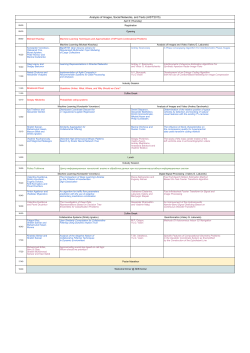
Program |
Program | 13 november
Track 1
10.00
Registration
11.30
Opening
Track 2
12.00 – 12.50
“Is infosec a game?”,
Alexander ‘Solar Designer’ Peslyak
13.00 – 13.50
“Crypto coding v2”,
Jean-Philippe Aumasson
“Hunting for top bounties”,
Nicolas Gregoire
14.00 – 14.50
“Chip reversing”,
Dmitry Nedospasov
“Steroids for your App Security
assessment”,
Marco Grassi
15.00 – 17.00
Lunch
17.00 – 17.50
“Project Heapbleed”,
Patroklos Argyroudis
“DTM components: shadow keys
to the ICS kingdom”,
Alexander Bolshev,
Gleb Cherbov,
Svetlana Cherkasova
18.00 – 18.50
“The past, the present and the
future of software exploitation
techniques”,
Nikita Tarakanov
“Non-cryptographic research of
orthodox cryptographic media,
or How we tested the security of
key data storage on tokens…”,
Sergey Soldatov, Mikhail Egorov
Moscow, Izmailovo Concert Hall, Izmailovskoe Ave., 71, bld. 5
Workshop 1
Workshop 2
“Computer forensic investigation
of {mobile} banking Trojan”,
Boris Ivanov
“Using radare2 framework for
reversing and debugging
malware and firmware”,
Part 1
Anton Kochkov, Julien Voisin
“iOS forensics with OpenSource
tools”,
Andrey Belenko
“Using radare2 framework for
reversing and debugging
malware and firmware”,
Part 2
Anton Kochkov, Julien Voisin
www.zeronights.org
Program | 14 november
11.00 – 11.50
12.00 – 12.50
Track 1
Track 2
Workshop 1
“How to *really* piss off the
surveillance state with your
privacy tool”,
Jake McGinty
“4x4G: from SIM to GGSN”,
Alexey Osipov, Timur Yunusov,
Kirill Nesterov
Defensive Track (20 min)
“Racing with Droids”,
Peter Hlavaty
13.00 – 13.50
“EMET 5.0 – armor or curtain?”,
Freingruber Renй
14.00 – 16.00
Lunch
16.00 – 16.50
“Deobfuscation and beyond”,
Dmitry Schelkunov,
Vasily Bukasov
“DPI as a means of access segregation in a corporate network”,
Igor Bulatenko
“WAF in scale”, Alexey Sintsov
“SMM monitoring guarding the
security of Internet services”,
Karim Valiev
“Building a complex incoming
mail analysis system based on
OpenSource solutions”,
Alexey Karyabkin, Pavel Kulikov
“Preventing mobile malware in
CSP’s network. Android honeypot
for antifraud”,
Denis Gorchakov, Nikolay Goncharov
“De-anonymization and total
espionage”,
Dmitry Boomov
Live discussion
“Unexpected expected
exception: think different about
web-related vulnerabilities”,
Ivan Novikov
“Fuzzer of the State - Evolutionary Black-Box Fuzzing”,
Fabien DUCHENE
FastTrack (15 min)
17.00 – 17.50
“Hardware assisted virtualization
in AV software”,
Peter Kamensky
“Security vulnerabilities in DVB-C
networks: Hacking Cable tV
network part 2”,
Rahul Sasi
18.00 – 18.50
“Your Q is my Q”,
Georgi Geshev
“Miniturization (Fitting a full process control attack into a small
microcontroller)”,
Jason Larsen
19.00 – 19.30
Closing
Moscow, Izmailovo Concert Hall, Izmailovskoe Ave., 71, bld. 5
Workshop 2
“Unsafe factory settings and
firmwares”,
Victor Alyushin
“Parkomagic: substandard look
on parking terminals”,
Denis Makrushin, Stas Merzlyakov
“Hidden timing channels based
on HTTP caching headers”,
Denis Kolegov, Oleg Broslavsky,
Nikita Oleksov
“A pentester’s view of Oracle Database Communication Protocol,
or Rude Oracle experiments”,
Roman Bazhin
“Fast (and almost automatic)
SSRF detection”,
Eldar ‘kyprizel’ Zaitov
“+22: reversing 64-bit binaries
using Hex-Rays x86 Decompiler”,
Vlad ‘vos’ Roskov
“Bypassing kernel patch guard on
Windows 8.1 and Windows 10”,
Artem Shishkin, Mark Ermolov
“Go in a virmaker production”,
Boris Ryutin
“Kernel AddressSanitizer: searching for vulnerabilities in Linux
kernel”,
Dmitry Vyukov
“Roaming tiger”,
Anton Cherepanov
“Deriving cryptographic keys
via power consumption”,
Part 1
Roman Korkikyan
“Deriving cryptographic keys
via power consumption”,
Part 2
Roman Korkikyan
www.zeronights.org
© Copyright 2026