Document 204018
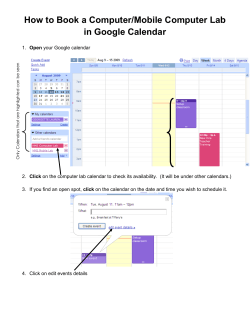
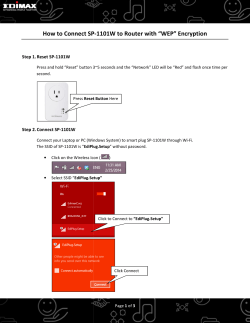
How To Upgrade a Management Server February 2003 1. Introduction 1.1. General This document describes the upgrade procedure of Check Point’s Management Server, from 4.1 (or a pre NG FP3 version), to NG FP3. Check Point’s Management Server upgrade consists of two main phases: • Changing the Management Server software. • Upgrading the server database format to the one required by the new software. This document describes in detail the alternative methods of upgrading Check Point’s Management Server to NG FP3, allowing you to select the method best to fit your needs. This document focuses on an upgrade procedure using a duplicate machine. 1.2. Terms 1. Production machine – The production Management Server you wish to upgrade. 2. Duplicate machine – A new machine, which, at the end of the process, will be identical to the production machine, and will be upgraded to NG FP3. 1.3. Assumptions This document assumes that your duplicate machine has the same IP/hostname and the same OS as the production machine. Otherwise, refer to the relevant appendices. 1.4. Basics There are two basic methods of upgrading Check Point’s Management Server: • Upgrade on the actual production management machine. • Upgrade on a duplicate machine, while the production Management Server is fully operational. Testing the full functionality of the new Management 1 Server, with the ability to either switch to new upgraded machine or copy the upgraded environment onto the production machine. Upgrade on the production management is done by choosing upgrade when installing NG FP3 software from the Check Point’s CD. Upgrade on a duplicate machine can be done in two ways that will be explained thoroughly throughout this document. Cases in which the machines have different IP addresses, host names or Operation Systems, will also be addressed. 1.5. Common Upgrade Scenarios on a Duplicate Machine There are two common scenarios for upgrading Check Point’s Management Server on a duplicate machine (Manual Upgrade is the recommended path, though the second method will yield with the same results): 1.5.1. Manual Upgrade 1. Install the Check Point NG FP3 Management Server software on the duplicate machine. 2. Copy the database files from the production Management Server onto the newly installed server. 3. Perform a manual upgrade to translate the database files into the NG FP3 format. 1.5.2. Replication and Upgrade 1. Replicate the production Management Server on the duplicate machine. 2. Install the NG FP3 Management Server software on the duplicate machine from the Check Point CD choosing the Upgrade option. The following sections describe each of the scenarios listed in 1.5 above in detail. You can choose from either of these scenarios. 2. Manual Upgrade in Details 2.1. When the production machine Management Server software version is 4.1 1. Run the PreUpgrade_Verifier tool on the production machine to detect potential problems that need to be addressed prior to upgrading. This is a read only tool which will not change the database. 2. Install the Check Point NG FP3 software on the duplicate machine. Take extra care to install the exact same products that are installed on the production machine. There is no need to install a license at this stage as each new NG FP3 machine has a built- in evaluation license for 15 days. 2 3. Run the Manual Upgrade command on the new machine to change the database format into NG FP3 format: 3.1. Download the upgrade script from SecureKnowledge solution #SK11635. 3.2. Decompress the downloaded file to receive a structure of directories. Note: On Windows platforms, the manual upgrade script should be installed on the same disk drive as the Management Server installation. 3.3. Stop Check Point software on both machines by executing the cpstop command. 3.4. Copy the following files from the production machine to the 4.1 subdirectory on the duplicate machine: • $FWDIR/conf objects.C rulebases.fws fwauth.NDB* fgrulebases.fws (if exists) xlate.conf (if exists) aftpd.conf (if exists) smtp.conf (if exists) sync.conf (if exists) masters (if exists) clients (if exists) fwmusers (if exists) gui-clients (if exists) slapd.conf (if exists) serverkeys (if exists) product.conf (if exists) • $FWDIR/database InternalCA.DB (if exists) Note: In case your duplicate machine has an OS different from the duplicate machine, see Appendix B. 3.5. Restart the Check Point software on your production machine by executing the cpstart command to get it back into operation. 3.6. If $FWDIR/database/InternalCA.DB file exists, run fwm sic_reset on the duplicate machine. 3.7. Activate the Upgrade Script on the duplicate machine: • For UNIX platforms: upgrade.csh<upgrade_script_directory> FP3 • For Windows platforms: upgrade.bat <upgrade_script_directory> FP3; upgrade_script_directory is the path of the upgrade script, created after decompressing the script file. 3 4. Run the PostUpgrade_Verifier tool on the duplicate machine to validate integrity of the upgraded environment. 5. Use the Check Point Configuration Tool to initialize the Internal CA. 6. Disconnect the production machine from the network and connect the duplicate machine. 7. Test your duplicate machine according to the instructions listed under Appendix E. 8. If the duplicate machine will function as the production machine, go to step 12. 9. If duplicate machine works as expected, backup the production machine (backup the files as defined in sub-section 3.4). 10. Upgrade the production machine using the process defined above. 11. Disconnect new machine; connect the production machine. 12. Test your production machine according to Appendix E. 13. Done. 2.2. When the production machine Management Server software version is NG 1. Run the PreUpgrade_Verifier tool on the production machine to detect potential problems that need to be addressed prior to upgrade. This is a read only tool, which will not change the database. 2. Install the Check Point NG FP3 software on a duplicate machine. Take extra care to install the exact same products installed on the production machine. There is no need to install a license at this stage as each new NG FP3 machine has a built- in evaluation license for 15 days. 3. In cases where your duplicate machine has a different IP/hostname, see Appendix A. If your duplicate machine has a different OS, see Appendix B. 4. Stop Check Point software on both machines by executing the cpstop command. 5. Copy the following files to their corresponding destination on the duplicate machine: • • • $CPDIR/conf 1. cp.license 2. sic_cert.p12 $CPDIR/database 1. *.C $FWDIR/conf 1. lists/* 2. *.fws 3. *.conf (except for components_reg.conf fwrl.conf, cpmad_rulebase.conf) 4. fwmusers 4 • 5. *.C (except for mv_doc.C, classes.C, scheme.C, fields.C, tables.C, rtmclasses.C, default_objects.C) 6. db_versions/Database/versioning_db.fws 7. gui-clients 8. vpe/* 9. XML/* 10. cpsc/* 11. I* 12. crls/* 13. db_versions/repository/* 14. fwauth.NDB. 15. DiapCpdList.NDB 16. DiapFwmList.NDB 17. DAIP_RS_Database.NDB 18. robo-gateways.NDB 19. robo-control.NDB 20. robo-ike.NDB $FWDIR/log 1. *.* 6. Start the Check Point software on your production machine by executing the cpstart command to get it back into operation. 7. Activate the command $FWDIR/bin/fwm up <fpx> fp3 on the duplicate machine, where fpx is the current version of the production Management Server. For example: if the server version is NG FP1 run: fwm up fp1 fp3. 8. Run the PostUpgrade_Verifier tool on duplicate machine to validate the integrity of the upgraded environment. 9. Disconnect the production machine from the network and connect the duplicate machine. 10. Test your upgraded duplicate machine according to the instructions listed in Appendix E. 11. If the new duplicate machine will function as the production machine, go to step 14. 12. If the duplicate machine works as expected, backup the production machine. 13. Upgrade production machine: • Uninstall Check Point software. • Go over steps 2-10. 14. Disconnect the duplicate machine; connect the production machine. 15. Test your production machine according to Appendix E. 16. Done. 5 3. Replication and Upgrade 3.1. When the production machine Management Server software version is 4.1 1. Run the PreUpgrade_Verifier tool on the production machine to detect potential problems that need to be addressed prior to upgrade. This it is a read only tool with no effect on the database. 2. Install the 4.1 Check Point Management Server software on the duplicate machine. Take extra care to install the exact same products installed on the production machine. Put appropriate licenses on the duplicate machine. 3. Stop Check Point software on both machines by executing the cpstop command. 4. Copy the following files from the $FWDIR/conf directory of the production machine to $FWDIR/conf directory of the duplicate machine: • $FWDIR/conf objects.C rulebases.fws fwauth.NDB* fgrulebases.fws (if exists) xlate.conf (if exists) aftpd.conf (if exists) smtp.conf (if exists) sync.conf (if exists) masters (if exists) clients (if exists) fwmusers (if exists) gui-clients (if exists) slapd.conf (if exists) serverkeys (if exists) product.conf (if exists) • $FWDIR/database InternalCA.DB (if exists) Note: In case your duplicate machine has a different OS, see Appendix B. 5. Start Check Point software on your production machine by executing the cpstart command. 6. In order to make sure that the replicated Management Server has been successfully upgraded as expected, try to push policy on the modules, receive logs and check the module’s status. 7. Install the Check Point NG FP3 software on the duplicate machine using the NG FP3 CD, and select the upgrade option to automatically upgrade of the software and the database format. 8. Run the PostUpgrade_Verifier tool on the duplicate machine to validate integrity of the upgraded environment. 6 9. Disconnect the production machine from the network and connect the duplicate machine. 10. Test your upgraded machine according to the instructions listed under Appendix E. 11. If the duplicate machine will function as the production machine, go to step 15. 12. If duplicate machine works as expected, backup the production machine. 17. Upgrade the production machine: • Uninstall Check Point software. • Go over steps 2-10. 13. Disconnect the duplicate machine; reconnect the production machine. 14. Test your production machine according to Appendix E. 15. Done. 3.2. When the production machine Management Server software version is NG 1. Run the PreUpgrade_Verifier tool on the production machine to detect potential problems that need to be addressed prior to upgrade. This is a read only tool with no effect on the database. 2. Install the Check Point NG software on the duplicate machine. Take extra care to install the exact same FP (feature pack), hotfixes and products that are installed on the production server. Put the appropriate licenses on the duplicate machine. 3. If your duplicate machine has a different IP/hostname or has a different OS, See appendix A for different IP, and appendix B for a different OS. 4. Stop the Check Point software on both machines by executing the cpstop command. 5. Copy the following files from the production machine to their corresponding place on the duplicate machine: • • • $CPDIR/conf 1. cp.license 2. sic_cert.p12 $CPDIR/database 1. *.C $FWDIR/conf 1. lists/* 2. *.fws 3. *.conf (except for components_reg.conf fwrl.conf, cpmad_rulebase.conf) 4. fwmusers 5. masters 6. *.C (except for mv_doc.C, classes.C, scheme.C, fields.C, tables.C, rtmclasses.C, default_objects.C) 7 7. db_versions/Database/versioning_db.fws 8. gui-clients 9. vpe/* 10. XML/* 11. cpsc/* 12. I* 13. crls/* 14. db_versions/repository/* 15. fwauth.NDB. 16. DiapCpdList.NDB 17. DiapFwmList.NDB 18. DAIP_RS_Database.NDB 19. robo-gateways.NDB 20. robo-control.NDB 21. robo-ike.NDB • $FWDIR/log 1. *.* 6. Start the Check Point software on your production machine by executing the cpstart command. 7. If they exist, Remove the $FWDIR/conf/CPMILinksMgr.* and $FWDIR/conf/applications.*. 8. Copy the SIC key from the Check Point registry on the production machine to the registry on the duplicate machine. See appendix D for a detailed description of copying Check Point’s SIC regis try entries. 9. Install Check Point NG FP3 software on the duplicate machine using the NG FP3 CD, and select the Upgrade Option to automatically upgrade the software and database format. 10. Run the PreUpgrade_Verifier tool on the duplicate machine to fix potential upgrade problems that need to be addressed prior to upgrade. This is a read only tool, which will not change the database. 11. Disconnect the production machine from the network and connect the duplicate machine. 12. Test your upgraded machine according to the instructions listed under Appendix E. 13. If the duplicate machine will function as the production machine, go to step 15. 14. If the duplicate machine works as expected, backup the production machine. 18. Upgrade the production machine: • Uninstall Check Point software. • Go over steps 2-10. 15. Disconnect the duplicate machine; connect the production machine. 16. Test your production machine according to Appendix E. 17. Done. 8 Appendix A - Duplicate machine with a different IP address or hostname This appendix specifies the steps that should be taken in case the duplicate machine has a different IP address or host name. 1. Before stopping the production machine, add rules that allow the new duplicate machine to access the modules it is managing: • Create a Management Object that includes the duplicate machine’s IP address: Ø When the production machine Management Server software version is 4.1 – From the Policy Editor: Manage > Network Objects > New…> Workstation and mark it as a Management Station. Ø When the production machine Management Server software version is NG – From the Policy Editor: Manage > Network Objects > New…> Check Point > Host/Gateway and mark it as Secondary Management. Note: If this object already exists, make sure it is marked as a Management. Create a rule, on the production machine, which allows FireWall-1 and CPD (NG only) services from the above object you have just created, to go to all managed gateways. • Install the rule on all managed gateways. • Delete the rule once you have completed this process. Continue with the instructions given under section 2.2 or 3.2. Do not copy the $CPDIR/conf/cp.license file. Update the primary management object on the duplicate machine. 3.1. Start the Check Point Management Server on the duplicate machine by applying the cpstart command. 3.2. Connect to the SmartDashboard (Policy Editor). 3.3. If a new primary management object was created, its IP address and topology should be configured to match the duplicate machine. If the same primary object exists, edit its IP address and topology to match its new configuration. 3.4. Replace all occurrences of the production object with the newly created duplicate machine object. You can find all occurrences with the Where Used… utility (right-click on the object to choose the command). If a new primary object was created then both objects now have the same SIC name. This must be corrected: 4.1. Close the SmartDashboard (Policy Editor). 4.2. Use Check Point Database Tool or the dbedit command to clear the SIC name from the old object. The attribute is called sic_name; the object is in the network_objects table. After the update it should look like this “:sic_name ()”. If you would like to delete the production management object: • 2. 3. 4. 5. 9 6. 7. 8. 9. 5.1. Stop the duplicate machine by running the cpstop command. Make the following change in $FWDIR/conf/objects_5_0.C: 5.1.1. Find the production management’s object. 5.1.2. Change the attribute Deleteable (if exists) to true (under AdminInfo). 5.1.3. Save the changes. 5.2. Start the Management Server by running the cpstart command. 5.3. Connect to the SmartDashboard (Policy Editor) and delete the production management object. This will revoke all of Check Point’s internal CA IKE certificates for that object. If the $FWDIR/conf/mgmtha* where created: 6.1. Stop the duplicate machine by running the command cpstop. 6.2. Delete $FWDIR/conf/mgmtha* files. 6.3. Start the Management Server by running the cpstart command. Use the Check Point Configuration Tool by running the cpconfig commmand > Certificate Authority to set the FQDN (You should enter the FQDN of the duplicate machine). Exceptions: If the gateways managed by this Management Server are involved in VPN with external entities, and the authentication of these VPN connections is based on ICA certificates, then the external gateways will use the distribution point on these certificates to access the relevant CRL. There are two alternatives for succeeding after the upgrade procedure: 7.1. Change the FQDN in the ICA to the duplicate machine’s FQDN, and reassign new certificates to all gateways and users . 7.2. Update the DNS so that the production’s FQDN will now be resolved to the duplicate machine. After doing this, the production machine’s FQDN should be changed to avoid ambiguity. Adjust masters and log servers for each module before installing on it a policy. You should add the duplicate machine’s object to the ‘masters list’, and if needed, add it to the ‘log servers list’ on each module. Re-establish trust with any module by using the putkey command (for 4.1 modules). Appendix B - Duplicate machine using an OS different than the production machine This appendix specifies the steps that should be taken in case the duplicate machine is using an OS that differs from the production machine. When the production machine Management Server software is 4.1 1. See Appendix C for an explanation about copying NDB files. 10 2. When moving from a Windows platform to a UNIX like platform, run the dos2unix command on all the files you have copied, except fwauth.NDB and serverkeys. When the production machine Management Server software is NG 1. Clear the log files on the production machine, by applying $FWDIR/bin/fw logswitch. 2. Copy the files as specified in 3.2. If the production machine platform is Windows and the duplicate machine is Unix, copy the *.NDB files according to the explanation in Appendix C. 3. If the production machine platform is Windows and the duplicate machine is Unix, run the dos2unix command on all the files listed under 3.2, except for: 1. 2. 3. 4. 5. 6. 7. 8. 9. $FWDIR/conf/I* $FWDIR/conf/crls/* $CPDIR/conf/sic_cert.p12 $FWDIR/conf/ fwauth.NDB. $FWDIR/conf/DiapCpdList.NDB $FWDIR/conf/DiapFwmList.NDB $FWDIR/conf/DAIP_RS_Database.NDB $FWDIR/conf/robo- gateways.NDB $FWDIR/conf/robo-control.NDB 10. $FWDIR/conf/robo- ike.NDB 11. $FWDIR/conf/InternalCA.NDB 4. If it exists, remove $FWDIR/conf/CPMILinksMgr.* 5. Run the $FWDIR/bin/cpca_dbutil d2u command. 6. Copy the SIC key from the Check Point registry on the production machine to the registry on the duplicate machine, see appendix D for details. Appendix C – How to copy NDB files (Windows to Unix) In Windows platforms the *.NDB files are pointers to another file: 1. Open the .NDB file with a text editor. 2. Find the number of the link which appears after the string __FWNTLINK 3. Copy the .NDB file which includes that number in its NDB suffix, and rename its NDB suffix by removing that number on the duplicate machine. For example: • The file fwauth.NDB contains the line __FWNTLINK3 • Copy the file fwauth.NDB3 from the production machine to the duplicate machine and call it fwauth.NDB 11 Appendix D – Copy the ‘SIC’ registry key 1. Run the following command on the production machine: $CPDIR/bin/cpprod_util CPPROD_GetValue SIC 2. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_SetValue SIC output of the above command> 1 3. Run the following command on the production machine: $CPDIR/bin/cpprod_util CPPROD_GetValue SIC 4. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_SetValue SIC <the output of the above command> 1. 5. Run the following command on the production machine: $CPDIR/bin/cpprod_util CPPROD_GetValue SIC 6. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_SetValue SIC output of the above command> 1. 7. Run the following command on the production machine: $CPDIR/bin/cpprod_util CPPROD_GetValue SIC 8. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_SetValue SIC output of the above command> 1 9. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_GetCpdir. 10. Run the following command on the duplicate machine: $CPDIR/bin/cpprod_util CPPROD_SetValue SIC output of the last command>/sic_cert.p12 1 ICAdn 1. ICAdn 1 <the HasCertificate 1. HasCertificate 4 MySICname 1. MySICname 1 <the ICAState 1. ICAState 4 <the CertPath 1 <the Appendix E – Testing your upgraded machine 1. Start the Check Point software by applying the cpstart command. 2. Open your SmartDashboard client. 3. Make sure all the rule bases, network objects, resources, servers, users and administrators and VPN settings are properly set. 4. Test SIC communication with the modules. 5. Install policy on the modules. 6. Open the SmartView Status. Make sure each module has the proper status. 7. Try to fetch policy from each of your modules by running the fw fetch <management IP> command. 12 Notes and limitations: 1. If both Management Servers are used simultaneously, and changes are done to both, these changes cannot be merged automatically. To synchronize them you will need to manually apply all changes to both. 2. Special care should be given to operations that involve Check Point internal CA modifications, like issuing or revoking certificates. These changes cannot be merged, even manually, and will result in different CA databases on both servers. For example, revoking a certificate on one Management Server will add it to the CRL on that Management Server, but there is no way to add this certificate to the other CRL. It is highly recommended not to perform any such changes as long as both Management Servers are in use. 13
© Copyright 2026