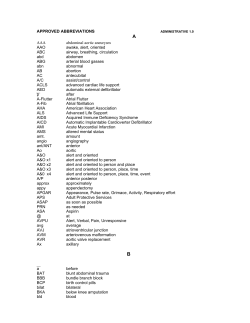
N C V
STANFORD TECHNOLOGY LAW REVIEW VOLUME 16, NUMBER 2 WINTER 2013 NOTE COPYRIGHT VIGILANTISM Rachel Storch* CITE AS: 16 STAN. TECH. L. REV. 453 (2013) http://stlr.stanford.edu/pdf/copyrightvigilantism.pdf ABSTRACT On July 6, 2011, some of the world’s largest entertainment companies, including Disney, Paramount, Warner Brothers, and Universal, as well as the MPAA and RIAA, entered into a historic agreement with the most prominent Internet service providers (ISPs), including AT&T, Verizon, and Time Warner. Their agreement created the Copyright Alert System. Under the system, copyright owners will be able to inform ISPs of the IP addresses of suspected infringers, and ISPs will then act on their own to impose a graduating series of sanctions on their subscribers, up to and including slowing connection speeds or suspending Internet service. ISPs began rolling out Copyright Alert in late 2012 and early 2013. This Note provides one of the first in-depth scholarly treatments of Copyright Alert. The discussion begins with a survey of the circumstances that led to Copyright Alert: clunky copyright laws unsuited to address infringement by individual Internet users coupled with a cultural acceptance or even valorization of piracy. Faced with legal and cultural hurdles to enforcement, copyright owners and ISPs have become vigilantes for their own cause, turning to private enforcement to accomplish what the copyright law could not. The Note moves on to address the strengths and weaknesses of the Copyright Alert System, leading to the conclusion that although a graduated response system can create gains in efficiency, privacy, and fairness over current copyright enforcement, regulatory oversight could help alleviate competency, legitimacy, and implementation problems that will otherwise hinder the sustainability and effectiveness of Copyright Alert. * J.D. Stanford Law School, 2013. The author thanks Peter Menell for his advice, criticism, encouragement, and mentorship on this project. 453 454 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 INTRODUCTION....................................................................................................... 454 I. DARKEST NIGHT: RAMPANT PIRACY AND THE FAILURE OF COPYRIGHT LAW ................................................................................................................. 455 A. The Online Piracy Problem ........................................................................ 456 B. The Procedural Labyrinth of Litigation Against Direct Infringers ............ 457 C. The Secondary Liability Arms Race ........................................................... 460 D. Infringement Culture and Congressional Paralysis ................................... 462 II. THE HERO COPYRIGHT NEEDS: GRADUATED RESPONSE AND COPYRIGHT ALERT .............................................................................................................. 463 A. Graduated Response Abroad...................................................................... 463 B. The American Version: Copyright Alert ..................................................... 465 III. WITH GREAT POWER COMES GREAT RESPONSIBILITY: CHALLENGES TO COPYRIGHT ALERT ........................................................................................... 469 A. The Competence of Private Actors to Enforce Copyright .......................... 469 B. Legitimacy: The Authority of Private Actors to Enforce Copyright ........... 472 C. The Challenges of Enforcing Copyright Alert ............................................ 477 IV. THE HERO COPYRIGHT DESERVES: REGULATORY OVERSIGHT OF GRADUATED RESPONSE .................................................................................... 478 A. The Role of Regulation ............................................................................... 479 B. Choosing an Agency ................................................................................... 481 CONCLUSION .......................................................................................................... 483 INTRODUCTION As a society, we have mixed feelings towards vigilantism. Our popular culture, from comic books to television, is full of heroes standing up to take action against injustice where the law has failed. We revel in our fantasies of superpowered do-gooders who fly over legal bureaucracy to exact violent justice directly upon wrongdoers.1 On the other hand, we detest real-life vigilantes. When neighborhood watchman George Zimmerman shot 17-yearold Trayvon Martin in February 2012, believing him to be a threat, there was widespread public outrage.2 In the copyright world as well, the line between principled self-help and reprehensible extralegal action is a thin one. The copyright law has consistently failed to protect the rights of artists and authors on the Internet, and Congress has been entirely ineffectual in passing better enforcement legislation. In addition, public opinion is hostile toward improved copyright protections. Forsaken by the law, frustrated copyright owners are taking matters into their own hands. The Copyright Alert System, born out of a historic agreement in 2011 between copyright owners and ISPs, is a new breed of private copyright 1. Two of the top four highest-grossing films at the box office in U.S. history were the vigilante superhero films The Avengers and The Dark Knight. See All-Time Box Office: USA, IMDB, http://www.imdb.com/boxoffice/alltimegross (last visited July 1, 2012). 2. See Trayvon Martin Protests—In Pictures, THEGUARDIAN (Apr. 13, 2012, 14:23 EDT), http://www.guardian.co.uk/world/gallery/2012/apr/13/trayvon-martin-killing-protestsjustice. Winter 2013] COPYRIGHT VIGILANTISM 455 enforcement mechanism that will function entirely without state intervention or oversight. Under Copyright Alert, copyright owners will inform ISPs of the IP addresses of alleged copyright infringers, and ISPs will respond with a series of progressively harsher sanctions, ending with the possibility of terminating a user’s Internet service or throttling his or her connection speeds.3 Although Copyright Alert promises faster, more effective enforcement of copyright online, its private contractual foundation makes it costly and difficult to enforce in court. In addition, Copyright Alert faces challenges to its legitimacy and institutional competence. Despite the ease and convenience of leaving copyright enforcement up to private actors, the same rule of law considerations that make us detest armed vigilantes may make it preferable to impose some measure of state oversight on Copyright Alert. This Note outlines the emergence of Copyright Alert and examines possible solutions to its institutional weaknesses. Part I details the failures of copyright law that have made enforcement through state mechanisms impossible. Part II outlines the details of the Copyright Alert System. Part III explores weaknesses in Copyright Alert and the effects that such weaknesses are likely to have on the effectiveness of the system. Part IV proposes oversight by an administrative agency as a remedy to the failings of Copyright Alert. Part V concludes. I. DARKEST NIGHT: RAMPANT PIRACY AND THE FAILURE OF COPYRIGHT LAW Vigilantism is born from a failure of the law. It is only when the established order breaks down that people begin to look for extrajudicial solutions. The turn to private enforcement of copyright is the result of a long, relentless breakdown of public copyright enforcement. Procedural hurdles to direct infringement actions have made it nearly impossible to hold individual Internet users liable for copyright violations. Secondary liability suits against ISPs are hindered by the safe harbors embodied in section 512 of the Digital Millennium Copyright Act (DMCA).4 Perhaps most cripplingly, these legal challenges occur against a cultural backdrop that increasingly accepts or even encourages piracy as an expression of free speech.5 Ever more desperate attempts by the content industry to enable enforcement of their rights have only resulted in negative press and public outrage.6 The spectacular failure of recent legislative reforms in the wake of massive Internet protest7 has left Congress 3. What Is a Copyright Alert?, CENTER FOR COPYRIGHT INFO., http://www.copyrightinformation.org/alerts (last visited July 1, 2012). 4. 17 U.S.C. § 512 (2006). 5. See Aaron Swartz, Guerilla Open Access Manifesto, INTERNET ARCHIVE (JULY 2008), http://ia700808.us.archive.org/17/items/GuerillaOpenAccessManifesto/Goamjuly 2008.pdf. 6. See Sarah McBride & Ethan Smith, Music Industry to Abandon Mass Suits, WALL ST. J. (Dec. 19, 2008), http://online.wsj.com/article/SB122966038836021137.html. 7. Julianne Pepitone, SOPA and PIPA Postponed Indefinitely After Protests, 456 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 paralyzed, politically incapable of pursuing new legislative avenues for enforcement. For all intents and purposes, copyright law has failed rights holders. A. The Online Piracy Problem The degree of online piracy of copyrighted works today is staggering. With the growth of streaming services, direct download sites, cyberlockers, and peerto-peer services such as BitTorrent, the old problem of online piracy has expanded and diversified in new and often unpredictable ways. Peer-to-peer systems especially have become bastions of Internet piracy. One study, based on a sample of 1021 BitTorrent files from the Mainline DHT system, found that 99% of the sample was likely infringing.8 Another study, which used server scrapes to gather information on one thousand BitTorrent transfers, found that 97.9% of non-pornographic torrents were likely infringing.9 Expert witnesses and other consultants have provided similarly overwhelming estimates for other peer-to-peer networks. Dr. Richard P. Waterman is a Professor of Statistics at the Wharton School of the University of Pennsylvania and president of Analytic Business Services, a consulting firm specializing in statistical analysis.10 In Arista Records LLC v. Lime Group LLC, Dr. Waterman testified to his findings that nearly 98.8% of files on the LimeWire peer-to-peer system were copyrighted and likely distributed without authorization.11 In Columbia Pictures Industries, Inc. v. Fung, Dr. Waterman testified for the plaintiffs that approximately 95% of downloads through the Torrentbox and Isohunt sites infringed copyrights.12 The piracy problem is not caused by a few die-hard infringers. The International Federation of the Phonographic Industry estimates that 28% of Internet users access unauthorized content services each month.13 A study by Envisional found that copyrightinfringing exchanges account for more than 17% of all U.S. Internet traffic.14 CNNMONEY (Jan. 20, 2012, 7:54 PM ET), http://money.cnn.com/2012/01/20/technology/ SOPA_PIPA_postponed/index.htm. 8. Ed Felton, Census of Files Available via BitTorrent, FREEDOM TO TINKER (Jan. 29, 2010), http://freedom-to-tinker.com/blog/felten/census-files-available-bittorrent (summarizing research by Sauhard Sahi). 9. Robert Layton & Paul Watters, Investigation into the Extent of Infringing Content on BitTorrent Networks, INTERNET COM. SECURITY LABORATORY 1, 18 (Apr. 2010) http://www.afact.org.au/assets/research/bt_report_final.pdf (excluding pornographic works from conclusions due to uncertainty over infringing status). 10. Arista Records LLC v. Lime Grp. LLC, 784 F. Supp. 2d 398, 412 (S.D.N.Y. 2011). 11. Id. 12. Columbia Pictures Indus., Inc. v. Fung, No. CV 06-5578 SVW(JCx), 2009 WL 6355911, at *4 (C.D. Cal. Dec. 21, 2009). 13. Digital Music Report 2012, INT’L FED’N OF THE PHONOGRAPHIC INDUS. 1, 16 (2012), http://www.ifpi.org/content/library/DMR2012.pdf. 14. Technical Report: An Estimate of Infringing Use of the Internet, ENVISIONAL, 1, 3 Winter 2013] COPYRIGHT VIGILANTISM 457 Although the extent of piracy is massive, there is wide-ranging disagreement about the effects such piracy has on content owners and on creativity in general. A frequently cited study from the Institute for Policy Innovation estimates that copyright piracy costs the United States $58 billion per year in total output and eliminates 373,375 jobs each year.15 However, this study has been criticized for its methodology, including its use of “multiplier effects” to arrive at larger loss estimates.16 A competing study prepared for the Computer and Communications Industry Association attempted to show that losses from piracy are largely offset by economic gains in industries making uncompensated “fair use” of copyrighted material. It found that fair use industries accounted for 16.2% of U.S. GDP in 2007, the year the Institute for Policy Innovation study was published.17 It is beyond the scope of this Note to resolve the long-running debate between Hollywood and Silicon Valley over the economic effects of piracy. It is enough to agree with the U.S. Government Accountability Office that although “it is difficult, if not impossible, to quantify” the economic effects of piracy, “research in specific industries suggest that the problem is sizeable.”18 B. The Procedural Labyrinth of Litigation Against Direct Infringers The Copyright Act contemplates enforcement through lawsuits against individual direct infringers. Section 501 defines an infringer as “Anyone who violates any of the exclusive rights of the copyright owner” and allows “[t]he legal or beneficial owner of an exclusive right under a copyright” to “institute an action for any infringement of that particular right committed while he or she is the owner of it.”19 In the offline world, enforcement against direct infringers is unproblematic. The anonymity of the Internet and the architecture of peer-to-peer networks, however, create frustrating procedural barriers to enforcement. Further complicating the matter, direct lawsuits against online infringers are negatively perceived by the public, who see them as instances of media corporations ganging up against vulnerable consumers to force easy settlements.20 (Jan. 2011), http://documents.envisional.com/docs/Envisional-Internet_Usage-Jan2011.pdf. 15. Stephen E. Siwek, The True Cost of Copyright Industry Piracy to the U.S. Economy, 189 INST. FOR POLICY INNOVATION 1, 11 (2007). 16. See Julian Sanchez, How Copyright Industries Con Congress, CATO AT LIBERTY (Jan. 3, 2012, 3:07 PM), http://www.cato-at-liberty.org/how-copyright-industries-concongress. 17. Thomas Rogers & Andrews Szamosszegi, Fair Use in the U.S. Economy, COMPUTER & COMM. INDUSTRY ASS’N 1, 8 (2010), http://www.ccianet.org/ CCIA/files/ccLibraryFiles/Filename/000000000354/fair-use-study-final.pdf. 18. U.S. GOV’T ACCOUNTABILITY OFFICE, GAO-10-423, INTELLECTUAL PROPERTY: OBSERVATIONS ON EFFORTS TO QUANTIFY THE ECONOMIC EFFECTS OF COUNTERFEIT AND PIRATED GOODS 15-16 (2010). 19. 17 U.S.C. § 501(a)-(b) (2006). 20. See, e.g., Copyright Trolls, ELECTRONIC FRONTIER FOUND., 458 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 When a copyright holder uncovers online piracy of his or her work, he or she can only discover the IP address (and other technical information) about the infringer. Only ISPs have the records to link an IP address with the name and physical address of an Internet user. In order to bring a suit for copyright infringement, the copyright holder needs to first uncover the identity of the defendant so that he or she can be served with process. One possible mechanism for uncovering an infringer’s identity is the ISP subpoena provided for in section 512(h) of the DMCA. That section allows a copyright owner to “request the clerk of any United States district court to issue a subpoena to a service provider for identification of an alleged infringer in accordance with this subsection.”21 However, two circuit court of appeals, the D.C. Circuit and the Eighth Circuit, have held that this section only allows a subpoena to be issued to an ISP that is storing infringing content on their servers, not to an ISP that merely carried infringing traffic on their network.22 Although early peer-to-peer networks, such as Napster, did store information about infringing files on a centralized server, later decentralized peer-to-peer networks, like Gnutella and Kazaa, and modern BitTorrent networks simply connect users to each other without storing information on the ISP’s servers.23 This change in architecture was driven partly by a desire on the part of ISPs to avoid secondary copyright liability.24 Another happy legal coincidence of ISPs distancing themselves from the infringing activities of their users has been immunity from DMCA subpoenas in direct suits against Internet users. Deprived of the DMCA subpoena as a tool to identify infringers, plaintiffs in direct copyright infringement suits have been forced to rely on the generic discovery provisions of the Federal Rules of Civil Procedure. In general, a plaintiff cannot pursue any discovery until after the parties to the suit have met and conferred.25 In a typical suit for online infringement, however, the identity of the defendant is unknown at the time of filing, making a pre-discovery conference impossible. The plaintiff requires discovery, in the form of a subpoena on the ISP, simply to learn the identity of the defendant and serve process. In order to proceed, the plaintiff must therefore move for expedited discovery under Rule 26(d) of the Federal Rules of Civil Procedure. Under Rule 26(d)(2), the court can, on motion, order expedited discovery before the parties have met and conferred “for the parties’ and witnesses’ convenience and in the interests of justice.”26 The various federal jurisdictions have different https://www.eff.org/issues/copyright-trolls (last visited Feb. 16, 2013). 21. 17 U.S.C. § 512(h)(1) (2006). 22. In re Charter Comms., Inc., Subpoena Enforcement Matter, 393 F.3d 771, 777 (8th Cir. 2005); Recording Indus. Ass’n of Am. Inc. v. Verizon Internet Servs., Inc., 351 F.3d 1229, 1237 (D.C. Cir. 2003). 23. See, e.g., John Borland, The Evolution of File Swapping, CNET (June 27, 2005, 8:34 AM) http://news.cnet.com/The-evolution-of-file-swapping/2100-1030_3-5752075.html. 24. Id. 25. FED. R. CIV. P. 26(d)(1). 26. Id. at 26(d)(2). Winter 2013] COPYRIGHT VIGILANTISM 459 tests for determining whether or not expedited discovery is warranted. Although most judges appear to accept the necessity of ISP subpoenas in online copyright infringement suits,27 some judges are more reluctant to allow such far-reaching early discovery. Some judges have denied expedited discovery or quashed issued subpoenas on the grounds that the court may not have personal jurisdiction over the accused Internet users. Most judges are willing to wait until after the identity of a defendant is determined before addressing the question of personal jurisdiction,28 but a handful are concerned about personal jurisdiction from the time of filing. These judges will only allow discovery to proceed if the plaintiff can make a prima facie or good faith showing that personal jurisdiction exists over the as-yet-unidentified defendants.29 At the very least, this requires plaintiffs to run geolocation software to determine if the IP address of the defendant is geographically within the borders of the court’s jurisdiction.30 Often judges impose such a burden on plaintiffs out of a fear that plaintiffs are merely abusing the expedited discovery process to learn information about Internet users to use in settlement offers or lawsuits in other jurisdictions.31 In suits against multiple Internet users, a number of judges are hesitant to allow large numbers of subpoenas to be served on ISPs out of a concern for the burden it will place on the ISPs’ businesses. In one suit, Time Warner estimated that the cost of linking an IP address to a real-world name and address at $120 per lookup.32 ISPs are not parties to direct infringement lawsuits, and courts would often prefer to protect them from intrusive discovery. Protective orders limiting the number of subpoenas that an ISP must answer per month are often employed in this capacity.33 Although the purpose of such orders is ostensibly to protect the business interests of the ISPs, ISPs may use them to stymie unpopular litigation against their subscribers, perhaps 27. See, e.g., Digital Sin, Inc. v. Does 1-176, No. 12-CV-00126 (AJN), 2012 WL 263491, at *2 (S.D.N.Y. Jan. 30, 2012); Pac. Century Int’l, Ltd. v. Does 1-48, No. C 113823 MEJ, 2011 WL 4725243, at *5 (N.D. Cal. Oct. 7, 2011); Cornered, Inc. v. Does 12177, No. 10-01476 (CKK), 2010 WL 4259605, at *1 (D.D.C. Oct. 22, 2010). 28. See, e.g., Cinetel Films, Inc. v. Does 1-1,052, No. JFM 8:11-cv-02438, 2012 WL 1142272, at *11 (D. Md. Apr. 4, 2012); Raw Films, Ltd. v. John Does 1-11, No. 12cv368WQH (NLS), 2012 WL 684763, at *4 (S.D. Cal. Mar. 2, 2012); W. Coast Prods., Inc. v. Does 1-5829, 275 F.R.D. 9, 14-15 (D.D.C. 2011). 29. See, e.g., Axel Braun Prods. v. Does 1-2,823, No. 11-56 (EGS/JMF), 2012 WL 177856, at *3 (D.D.C. Jan. 19, 2012); DigiProtect USA Corp. v. Does 1-240, No. 10 Civ. 8760(PAC), 2011 WL 4444666, at *2 (S.D.N.Y. Sept. 26, 2011). 30. See, e.g., Axel Braun Prods., 2012 WL 177856, at *3. But see Celestial Inc. v. Swarm Sharing Hash 8AB508AB0F9EF8B4CDB14C6248F3 C96C65BEB882 on December 15, 2011, No. CV 12-00132 DDP (SSx), 2012 WL 995273, at *2 (C.D. Cal. Mar. 23, 2012) (questioning the accuracy of geolocation software and finding the results of such software insufficient to show personal jurisdiction). 31. See, e.g., CP Prods., Inc. v. Does 1-300, No. 10 C 6255, 2011 WL 737761, at *1 (N.D. Ill. Feb. 24, 2011). 32. DigiProtect USA Corp., 2011 WL 4444666, at *4. 33. See, e.g., id. 460 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 in an attempt to deter such litigation in the future. Taken together, the challenges to discovering the identities of direct infringers and getting them into court form a rigorous procedural labyrinth. In order to assert their rights against the innumerable anonymous Internet users pirating their works, copyright owners must convince a court of the necessity of ISP subpoenas34 and contend with the reluctance of ISPs to identify subscribers. In some jurisdictions they must pursue pre-discovery investigation to estimate the geographic location of an infringer just to avoid being thrown out of court for lack of personal jurisdiction.35 In many jurisdictions, joinder rules prevent joining in a single suit individuals who have shared the same file, thereby forcing plaintiffs to pay a separate filing fee for each of the often thousands of individuals infringing their works.36 C. The Secondary Liability Arms Race The difficulty of holding direct infringers accountable led copyright holders to explore alternate liability theories. By asserting various secondary infringement claims against ISPs and payment services, copyright holders hoped to choke online piracy by depriving it of the Internet resources on which it depended. As new secondary liability theories were developed in the courts, new kinds of Internet architecture developed to thwart these theories. The arena of secondary liability has thus developed into a frustrating cat-and-mouse game between copyright owners and pirates. The first generation of peer-to-peer networks utilized a centralized server/client architecture. A centralized server contained indices of the files stored on each computer on the network and directed users to the files they requested.37 Napster was an example of this type of network. Centralized peerto-peer networks were vulnerable to vicarious liability or contributory copyright infringement claims, as evidenced by the takedown of Napster in 34. See, e.g., New Sensations, Inc. v. Does 1-306, No. 2:12-cv-1885-GEB-EFB, 2012 WL 5031651 at *2 (E.D. Cal. Oct. 17, 2012) (“Courts in the Ninth Circuit apply a ‘good cause’ test in deciding whether to permit expedited discovery before the Rule 26(f) conference.”); Digital Sin, Inc. v. Does 1-176, No. 12-CV-00126 (AJN), 2012 WL 263491 at *2 (S.D.N.Y. Jan. 30, 2012) (“Courts in this district have applied a ‘flexible standard of reasonableness and good cause’ in determining whether to grant a party’s expedited discovery request.” (citation omitted)). 35. See, e.g., Patrick Collins, Inc. v. Does 1-72, No. 11-58 (RMU/JMF), 2012 WL 177864 at *3 (D.D.C. Jan. 19, 2012) (“The Court, therefore, will order plaintiff to show cause why it should assert jurisdiction over the person of each John Doe defendant unless it has a good faith belief that that person is domiciled in the District of Columbia which . . . may be premised on ‘utilizing geolocation services . . . .” (citation omitted)). 36. See, e.g., Hard Drive Prods. v. Does 1-33, No. C 11-03827 LB, 2011 WL 5325530 at *3 (N.D. Cal. Nov. 3, 2011). 37. SANDVINE INC., PEER-TO-PEER FILE SHARING: THE IMPACT OF FILE SHARING ON SERVICE PROVIDER NETWORKS 4 (2002), available at http://downloads.lightreading.com/wplib/sandvine/P2P.pdf. Winter 2013] COPYRIGHT VIGILANTISM 461 2001.38 After Napster, peer-to-peer networks decentralized so that servers owned by the peer-to-peer service no longer stored indices of available files. Instead, computers on the network provided file information to the service in response to searches.39 Although this architecture seemingly evaded vicarious or contributory liability theories by ensuring that the service never had knowledge of infringing activity, courts borrowed the theory of “inducement” liability from patent law in order to address the new configuration. In MGM Studios, Inc. v. Grokster, Ltd., the Supreme Court applied an inducement theory to decentralized peer-to-peer service Grokster.40 The Court held that although Grokster did not have specific knowledge of infringing activity on their network, they intended their network to be used for piracy and had actively encouraged their users to share infringing files. After Grokster, the file-sharing community has once again jumped ship and moved to new services that evade inducement liability. The new services act only as delivery systems for files sent at the request of Internet users. For example, users of the popular BitTorrent client upload files containing a “tracker” to the Internet. These files contain information on the location of the file, but no content. Trackers can be located by using one of the many tracker search engines that have grown up on the Internet. There is no central search engine or repository of files or trackers.41 Once a user finds a file she would like to share, she enters the “swarm” of users sharing that file, simultaneously uploading and downloading small quantities of the file with each other.42 BitTorrent is only a delivery system, and never has knowledge of the contents of a particular file or even who is using the service. Despite occasional successes in holding file-sharing services liable for infringement, the swift evolution of technology will continue to make any sustained program of enforcement against these services impossible. New technologies continually arise to make each hard-fought secondary liability battle obsolete. Services and Internet users have caught copyright owners in a never-ending game of cat-and-mouse in which the law is too slow to keep up with technological advances. Although secondary liability theories will no doubt continue to be employed by copyright owners, an effective approach to direct infringement by Internet users will be necessary to truly address the root of piracy. 38. 39. 40. 41. 42. A&M Records, Inc. v. Napster, Inc., 237 F.3d 1004 (9th Cir. 2001). SANDVINE INC., supra note 37, at 6. MGM Studios, Inc. v. Grokster, Ltd., 545 U.S. 913, 926 (2005). Bryan H. Choi, The Grokster Dead-End, 19 HARV. J.L. & TECH. 393, 403 (2006). Frequently Asked Questions: Concepts, BITTORRENT, http://www.bittorrent.com/ help/faq/concepts (last visited July 1, 2012). 462 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 D. Infringement Culture and Congressional Paralysis The greatest threat to copyright enforcement in the Internet age likely is not legal at all, but cultural. Today’s pirates grew up in a world with limited enforcement of copyright online. Many have developed the feeling that they are entitled to free access to content, or at the very least that piracy is acceptable.43 Enforcement of copyright has been lumped together in the public consciousness with suppression of free speech, and compared to censorship of political speech in China or Iran.44 In such an environment, any new measures introduced to enforce copyrights on the Internet are likely to be received with anger and protest. The RIAA was forced to end its campaign of litigation against direct online infringers in 2008 amid widespread public complaint.45 In 2011, a high-profile online campaign, including a blackout of several important web services,46 was responsible for Congress abandoning SOPA47 and PIPA,48 two pieces of proposed litigation that would have given copyright holders the ability to demand the takedown of entire sites or domains, rather than just specific content as it can under the DMCA.49 The public backlash against SOPA and PIPA has made Congress wary to pursue any new online copyright enforcement legislation. Copyright holders are left with the existing copyright law, which has proven inefficient and unsuited to stopping piracy in the Internet age. In addition to closing off legislative avenues of enforcement reform, public resentment of copyright enforcement fosters continued acceptance of largescale piracy. Infringers are insulated against any public reproach for their actions and may not experience an internal sense of guilt, such as might accompany theft of physical property. Enforcement attempts likely will be less than optimally effective so long as they run counter to embedded cultural norms. 43. See Swartz, supra note 5. 44. Josh Halliday, Google Boss: Anti-Piracy Laws Would Be Disaster for Free Speech, THEGUARDIAN (May 18, 2011, 11:24 EDT), http://www.guardian.co.uk/technology/ 2011/may/18/google-eric-schmidt-piracy;Rebecca MacKinnon, Internet Freedom Starts at Home, FOREIGN POL’Y (Apr. 3, 2012) available at http://www.foreignpolicy.com/ articles/2012/04/03/The_Worlds_No_1_ Threat_to_Internet_Freedom; Letter from Human Rights Organizations to Harry Reid, Majority Leader, U.S. Senate (Jan. 16, 2012), available at https://www.accessnow.org/ policy-activism/press-blog/human-rights-community-speaksout-on-protect-ip-act. 45. See McBride & Smith, supra note 6. 46. Zach Carter & Ryan Grim, SOPA Blackout Aims to Block Internet Censorship Bill, HUFFINGTON POST (Jan. 18, 2012), http://www.huffingtonpost.com/2012/01/18/sopablackout-internet-censorship_n_1211905.html. 47. Stop Online Piracy Act, H.R. 3261, 112th Cong. (2011). 48. Protect IP Act, S. 968, 112th Cong. (2011). 49. Pepitone, supra note 7. Winter 2013] II. COPYRIGHT VIGILANTISM 463 THE HERO COPYRIGHT NEEDS: GRADUATED RESPONSE AND COPYRIGHT ALERT The utter breakdown of public copyright enforcement mechanisms has galvanized content owners to seek out their own solutions to piracy. Mimicking regulatory enforcement schemes in France, South Korea, and New Zealand, American content owners have begun to experiment with “graduated response” enforcement. A. Graduated Response Abroad The graduated response approach involves obtaining the cooperation of ISPs to implement a series of increasingly severe sanctions against Internet users accused of copyright infringement.50 Sanctions usually begin with mere warnings in response to a first or second offense, and escalate to include throttling of connection speeds, blocking of sites, or even outright termination of service for subsequent offenses.51 An administrative approach to graduated response has already been attempted in several other nations. Until recently, the program overseen by the French agency, Haute Autorité pour la diffusion des œuvres et la protection des droits sur internet (HADOPI), was widely lauded in the copyright world as a model of efficient, effective, and fair enforcement. The French law, passed in 2009, created HADOPI to oversee a graduated response system.52 HADOPI has the authority to monitor for online piracy and to send two injunctions to Internet users accused of piracy ordering them to cease their illegal behavior.53 If these injunctions are not heeded within a year, HADOPI is authorized to suspend the user’s Internet service for between two months and a year.54 An Internet user can appeal actions taken by HADOPI in court.55 By the end of December 2011, HADOPI had sent 822,000 initial warnings to Internet users, but only 165 people reached the third stage of the program and faced having their Internet suspended.56 Of these, only 134 cases were prosecuted, and no users ultimately had their Internet cut off.57 HADOPI reports that 95% of alleged infringers cease their infringing after receipt of a 50. See Peter K. Yu, Copyright USA—A Collection: The Surging Influence of Copyright Law in American Life: The Graduated Response, 62 FLA. L. REV. 1373, 1374 (2010). 51. Id. 52. CODE DE LA PROPRIETE INTELLECTUELLE [C.P.I.] art. L. 331-12 (Fr.). 53. Id. at art. L. 331-26. 54. Id. at art. L. 331-27. 55. Id. 56. Eric Pfanner, Copyright Cheats Face the Music in France, N.Y. TIMES (Feb. 19, 2012), http://www.nytimes.com/2012/02/20/technology/20ihtpiracy20.html?pagewanted=all. 57. Richard Chirgwin, France Backs Away from Hadopi, THE REGISTER (Aug. 6, 2012, 10:59 PM), http://www.theregister.co.uk/2012/08/06/hadopi_under_fire. 464 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 first notice, 92% of continuing infringers cease after a second notice, and 98% of continuing infringers cease after a third notice.58 An independent study found that French iTunes sales increased 22.5% more than sales in comparable countries after the introduction of graduated response,59 possibly indicating that former pirates were seeking legitimate sources for music. In 2012, the head of HADOPI, Marie-Françoise Marais, told IFPI that “Hadopi . . . is gaining widespread acceptance. People are changing their behavior in favour of legal offerings.”60 Recently, however, the French government has become unhappy with the costs generated by HADOPI. The agency costs the French government twelve million euros a year, and requires a staff of sixty agents.61 French culture minster Aurélie Filippetti described HADOPI as “unwieldy, uneconomic and ultimately ineffective.”62 As a result, the French government is now conducting a consultation on Internet piracy, and is considering cutting appropriations to HADOPI or pursuing other avenues of enforcement.63 Despite these concerns about the cost-effectiveness of the French program, HADOPI has served as an inspiration and jumping-off point for other graduated response programs around the world. In South Korea, where graduated response legislation has been in place since 2009, the government reports that 70% of alleged infringers stop their infringing activity after receiving a single warning notice, and that a further 70% of those who continue to infringe cease after a second notice.64 The New Zealand graduated response legislation is recent, passed in September of 2011. Nevertheless, data gathered by IFPI shows that P2P network usage fell 16% in New Zealand within the two months after the graduated response legislation was passed, with digital sales rising 35% during the same period.65 Given the successes of graduated response programs abroad, it is no surprise that interested parties would attempt a similar scheme in the United States. 58. HADOPI, 1 ½ YEARS AFTER ITS LAUNCH 3 (2012), available at http://hadopi.fr/sites/default/files/page/pdf/note17.pdf. 59. Brett Danaher et al., The Effect of Graduated Response Anti-Piracy Laws on Music Sales: Evidence from an Event Study in France 14 (Working Paper, 2012), available at http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1989240. But see Brett Danaher, Michael D. Smith & Rahul Telang, Did HADOPI Cause an Increase in iTunes Music Sales in France?, INFOJUSTICE.ORG (Mar. 14, 2012) http://infojustice.org/archives/8891 (emphasizing the limits of the explanatory power of their earlier study). 60. Digital Music Report 2012, INT’L FED’N OF THE PHONOGRAPHIC INDUS. 20 (2012), http://www.ifpi.org/content/library/DMR2012.pdf. 61. Chirgwin, supra note 57. 62. Id. 63. Id. 64. Id. at 17. 65. Id. at 19. Winter 2013] COPYRIGHT VIGILANTISM 465 B. The American Version: Copyright Alert The most recent attempt to create a graduated response system in the United States is the Copyright Alert System, popularly known as the “six strikes” program.66 Unlike graduated response programs in other countries, Copyright Alert is an entirely private and contractual scheme, not an administrative program instituted through legislation. The program was created through a memorandum of understanding (MOU) among representatives of the RIAA, MPAA, several media corporations, and all of the major ISPs.67 The MOU was signed on July 6, 2011. Due to delays in implementation,68 the program has been delayed, but is expected to roll out during early 2013.69 The program calls for a six-stage graduated response to infringement coupled with the creation of a private regulatory body, the Center for Copyright Information, tasked with educating the public about infringement and resolving disputes under the MOU.70 By the terms of the MOU, the responsibility for detecting instances of online infringement falls on the RIAA and MPAA (the Content Owner Representatives).71 These organizations are empowered to send notices to the signatory ISPs containing the IP addresses and other identifying information of alleged infringers.72 The notifications must contain a detailed description of the work allegedly infringed and the basis for believing it was infringed.73 In addition, the Content Owner Representatives agree to identify infringement only through methodologies that have been reviewed by an independent expert and to avoid cases of de minimus infringement.74 These safeguards are 66. Doug Gross, With SOPA Shelved, Anti-Piracy Advocates Take New Approaches, CNN.COM (Mar. 22, 2012, 12:23 PM), http://www.cnn.com/2012/03/22/tech/web/isps-sopapiracy/index.html. 67. Memorandum of Understanding (July 6, 2011), available at http://info.publicintelligence.net/CCI-MOU.pdf. Content owner parties to the agreement are Walt Disney Studios Motion Pictures; Paramount Pictures Corp.; Sony Pictures Entertainment Inc.; Twentieth Century Fox Film Corp.; Universal City Studios LLC; Warner Bros. Entertainment Inc.; UMG Recordings, Inc.; Warner Music Group; Sony Music Entertainment; and EMI Music North America. Id. at Attachment B. The ISP parties to the agreement are AT&T Inc.; Verizon; Comcast Cable Communications Management, LLC; Time Warner Cable Inc.; and the New York, New Jersey, and Connecticut cable systems operated by CSC Holdings, LLC. Id. at Attachment A. 68. Gigi Sohn, What’s Going on with the Copyright Alert System?, PUBLIC KNOWLEDGE (Aug. 7, 2012), http://www.publicknowledge.org/blog/whats-going-copyrightalert-system (stating that the delays have three causes: ISPs working to implement technology, the Center for Copyright Information working to phrase notices effectively, and the American Arbitration Association working out the procedure for appeals). 69. Jill Lesser, Dotting Our “I”s, CENTER FOR COPYRIGHT INFO. (Nov. 28, 2012), http://www.copyrightinformation.org/node/714. 70. Memorandum of Understanding, supra note 67, at § 2(A). 71. Id. at § 4(A). 72. Id. at § 4(C)-(D). 73. Id. at § 4(D). 74. Id. at § 4(C). 466 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 designed to provide some measure of protection to Internet users by minimizing wrongful or arbitrary notices. The form of Copyright Alert notices mirrors the required form of similar notices under the DMCA.75 Upon receiving a notice from a Content Owner Representative, ISPs are required to respond in accordance with the Copyright Alert System. By requiring the ISPs to independently enforce the program, Copyright Alert addresses some of the privacy concerns that have attended copyright infringement litigation. The program does not require ISPs to release identifying information about the owners of allegedly infringing IP addresses to law enforcement or copyright owners. The ISP can simply match IP addresses from received notices to subscriber names and implement an appropriate response on their own. Each ISP will develop and independently enforce its own enforcement program, subject to the minimum standards laid out in the MOU.76 Every Copyright Alert System will consist of six graduated responses to infringement.77 For the first two notices, ISPs will do no more than send a warning to the subscriber. This is called the “Initial Educational Step.”78 The next two responses, called the “Acknowledgement Step,” also only entail warnings to the subscriber.79 Unlike the warnings sent at the Initial Educational Step, the warnings at the Acknowledgement Step will require subscribers to “acknowledge” receipt of the warning, likely through a pop-up box or landing page on their browser.80 This acknowledgement is treated as consent for the ISP to release subscriber information to copyright owners or law enforcement in the event that further instances of alleged infringement lead to a review proceeding.81 The acknowledgement also helps content owners avoid procedural issues concerning which of multiple users of an account actually committed the infringing act. The acknowledgement signifies that the subscriber “agrees immediately to cease, and/or agrees to instruct other users of the Subscriber’s account to cease infringing conduct, if any exists.”82 In this way, the acknowledgement effectively applies to all users of an account, not only the subscribers themselves. Finally, after five notices relating to the same account, the ISP will move to the “Mitigation Measures Step.”83 At this point, the ISP will take disciplinary action against the subscriber, including throttling Internet speeds, steppingdown the subscriber’s service tier, or restricting Internet access.84 The sixth 75. 76. 77. 78. 79. 80. 81. 82. 83. 84. See 17 U.S.C. § 512(c)(3)(A). Memorandum of Understanding, supra note 67, at § 4(G). Id. Id. at § 4(G)(i). Id. at § 4(G)(ii). Id. at § 4(G)(ii). Id. Id. Id. at § 4(G)(iii). Id. at § 4(G)(iii). Winter 2013] COPYRIGHT VIGILANTISM 467 step, the “Post Mitigation Measures Step,” is essentially identical to the previous one, except that the notice sent to the subscriber will warn them of the possibility of legal action under the DMCA.85 Subscribers are given a sevenday grace period between alerts,86 and a year without any notices will “reset” a given subscriber’s account back to the Initial Educational Step.87 The details of each ISP’s Copyright Alert System are to be included in the Acceptable Use Policies or Terms of Service between the ISP and their subscribers,88 thus binding Internet users to the contractual scheme. The notice process outlined in the MOU also contains provisions meant to protect participating ISPs from undue costs associated with responding to notices. The Content Owner Representatives are only permitted to send a certain volume of notices to each ISP, which will be determined in subsequent Implementation Agreements.89 Also, if an ISP receives more notices or complaints about notices than their business can handle, they are permitted to temporarily stop enforcing their program.90 These safeguards limit the burden on ISPs of addressing subscriber infringement, a burden that had been a matter of concern in direct infringement cases where ISPs were asked to respond to third-party subpoenas for subscriber information.91 The MOU also provides for a private review proceeding through which Internet users can challenge the mitigation measures imposed on them.92 The review proceeding only adjudicates the Internet user’s rights under the Copyright Alert System, and does not claim to settle the question of copyright infringement under the law.93 Nevertheless, the law applied in the review is United States copyright law,94 indicating that the Copyright Alert System is intended as an alternate enforcement mechanism for copyright, not as a new set of private substantive rights. In the review proceeding, an Internet user is limited to asserting one of seven defenses against the allegation of infringement. Five of these defenses essentially claim that the Content Owner Representative erred in sending a notice to the ISP. This could be because the subscriber’s account was misidentified, because the subscriber’s use of the work was authorized by the copyright holder, because the file in question did not in fact primarily consist of the identified copyrighted work, or because it did consist of the work, but the 85. 86. 87. 88. 89. 90. 91. Id. at § 4(G)(iv). Id. at § 4(G). Id. at § 4(G)(v). Id. at § 4(F). Id. at § 5(A). Id. at § 5(D). See, e.g., Nate Anderson, Time Warner Cable Tries to Put Brakes on Massive Piracy Case, ARS TECHNICA (May 15, 2010, 6:16 PM) http://arstechnica.com/techpolicy/news/2010/05/time-warner-cable-tries-to-put-brakes-on-massive-piracy-case.ars. 92. Memorandum of Understanding, supra note 67, at § 4(H). 93. Id. at § 4(H)(i). 94. Id. at Attachment C, § 6. 468 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 work was published before 1923 and is no longer protected. A sixth defense is that the alleged infringing activity was by someone outside of the subscriber’s household acting without the subscriber’s knowledge or authorization. Finally, an Internet user can argue that her activity constituted fair use under United States copyright law and should not be subject to sanction.95 The review proceeding will be overseen by a private “Administering Organization” consisting of members selected by the Executive Committee of the Center for Copyright Information (CCI).96 The CCI has selected the American Arbitration Association to manage the review process.97 The MOU provides that reviewers will rely on an independent expert for interpretations of current copyright law.98 The Copyright Alert System represents a sophisticated attempt to reassert copyright enforcement in the face of massive infringement, while at the same time respecting the business interests of ISPs and the privacy and speech rights of Internet users. The program has a variety of advantages over traditional enforcement under the Copyright Act. It allows for a swift and efficient response to online infringement without the expense or procedural difficulties associated with litigation. Copyright holders also benefit from avoiding the bad press associated with copyright infringement lawsuits. ISPs benefit from cooperating with content owners to address piracy concerns. Although the DMCA provides a safe harbor to ISPs that merely serve as passive conduits for infringing material distributed by users,99 as technology becomes more sophisticated ISPs increasingly face the risk of falling outside of the safe harbor. Improved deep-packet inspection technologies have allowed ISPs to determine the contents of the data going through their systems.100 ISPs use this technology to manage their traffic or provide varied levels of service for different pricing tiers,101 but it could just as easily be employed to identify infringing traffic. The use of deep-packet inspection may eventually transform ISPs from “mere conduits” to active network managers in the eyes of the law, depriving them of safe-harbor protection.102 In addition, as many ISPs move into the content distribution marketplace,103 they have an incentive to protect their own sales by cutting 95. Id. at Attachment C, § 1. 96. Id. at Attachment C, § 5.1. 97. Frequently Asked Questions, CENTER FOR COPYRIGHT INFORMATION, http://www.copyrightinformation.org/faq (last visited May 15, 2012). 98. Memorandum of Understanding, supra note 67, at Attachment C, § 6. 99. 17 U.S.C. § 512(a) (2012). 100. Yu, supra note 50, at 1375 n. 10. 101. Id. at 1387. 102. Id. 103. See, e.g., Digital TV, AT&T, http://www.att.com/shop/tv.html#fbid= RpgaKpWhFEK (last visited July 1, 2012); Media, VERIZON WIRELESS, http://products.verizonwireless.com/index.aspx?id=fnd (last visited July 1, 2012); TWC TV, TIME WARNER CABLE, https://video.timewarnercable.com (last visited July 1, 2012). Winter 2013] COPYRIGHT VIGILANTISM 469 down competition from illegal sources. Even those ISPs that do not distribute their own content will benefit from the decreased network traffic generated by piracy over peer-to-peer networks, which currently consumes an outsized amount of bandwidth.104 Internet users benefit as well. Because ISPs respond independently to notices, there is no need to release identifying information for alleged infringers, and the privacy concerns often raised in civil proceedings are eliminated.105 Users will be spared the often aggressive settlement tactics of copyright plaintiff’s attorneys and the litigation costs of resisting such tactics. Further, addressing suspected infringement through private mitigation measures eliminates the risk of statutory damages for copyright infringement, which can be as high as $30,000 per work, or $150,000 per work for willful infringement.106 Overall, graduated response should protect law-abiding Internet users from inconvenience and expense while protecting infringers from certain unfair aspects of in-court enforcement. III. WITH GREAT POWER COMES GREAT RESPONSIBILITY: CHALLENGES TO COPYRIGHT ALERT Despite the promise of graduated response, the Copyright Alert System suffers from its private contractual foundation. Frustrated with the failure of the government and the courts to protect and enforce their rights, copyright owners have become copyright vigilantes, defending their rights through Copyright Alert. Like all vigilantes, they face competency, legitimacy, and enforcement challenges as they shoulder responsibilities that properly belong to state or federal officials. Copyright owners and ISPs should be aware of these weaknesses going forward as they begin to employ Copyright Alert, and policymakers should bear them in mind as they consider future avenues of copyright enforcement. A. The Competence of Private Actors to Enforce Copyright Copyright Alert raises the question of whether private actors, such as copyright owners and ISPs, are competent to enforce copyright. By “competence,” I mean an institution’s ability to perform the tasks set for it. Private actors may prove incompetent to enforce copyright either because they cannot adequately address sophisticated equitable concerns, such as those involved in the defense of fair use, or because they are biased and thus unable to fairly assess infringement. Either variety of incompetence could lead to under- or more likely over-enforcement of copyright. Determination of fair use is perhaps the clearest example of the first kind 104. See Yu, supra note 50, at 1385. 105. See id. at 1383. 106. 17 U.S.C. § 504 (2006). 470 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 of incompetence: objective inability of an institution to perform a task. The Copyright Alert review proceeding allows Internet users to assert a fair use defense, which is a defense to copyright infringement based on free speech concepts. Although now codified in the Copyright Act,107 fair use has its roots in the common law. The defense was first outlined by Justice Story in his seminal opinion in Folsom v. Marsh, in which he wrote that infringement could be justified where copyrighted material is used in “an original and new work, [constituting,] in no just sense, a piracy of the work of the plaintiffs.”108 In making the determination of whether a use of copyrighted material was justified, Story looked at the importance of the material taken to the value of the copyrighted work and the degree to which the new work was a substitute for the copyrighted work.109 Over time, the doctrine came to be understood as a free speech carve-out from copyright, based largely on equitable balancing of the value of new infringing speech against the value of copyright enforcement. The statutory codification of fair use leaves a good deal of space for such judicial balancing. It lays out the four factors to be considered in a fair use determination—the character and purpose of the use, the nature of the copyrighted work, the amount and substantiality of the portion used, and the effect on the potential market for the copyrighted work110—without substantial guidance as to how these terms are to be interpreted or how each factor is to be weighed relative to the others. The legislative history of the statutory fair use defense provides that these four factors were “derived from earlier court decisions” and that “additional factors may also be considered in the court’s discretion.”111 As a result, fair use jurisprudence retains much of its equitable character, with judges incorporating the statutory factors to organize a generally fact-based and ad hoc determination. A judge’s decision is informed by their experience in common-law and equitable reasoning and by the copyright expertise of litigators in their briefs and arguments. Under Copyright Alert, fair use determinations will be made initially by copyright owners (or their representatives), and later possibly by AAA arbitrators on review. No one involved will be a judge, and relatively few will have ever litigated a copyright case. This means that fair use determinations will be made with limited knowledge of fair use jurisprudence and no practical experience making equitable determinations. The MOU does provide that the CCI will appoint a single copyright expert to advise arbitrators involved in the review process.112 This expert would be tasked with outlining the current state of the law of fair use “as determined by United States federal courts.”113 Such 107. 108. 109. 110. 111. 112. 113. 17 U.S.C. § 107 (2006). Folsom v. Marsh, 9 F. Cas. 342, 347 (D. Mass. 1841) (Story, J.). Id. at 348. 17 U.S.C. § 107. H.R. REP. NO. 102-836, at 3 (1992). Memorandum of Understanding, supra note 67, at Attachment C, § 6. Id. Winter 2013] COPYRIGHT VIGILANTISM 471 a procedure ignores the fact-based nature of fair use analysis, which resists simple summarization. An expert summary applied to all reviews cannot provide the same degree of guidance to arbitrators as, for example, briefs by copyright litigators, which are composed with the facts of a given case in mind. The institutions tasked with overseeing Copyright Alert simply do not have the judicial or legal expertise to make correct determinations, creating a risk of incorrect decisions. The competence of private actors to enforce copyright law could also be undermined by bias. Both Copyright Alert itself and the private review program provided for in the MOU are overseen and funded by copyright owners and ISPs. Each of these groups may have the incentive to over-enforce a copyright, punishing Internet users who have not, in actuality, violated the law. This danger is clearest in the case of copyright owners, who may prefer to exercise more extensive control over their work than copyright actually allows. In the realm of DMCA takedown requests, a study cited by Google in their Transparency Report114 found that 31% of sampled takedown requests presented a substantive copyright law question, such as a fair use or uncopyrightable subject matter argument.115 The participation of ISPs in the Copyright Alert system is not likely to counterbalance over-enforcement by copyright owners. The interests of ISPs are rapidly converging with those of copyright owners as ISPs enter the content industry116 and as they develop deep packet scanning technologies that could eventually threaten their safeharbor protection.117 The very existence of the MOU is evidence that ISPs are interested in policing copyright. Therefore, although the MOU does allow ISPs to waive an alert once for each identified IP address,118 ISPs are not likely to exercise this prerogative often. Even where it is invoked, it provides only limited protection against over-enforcement. At the review stage, bias is less likely, but may be introduced through the summary of copyright law prepared by the CCI’s expert. Incompetence has the potential to make Copyright Alert less effective than it might otherwise be. If users do not believe that Copyright Alert will accurately identify infringers, then Copyright Alert sanctions will be seen as somewhat arbitrary. Arbitrary enforcement will not have the desired deterrent effect on piracy. Concerns about fairness and over-enforcement also have the potential to 114. FAQ, GOOGLE TRANSPARENCY REPORT, http://www.google.com/transparency report/removals/copyright/faq (last visited June 2, 2012). 115. Jennifer M. Urban & Laura Quilter, Efficient Process or “Chilling Effects”? Takedown Notices Under Section 512 of the Digital Millennium Copyright Act, 22 SANTA CLARA COMPUTER & HIGH TECH. L.J. 621, 667 (2006). 116. Consider, for example, Comcast’s controlling stake in NBC. See Company Overview, COMCAST (2012), http://corporate.comcast.com/news-information/companyoverview. 117. See Yu, supra note 50, at 1387. 118. Memorandum of Understanding, supra note 67, at § 4(G)(iii). 472 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 tarnish the reputations of copyright owners and ISPs, harming their relationships with their customers. More directly, they could breed discontent among Internet users and undermine the core purpose of Copyright Alert, which is to educate users about piracy and encourage legal access to content. Copyright Alert is unlikely to change public attitudes toward the morality of piracy if users feel that it unfairly punishes them. Notably, these reputational harms will arise from the mere perception of incompetence, whether or not private enforcers actually do erroneously punish a significant number of innocent users. B. Legitimacy: The Authority of Private Actors to Enforce Copyright Related to but distinct from questions of competence are questions of legitimacy. Whereas “competence” indicates the ability of an institution to act, “legitimacy” indicates its authority to act. Copyright, like other forms of intellectual property, is a state-created right. Absent government intervention, it is relatively difficult to exercise property rights, especially the right of exclusion, over copyrightable subject matter. Literary and artistic expression is a public good, benefitting the viewer or listener with no marginal cost to the performer or speaker.119 While all property rights have their origin with the State, ownership and exclusive use of real property would likely persist absent legal enforcement. In contrast, we might expect there to be no ownership of intellectual property at all absent legal protections. The non-excludible quality of intellectual property makes ownership of intellectual property a uniquely legal, rather than natural, property right. The result is that copyright is uniquely defined by the State. The right has no meaning outside of its legal definition, and this definition encompasses the entire set of copyright rights, defenses to infringement, and procedural and legal protections. The failure to provide the substantive defenses and procedural protections that are an integral part of copyright law undermines the legitimacy of the Copyright Alert program. Internet rights activists have already begun to complain that the MOU was drafted and signed without input from representatives of Internet users.120 Copyright Alert will be imposed on users through their contracts with their ISPs without any opportunity for input or negotiation. These contracts are contracts of adhesion, presented to users on a take-it-or-leave-it basis. Most areas are only served by two ISPs—a cable company and a telephone 119. See Frederick R. Warren-Boulton, Kenneth C. Baseman & Glenn A. Worock, The Economics of Intellectual Property Protection for Software: The Proper Role for Copyright, 1 (1994), available at http://ideas.repec.org/p/wpa/wuwpio/9411004.html. 120. See, e.g., Corynne McSherry, Graduated Response Program: Let’s Press the Reset Button, ELECTRONIC FRONTIER FOUNDATION (Apr. 3, 2012), https://www.eff.org/deeplinks/2012/04/graduate-response-program-lets-press-reset-buttonbackroom-deal. Winter 2013] COPYRIGHT VIGILANTISM 473 company121—and most of these providers have signed onto the MOU and will incorporate Copyright Alert into their contracts. This means that the only alternative for an individual who objects to Copyright Alert may be to go without Internet, an increasingly untenable prospect in today’s world. Although contracts of adhesion are not unenforceable as a legal matter, users may feel that Copyright Alert is being unfairly forced on them by their ISPs, undermining the perceived legitimacy of the program. Turning to the content of the plan, a number of procedural concerns arise. The United States Constitution provides that “no person shall . . . be deprived of life, liberty, or property, without due process of law.”122 Due process generally requires that a defendant receive notice and an opportunity to contest allegations against him or her before a court can render judgment.123 The Fifth Amendment is binding on the government, not on private actors, and the parties to the MOU therefore are not constitutionally bound to provide due process to Internet users accused of copyright infringement. Nevertheless, if copyright owners turn to Copyright Alert notices in place of the court system, Internet users may be concerned that they will no longer receive the same procedural protections against accusations of copyright infringement, and consequently will perceive the system as less legitimate. Copyright Alert requires that notices be sent to Internet users each time they are accused of infringement. These notices are intended to educate users about copyright infringement, but they serve the additional purpose of informing users of allegations against them and providing them with an opportunity to challenge accusations in court or through the private review hearing described in the MOU. However, the private review process is not available to users until after they have reached the mitigation measures step of the program.124 There does not appear to be any mechanism for users to challenge earlier notices without reaching the mitigation measures step. Even at the mitigation measures step, review is not an unconditionally guaranteed right. Users must pay a $35 filing fee for the privilege of invoking a review proceeding.125 The imposition of a filing fee on users challenging mitigation measures highlights another worrisome oddity about the Copyright Alert system. In a court proceeding, copyright owners are the plaintiffs paying a filing fee to bring a suit against Internet user defendants. Sanctions cannot be imposed against the user until after the copyright owner proves its case and earns a ruling of infringement. Under Copyright Alert, sanctions are imposed on accused infringers unless they themselves demand a review. Internet users thus become 121. See NATIONAL BROADBAND PLAN, ch. 4.1 (2010), available http://www.broadband.gov/plan/4-broadband-competition-and-innovation-policy. 122. U.S. CONST. amend V. 123. Mullane v. Central Hanover Bank & Trust Co., 339 U.S. 306, 313 (1950). 124. Memorandum of Understanding, supra note 67, at Attachment C, § 4.1.4. 125. Id. at Attachment C, § 4.1.6. at 474 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 the plaintiffs, the ones alleging a wrong, requesting relief, and paying a filing fee. This role reversal comes with an attendant shift in the burden of proof. Rather than requiring the copyright owner to prove infringement, the Copyright Alert review requires the Internet user to prove one of the outlined defenses.126 In effect, the user is deemed guilty until proven innocent, a burden made even heavier for the user by the reduction of all legal copyright defenses to the seven permitted in the MOU. Although the roles of plaintiff and defendant are effectively swapped in Copyright Alert review proceedings, a ruling in the Internet user’s favor does not entitle her to recover against the copyright owner who accused her or the ISP that wrongfully attempted to sanction her. The only effect of the review is to determine whether or not mitigation measures will be imposed on the Internet user. This has raised hackles in some quarters, with Internet rights activists demanding that copyright owners be held responsible for harassing users with erroneous Copyright Alert sanctions.127 Perhaps most disturbingly for opponents of Copyright Alert, sanctions are imposed and disputes resolved without any involvement of a judge or other representative of the legal system. This raises both legitimacy and competency concerns. During the six steps of the graduated response, legal determinations would be made solely by copyright holders or their representatives. In the MOU review proceeding, determinations would be made by AAA arbitrators relying on the copyright law expertise of a single advisor selected by the Administering Organization and approved by the CCI Executive Committee.128 Despite the MOU’s instruction that the review proceeding is to apply current copyright law “as determined by United States federal courts,”129 the form of copyright law applied in review proceedings is drastically altered by the artificial limitation of available defenses to infringement. Internet users are limited to the seven defenses listed in the MOU. This prevents Internet users from taking advantage of the full range of defenses available to them under the law. Users cannot argue that the work at issue is not copyrightable subject matter (under the merger doctrine, for example) or that the copyright owner’s claim is barred by the statute of limitations. Users can only claim that copyright on the work at issue has expired if the work was published before 1923, foreclosing any other argument that the work is in the public domain, such as if the copyright owner had failed to renew their copyright under the 1909 Copyright Act. The limitation of the available defenses radically alters the shape of copyright law, to the extent that the rights enforced under Copyright Alert are not the same rights protected by United States copyright law. In fact, taken from a theoretical perspective, purely private enforcement of 126. 127. 128. 129. Id. at Attachment C, § 2. See McSherry, supra note 121. Memorandum of Understanding, supra note 67, at Attachment C, § 6. Id. Winter 2013] COPYRIGHT VIGILANTISM 475 property rights in literary and artistic property is never enforcement of legal copyright. In our system of government, in which all power is derived from the electorate, only the legislature has the authority to set out legal rights, defenses, and remedies, and only judges and regulatory agencies acting under a statutory mandate have the authority to interpret the law and articulate it through common law precedents or regulations. Private adjudicators may arbitrate rights between two contracting parties, but they have no power to eliminate statutory defenses, change remedial schemes, or create common-law precedent. Copyright law encompasses the entire set of substantive, procedural, and institutional features derived from the Copyright Act and the Constitution. Interpretations of copyright law made by non-judges do not have the force of law, and enforcement of such interpretations is not, strictly speaking, an enforcement of copyright, although such interpretations may overlap to a large degree with legal rights. The legitimacy concerns raised above are not simply philosophical quibbles. Although a commitment to fairness and the rule of law is doubtless sufficient to justify complaints about the design of Copyright Alert, failures of legitimacy also measurably impact the effectiveness of enforcement schemes. In a study by Tyler, Chicago residents were surveyed about a variety of factors that might contribute to compliance with the law. They were then asked to report on how often they engaged in minor legal violations, such as littering, illegal parking, speeding, and shoplifting.130 A regression analysis showed that legitimacy, defined as a feeling that one has an obligation to obey the law and legal authorities, is independently correlated with compliance.131 Legitimacy was the second largest contributor to compliance overall, after personal morality. By contrast, fear of punishment (called “deterrence” by Tyler) contributed half as much as legitimacy to predicting compliance with the law.132 Other empirical studies have shown similar correlations between legitimacy and obedience to the law133 and between legitimacy and acceptance of legal rulings.134 People are more willing to acquiesce to the authority of legal actors and processes when they feel that these actors and processes are invested with legitimate authority. A series of studies beginning with work by Thibaut and Walker in 1975 shows that legitimacy, and subsequently compliance, are significantly dependent on the perceived fairness of the legal process.135 Tyler found that 130. 131. 132. 133. TOM R. TYLER, WHY PEOPLE OBEY THE LAW 40-45 (2006). Id. at 58-59. Id. at 60. See, e.g., C.R. TITTLE, SANCTION AND SOCIAL DEVIANCE: A QUESTION OF DETERRENCE (1980); H.B. Gibson, Self-Reported Delinquency Among Schoolboys and Their Attitudes Toward the Police, 6 BRITISH J. SOCIAL & CLINICAL PSYCH. 168 (1967); A. Sarat, Support for the Legal System, 3 AM. POLITICS Q. 3 (1975). 134. See, e.g., D. Jaros & R. Roper, The U.S. Supreme Court: Myth, Diffuse Support, Specific Support, and Legitimacy, 8 AM. POLITICS Q. 85 (1980). 135. See J. THIBAUT & L. WALKER, PROCEDURAL JUSTICE (1975); see also R. MACCOUN 476 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 15% of the variance in public opinions of the courts was attributable to the quality of treatment people felt they received from the courts, with only 3% attributable to whether or not they thought the court came to the correct result.136 Thibaut and Walker explained this correlation by arguing that people are more deferential to the law when they believe that they have some control over how it is applied to them.137 The opportunity for a fair and unbiased hearing is thus an integral part of peoples’ willingness to acquiesce to legal prohibitions and sanctions. Applying these empirical insights, even if Copyright Alert accurately and efficiently punishes infringers, failures of legitimacy are likely to limit its deterrent power. Internet users punished under the system are more likely to challenge their punishments than they would be if the system was perceived as legitimate, and those who have not yet infringed are less likely to be deterred. Although the risk of punishment will doubtless have an effect on the incidence of infringement, it will be far less than could be achieved if the system was imbued with the moral authority of state action carried out with procedural safeguards. As Pierre Lescure, the head of France’s “Future of Piracy” commission, has said in criticizing France’s HADOPI, “[i]f one starts from the penalty, it will fail.”138 Popular conceptions of legitimacy are the key to effective enforcement. In addition to increasing compliance, enhanced legitimacy could also reduce enforcement costs in the long run. Although additional process comes with costs, these could be recouped with the decreased resources that would be required for enforcement. In general, people refrain from shoplifting or vandalism, even when they do not face a high likelihood of punishment, because they have an internal sense that these behaviors are wrong, either for their own sake or because they are prohibited by a legitimate law.139 As alluded to above,140 current cultural norms have fostered online piracy and insulated it from moral reproach. If Internet users had an internal sense that infringement is wrong, they would self-police as people do when presented with the opportunity to steal. Establishing this moral intuition is not the same thing as educating Internet users; many Internet users are already aware that ET AL., ALTERNATIVE ADJUDICATION: AN EVALUATION OF THE NEW JERSEY AUTOMOBILE ARBITRATION PROGRAM (1988); R. Paternoster et al., Do Fair Procedures Matter?, 31 LAW & SOC’Y REV. 163 (1997); R. Wissler, Mediation and Adjudication in Small Claims Court, 29 LAW & SOC’Y REV. 323 (1995); KM Kitzman & RE Emery, Procedural Justice and Parents’ Satisfaction in a Field Study of Child Custody Dispute Resolution, 17 LAW & HUMAN BEHAV. 553 (1993); EA Lind et al., Individual and Corporate Dispute Resolution, 38 ADMIN. SCI. Q. 224 (1993). 136. Tom R. Tyler, Public Trust and Confidence in Legal Authorities: What Do Majority and Minority Group Members Want from the law and Legal Institutions?, 19 BEHAV. SCI. AND THE LAW 215, 226 (2001). 137. THIBAUT & WALKER, supra note 127, at 94. 138. Chirgwin, supra note 57. 139. TYLER, supra note 131, at 4. 140. See Part I.D infra. Winter 2013] COPYRIGHT VIGILANTISM 477 piracy is illegal. Nor does it require users to be convinced of the moral rectitude of the copyright law. It would be sufficient to make users feel that the copyright law is a legitimate law, and that punishments they receive under it are determined by a fair process. If they believe that, then at the very least they will be more willing to dutifully obey the law without the need for expensive notifications and Copyright Alert sanctions. C. The Challenges of Enforcing Copyright Alert The financial, logistical, and legal difficulties of enforcing the Copyright Alert system pose additional problems for copyright owners. Copyright owners and their representatives are aware of these challenges, but have resigned themselves Copyright Alert as a third-best alternative after enforcement through the courts and legislative reform both failed to address copyright owners’ concerns about piracy. Copyright Alert places a heavy financial burden on copyright owners, both in terms of the direct costs of identifying infringement and the opportunity or labor costs of diverting time and resources into enforcement rather than production. Under the MOU, copyright owners, the MPAA, and RIAA bear the full costs of identifying infringing IP addresses and notifying ISPs,141 as well as 50% of the costs of funding the CCI142 and 50% of the costs of the Independent Review system.143 This represents a rather large concession on the part of copyright owners, who have historically pushed for legislation imposing the burden of monitoring infringement on ISPs. The fact that Copyright Alert requires copyright owners and ISPs to privately fund their own administrative agency—the CCI—and an adjudicatory institution—the Independent Review system—only underscores the downsides of completely private enforcement. In effect, Copyright Alert requires private parties to foot the bill for an entire legal system to protect their rights. Copyright owners are also limited in the number of notices that can be sent to each ISP per month, a reflection of the financial burden on ISPs of responding to complaints of online infringement. A system that requires copyright owners to monitor the entirety of the Internet and still lacks the capacity to address all identified instances of infringement is not only burdensome, but moreover is inefficient. Even after copyright owners and ISPs expend the resources to identify and sanction an Internet user, there is the possibility that enforcement will be stymied in the courts. Rather than filing for the independent review proceeding described in the MOU, or even after a decision has been made in such a proceeding, Internet users may choose to challenge the sanctions imposed against them in court. In such a case, the courts are unlikely to give any 141. Memorandum of Understanding, supra note 67, at § 4(A). 142. Id. at § 2(E). 143. Id. at § 4(H)(ii). 478 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 deference to the outcome of a private review hearing. Although the decisions made in private arbitrations are typically given some deference by the courts, the MOU itself states that Copyright Alert reviews adjudicate only the issue of whether or not a Copyright Alert sanction should be imposed on an Internet user, not any of the other rights under copyright. In a lawsuit for copyright infringement, “neither the Subscriber nor the Copyright Owner shall seek to enter into evidence, or otherwise refer to or cite, either the fact of the Independent Review or any outcome of the Independent Review.”144 Similar language is found in the Uniform Domain Name Dispute Resolution Policy (UDRP) administered by the Internet Corporation for Assigned Names and Numbers (ICANN). ICANN is the organization responsible for maintaining the domain name architecture of the Internet.145 The UDRP is a private dispute resolution policy for adjudicating rights in domain names.146 In court proceedings filed after a UDRP proceeding had already occurred, the First, Second, Third, and Fourth Circuits refused to grant any deference or res judicata effect to the UDRP decisions.147 The Fifth and Ninth Circuits have both reconsidered de novo domain name rights previously adjudicated in a UDRP proceeding.148 In all cases, the UDRP was treated as only a convenient alternative to litigation, not a binding arbitration deserving deference. Decisions generated in review proceedings under Copyright Alert are likely to receive similarly dismissive treatment. Every determination made in a Copyright Alert review proceeding will face the possibility of complete de novo litigation in court, hobbling the speed and efficiency that make the system so attractive to copyright owners. In sum, the benefits of graduated response—more efficient enforcement, effective sanctions, and improved privacy protections for users—are undermined by the private nature of the Copyright Alert scheme. A contract can only be enforced as a contract; it cannot preempt federal copyright law. Should a United States judge with authority backed by the power of the United States government disagree with the finding of infringement made by the Copyright Alert system, copyright owners would be powerless to enforce their vision of how copyright should work. IV. THE HERO COPYRIGHT DESERVES: REGULATORY OVERSIGHT OF 144. Memorandum of Understanding, supra note 67, at § 4(H)(i). 145. See Welcome to ICANN!, ICANN, http://www.icann.org/en/about/welcome (last visited May 26, 2012). 146. See Uniform Domain Name Dispute Resolution Policy, (1999) ICANN, http://www.icann.org/en/help/dndr/udrp/policy. 147. Storey v. Cello Holdings, L.L.C., 347 F.3d 370, 381-83 (2d Cir. 2003); Barcelona.com, Inc. v. Excelentisimo Ayuntamiento de Barcelona, 330 F.3d 617, 623 (4th Cir. 2003); Dluhos v. Strasberg, 321 F.3d 365, 371-73 (3d Cir. 2003); Sallen v. Corinthians Licenciamentos LTDA, 273 F.3d 14, 28 (1st Cir. 2001). 148. GoPets Ltd. v. Hise, 657 F.3d 1024, 1027, 1029 (9th Cir. 2011); ISystems v. Spark Networks, Ltd., 428 Fed. Appx. 368, 370-71 (5th Cir. 2011). Winter 2013] COPYRIGHT VIGILANTISM 479 GRADUATED RESPONSE As described above,149 graduated response has great potential to improve efficiency and effectiveness in copyright enforcement. The challenges presented by Copyright Alert stem largely from its private, contractual foundations. The solution is to introduce a degree of regulatory oversight. Other countries, most notably France, have already had success with regulatory graduated response models. A regulatory agency could grant a graduated response approach much-needed legitimacy and legal weight, solve competence problems by opening up the possibility of judicial review, and relieve private actors of some of the burden of sustaining the system. Although regulatory involvement will doubtless introduce some delay and bureaucracy into graduated response, the result would still be more efficient than the current legislative stalemate and judicial quagmire. Furthermore, the usual objections to regulation, such as agency capture or federalism concerns, are not present in this context. A. The Role of Regulation Regulatory oversight could alleviate each of the weaknesses of Copyright Alert identified above.150 The question now becomes identifying administrative mechanisms that address these weaknesses without drowning the enforcement system in bureaucracy. A useful compromise approach would be to replace the Independent Review program outlined in the MOU151 with an administrative hearing overseen by a regulatory agency. Administrators in such a hearing would review notices in accordance with substantive copyright law. Procedure would be in accordance with the Administrative Procedure Act and regulations passed through Notice and Comment rulemaking. Decisions made by the regulatory agency could be appealed to an Article III court. Routing appeals to a state administrative body rather than to a private adjudicator alleviates the risk of bias and over-enforcement raised above.152 Although scholars frequently express concern that administrative bodies are subject to capture by special interests,153 that fear is quite minimal in the area of graduated response. The current system, Copyright Alert, is run entirely by industry interests. It is essentially captured by design. Although a risk of agency capture is always possible in a regulatory context, it cannot be more threatening than the current biases embodied in the design of Copyright Alert.154 149. 150. 151. 152. 153. See Part II infra. See Part III infra. Memorandum of Understanding, supra note 67, at Attachment C. See Part III.A infra. See George J. Stigler, The Theory of Economic Regulation, 2 BELL J. OF ECON. & MGMT. SCI. 3, 17-18 (1971). 154. See Part III.A infra. 480 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 The possibility of appeal to an Article III court would eliminate what remains of the competence concerns outlined above. Even where the legal expertise of an administrative agency fails, parties will have access to competent judicial authorities. Administrative involvement could also improve the effectiveness of enforcement under a graduated response scheme. Rather than forcing copyright owners and ISPs to maintain their own judicial system to enforce their legal rights, funding for administrative appeals would come out of the public fisc. This not only alleviates an inappropriate financial burden on these industries, but also leaves copyright owners and ISPs more resources to seek out infringers and respond to notices, increasing the overall reach of the program. The outcomes of administrative appeals also would be superior to private adjudications because such outcomes are entitled to deference in the courts. Unlike private adjudications, which are not binding and are owed no deference on appeal,155 courts are bound to defer to the legal interpretations of administrative agencies acting within the scope of their statutory authority.156 In contrast to the present state of affairs, parties dissatisfied with the outcome of the review process will not be allowed to simply disregard this outcome and take a second bite at the apple in the courts. Perhaps most importantly, administrative oversight would grant graduated response much-needed legitimacy. Instead of being imposed on Internet users from above, review procedures would be determined through the relatively democratic Notice and Comment rulemaking process required by the Administrative Procedure Act157 and would be required to conform with the constitutional guarantee of due process. Interested parties will be able to submit comments and criticisms on proposed procedures in a collaborative and transparent process. The law applicable on review would be the entirety of substantive copyright law with the exception of damages provisions. Internet users would have access to the full range of defenses to infringement and would not bear the burden of proof on the question of infringement. With improved legitimacy would come improved respect for copyright, if not as a moral imperative then as a legal obligation.158 Although the involvement of administrative agencies could slow the enforcement process and add red tape, by leaving the initial investigative and enforcement machinery in the hands of copyright owners and ISPs, the hallmark privacy and efficiency of the graduated response model would be preserved. Administrative hearings are unlikely to be significantly slower than private adjudications, and the tedious process of judicial review would only be 155. 156. 157. 158. See Part III.C infra. Chevron U.S.A. v. NRDC, 467 U.S. 837, 842-43 (1984). Administrative Procedure Act, 5 U.S.C. § 553 (2012). See Part III.B infra. Winter 2013] COPYRIGHT VIGILANTISM 481 necessary as a last resort. In sum, administrative oversight could give graduated response the strength and legitimacy that it lacks in its current form. With adjustment, the system can become not only efficient, but also effective and fair. B. Choosing an Agency All that remains is to identify the best administrative agency to oversee a graduated response program. Although there are several agencies with expertise in intellectual property or Internet communications, the Federal Communications Commission (FCC) is ultimately the best situated to oversee the review process I have described. The FCC already has expanded its regulatory authority into the domain of online communications with its network neutrality rules.159 The net neutrality rules, issued by the FCC in 2011, prohibit “[a] person engaged in the provision of fixed broadband Internet access service” from “block[ing] lawful content, applications, services, or non-harmful devices, subject to reasonable network management”160 or from engaging in unreasonable discrimination in “transmitting lawful network traffic over a consumer’s broadband Internet access service.”161 Mobile Internet providers are subject to a prohibition against “block[ing] consumers from accessing lawful Web sites, subject to reasonable network management.”162 The network neutrality regulations do not prevent ISPs from any “reasonable efforts” to “address copyright infringement.”163 Nonetheless, Copyright Alert may put ISPs afoul of net neutrality rules. If the Copyright Alert program errs in identifying an infringer, any throttling or termination of their Internet service could violate the rules. Limitation of Internet access as a punishment for copyright infringement is the flipside of the coin from violating the network neutrality rules. Every decision to throttle or terminate a user’s service is either a valid act of copyright enforcement or a violation of the rules. It seems only natural that Internet users dissatisfied with throttling or termination of their service under a graduated response scheme be able to turn to the FCC for review. If the FCC determines that a graduated response action was inappropriate, they can then consider whether there has been a net neutrality violation. Although not as experienced in copyright matters, the FCC has a large and well-established infrastructure for adjudicating disputes that arise under its regulations. Unlike the more specialized intellectual property agencies, such as the Patent and Trademark Office (PTO), the FCC arguably could proceed to 159. 160. 161. 162. 163. FCC Preserving the Open Internet, 47 C.F.R. § 8.1 et seq. (2012). Id. at § 8.5(a). Id. at § 8.7. Id. at § 8.5(b). Id. at § 8.9. 482 STANFORD TECHNOLOGY LAW REVIEW [Vol. 16:229 enforce a graduated response program without the need for new legislation. The FCC passed the net neutrality regulations under their traditional authority to regulate telecommunications networks, broadcast, and cable, as well as under section 706 of the Telecommunications Act of 1996, which directs the FCC to “encourage the deployment of ‘advanced telecommunications capability.’”164 No new legislation was passed conferring authority to regulate the Internet to the FCC. In the wake of the outcry over SOPA, Congress is currently paralyzed and incapable of passing new intellectual property legislation.165 The FCC’s ability to regulate in the Internet without new legislation enables them to bypass Congressional cowardice and implement new copyright enforcement on their own. There are other administrative agencies with expertise in intellectual property, but none possesses the combination of expertise in administrative adjudications and broad regulatory authority. Ironically, the Copyright Office is perhaps the organization least suited to oversee a high-volume enforcement campaign. Unlike most agencies, the Copyright Office is actually a part of the legislative rather than the executive branch. It operates as a division of the Library of Congress, with primary responsibilities focused on the registration of copyrights and recordation of transfers.166 Although it exercises rulemaking authority and even oversees adjudications on the subject of compulsory license rates,167 their involvement as a regulatory agency is quite limited. Delegating power over a graduated response program to the Copyright Office would require a vast new delegation of power by Congress. This could prove constitutionally problematic given separation of powers limitations on the legislative’s ability to delegate enforcement and judicial powers to itself.168 Even if such legislation were possible, the Copyright Office is not currently equipped to handle administrative review proceedings, especially not in the large volume that may be required for graduated response. Another possibility might be the Office of the Intellectual Property Enforcement Coordinator (IPEC). The position of IPEC was created in 2008 within the White House’s Office of Management and Budget.169 The responsibilities of the position are mostly related to “coordinat[ing] the 164. FCC Preserving the Open Internet, 76 Fed. Reg. 59192, 59214-59220 (Sept. 23, 2011) (to be codified at 47 C.F.R. pts. 0, 8). 165. See Part I.D infra. 166. United States Copyright Office: A Brief Introduction and History, U.S. COPYRIGHT OFF., http://www.copyright.gov/circs/circ1a.html (last visited July 1, 2012). 167. See 37 C.F.R. § 201 et seq. (2012). 168. See E. Fulton Brylawski, The Copyright Office: A Constitutional Confrontation, 44 GEO. WASH. L. REV. 1, 12 (1975). But see Terry Hart, Can the Copyright Office Regulate?, COPYHYPE (Nov. 4, 2010), www.copyhype.com/2010/11/can-the-copyrightoffice-regulate/#footnote_9_147 (arguing that the Copyright Office is actually controlled by the executive and therefore has all of the powers of an administrative agency). 169. About the Office of the U.S. Intellectual Property Enforcement Coordinator (IPEC), WHITE HOUSE OFF. OF MGMT. & BUDGET, http://www.whitehouse. gov/omb/intellectualproperty/ipec (last visited July 1, 2012). Winter 2013] COPYRIGHT VIGILANTISM 483 development” of the Joint Strategic Plan called for by the 2008 PRO-IP Act170 by providing organizational and logistical assistance.171 The current IPEC, Victoria Espinel, was one of the forces pushing for the development of Copyright Alert in the first place by encouraging dialogue between ISPs and the entertainment industry.172 Nonetheless, despite the unquestionable expertise of the office, it serves mainly as an organizer and facilitator for policy initiatives, and lacks both the rulemaking authority and adjudicative infrastructure to aid in the enforcement of a graduated response system. The PTO potentially is a promising option for providing administrative oversight to copyright enforcement. Like the FCC, it possesses strong organization and infrastructure as well as experience in overseeing administrative adjudicatory hearings. It also has great expertise in the realm of intellectual property, including copyright. The PTO has a Copyright Group that formulates copyright policy in conjunction with other organizations.173 Additionally, the PTO commonly assists in advising the executive on IP policy or preparing testimony for Congress on IP legislation.174 Although the PTO might otherwise be an ideal candidate to oversee a graduated response program, their involvement would require a new legislative grant of authority. In light of the current difficulty of legislative action in the intellectual property sphere, the FCC appears to provide a better option. CONCLUSION Graduated response has great potential to improve copyright enforcement online, and the addition of administrative oversight would only improve its effectiveness. Copyright owners and ISPs should not have to resort to vigilantism to defend their rights. By bringing together copyright owners and ISPs under the watchful eyes of the State, graduated response can harness their respective powers to create an enforcement scheme that both protects the rights of copyright owners and treats Internet users fairly. 170. 15 U.S.C. § 8111(b)(1) (2012). 171. Id. at § 8113(c). 172. Victoria Espinel, Safeguarding America’s Job Creating Innovations, WHITE HOUSE OFF. OF MGMT. & BUDGET (Mar. 30, 2012), http://www.whitehouse.gov/ blog/2012/03/30/safeguarding-america-s-job-creating-innovations. 173. Office of the Administrator for Policy and External Affairs—Copyrights, U.S. PATENT & TRADEMARK OFF. http://www.uspto.gov/ip/global/copyrights/index.jsp (last modified 9:05 AM, Mar. 14, 2012). 174. Office of Governmental Affairs, U.S. PATENT & TRADEMARK OFF., http://www.uspto.gov/ip/officegovaffairs.jsp (last modified 1:07 PM, Jan. 30, 2012).
© Copyright 2026