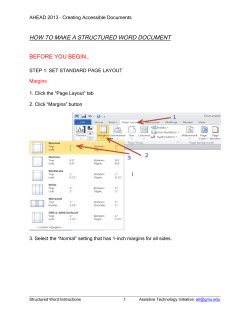
How to Make Everyone Hate You – Communication Skills for Security
How to Make Everyone Hate You – Communication Skills for Security and Governance Professionals Todd Fitzgerald, CISA,CISM, CGEIT, CRISC, PMP, ISO27000, CISSP, ITILv3f Director, Global Information Security ManpowerGroup, Milwaukee, WI Session 124 & 134 11/14/12 1-3:15 Las Vegas, NV Speaker Biography Todd Fitzgerald, CISSP, CISA, CISM, CRISC, CGEIT,is the Director, Global Information Security for ManpowerGroup. He is responsible for providing strategic information security leadership, policy, direction and working closely with local country security teams supporting 4,000 offices in 82 countries and territories to ensure information asset protection and compliance with global laws and regulations. Fitzgerald authored the 2012 book, Information Security Governance Simplified: From the Boardroom to the Keyboard”, and co-authored the 2008 ISC2 Press Book Entitled CISO Leadership: Essential Principles for Success, along with numerous other chapters for security publications, including the Official ISC2 Guide to the CISSP CBK. Todd has spoken frequently and chaired national/international conferences for ISACA, CSI, ISSA, MISTI, COSAC, HIMSS, HIPAACOW, CMS and others. He has previously held senior information technology leadership positions with Fortune 500 organizations such as WellPoint (National Government Services), AstraZeneca (Zeneca), Syngenta, IMS Health, American Airlines and Blue Cross Blue Shield United of Wisconsin. About ManpowerGroup • World Leader in Innovative Workforce Solutions • Most Admired in Industry • $22 Billion Company, Fortune #138/500, NYSE:MAN • 4,000 Offices in 82 countries • 30,000 Employees • 65% of revenues outside the US • 3.5 Million placements in permanent, temporary and contract positions • World Headquarters – Milwaukee, WI A Little ‘Presentation Disclaimer’ … The opinions expressed are solely the opinions of Todd Fitzgerald and do not necessarily represent the opinions of his employer. You may or may not want to adopt the these concepts in your organization. Use a riskbased approach before attempting this at home. Today’s Objectives… • What Does My Age Have To Do With It ? • Who Do You Think You Are ? Who Are Those %$%#$! People That Work With Us? • Soft Stuff and My Body Ain’t Talkin! • Obama and Romney Are The Only Ones Who Care About Politics, Or Should We? What Does My AGE Have To Do With It ? Trends Changing the World of Work One Size Fits One Traditionalist Boomer Born 1928-1945 Born 1946-1960 Generation X Generation Y Re-Generation Born 1961-1979 Born 1980- 1995 Born 1996 - Each generation approaches work differently, shaped by the economic, social and political forces of their time ultimately forming their individual preferences. 7 | © 2011 Tamara J. Erickson and Moxie Insight. The United States Population Pyramid Source: International Data Base, U.S. Census Bureau Iconic Generational Moments Traditionalists: Born 1928 to 1945 Traditionalists shared experiences of the 1940s and 1950s in the United States: Allied military success in World War II The early days of the Cold War A wave of new technology Booming Post-War economy Growth of suburbs Increased availability of consumer goods © 2011 Tamara J. Erickson and Moxie Insight. All Rights Reserved. What Are The Implications For Communications (Work Approach, Technology, Verbal, Feedback Needs, Work/life Balance, Rewards) These Experiences Produce? Iconic Generational Moments Boomers: Born 1946 to 1960 Boomers shared experiences of the 1960s and 1970s in the United States: Kennedy’s “Camelot” Presidency The Cuban Missile Crisis Assassinations of Kennedy, King, and other idealistic leaders Vietnam Civil Rights Women’s liberation Widespread protests Watergate and Nixon’s resignation Lots of other Boomer teenagers! © 2011 Tamara J. Erickson and Moxie Insight. The 1967 Man of The Year What Are The Implications For Communications (Work Approach, Technology, Verbal, Feedback Needs, Work/life Balance, Rewards) These Experiences Produce? Iconic Generational Moments Generation X: Born 1961 to 1979 Generation X’s shared experiences of the late 1970s through the Mid-1990s in the United States: Troubled economy Widespread layoffs from reengineering Women entering the workforce Rising divorce rates Challenger shuttle disaster Era of “Greed is Good” CNN and electronic games The first Gulf War © 2011 Tamara J. Erickson and Moxie Insight. What Are The Implications For Communications (Work Approach, Technology, Verbal, Feedback Needs, Work/life Balance, Rewards) These Experiences Produce? Iconic Generational Moments Generation Y: Born 1980 to 1995 Generation Y Shared experiences of the Mid-1990s through the late 2000s in the United States: Terrorism: 9/11, World Trade Center, Oklahoma City School violence: Columbine Ubiquitous technology Clinton’s sexual indiscretions Working mothers Pro-child culture © 2011 Tamara J. Erickson and Moxie Insight. What Are The Implications For Communications (Work Approach, Technology, Verbal, Feedback Needs, Work/life Balance, Rewards) These Experiences Produce? $h*! Gen Y’s Say* Can I bring my iPhone, iPad and Mac to work and use this? Can I text my manager if I am sick rather than call in? Do I have to wear shoes to work? Do you drug test often? Do I have to show up each day? Can I friend my manager on Facebook once I get hired? How long will it take to become next CEO? Does your company have game room, nap room, sports team? Can I access Facebook and Twitter at work? Do I really need to be on time? Is it ok to be 15-30 late each day? *Not the Actual Name of the Survey Source: Workplace 2020 Important Differences Around the World The U.S. China Brazil Traditionalists Joiners Respectful Fiscally conservative Hard-working Idealistic Cautious Modest Respectful Risk-averse Boomers Competitive Anti-authoritarian Idealistic Authoritarian Loyal to the Party Work as service Consumers Politically cautious Idealistic Generation X Self-reliant Mistrustful Dedicated parents Sacrificing for the common good Dedicated children Self-reliant Wary Family-centric Generation Y Immediate Optimistic Digital natives Family-centric Immediate High self-esteem Digital natives Materialistic Immediate Optimistic Digital natives Financially driven For Example . . . © 2011 Tamara J. Erickson and Moxie Insight. All Rights Reserved. Gen Z Enters the Workplace in a Decade Shared experiences and predictions about their future work life: • They have grown up with shortages. – Energy – Water – Money • Their work life will be different – – – – – Technology will replace jobs faster. They will work for more women executives. Work will be more virtual and lonely. Their career(s) will be many and long. Their focus will be on renewal. The Shift, the future of work is already here, Moxie Insight World Map According to Land Distribution in 2011 Source: WorldMapper ManpowerGroup Proprietary Information World Map According to Population Distribution in 2050 Source: WorldMapper Leading a Multiple Generation Workforce Don’t Judge Appreciate Differences Build Trust Embrace Diversity Changing Workforce, Changing View of The World THEN • Cubicle Slavery • Job For Life • Personnel file at Big company • • • • Do What You Are Told Competence Corporation Peers Work with the same folks day in and day out • Become the boss (after 25 years) • Goal: Get through the day • Know the “ropes” Source: Tom Peters Essential Series “Talent”, 2005 NOW • • • • • • • • • • Free Agent Gig for Now Temp Assignments Do what you excel at Mastery Peers in my craft Shifting network of partners Be the boss (now) Goal: Get things done Learn to Bungee Jump The Generational Differences Will Impact Future Communications • Baby Boomers (1946-60) loyal, dependable, workaholics • Gen Xers (1961-1979) independent, reject rules • Gen Y (1980+) short attention span, tech savvy Soft Stuff and My Body Ain’t Talkin’ Gartner Research Says The CISO… Source: Emerging Role and Skills For the CISO Gartner Report • Balances needs of the business with – Increased regulated controls – Increased complexity • Translates “technical speak” • Has a solid background – 5-7 Years Information Security – Additional IT Background • Thinks strategically, Politically Savvy • Knowledgeable of key aspects of business • Possesses certification “Techie” Core Competencies Analytical Problem Solving Tool Expertise Best Practices Industry Standards Technical Knowledge Team Work Emerging Technologies Crisis Mgmt Leadership Competencies Interpersonal Self-control Awareness Self-control Perseverance Adaptability Technical Competency Security/Audit/ Compliance Leadership & Managerial Competency Results-Oriented Flexibility Initiative Self-Development Critical Efficiency Orientation Information Seeking Thoroughness Non-Technical Core Competencies Financial/ Vision Budgetary Leadership Interpersonal Influencing Effectiveness Skills Customer Team Focus Work Conceptual & Written/Oral Strategic Communication Thinking Important Security Leadership Skills Self Confidence 65% Oral Communications 74% Written Communications 74% Influence 69% Teamwork 68% Source: Fitzgerald/Krause CISO Survey, CISO Leadership Skills, 2008 ISC2 Press Career Path Decision Point: Techie or CISO Differences In Thought Processes Technical • Technical challenge • Concrete non-ambiguous solutions • Task-oriented • Mastery of technical skill • Hands-on training focus • Documentation aversion • High level of individual contribution • Meetings are distractions Technical Expert Chief Information Security Officer Career Path Decision Point: Techie or CISO Differences In Thought Processes ? Managerial • Business relationships • People-oriented Technical • Consensus building Expert • Many presentations • Influence Chief • Team building Information • Accepting ambiguity and Security uncertainty Officer • Meetings, meetings, Meetings! • Oral communication with all organizational levels Let’s Assume.. We Are Creating A New Team Question #1 What Department Do You Want On Your Team ? Question #2 What Perspective Do They Bring ? Question #3 What Level of Individual Should Be Involved ? Soft Skills of The Security Leader Are Need To Manage The Team • Excitement • Trust building Forming Phase • Draw out opinions • Patience, permit dialogue Storming Phase • Doubt Surfaces • Team Divisions • Rules of behavior • Dissention critical Norming Phase • Role acceptance • Individual contribution respect • Team emerges • Focus on meaningful work Performing Phase • Functioning unit • Attention to deadlines • May regress • New members, new perspectives Communication To Executives– Present In Understandable, Organized Business Terms 2002 2003 2004 2005 2006 2007 How Does The Mobile Commuting Trend Impact Communications ? • “Office less” work-athome • Telecommuters • Road Warriors • Employees at work working in distributed environments • After hours work at home 41 12 Roadblocks to Effective Listening • • • • • • Comparing Mind Reading Rehearsing Filtering Judging Dreaming • • • • • • Identifying Advising Sparring Being right Derailing Placating Source: McKay, M How to Communicate: The Ultimate Guide to Improving your Personal and Professional Relationships Body Language • • • • • Not an exact science Facial expressions Touching Eye contact key aspect Enables better self-awareness and self-control • Several signals more reliable 6 Universal Facial Expressions • • • • • • Happiness Sadness Fear Disgust Surprise Anger Who Do You Think You Are? Who Are Those $%%#$! People That Work with Us? The 4 Dimensions of Personality Type How People Are Energized (E) Extroversion Introversion (I) The Kind of Information We Naturally Pay Attention To Intuition (N) (S) Sensing How We Make Decisions Feeling (F) (T) Thinking How We Organize Our World (J) Judging Perceiving (P) 4 Letters = 16 Different “Personalities” ISTJ ISFJ INFJ INTJ ISTP ISFP INFP INTP ESTP ESFP ENFP ENTP ESTJ ESFJ ENFJ ENTJ GETTING ENERGY:Outer World (Extraverted) vs. Inner World (Introverted) EXTRAVERTS (E) Seek Interaction Enjoy Groups Act or speak first, then think Expend energy Focus outwardly Talkative Energy! Like variety and action Outgoing Think out loud Enjoy discussing, Gregarious Breadth GETTING ENERGY:Outer World (Extraverted) vs. Inner World (Introverted) Introverts (I) Like to be alone Enjoy one-on-one Think first, then speak or act Conserve Energy Focus Inwardly Quiet Like To Focus on on thing at a time Reserved Think To Themselves Enjoy Reflecting Depth Spotting An Extravert or Introvert.. Introverted Enthusiastic demeanor Talk more, animated, faster, louder Easily distracted Change subjects quickly Seek center stage Interrupt and finish sentences Act first, think later Calm, measured demeanor More reserved, talk less Think, then talk, slower Focus their attention Stay with one subject at a time Shun the limelight Cautious and hesitant Like to spend time alone GATHERING INFORMATION: Sensing(S) or Intuition (N) Sensing (S) Prefer facts Concrete data Actual Pay attention to specifics Practical, realistic, “down to earth” Present focus Value common sense Pragmatic Intuition (N) Prefer insights Abstract information Theoretical, possibilities Focus on big picture Inspired, imaginative, “head in clouds” Future focus Value innovation Speculative Sensing and Intuition Clues: The Forest or The Trees ??? Intuition Sensing 65% of population Clear, straightforward speech Sequential thoughts Literal, facts examples More aware of bodies Attracted to practical jobs Prefer nonfiction reading Remember past accurately Listen until others complete thought Sensing and Intuition Clues: The Forest or The Trees ??? Intuition Sensing 35% of population Complex speech compound sentences, Roundabout Thoughts Figurative, metaphors, analogies Attracted to creative jobs Prefer fiction reading, Graduate Degrees Repeat themselves, rephrase Talk about big picture, Envision Future Finish others sentences MAKING DECISIONS:Principles (Thinking) or Values (Feeling) ? Feeling (F) Thinking (T) Firm-minded Objective, convinced by logic Laws, Justice, Policy Analytical, Clarity Decide with their head Some view as insensitive Good at critiquing Detached, Direct Don’t take things personally Gentle-hearted Subjective, convinced by values Humane, Social Values Appreciative, Sympathetic Decide with their heart Some view as overemotional Good at appreciating Involved, Harmony, Tactful Usually take things personally Finding the Thinker.. Pros and Cons Cooler, more distant May be blunt, tactless, insensitive Businesslike, get to the point More “thick skinned” Appear low-key, matter-of-fact Give praise sparingly Assertive, impersonal language Often engaged in jobs of strategy May argue, debate for fun 65% chance they are male Finding the Feeler, How Others Are Affected? Warmer, friendlier Sensitive to feeling, gentle, diplomatic Engage in social niceties Engage in small talk first Appear excited, emotional Generous with praise Lack assertiveness “Value” words, lots of them Often in helping jobs 65% chance they are female ORGANIZING OUR WORLD AND LIVING OUR LIVES:Planning It (J) or Letting It Happen (P) Judging (J) Seek closure, things settled Value structure, goals Plan ahead Like order, scheduled Work now/play later Enjoy completing projects More Structured Perceiving (P) •Seek openness •Value the flow, Adapt •Like flexibility, tentative •Process-oriented •Spontaneous •What deadline ? •Play now/work later •Like to start projects •More easygoing •Flexible Spotting The Judger Judging Formal, conventional, serious Quick Decisions Perceiving Take charge, in control,in a hurry Dress more for appearance, straighter posture Neat car interior Like rules, systems, structure Make lists, organized Straighter posture, walk faster Seek jobs that give them control Tidy, neat workplaces Spotting The Perceiver Casual, unconventional MoreJudging playful, good at adapting Procrastinate, put off decisions Leisurely place Dress for comfort, may slouch Messy car interior Rules, systems are confining Make lists, seldom finish May walk slower Seek jobs that are fun Perceiving Putting It All Together… ISTJ LIFE’S NATURAL ORGANIZERS ISFJ COMMITTED TO GETTING THE JOB DONE INFJ AN INSPIRING LEADER AND FOLLOWER INTJ LIFE’S INDEPENDENT THINKERS ISTP JUST DO IT ISFP ACTION SPEAKS LOUDER THAN WORDS INFP MAKING LIFE KINDER AND GENTLER INTP LIFE’S PROBLEM SOLVERS ESTP MAKING THE MOST OF THE MOMENT ESFP LET’S MAKE WORK FUN ENFP PEOPLE ARE THE PRODUCT ENTP PROGRESS IS THE PRODUCT ESTJ LIFE’S NATURAL ADMINISTRATORS ESFJ EVERYONE’S TRUSTED FRIEND ENFJ SMOOTHTALKING PERSUADERS ENTJ LIFE’S NATURAL LEADERS Source: Type Talk At Work, Otto Kroeger with Janet M.Thuesen Effective Communicaton Appreciates and Leverages The Differences E S T J Tailored Security Message I N F P Obama and Romney (or is it Romney and Obama) Are The Only Ones Who Care About Politics… Or should We ? THE WHITE HOUSE NEEDS A SECURITY GUY VOTE FOR TODD... OR AM I TOO LATE? Just Like The Winchester House… “All organizations are perfectly aligned to get the results they get.” - Arthur W. Jones, The 8th Habit By Steven Covey. EVERY Organization Has A Culture, Intentional or Accidental Geography Collaboration Trust Level Hierarchical Bureaucratic Hidden Agendas A C L U I L G Strategies T N U M R E E Action Plans N T Vision Lead By Edict Or Example Cost Cutting Vs Innovator Risk Appetite Celebrate Teams Or Individuals Company Size Industry How Much Do You Know About Your Organization ? • Who talks to whom? • Who talks first? For how long? What are their agendas? • Who are the insiders? • What are their views? What stories do they share? • How do people around you get things done? • What are their motives and attitudes on work issues? Source: It’s All Politics, Kelley Reardon How Much Do You Know About Your Organization ? • Whose side are they on and is it yours? • What inconsistencies are in their words and behaviors? • That types of behavior are rewarded and by whom • What organizational fictions are passed around, and what happens to people who buy into them ? • Are you on the inside track? Source: It’s All Politics, Kelley Reardon Key Savvy Behaviors • • • • • • • • • • Be aware Establish long-term goals Establish at-the moment goals Develop allies Offer favors, pay back favors Build an organization Be a good team player Know your legend Be resilient Have a meeting before the meeting • • • • • Make your boss look good Share the glory Pick your battles wisely Get a reputation Get in the information loop • Don’t confuse the company with your family • Depersonalize Source: Ciso Leadership Skills: Essential Principles for Success Fitzgerald/Krause (2008), How Savvy Are You? Billi Lee Matching Response to Personality PERSONALITY Forceful YOUR RESPONSE Speak with conviction Brusque Down-to-earth Antsy Perfectionist Irascible Charming Sensitive Hands-on Brief comments to hold attention Practical data and examples Provide reassurance not problems Assure loose ends considered and dealt with Choose timing carefully before request Enjoy their repartee Avoid drawing attention to shortcomings Demonstrate your ability to roll-up sleeves and do what is needed Ironclad data, don’t focus on feelings Insecure Communication Final Thoughts • Communication has many dimensions – Generations – Soft Skills/Body Language – Personality hard-wiring – Political Skill • Develop strengths; mitigate weakness • Get feedback [email protected] [email protected] www.linkedin.com/in/toddfitzgerald Thanks For Your Participation!!!! Available Jan 2012 at Amazon & Barnes & Noble Collaborate – Contribute – Connect http://www.isaca.org/Knowledge-Center The Knowledge Center is a collection of resources and online communities that connect ISACA members – globally, across industries and by professional focus - under one umbrella. Add or reply to a discussion, post a document or link, connect with other ISACA members, or create a wiki by participating in a community today! This is a pre-publication draft of Chapter 12 for the book Information Security Governance Simplified: From the Boardroom to the Keyboard by Todd Fitzgerald (Auerbach, 2012). The complete book may be ordered from Amazon.Com or Barnes and Noble websites. 12 EFFECTIVE SECURITY COMMUNICATIONS The meeting of two personalities is like the contact of two chemical substances: if there is any reaction, both are transformed. Carl Gustav Jung, 1875–1961 Why a Chapter Dedicated to Security Communications? If the phrase security communications conjures thoughts of the network, protocols, blocking, terminating communications, ensuring messages get from point A to point B intact, and must be available 24/7, you are correct. However, the topic is not about computer communications but rather human communications. Information security governance depends upon humans to deliver the right message to the right individuals at the right time in the right manner for the messages to be heard and acted upon. Imagine for a moment that the information security department creates a plethora of security policies representing the equivalent of creating the Mona Lisa to an artist or creating a team of athletes that wins the Super Bowl. Imagine then that what would have happened if no one had ever seen the Mona Lisa that was stored in an attic or the team that was capable of winning the Super Bowl never showed up for its games? A similar fate can fall upon the information security program if information security policies, ideas, and initiatives are not properly communicated. True information security governance may look good on paper, with policies drafted and technical solutions appearing to be in place, but if these are not communicated properly, security governance is really not occurring. 305 .LQGE 30 306 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Security communication takes on many forms such as the publishing of information security policies, selling the next information investment to management, explaining the current status of security audit issues to the board of directors, crafting security e-mail messages of the latest security concerns, or simply having a conversation about a security issue with a security colleague or business unit manager. It should be clear that every communication by every individual associated with the information security team has the potential to either (a) provide increased credibility and support to the information security program or (b) cause the information security area to be viewed as a roadblock or lessen trust that the security group has the organization’s best interests front and center. Communication skills are constantly evaluated as we are growing up—from formal penmanship, written communication skills, listening skills, plays well with others, and speaks up when called upon as a child to the formal performance reviews where written and oral communication skill competencies are evaluated on an annual basis. The continuous evaluation of these skills indicates the importance of them. After all, how effective can we be in the workplace if we cannot effectively communicate with others? Hence, due to this importance, this chapter is dedicated toward how security professionals can improve their communication skills to convey the appropriate security messages throughout the organization. Different aspects of communication are explored and by understanding the different communication styles that are occurring within the company, the security executive and professional can be more effective in constructing and delivering the appropriate message. End User Security Awareness Training One of the debates over the past decade has been whether information security awareness training has been effective. Much of this concern is generally started from an analysis of the number of security incidents in a given year and then concluding whether the end users were receiving the message and acting in a secure manner in their day-to-day jobs. The conclusion then usually suggests that technical controls need to be implemented to take out the risk of “human error.” Unfortunately, these conclusions are made without the benefit of a scientifically controlled experiment, whereby the “test group” of users .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S AU: Does “they” refer to the test group? 307 of the same organization received no security awareness training were evaluated against a “control group” in which they were to determine whether there would have been more or less incidents experienced by the control group. Obviously, technical controls are very important to the information security program, and are necessary to address the aspects such as antivirus, encryption, firewalls, security mechanisms, physical security, authentication, and monitoring, but given that technical controls cannot fully address the end-user behaviors, security awareness training must be in place to reduce the risk. Information also comes in nontechnical forms (oral and paper documents) that cannot be secured by technical means or without the diligence and assistance of the end user. For example, a policy may state that all documents transported between the office and home need to be transported in a locked container. If the end user is not aware of the policy or does not understand the rationale for the policy, she might decide it is not necessary and not place the documents in a locked box. Alternatively, an individual may load boxes of documents in his car in the wintertime, leaving the engine running to keep it warm while hr runs back into the house to retrieve more boxes for loading. Meanwhile, the end user may be taking an increased risk that the car will be stolen and the confidential documents exposed. Since there are no technical controls to prevent this (other than the end user locking the door in between trips), security needs to be continuously reinforced with the end user to reduce the risk of this type of error. Awareness Definition Security awareness training is different from security training. The National Institute of Standards and Technologyy (NIST) provides the AU: Where is definifollowing definition: tion from? Web site? Document? Awareness is not training. The purpose of awareness presentations is simply to focus attention on security. Awareness presentations are intended to allow individuals to recognize IT security concerns and respond accordingly. In awareness activities, the learner is the recipient of information, whereas the learner in a training environment has a more active role. Awareness relies on reaching broad audiences with attractive packaging techniques. Training is more formal, having a goal of building knowledge and skills to facilitate job performance. .LQGE 30 308 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED In short, the basic objective of security awareness training is to (1) provide enough information to the end users as to what they and others should and should not do and recognize what would constitute a security incident, and (2) know what they should do if they recognize or suspect that a security incident has occurred. If these two objectives have been met, then the information security awareness program has been successful. Delivering the Message Information security programs fall short of the message when the security message is not crafted in a manner that grabs the end users’ attention or fails to provide them with the necessary information. Let’s face it, many security people progressed to higher levels within the organization due to their technical abilities, not based upon their communication or marketing skills. Providing information security awareness is essentially marketing—inducing the recipient of the message to buy something (in this case buy into) what they ordinarily may not have thought to buy on their own. Savvy marketers craft the message not in pages of boring technical, jargon-filled presentations, but rather in short, high-impact, sound-bite type messages that grab our attention and are retained. Security professionals must do the same. The following seven steps, adapted from NIST security awareness guidance, provide a process for delivering an effective information security program. Step 1: Security Awareness Needs Assessment Assessing security awareness is often an overlooked step when first implementing a security awareness program. Without knowing where the highest risk areas or areas that have been causing the most incidents are, valuable time with the end users could be wasted. The needs can be determined from multiple sources, as described next. If the organization is rolling out a new identity management system or a new incident reporting process, this may be a good time to explain how this will work. Or a new law or regulation could mandate new reporting requirements that would need to be communicated. New or Changed Policies .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 309 Past breaches can provide a wealth of information from which to construct the security awareness program. These are also very useful in obtaining the end users’ attention, as it demonstrates that security issues are occurring within their organization versus a theoretical concept that “this could happen.” It also reduces the likelihood that the end user will think that the security department is sensationalizing the news. Care should be taken when presenting actual incidents within the company that it is not possible for the end users to deduce the person or in which department that the individual was working. This could cause some ethical and legal issues in disclosing personal human resource issues. The objective is to explain the incident so that the same type of incident does not reoccur through someone else’s behavior. Incidents of the same type that have a high number of occurrences would be excellent candidates for targeted security awareness training. Past Security Incidents Systems Security Plans Systems security plans (SSPs) document the current state of an information security system and can take the form of a major application (MA) or general support system (GSS). Since these plans define the overall business objective of the system, the infrastructure, and the managerial, technical, and operational controls required to support the system, these documents can provide excellent sources of the types of information that needs to be shared with the end users. For example, if there are many business partners that are part of the infrastructure, the end users may need to be made aware of which email communications are secure or what is permissible to discuss with the business partner due to intellectual property rights that are defined in the systems security plan. Audit Findings and Recommendations If there are recurring audit issues that have not been mitigated, these should be included in the security awareness training. Since auditors cannot audit 100% of everything, samples are taken that represent a statistical significance if an issue is found. The issues found may or may not have occurred across every department; however, that does not mean that the issue is not broader than the audit issue found. For example, the auditors may pull a sample of policies and procedures and determine that they have not been updated on an annual basis for a couple of departments. .LQGE 30 310 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Odds are, just as when a pest exterminator sees one mouse, there are likely to be many more, so is it likely that other areas have not been following the process of annual updates. Typically these are issues of security governance across the organization; the tone at the top has not made this a priority or there have not been the processes in place to monitor and ensure this is completed on an annual basis. Repeat audit issues should always be addressed either to a targeted group or broadly across the organization, depending upon the issue. Similar to security incidents, event analysis of the monitoring logs can highlight areas of concern. These are likely to evolve into targeted training more than security awareness training. For example, logs indicating that firewall vulnerability is repeatedly being exploited by external hackers may indicate the need to train the network group on device configurations. Event Analysis Industry Trends Introduction of new technology into the marketplace can provide a rich source for discussion. Discussing the use of social media in the workplace, such as Facebook, LinkedIn, or Myspace, will provide relevant discussion of issues that most end users can relate to. Alternatively a discussion of the use (or nonuse) of personal e-mail and the acceptable use policy to govern appropriate Internet behavior will be of interest to the end users. The security officer has to keep abreast of the current industry trends to ensure that the risks are mitigated, as new technologies are often released first and then security controls are added second. The reality of this situation is that products are usually in a race to become the first to capture market share and may not have implemented the necessary security controls. As an example, consider the evolution of the Windows operating system and how it took almost nine releases over a period of more than two decades to build-in many of the security concepts that are expected today. Managers should be polled to determine what issues they are aware of that need more focus. They may be concerned with documents not being properly disposed or laptops not being put away at the end of the day or securely transported. Management Concerns .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 311 After reorganizations, employees are oftentimes reporting to a new manager that may operate differently. This is a good time to reinforce the security concepts. Locations may have closed during the reorganizations or whole departments eliminated, thus creating potential changes in the security procedures. Organizational Changes Step 2: Program Design Communications can either happen through the best intentions or be designed. By approaching the security awareness program as something that must be designed, the chances of leaving out critical components are lessened. A car would not be produced without a design; a TV show would not be delivered without a script to guide the flow of the contents. A cliché in providing presentations is to know your audience. The security awareness presentation delivered to a group of airline mechanics may be different than to a group of customer service representatives. The analogies or stories used in the presentation to connect with the audience may be different. For example, relating the information security concepts of physical protection to ensure that no unauthorized people are in the hangar that could cause loss of life by tampering with the airplane engine parts may be effective with the airline mechanics. The customer service representatives may relate to the importance of verifying the caller with identifying information so as to not release confidential information to the wrong person. Alternatively, talking about sending faxes to the wrong healthcare provider would have little relevance to the airline mechanics. Target Audience Security awareness training should be performed minimally once a year and preferably during a time in the business cycle that will not cause an increased burden in meeting the company objectives. For example, having a training session for a group of accountants at fiscal yearend or right before tax season would not be welcomed. If face-to-face sessions are used, scheduling of the sessions needs to be planned so that there is ample time for individuals to plan the training into their schedules. Frequency of Sessions .LQGE 30 312 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Face-to-face sessions work best when the number is kept to 30 or less. A group of this size allows for interaction and more exchange of information between the participants. Schedules should be drawn up 6 to 8 weeks in advance of the training to ensure the greatest attendance and to obtain the appropriate facilities. Number of Users Face-to-face sessions work best, however, these are also time consuming, as multiple sessions are needed to cover the workforce in groups of 25 to 30 people. The security officer and his staff have to dedicate significant resources to this task, especially if the associates are spread out across multiple locations. As a result of cost reductions, some security departments have gravitated to online learning management systems to deliver PowerPoint-type contact to the end user. The difficulty with this approach is that users may simply click through the material without providing their full attention, which is much harder to do in an interactive security awareness session. Even though quizzes can be incorporated into the material to determine whether the end user was paying attention, it is difficult to ascertain if the end user was truly engaged. The more engaged the participants in the learning process, the greater the likelihood that the material will be retained. Method of Delivery The labor, materials, locations, and budget required for the program need to be reviewed. At this stage the full costs may not be known, however, the budget parameters should be determined. It would not be unreasonable to spend 1% to 2% of the information security budget on security awareness training and a greater percentage on a small budget. Resources Required Step 3: Develop Scope The security awareness program must be scoped or there is a risk that the message will be lost in delivering the training. Scoping utilizes the needs assessment captured in step 1 and determines what topics are provided. Once the scope of the training has been initially defined, the population that is required to attend Determine Participants Needing Training .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 313 or participate in the training needs to be defined. Depending upon the company desire or the law or regulation, all employees, including contractors requiring systems access may be subject to the training. If a subcontractor relationship exists with another firm that is performing work on the organization’s behalf, then it should be determined whether the subcontractor should provide its own security awareness training (as the subcontractors are employees or contracted to that firm) or should the company that hired the subcontractor require the security awareness training provided to its own employees. New hires present a special situation that must be addressed. The organization may require annual refresher training for the existing employees and contractors, but the new hires also need the security awareness training from day one. New hires should not be allowed access to the system until they have had some form of security awareness training. One technique that is very effective is to have the hiring manager provide security awareness training to the employee (e.g., in the form of a PowerPoint presentation); have the employee sign an attestation that they have read the security requirements, understand them, and will abide by them; and have the manager fax or e-mail the signed copy to the security administration or access management department or whichever department is responsible for account establishment. Once the fax or e-mail is received, then the department can release the login ID and password to the manager to provide to the employee. The employee would then log on and change the onetime password. In this manner, the new hire has the appropriate onboarding security awareness training that may not line up with the scheduled annual awareness training, which they would take during the next cycle with everyone else. Business Units Security awareness training is generally developed for the current cycle (i.e., annual training) and provided to everyone in the organization. However, there may be special situations where the training is customized to a particular department because of different concerns. Select Theme One of the most important aspects in designing a security awareness program is to select a theme for the training. A list of themes is shown in Table 12.1. This helps to focus the training around a subject and keeps the scope from drifting. Selecting a theme .LQGE 30 314 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Table 12.1 Security Awareness Themes Appropriate Internet usage E-mail security Social engineering Viruses, worms, Trojans, malicious code Identity Theft Incidents and incident response Tablet computing Need-to-know access Wireless security Copyright protections and licensing E-mail etiquette Clean desk policy Handling of protected health information or credit card data Latest information security events in the news Spyware Phishing attacks Confidentiality, information sensitivity Shoulder surfing Spam Smartphones Individual security responsibility Home network usage What is risk? Government regulations Laptop security Password management Protecting yourself and your company in a disaster Obtaining access to information does not limit the creativeness of the training, but rather permits the designer to build the program around a common concept while introducing other security-related items into the program. For example, while constructing a security awareness training program using the theme “Internet and Email Security,” the concepts of antivirus, confidentiality, non-sharing of passwords, encryption, phishing, and Web site malware can be introduced into the training. The common mistake is that the fire hose method of security awareness education is used, and all possible aspects of security are communicated during a 1 to 2 hour presentation or during a webinar. The end users eyes glaze over and little is retained other than “be sure to not let someone piggyback behind you when walking in the building” or “hit CTL–ALT–DELETE and Lock when stepping away from the computer.” The themed approach avoids this scenario. Step 4: Content Development Once the theme is chosen for the security awareness training, the content should be developed to be as impactful as possible to achieve the highest retention rate after training. Face-to-face training affords the ability to combine video, music, props, and attendee interaction to create an unforgettable learning environment (versus the twodimensional Internet training delivery mechanisms). Game shows, .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 315 use of online videos, and interactive skits to grab the participant’s attention work very well. Once the security awareness training grabs attendees’ attention, it is not uncommon to see that people enjoy coming to the sessions and are the first ones to sign up in subsequent years. Security awareness should be fun! One of the first places to start to build the security training session is to go to the toy store and the party store to buy some toys. As silly as this may sound, when people walk into the room feeling like they are about to play a game, their mood changes from “Is this going to be another boring security PowerPoint presentation?” to one of “Hey, this looks like fun!” Their curiosity takes over and as a result, they are more likely to pay attention. Security is a serious subject, but that does not mean that it has to be presented that way to be impactful. If the security professional is uncomfortable with giving presentations that appear silly or humorous, then another possibility is to enlist someone from corporate communications or marketing for support. Imagine being in the place of the end user that is required to attend mandatory awareness training. Programs should be constructed in such a manner that the end-user wants to attend the security awareness training. Step 5: Communication and Logistics Plan A one-page slide announcing the theme of the program should be developed as well as posters indicating the dates of the program. If multiple locations are part of the program, the poster could look something analogous to rock concert tour dates to generate interest. E-mails to the end users at least 1 month prior to the awareness session should be mailed, along with follow-up reminders at 2- and 1-week intervals. People are often very busy and may appreciate the e-mail reminders to sign up for the awareness session. Provisions for make-up signups should also be planned by scheduling one or two make-up sessions after the regular sessions have concluded. The e-mail reminders should stress promptness in attending the sessions. Each location should have signup sheets for the session to ensure that sessions are appropriately filled and do not exceed the size of the room. A good rule of thumb is to only have enough signups for five less than the capacity of the session. For example, if the room will comfortably seat 30 people in the session, then permit 25 to sign up. Why? Because .LQGE 30 316 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED there will always be some individuals that will add their names below the line exceeding the capacity. This can cause problems if tables and exercises were set up for a group size of 25, but 30 show up. By planning for a maximum of 30 people, and allowing 25 to sign up with a 5-person contingency, there would be no problem if 30 people showed up. Travel arrangements to the various sites are also determined in this step, making reservations at least 30 to 60 days in advance to reduce the costs of the program. Step 6: Awareness Delivery Details at this stage are very critical, as the security awareness session should be managed as a production with contingencies for items that may go wrong. The trainer should arrive at the room location at least 1 hour before the start of the session so that the room can be set up in advance of people arriving for the first session. Items such as visual props, table arrangements, candy or food, evaluation sheets, and presentation copies need to be arranged around the room. The LCD projector and computer need to be tested to ensure the video, audio, and presentation operation are working correctly. Sessions should be no more than 1 hour, as the attention span starts to fade after 45 to 60 minutes. Sessions should also be scheduled 30 minutes apart to allow for (a) those individuals that arrive early to “get a good seat,” (b) those individuals that stay after the last session to ask one-on-one questions, and (c) set up for the next session. The trainer should be available at the start of each session to greet each person as they enter the room, and if the trainer is still running around setting up tables, projectors, and props, he or she will not be available. Greeting each person helps to make the program personable and starts the connection process, which increases the likelihood the individual will pay more attention. The delivery should be scripted, but be spontaneous at the same time. Each subsequent delivery can incorporate what worked and remove what did not work in the prior sessions. Sessions should start 5 minutes after the posted start time of the session and end 5 minutes prior to the end. Starting 5 minutes into the session accounts for the latecomers that would miss the start of the session. In high school, students have 5 minutes to get to their next .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 317 class, but once people get into the work world, they are faced with back-to-back meetings with no built-in travel time. Ending 5 minutes early provides time for them to fill out the evaluations. Step 7: Evaluation/Feedback Loops Evaluations provide insight into what is and is not working with the security awareness program. The quality adage “If you can’t measure it, you can’t improve it” applies to information security as well. Did the end users enjoy the training? Did they learn what was expected? Was there anything that could have been improved (content, logistics, delivery, understanding, etc.)? One method that is highly successful is to provide a trade of sorts, or an exchange, at the door as the attendees are leaving, exchanging a security trinket for an evaluation. They may place the evaluation facedown in the chair, but they do not receive the trinket unless they provide an evaluation. A small percentage will be blank; however this technique usually results in 95% to 100% return of the evaluations. The evaluations can then be tracked in a database by location, and assessments of the training can be performed. Numerical scores are tabulated (e.g., 4 out of 5 on a 5-point scale) and open-ended question responses are recorded. Quizzes several months after the training can be issued to determine whether the preceding training was effective. Security Awareness Training Does Not Have to Be Boring By injecting some creativity into the security awareness program, the training can be fun for the participants and fun for the creators. As a side benefit, engaging security professionals where this is not their daily role can broaden their own interpersonal and communication skills. The approach demonstrated in the aforementioned seven steps aides in the understanding and retention of the security message, which is the primary goal of creating a fun security awareness program. Targeted Security Training Security awareness training provides the broad security training that is sufficient for most of the organization. However, to ensure that the .LQGE 30 318 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED proper skills are retained by the organization to carry out the implementation of the security policies, targeted training needs to be developed for certain groups, primarily those individuals managing others and those who are directly involved in an information security function. Security administrators need targeted training in areas such as Microsoft Active Directory, RACF, AC2, and UNIX administration to be able to set up and administer accounts correctly. Depending upon the level of the staff and the expectations, the depth of the training may vary. For example, the security administrator that is setting up accounts may need training on how to use the identity management system but not necessarily the technical details of Active Directory. On the other hand, the security analyst who is responsible for building automated queries and processes may need a seminar in Active Directory. Information security governance cannot occur if individuals are not competent within their assigned jobs. This does not mean that everyone needs the 5-day class, where a PowerPoint or 2-hour hands-on training session may suffice. Managers of employees and contractors typically require additional training, usually an hour or less PowerPoint or learning management system–type course to address issues such as access authorization using the identity management system and the handling on onboarding and terminations. During the on-boarding process, security awareness training, ensuring that background checks are completed, and providing the new hires initial access are subjects that may be covered. When the employee or contractor is terminated, the manager usually has some responsibility to enter information into the system and collect physical property such as badges, credit cards, laptops, and tokens. Communicating these requirements through training can reduce the risk that these activities are not occurring and increasing the exposure to the systems after the employee leaves the company. There are also specialized types of training depending upon the department that may need to occur, such as training of the handling of a customer care application, data center operations, and emergency response training. Not everyone in the organization would need to do what is required in the event of an emergency in the data center, such as a fire, however, the computer operators would need to know what to do to protect the data center and minimize the loss as well as how to safely evacuate. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 319 Continuous Security Reminders A daily e-mail from the help desk explaining the latest security incident would cause most users to set up an e-mail filter to move this type of e-mail to the delete bucket. A balance of the security message must be achieved whereby when the users see an information security message, they are likely to read it and act upon it accordingly. E-mails of the latest incidents as applied to the organization can be very beneficial, especially if employees can relate to the issues in their own home environment. The breach involving Epsilon in 2011 where there was an exposure to the e-mail accounts of millions of customers to firms such as Chase, Citigroup, and Verizon, caused e-mail messages to be spammed and appeared to be coming from these organizations. This represented a great opportunity for organizations to communicate what was occurring and educate the end users about protecting their accounts. Since this occurred to many users as part of their personal computer involvement outside of work, this also has a side benefit of demonstrating the organization’s caring for the associate. These opportunities should be leveraged, which increase the likelihood of compliance to the security policies. Utilize Multiple Security Awareness Vehicles The potential avenues for security communication can fill a book by themselves. Some of the avenues for communication include: • • • • • • • • • • • • .LQGE Company newsletters Posters Learning management system online presentations Brown bag lunches Links on corporate intranet sites Weekly e-mails Logon page or scrolling marquee messages Hosting a “security day” Monthly, short three- to five-page presentations Online quizzes Online “scavenger hunts” Security contests 30 320 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Each of these methods should be considered as supplemental to the classroom-type training that is delivered face-to-face in person annually. Posters should also be used sparingly and typically in support of a specific security awareness campaign. Posters that utilize slogans tend to have limited lasting power beyond the campaign period. Posters can serve as a great advertisement for ongoing online training or classroom training, but by themselves have limited value. If posters are used, care should be taken to track where the posters have been displayed so that they can be removed in a timely manner. The messages should be impactful and address different security concerns beyond the “don’t share your password” type of message. Relating the security message back to how implementing security controls serves to protect the information for the customers that entrust their information to us can be very impactful. Security Officer Communication Skills Fill in chapAs discussed in Chapter X on information security management, t the AU: ter number. security officer must be able to interact with multiple levels off management. Oftentimes when employees respond to the first survey that an organization issues on employee satisfaction, a frequent issue that surfaces is lack of communication. What does this really mean? That the associate did not feel listened to? That their ideas were not acted upon? That there was not an avenue to provide input? That the manager or supervisor was not sharing relevant news in a timely manner? It could be any one or more of those items or something else. The security officer must be able to communicate with individuals in different levels of the organizational hierarchy, from the board of directors to the end users and everywhere in between. There are different personalities that must be communicated with, different styles of working and different ways that people deliver, receive, and process information. The subsequent techniques can improve the ability of the security officer or any security professional to communicate with others. Talking versus Listening Many people appear to believe that they are best communicating when they are talking, however, when we are listening and the other .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 3 21 person feels that he or she has been heard, our ability to communicate is much greater. Unfortunately, we block ourselves from effective listening by not paying full attention to the person speaking. Those who are good listeners tend to draw other people to them; people confide in them and they become a trusted member of the team. By not listening, it sends the message that what they have to say is not very important. Critical information is then missed and opportunities to demonstrate that the person is cared about is also missed. True listening involves providing our full attention. Roadblocks to Effective Listening There are 12 roadblocks that get in our way of effective listening, that make it hard for us to truly listen to what the other person is saying. g Because listening is so crucial in communications, we should continuously be aware of our behavior when another person is speaking. AU: Clarify “different situation is driving …” .LQGE 1. Comparing—While the other person is talking, you are trying to determine if you have had that situation before, and was it worse or not. They may be talking about an issue that you have had before, and the thought is running though your mind, “Hey, it isn’t that tough to complete that, why are they having a problem.” By comparing, it is difficult to listen to what their problem is, as the mind is busy analyzing our own past experiences. 2. Mind reading—Instead of focusing on what the person is saying, the listener is focused on trying to understand the meaning behind what they are saying and interpret a different situation is driving the comments. For example, they h may be saying “I have worked long hours to review these security violation reports, and I am tired of reworking them,” while the listener is thinking, “Oh, they just had a long day because they are going to school in the evenings and are probably just tired.” This may not be the case at all, and in fact the real issue is that the rework is preventing other work from being performed. 3. Rehearsing—The mind is too busy thinking of what the listener will say next, that they are not focusing on the message that is being delivered. In this case, the listener “appears” to be interested in what is being said. 30 322 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED 4. Filtering—The listener listens just long enough to hear whether the person is angry, unhappy, or in danger. Once the emotion is determined, then the listening stops and focuses on other activities or plans that the person is thinking about. The listener only hears half of what is being said. 5. Judging—Judging occurs when someone is prejudged before they even start talking. A negative label is placed on the person who devalues what they may have to say. If the person is seen as unqualified, incompetent, or lacking necessary skills by the listener, they may discount what they have to say. This causes insights to be missed that could provide valuable insight to the solution. 6. Dreaming—When the talker mentions a thought that causes you to think of something in your own life that is unrelated to what they are saying, this is dreaming. They may be talking about what happens if the contract that the company is bidding on is not won, what will happen to the security staffing levels, but before they get to ask the questions, your mind has drifted off to the last company that you worked for that lost a huge contract and how you hated going through the reduction in force motions with your staff. 7. Identifying—Similar to dreaming, in this case every thing the person is telling gets related back by the listener to an experience in their own life. This is commonly shown when people are talking about a situation and then a similar situation is parroted back from the listener’s life. 8. Advising—In this scenario, the listener is too busy thinking of the solution to the problem from the first few sound bites that they miss important information or fail to pickup on how the listener is feeling. 9. Sparring—Quickly disagreeing by the listener causes the listener to search for items to disagree with. This can take the form of a put-down where the talker does not feel listened to and possibly humiliated. 10. Being right—This person will go to great lengths to demonstrate that they are right, including standing by their convictions, not listening to criticism, making excuses, shouting, and twisting the facts. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 323 11. Derailing—The conversation is ended by changing the subject and avoiding the conflict. This is sometimes done by joking to avoid the discomfort of having to discuss the subject. 12. Placating—The listener is very agreeable, as you want people to like you, see you as nice, pleasant, and supportive. Listening may be at the level just enough to get the idea of what is being said, however, you are not fully engaged. By being conscious of these blocks, they can be avoided to become a better listener. There are also four steps to becoming a better listener, as discussed in the next few sections. Generating a Clear Message Effective oral communication depends upon generating a series of clear, straightforward messages that expresses the thoughts, feelings, and observations that need to be conveyed. Since over 90% of what we “hear” is not from the words, but from the volume, pitch, and rhythm of the message and the body movements, including facial expression, it is important that our messages are congruent. We cannot be verbalizing the need for a new, exciting security initiative with our posture slouched in the chair and expect the recipient of the message to be as excited as we are (or potentially not). Double messages should be avoided without hidden agendas. Over the long-term, hidden agendas serve to undermine the security department’s credibility. Influencing and Negotiating Skills Not everyone is going to automatically sign up for the information security initiatives, especially if this means spending money that could be allocated to other programs, involves an increase in the number of rules or adds perceived overhead to their business operations. To successfully negotiate when discussing a position, the security officer must be able to separate the problem from the individual. Direct attacks based upon prior experience with a particular department will not help gain its support. The key is to look at the security initiative that is being proposed from the perspective of the person that you .LQGE 30 324 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED are trying to influence. It is also dangerous to try to read the other person’s mind as noted in the previous section and come to prejudged conclusions of their support or nonsupport of the project. It is OK to postulate in advance what the stakeholders may think about the situation to assist with the preparations; however, it is not prudent to come to foregone conclusions about their reaction. Consider various options to implementing a strategy that may be pliable to the stakeholder. There is always more than one way to perform something. A request by a business manager may be met with resistance by the security officer. However, by brainstorming various options, one of these solutions may be palatable, with some investigation, for both the business manager and the security officer. Once options are determined, these can be generated into requirements that are not demands but rather where the solution is mutually agreeable. Written Communication Skills Written communication takes on several forms in today’s word from e-mail, texting, twittering, social media (Facebook, Myspace, LinkedIn) posting, report writing, policy/procedure writing, and memo writing. E-mail is the predominant written form of communication and is much different than writing a memo or a policy and procedure. Care must be taken to know the audience and the purpose of the written communication. Although e-mail is a very quick method to communicate across the organization, it is amazing how many e-mails people send that have incorrect grammar, misspelled words, or use negative language. Since there is no tone button on the e-mail that is sent, words must be chosen carefully so as to not alienate the recipient. A simple request may turn into hurt feelings if not written in a clear, nonconfrontational manner. E-mails are also received almost as quickly as the send button is pressed, so extra care needs to be made taken constructing the message. Although it may be easy to become emotional over an issue, these are best handled by picking up the phone if they cannot be addressed using a fact-based, diplomatic written approach. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 325 Presentation Skills Presentations come with the territory and security officers will find themselves in the position of having to deliver a presentation to senior management. Since management has limited time, presentations need to be focused with, “What do I hope to obtain or convey with this presentation?” Sometimes presentations will be an impromptu-type, such as the 30-second elevator speech, or it may be at the other extreme in the form of a memorized speech. Most presentations are combination of the two, whereby the presentation slides serve to guide the presentation, with much of the material being an impromptu delivery (albeit prepared) by the presenter. Presentation dos and don’ts are shown in Table 12.2. Table 12.2 Presentation Dos and Don’ts DO THIS DON’T DO THIS Know the audience: General end users? Technically oriented users? Management? Engage the audience by asking questions. Assume that the audience has the same level of understanding. Speak nonstop for 45 minutes or more (beyond the normal attention span). Exclusively using PowerPoint. Use a mixture of audio, video, and visual artifacts to make a point. Translate the technical issues by using analogies, stories, and relating to common everyday language. Make eye contact and use a friendly demeanor. Answer their questions using the no-dumbquestion rule. Ask questions early to get the audience engaged. If unsure of an answer, open the question up to the group. Leave time for questions and end the presentation 5 minutes early to permit time for attendees to make their next meeting. Focus on a few main objectives for the presentation. Keep the type text at least 24 font point. Speak with a microphone in larger rooms so the audience in the back of the room can hear. .LQGE Use technical security jargon when unnecessary. Read the presentation slide by slide or from note cards. Act superior to the questioner by failing to recognize their comments as valid, albeit they may be coming from a different perspective or disagree. Completely, but briefly, answer their questions. Lose credibility by talking about subjects that you have little experience with. Speak right up until the end of the hour and not get the conclusion or discussion of options completed. Provide histories (organization, computing) that are not related to the current discussion. Use graphics that are hard to see or are distracting (e.g., excessive use of animation). Assume that your voice is loud enough; some individuals may not be able to pick up the modulation properly. 30 326 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Applying Personality Type to Security Communications Ideas emanating from the early work of Carl Jung, a Swiss psychologist, were extended through the development of an instrument to indicate personality type differences by Isabel Myers and her mother Katharine Cook Briggs in 1943. This later became known as the Myers–Briggs Type Indicator, or MBTI, which has been taken by M millions of people. The MBTI is a very powerful tool, which at its simplest form breaks down all of the personalities into 16 types. Understanding each of these 16 types can help the security organization communicate more effectively with different individuals based upon their type. In other words, it helps to know how they may be wired to understand how they take in information, make decisions, where they get their energy from, and how they organize their lives. The Four Myers–Briggs Type Indicator (MBTI) Preference Scales The complete psychology explanation of the 16 types is well beyond the scope of this book, but there are many useful books written on the MBTI type noted at the end of this chapter. However it is useful to provide a brief primer on the 16 types and, more important, what the implications are for the information security department. There are four scales, with each person having a natural preference for one of the two opposites on each scale. While we all use each of the opposites at different times, one scale feels more natural to us most of the time. This natural tendency becomes our preference or the place where we are the most comfortable. The combination of the four scales, with two opposite values, yields 16 combinations of letters. Each set of letters yields a describable personality, not in a stereotypical manner, but rather a mechanism to explain the personality and what may be expected behavior, career interests, reactions to certain events, and so forth from that personality type. It is important to note that no “preference” is better than another, it is just different. Each of us uses all of the dimensions of preference at some point, and we flex our behaviors depending upon the situation. For example, an introverted parent may flex their extraversion when providing discipline to a child. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S Table 12.3 327 Where Do I Prefer to Focus My Energy (Inner or Outer World)? EXTRAVERSION (E)—TUNED INTO OUTER WORLD OF PEOPLE AND EVENTS INTROVERSION (I)—DRAWN TO INNER WORLD OF IDEAS AND EXPERIENCES Seek interaction Enjoy groups Act or speak first, then think Sociable and expressive Expend energy Focus outwardly Take initiative in work and relationships Like variety and action Outgoing Breath of information Like to be alone Enjoy one-on-one conversation Think first, then speak or act Think to themselves Conserve energy Focus inwardly Quiet, reserved Like to focus on one thing at a time Enjoy reflecting Depth of information The first preference is about where you prefer to get your energy: the external world (extraversion, E) or from the inside world (introversion, I). Extraverts tend to get energy from the people, interactions, and events, whereas introverts tend to derive their energy from their internal thought, feelings, and reflections. It is sometimes said that extraverts are processing information as they are talking, while introverts tend to crystallize the idea internally first before speaking. Introverts draw their energy from being alone, while the extravert may feel drained by spending long periods without interaction. Table 12.3 shows some of the characteristics of extraverts and introverts. Extraversion versus Introversion Scale This preference indicates how information is gathered. Sensing (S) individuals prefer to take in information through their senses, such as seeing, hearing, smelling, and so forth, to see what is actually happening. They are observant of what is going on around them and very good at determining the practicality of the situation. Information presented is preferred to be delivered in a very specific manner. Sensors tend to prefer to be presented with the facts and details of what they are reviewing. About 70% of the world prefers to gather information this way. Individuals that prefer to see the big picture to take in information most likely prefer intuition (N) to gather information. They focus on Sensing versus Intuition Scale .LQGE 30 328 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED Table 12.4 What Kind of Information Do I Normally Pay Attention To? SENSING (S)—FOCUS ON CONCRETE, REAL, ACTUAL INTUITION (N)—FOCUS ON ABSTRACT, RELATIONSHIPS, PATTERNS Prefer facts, concrete data Value practical applications Present oriented Focus on reality, details, specifics Like step-by-step instructions Pragmatic Value common sense Prefer insights Value imaginative insight Future oriented Focus on the big picture, possibilities Like to jump around, move in anywhere Speculative Value innovation the relationship between various facts, facts that may not appear to have any relationship to the sensor. They are good at seeing new possibilities and new ways of doing things. Table 12.4 shows some of the characteristics of sensing and intuition preferences. How decisions are made is attributed to the decision-making preference, which has two ends of the scale, thinking (T) and feeling (F). Thinkers tend to look at the logical ramifications of a course of action. The goal of the thinker is to make a decision from an objective viewpoint and tend not to get personally involved in the decision. They are often called firm minded and seek clarity in the decision. They are good at figuring out what is wrong with something so that problem-solving abilities can then be applied. The feelers tend to approach decision making based upon what is important to them and to the other people. While the decision making of the thinker may gravitate toward what is right, lawful, or concludes with justice, the feeler may base the decision on personcentered values to achieve harmony and recognition of other individuals through understanding, appreciating, and supporting others. In short, feelers tend to prefer empathy over intellect. Table 12.5 shows some of the characteristics of thinkers and feelers. Thinking versus Feeling Scale Judging versus Perceiving Scale The last preference indicates the preference as to how you orient your world. Judgers (J) want to regulate and control life by living in a scheduled, organized, and structured way. They do not like things unsettled and want order in their lives. They enjoy their ability to stick to a schedule and get things done. For the judgers there is usually a right way and a wrong way to do things. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S Table 12.5 How Do I Make Decisions? THINKING (T)—ANALYTICAL, LOGICAL CONSEQUENCES, PRINCIPLED FEELING (F)—CONSIDER IMPORTANCE TO THEM, OTHER PEOPLE AND VALUES Firm minded Objective, convinced by logic Laws, justice, policy Reasonable Logical problem solvers Don’t take things personally Good at critiquing Gentle hearted Subjective, convinced by values Humane, social values Compassionate Assess impact on people Likely to take things personally Good at appreciating Table 12.6 329 How Do I Organize My World? JUDGING (J)—PLANNED, ORDERLY, CONTROLLED LIFE PERCEIVING (P)—FLEXIBLE, SPONTANEOUS, EXPERIENCE LIFE Seek closure, things settled Value structure, goals Scheduled, methodical Systematic Like closure and have things decided Avoid last-minute stresses Enjoy completing projects Seek openness Like flexibility, tentative Spontaneous, flexible Casual Like to have their options open, able to change Energized by last-minute pressures Enjoy starting projects Perceivers (P) prefer to be flexible and adaptable in different situations. They want to be able to be spontaneous and flexible to rise to the opportunity as it presents itself. They are called perceivers due to their ability to keep collecting new information, rather than draw premature conclusions on a subject. In other words, they prefer the open-endedness and ability to change their decision based upon new information. Table 12.6 shows some of the characteristics of judgers and perceivers. Determining Individual MBTI Personality Using the aforementioned descriptions and characteristics, by now it should be possible to determine your approximate MBTI or set of four letters describing your personality. This can be used as a guide for the next section in determining the individual temperament. The actual determination of the letters is more accurately determined by taking an assessment of the MBTI® by Consulting Psychologists Press, .LQGE 30 330 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED containing more than 200 preference questions and determining the y In real life, we have to learn to approxiletters with more accuracy. mate the Myers–Briggs off our peers, unless we ask them if they know what theirs are, as they are not going to take a 200-plus question assessment for us! Over time, speed reading the types for individuals become easier and a very valuable tool for interacting with others. In an effort to distill the 16 types into commonalities for ease of discussion, David Keirsey portioned the 16 types into four temperaments by grouping the SPs, SJs, NTs, and NFs. Although there are individual differences due to the other two letters that make up each set of 4 letters (for an individual’s personality), there was a strong commonality within these groups, which simplifies the discussion of their temperament. Following is a brief description of some of the characteristics of personality types that fall into each of the four temperaments, along with the implications as to how security should be communicated with each temperament. For example, the SJ temperament consists of those individuals who have the ESTJ, ISTJ, ESFJ, or ISFJ personality preferences. For example, the ESTJ natural preferences are to obtain their energy from extraversion, gather information through sensing (concrete, detail-oriented), make decisions based upon thinking (logical, analytical values), and orient their world through Judging (schedule oriented, organized). The ESTJs share some common characteristics with the other SJs (ISTJ, ESFJ, ISFJ), even though they may vary on one of the other dimensions. The Four Temperaments SJ “Guardian” Temperament Those personality preferences shar- ing the SJ temperament (ESTJ, Supervisor; ISTJ, Inspector; ESFJ, Provider; ISFJ, Protector) share characteristics of being reliable, organized, task focused, and hard working at their best. At their worst, they may be perceived as being judgmental, controlling, inflexible, or close minded. They typically respect the laws and traditions of society, like to be in charge, have a standard way of doing things, expect others to be realistic, strive to belong and to contribute, have high expectations of themselves and others, are critical of mistakes and may fail to reward expected duties, have difficulty refusing to take on .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 3 31 other assignments, and do not like surprises. They are also good at anticipating problems. While people of any temperament can be successful at any job, there are some careers that attract this temperament more than others. The SJ temperament may choose careers as a project manager, regulatory compliance officer, budget analyst, chief information officer, bank manager/loan officer, government employee, administrative assistant, nurse, auditor, pharmacist, engineer, or an accountant. These are jobs typically involving adhering to a set of rules and standards without a large amount of ambiguity, which is attractive to the SJ temperament. SJs are also attracted toward positions that can create financial security. When communicating information security issues with the SJ temperament, it is important that if something was done wrong, that regret is expressed and a simple I’m sorry is used. This can set things straight and allow the SJ to move forward. SJs should be appreciated for their responsibility and willingness to handle the details of the situation in the form of compliments. For example, individuals in the security group managing the very detailed logging and monitoring may be of the SJ temperament as evidenced by their willingness to handle and organize the vast amount of detail. Commitments must be kept with SJs to win their trust. If the CEO is an SJ and there were promises made to implement a security initiative by the end of March so that a new product could be launched in May, the CEO who shares this personality type preference will most likely be less forgiving than the SP type, for example, when the deadline is not met. Communications with SJs should be specific and practical, as Dragnet’s Joe Friday would iterate, “Just the facts ma’am. Just the facts.” SJs are also resistant to change and need to be brought into change more slowly with logical reasons for the change. However, once the change has been embraced, they can be one of the strongest supporters of the change. The SP temperament (ESTP, Promoter; ISTP, Crafter; ESFP, Performer; ISFP, Composer) personality types may be viewed as the action seekers. They may be viewed as optimistic, generous, fun loving, adventurous, realistic, and adaptable at SP “Artisan” Temperament .LQGE 30 332 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED their best, or hyperactive, impatient, impulsive, and scattered at their worst. They enjoy life in the here and now, highly value freedom and action, like risk and challenge, are spontaneous, may be perceived as indecisive, are observant, ask the right questions to get what they need, respond well to crisis, like short-term projects, and dislike laws and standard ways of doing things. This is sharp contrast to the SJ temperament previously discussed, which thrives on standards and ensuring that the rules are being followed. For career selections, the SPs tend to gravitate toward careers that permit them to experience life versus a means toward an end. Potential career choices for the SJ may include emergency room nurse, medical assistant, photographer, police officer, public relations specialist, fire/ insurance fraud investigator, news anchor, airline mechanic, marine biologist, or paramedic/firefighter. In the security field, individuals wanting the excitement of responding to a disaster recovery situation or an intrusion may gravitate toward this area. When communicating with the SP temperament, appreciation should be shown for their enthusiasm, common sense, and ability to deal with crisis. Joining in some of their activities may be appropriate, such as an invitation to meet them and a group of security vendors after work. Business executives of this type may be part of the golf club or bowling league, and this would be a good opportunity to network with these individuals and build rapport to create a nonadversarial environment. Given choices and alternatives, those sharing the SP temperament will want to do things their own way in their own timeframe. Issues should be pinpointed and overwhelming them with information avoided. They also do not like being told how to change or what to do. NF “Idealist” Temperament Those sharing the NF temperament (ENFJ, Teacher; INFJ, Counselor; ENFP, Champion; INFP, Healer), known as the ideal seekers, share the characteristics of being compassionate, loyal helpful, genuine, warm hearted, and nurturing at their best, or may be perceived as moody, depressed, or oversensitive at their worst. They are stimulated by new ideas, take an antiauthoritarian attitude, often side with the underdog, see possibilities in institutions and people, search for meaning and authenticity, self-actualize, .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 333 maintain close contact with others, give freely and need positive appreciation, and are good listeners. NF temperaments may gravitate toward jobs such as psychologist, sociologist, facilitator, career counselor, travel agent, human resources recruiter, teacher (health, art, drama, foreign language), social worker, or hotel and restaurant manager. When communicating with the NF temperament, cards, gifts, compliments and adoration go a long way. They are sensitive to criticism, so extra tact is necessary. Patience is needed to understanding of their need to express their feelings. Their support can be gained by appealing to their creativity and vision of their ideals. Individuals sharing the NT temperament group (ENTJ, Field Marshal; INTJ, Mastermind; ENTP, Inventor; INTP, Architect), known as the knowledge seekers, have strengths of being innovative, inquisitive, analytical, bright, independent, witty and competent at their best, or they may be perceived as arrogant, cynical, critical, distant, or self-righteous at their worst. They work well with ideas and concepts, value knowledge and competency, understand and synthesize complex information, anticipate future trends, focus on long-term goals, like to start projects (although not as good on follow-through), not always aware of other’s feelings, aim for mastery, and deal with the day-to-day details but have little interest in them. Knowledge seekers may be found as an executive, senior manager, personnel manager, sales/marketing manager, technical trainer, network integration specialist, technical writer, investment banker, attorney, psychiatrist, database administrator, credit analyst, technical project manager, architect, or Web developer/computer programmer. When communicating a security concern or initiative with the NT temperament, the security professional should attempt to appreciate their objectivity, quick minds, and knowledge. Since they value mastery in what they do, conversations that are intellectually stimulating should be pursued, feelings should be avoided in conversation, and debate with them, letting them know frequently you value their insights. Many of the technical staff involved in connecting patterns together, such as the network engineers or database administrators, NT “Rational” Temperament .LQGE 30 334 IN F O RM ATI O N SEC U RIT Y G O V E RN A N C E SIM P LIFIED can become supportive of the security program by simply asking them for their input and genuinely incorporating their insights into the security strategy and subsequent implementations. Summing Up the MBTI for Security Communication is so important and goes well beyond providing a written report or an oral presentation; it is how we interact with others on a daily basis. As the security program must remain credible to be effective, we must ensure that we are communicating the security messages clearly, and in a manner in which they will be heard. We tend to communicate by default by the manner that we are comfortable receiving. Unfortunately, and fortunately, we are not all the same, and we take in and process information differently. To be successful within the organization, the security officer and his or her team need to be able to communicate at an appropriate level with others within the organization. Understanding the differences in personalities will increase the effectiveness of the security message that needs to be delivered. References 1. McKay, Mathew, Davis, Martha, and Fanning, Patrick. 1995. How to communicate: The ultimate guide to improving your personal and professional relationships. New York: MJF Books. 2. National Institute of Standards and Technology (NIST). October 2003. Special Publication 800-50: Building an information security technology security awareness and training program. http://csrc.nist.gov/ publications/nistpubs/800-50/NIST-SP800-50.pdf 3. National Institute of Standards and Technology (NIST). October 1995. Special Publication 800-12: An introduction to computer security: The NIST handbook. http://csrc.nist.gov/publications/nistpubs/800-12/ handbook.pdf 4. Herold, Rebecca. 2005. Managing an information security and privacy awareness and training program. Boca Raton, FL: Auerbach. 5. Tieger, Paul D., and Barron-Tieger, Barbara. 1998. The art of speedreading people: Harness the power of personality type and create what you want in business and in life. Boston: Little, Brown and Company. 6. Tieger, Paul D., and Barron-Tieger, Barbara.1998. Do what you are: Discover the perfect career for you through the secrets of personality type. Boston: Little, Brown and Company. .LQGE 30 E F F EC TI V E SEC U RIT Y C O M M U NI C ATI O N S 335 7. Myers, Isabel Briggs, and Myers, Peter. 1995. Gifts differing: Understanding personality type, 2nd ed. Palo-Alto, CA: Davies-Black. 8. Kroeger, Otto, and Thuesen, Janet M. 1992. Type talk at work. New York: Tilden Press. 9. Bolton, Robert, and Bolton, Dorothy Grover. 1996. People styles at work: Making bad relationships good and good relationships better. New York: Ridge Associates. 10. Keirsey, David. 1998. Please understand me II: Temperament, character, intelligence. Del Mar, CA: Pometheus Nemesis. 11. Myers, Isabel Briggs.1993. Introduction to type, 5th ed. Palo Alto, CA: Consulting Psychologists Press, Inc. .LQGE 30 .LQGE 30 13 THE L AW AND I NFORMATION S ECURIT Y If you give to a thief he cannot steal from you, and he is then no longer a thief. William Saroyan, 1908–1981 Over the past several decades, and particularly in the last decade, there has been an increased focus on information security in concert with the fear that individual privacy could be compromised. As information has become more electronic and networks such as the Internet provide access points to personal computers and company computer networks, the attention of lawmakers has been raised. The fear is that this massive aggregation and interconnection of information will lead to exposures of sensitive information. Numerous laws have been put in place. In some cases, these laws overlap, adding to the complexity for the security officer attempting to build a one-size-fits-all information security program. The governance strategy must ensure the compliance with existing laws, as well as remain abreast of the emerging laws and regulations that are on the horizon. When the regulations are published, they come with a mandated compliance date and depending upon the size of the organization and the scope of the mandate, can be very time consuming to complete between the period of final law issuance and the required implementation. Therefore, it is in the best interest of the security officer to review draft regulations and proactively anticipate what types of requirements have a good chance of remaining in the final version of the law to provide more time to implement the new requirements. An added benefit of this approach is that by being well versed in the upcoming provisions, the security officer has the opportunity to provide input by way of comments to the proposal, usually within a 60-day period for federal regulations, to help shape the legislation. 337 .LQGE 30
© Copyright 2026