of all databases with data objects should be maintained. 2. Invalid or forgotten database inventory also should be maintained.. 1.Stay on-top of maintaining database configurations even when patches are available.It generally takes months to patch databases once a patch is available. During the time your databases are un-patched,they remain vulnerable. 2.If a vulnerability is discovered and the database vendor hasn't released a patch, a virtual patching solution should be used. Applying virtual patches will block attempts to exploit vulnerabilities without requiring actual patches or changes to the current configuration of the server.Virtual patching will protect the database from exploit attempts until the patch is deployed.Again,focus on patching highrisk vulnerabilities that can facilitate DoS and SQL injection attacks. 1. Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection. Discovery and Assessment - locate where database vulnerabilities and critical data reside. Cybercriminals, state-sponsored hackers, and spies use advanced attacks that blend multiple tactics such as spear phishing emails and malware to penetrate your organization and steal sensitive data. You could be unaware that malware has infected your device, so legitimate users become a conduit for these groups to access your networks and sensitive data. Identify malware-infected hosts so that you can prevent these devices from accessing sensitive information in databases as well as unstructured data stores. Once you identify compromised devices, you should apply controls to sensitive data to restrict those devices from accessing and exfiltrating data. Discovery and Assessment - locate where database vulnerabilities and critical data reside. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. le There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what. Re 1. Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what. User Rights Management - identifies excessive rights over sensitive data. Users may abuse legitimate database privileges for unauthorized purposes. Once data reach a client machine, the data then becomes susceptible to a wide variety of possible breach scenarios. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection. 1. Aggregate access rights, enrich access rights information based on careful scrutiny. Remove excess rights. po Discovery and Assessment - locate where database vulnerabilities and critical data reside. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 2. Maintain real-time alerting & blocking. 3. Detect unusual access activity.. 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. rt Staff are granted database privileges that exceed the User Rights Management requirements of their job function, and these privileges - identifies excessive can be abused. rights over sensitive data. There are no records of analysis of user privileges or who has what privilege and why.. 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties issues, and remove excessive rights that are not required for users to do their job. Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence Page 7 of 13 Key Performance Indicators Process Gaps Recommendations Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. Sa User Rights Management - identifies excessive rights over sensitive data. Users may abuse legitimate database privileges for unauthorized purposes. Once data reach a client machine, the data then becomes susceptible to a wide variety of possible breach scenarios. 1. Aggregate access rights, enrich access rights information based on careful scrutiny. Remove excess rights. 2. Maintain real-time alerting & blocking. 3. Detect unusual access activity.. 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. mp 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. Staff are granted database privileges that exceed the User Rights Management requirements of their job function, and these privileges - identifies excessive can be abused. rights over sensitive data. There are no records of analysis of user privileges or who has what privilege and why.. le 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties issues, and remove excessive rights that are not required for users to do their job. Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. Re Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples User Rights Management of regulations with clear database audit requirements. - identifies excessive Organization uses native audit tools provided by your rights over sensitive database vendors or rely on ad-hoc and manual data. solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. User Rights Management - identifies excessive rights over sensitive data. Users may abuse legitimate database privileges for unauthorized purposes. Once data reach a client machine, the data then becomes susceptible to a wide variety of possible breach scenarios. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. Identify malware-infected hosts so that you can prevent these devices from accessing sensitive information in databases as well as unstructured data stores. Once you identify compromised devices, you should apply controls to sensitive data to restrict those devices from accessing and exfiltrating data. rt Cybercriminals, state-sponsored hackers, and spies use advanced attacks that blend multiple tactics such as spear phishing emails and malware to penetrate your organization and steal sensitive data. You could be unaware that malware has infected your device, so legitimate users become a conduit for these groups to access your networks and sensitive data. 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. po User Rights Management - identifies excessive rights over sensitive data. 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. 1. Aggregate access rights, enrich access rights information based on careful scrutiny. Remove excess rights. 2. Maintain real-time alerting & blocking. 3. Detect unusual access activity.. Staff are granted database privileges that exceed the User Rights Management requirements of their job function, and these privileges - identifies excessive can be abused. rights over sensitive data. There are no records of analysis of user privileges or who has what privilege and why.. Report generated date & time: 28/03/2014 2.03 PM 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, © 2013-14 | Ignite Intelligence Page 8 of 13 Key Performance Indicators Process Gaps Recommendations CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. Sa 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties issues, and remove excessive rights that are not required for users to do their job. Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. mp 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. le Staff are granted database privileges that exceed the User Rights Management requirements of their job function, and these privileges - identifies excessive can be abused. rights over sensitive data. There are no records of analysis of user privileges or who has what privilege and why.. 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties issues, and remove excessive rights that are not required for users to do their job. Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. Monitoring and Blocking - protect databases from attacks, data loss and theft. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. Cybercriminals, state-sponsored hackers, and spies use advanced attacks that blend multiple tactics such as spear phishing emails and malware to penetrate your organization and steal sensitive data. You could be unaware that malware has infected your device, so legitimate users become a conduit for these groups to access your networks and sensitive data.. 1.Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. po Monitoring and Blocking - protect databases from attacks, data loss and theft. Re 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. Identify malware-infected hosts so that you can prevent these devices from accessing sensitive information in databases as well as unstructured data stores. Once you identify compromised devices, you should apply controls to sensitive data to restrict those devices from accessing and exfiltrating data. 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. Staff are granted database privileges that exceed the requirements of their job function, and these privileges can be abused. There are no records of analysis of user privileges or who has what privilege and why.. rt Monitoring and Blocking - protect databases from attacks, data loss and theft. 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence Page 9 of 13 Key Performance Indicators Process Gaps Recommendations issues, and remove excessive rights that are not required for users to do their job. Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. Sa Monitoring and Blocking - protect databases from attacks, data loss and theft. Monitoring and Blocking - protect databases from attacks, data loss and theft. Users may abuse legitimate database privileges for unauthorized purposes. Once data reach a client machine, the data then becomes susceptible to a wide variety of possible breach scenarios. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples of regulations with clear database audit requirements. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. 1.Extract Real User Identity: Leverage solutions that correlate user information with database transactions, also known as Universal User Tracking, or UUT. The resulting audit logs can then include unique application user names. 2. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection.. 1. Extract Real User Identity: Leverage solutions that correlate user information with database transactions, also known as Universal User Tracking, or UUT. The resulting audit logs can then include unique application user names. 2. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection.. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. Organization uses native audit tools provided by your database vendors or rely on ad-hoc and manual solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. Users may abuse legitimate database privileges for unauthorized purposes. Once data reach a client machine, the data then becomes susceptible to a wide variety of possible breach scenarios. 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. po Monitoring and Blocking - protect databases from attacks, data loss and theft. There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what. 1. Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. Re Monitoring and Blocking - protect databases from attacks, data loss and theft. There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what.. le Monitoring and Blocking - protect databases from attacks, data loss and theft. 2.Maintain real-time alerting & blocking. 3. Detect unusual access activity.. mp Monitoring and Blocking - protect databases from attacks, data loss and theft. 1.Aggregate access rights, enrich access rights information based on careful scrutiny. Remove excess rights. 1.Aggregate access rights, enrich access rights information based on careful scrutiny. Remove excess rights. 2.Maintain real-time alerting & blocking. 3. Detect unusual access activity.. Monitoring and Blocking - protect databases from attacks, data loss and theft. Report generated date & time: 28/03/2014 2.03 PM Staff are granted database privileges that exceed the requirements of their job function, and these privileges can be abused. rt Monitoring and Blocking - protect databases from attacks, data loss and theft. A successful SQL injection attack can give someone unrestricted access to an entire database. SQL injection involves inserting (or injecting) unauthorized or malicious database statements into a vulnerable SQL data channel such as a Web application or stored procedure. If these injected statements are executed by the database, critical data stores can be viewed, copied, and altered. 1.Scan for Vulnerabilities : Understanding vulnerabilities that expose databases to SQL injection is essential. Malware may be looking to exploit known database vulnerabilities, making un-patched databases an easy target. 2. Weak authentication rules can enable a DoS attack by granting access to a database without needing a password. Use vulnerability assessment tools to detect security vulnerabilities, misconfigurations, and missing vendor patches. 3. Assessments should use industry best practices for database security, such as DISA STIG and CIS benchmarks.. 1.Privilege control mechanisms for job roles to be well defined or maintained. As a result, users may not be granted generic or default access privileges that far exceed their specific job requirements. This removes unnecessary risk. © 2013-14 | Ignite Intelligence Page 10 of 13 Key Performance Indicators Process Gaps Recommendations 2. Aggregate Access Rights: Scan databases for both granted and privileged user rights and extract details such as the actual access right (e.g. SELECT, DELETE, CONNECT, etc), who granted them, who received those rights, and objects to which rights have been granted. Aggregating user rights into a single repository helps streamline the reporting and analysis of user access to sensitive data. Sa There are no records of analysis of user privileges or who has what privilege and why.. Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples of regulations with clear database audit requirements. Organization uses native audit tools provided by your database vendors or rely on ad-hoc and manual solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. 28/03/2014 2.03 PM 1. Extract Real User Identity: Leverage solutions that correlate user information with database transactions, also known as Universal User Tracking, or UUT. The resulting audit logs can then include unique application user names. 2. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection.. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. rt Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples of regulations with clear database audit requirements. Organization uses native audit tools provided by your database vendors or rely on ad-hoc and manual solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. Report generated date & time: 2. Calculate Risk Scores : Score risks based on the severity of vulnerabilities and the sensitivity of the data. Severity values should be based on known systems such as the Common Vulnerability Scoring System (CVSS). Risk scores help prioritize risk, manage, and research vulnerabilities. For example, higher risk scores would relate to SQL injection.. po Auditing - helps demonstrate compliance with industry regulations. There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what. 1. Extract Real User Identity: Leverage solutions that correlate user information with database transactions, also known as Universal User Tracking, or UUT. The resulting audit logs can then include unique application user names. Re Auditing - helps demonstrate compliance with industry regulations. There is no analysis of Discovery Results : There are no mechanisms to determine which databases that store sensitive data need to be monitored, and who should have access to what. le Monitoring and Blocking - protect databases from attacks, data loss and theft. 4. Identify and Remove Excessive Rights and Dormant Users: Identify users that have too many privileges and users who don't use their privileges. This helps determine if user access rights are appropriately defined, find separation of duties issues, and remove excessive rights that are not required for users to do their job. Hackers use access rights to impersonate users and go after sensitive data stores. Therefore, reducing excessive rights helps protect against malware compromise. 5. Review and Approve/Reject Individual User Rights: Perform an organized review of user rights to determine if they are appropriate. Reviewers should approve or reject rights, or assign them to another for review, and administrators can report on the review process. Conducting organized user rights reviews meets regulatory requirements and reduces risk by ensuring that user privileges are granted on a need-to-know basis.. mp Monitoring and Blocking - protect databases from attacks, data loss and theft. 3. Enrich Access Rights Information with User Details and Data Sensitivity: Adding information related to user roles and their database behavior adds considerable value to user rights analysis and helps zero-in on the abuse of privileges. Collect and append contextual details to user rights information including the user name, department, database object sensitivity, and last time accessed. This allows you to focus your analysis on the access rights that represent the highest business risk. 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. © 2013-14 | Ignite Intelligence Page 11 of 13 Key Performance Indicators Process Gaps Recommendations For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. Sa Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples of regulations with clear database audit requirements. Auditing - helps demonstrate compliance with industry regulations. mp Organization uses native audit tools provided by your database vendors or rely on ad-hoc and manual solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. Organization uses native audit tools provided by your database vendors or rely on ad-hoc and manual solutions. These approaches do not record details necessary to support auditing, attack detection, and forensics. Furthermore, native database audit mechanisms are notorious for consuming CPU and disk resources forcing many organizations to scale back or eliminate auditing altogether. Finally, most native audit mechanisms are unique to a database server platform. For example, Oracle logs are different from MS-SQL, and MS-SQL logs are different form DB2. For organizations with heterogeneous database environments, this imposes a significant obstacle to implementing uniform, scalable audit processes.. Backup storage media is often completely unprotected from attack. As a result, numerous security breaches can be involved in the theft of database backup disks and tapes. Furthermore, failure to audit and monitor the activities of administrators who have low-level access to sensitive information can put your data at risk. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. 4. Finally, users with administrative access to the database (either legitimately or maliciously obtained) to be limited and closely monitored so that they don't turn off native database auditing to hide fraudulent activity. 5. Audit duties should ideally be separate from both database administrators and the database server platform to ensure strong separation of duties policies.. Taking the appropriate measures to protect backup copies of sensitive data and monitoring your most highly privileged users is not only a data security best practice, but also mandated by many regulations. 1.Cultivate Experienced Security Professionals: To defend against a growing array of internal and external threats, hire information security personnel that are well versed in IT Security and have experience implementing, administering, and monitoring security solutions. Ongoing education and training are also important for growing deeper security knowledge and skills. Consider outside IT security and specialists to help with implementation, conduct security assessments and penetration tests, and provide training and support for your administrators. 2. Educate Your Workforce: Train your workforce on risk mitigation techniques including how to recognize common cyber-threats (e.g. a spear-phishing attack), best practices around Internet and email usage, and password management. Failure to enforce training and create a security conscious work culture increases the chances of a security breach. The end result is well-informed users who are trained to securely function when connected to key systems.. rt Non-Technical Security instills and reinforces a culture of security awareness and preparedness. Internal security controls are not keeping pace with data growth and your organization is ill-equipped to deal with a security breach.Often this is due to the lack of expertise required to implement security controls, policies, and training.According to PWC's 2012 Information Security Breaches Survey, 75% of the organizations surveyed experienced staff-related breaches when a security policy was poorly understood and 54% of small businesses did not have a program for educating their staff about security risks. 28/03/2014 2.03 PM 3. Reporting, visibility, and forensic analysis are to be promoted with a link to the responsible user. po Non-Technical Security instills and reinforces a culture of security awareness and preparedness. Internal security controls are not keeping pace with data growth and your organization is ill-equipped to deal with a security breach.Often this is due to the lack of expertise required to implement security controls, policies, and training.According to PWC's 2012 Information Security Breaches Survey, 75% of the organizations surveyed experienced staff-related breaches when a security policy was poorly understood and 54% of small businesses did not have a program for educating their staff about security risks. Report generated date & time: 2. When users access the database via enterprise Web applications (such as SAP, Oracle E-Business Suite, or PeopleSoft) there should have the knowledge of what database access activity relates to a specific user instead of all activity being associated with the Web application account name. Re Data Protection ensures data integrity and confidentiality. le Data Protection ensures data integrity and confidentiality. Failure to collect detailed audit records of database activity represents a serious organizational risk on many levels. This weakness (or sometimes non-existent) database audit mechanisms will increasingly find that they are at odds with industry and government regulatory requirements. For example, Sarbanes-Oxley (SOX), which protects against accounting errors and fraudulent practices, and the Healthcare Information Portability and Accountability Act (HIPAA) in the healthcare sector, are just two examples of regulations with clear database audit requirements. 1. Automated recording of database transactions involving sensitive data should be part of any database deployment in the organization. 1.Cultivate Experienced Security Professionals: To defend against a growing array of internal and external threats, hire information security personnel that are well versed in IT Security and have experience implementing, administering, and monitoring security solutions. Ongoing education and training are also important for growing deeper security knowledge and skills. Consider outside IT security and specialists to help with implementation, conduct security assessments and penetration tests, and provide training and support for your administrators. 2. Educate Your Workforce: Train your workforce on risk mitigation techniques including how to recognize common cyber-threats (e.g. a spear-phishing attack), best practices around Internet and email usage, and password management. Failure to enforce training and create a security conscious work culture increases the chances of a security breach. The end result is well-informed users who are trained to securely function when connected to key systems.. © 2013-14 | Ignite Intelligence Page 12 of 13 ROADMAP FOR THIS SAMPLE Sa DATABASE SECURITY PROCESS RISK ANALYSIS mp Process Gaps Severe Risk Items High Risk Items Medium Risk Items Low Risk Items Total Risk Items Discovery and Assessment - locate where database vulnerabilities and critical data reside. 6 6 2 1 15 User Rights Management - identifies excessive rights over sensitive data. 3 2 3 1 9 Monitoring and Blocking - protect databases from attacks, data loss and theft. 2 5 6 0 13 Auditing - helps demonstrate compliance with industry regulations. 0 2 1 0 3 Data Protection - ensures data integrity and confidentiality. 1 1 0 0 2 Non-Technical Security - instills and reinforces a culture of security awareness and preparedness. 0 1 1 0 2 le Key Performance Indicators rt po Re Report generated date & time: 28/03/2014 2.03 PM © 2013-14 | Ignite Intelligence Page 13 of 13
© Copyright 2026