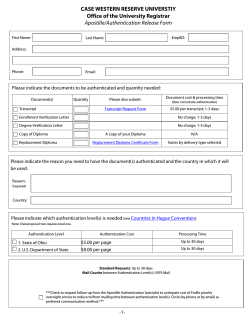
MAKE IT - SC Magazine
APRIL 2015 • WWW.SCMAGAZINE.COM REVIEWED IN OUR GROUP TEST Entrust P39 A jack-of-all-trades when it comes to dual-factor authentication FEATURES: MAKE IT Sharing lessons learned with managers and staff is key to halting breaches, says Lena Smart, CIO, New York Power Authority. P20 Taming the third-party threat The challenge for security practitioners is to make the mobile ecosystem more trustable. P24 Zone of protection To what extent is state-sponsored cybercrime extending the protection for hackers who operate outside U.S. borders? P28 PistolStar P43 Excellent first step into dual-factor authentication VASCO P47 A trusted hardware device for visual transaction-signing VOLUME 26 NO. 4 • April 2015 • WEBSITE WWW.SCMAGAZINE.COM • EMAIL [email protected] A D MIN ACCESS SEC U R E D R Å M NIC U VÅLCE A, R O M A NIA 0 4-2 3-2 01 5 2 A M REGULARS PRODUCT REVIEWS 4 Editorial Giving IT security pros 35 Product section some love. Strong authentication used to mean multifactor. But now we have some special use cases that call for strong authentication, but do not necessarily require multifactor. 8 Threat report Bitcoin exchange CAVIRTEX is shutting down following a database compromise. 10 Threat stats Data of 80 million 36 Group Test: Authentication health insurance clients exposed. It now is feasible for organizations of just about any size to support everyone in the organization with strong authentication. 12 Update The “Equation” group was unveiled by Kaspersky Lab. 13 Debate Your money is safe online. 48 First Look: Bromium vSentry The most creative use of virtualization we’ve seen. 14 Two minutes on… An answer to ransomware? 15 Skills in demand IT pros are needed for web application security. 16 From the CSO’s desk The failure of the security industry, by Alex Stamos, CISO, Yahoo. 17 Opinion Mobile interfacing with Lena Smart, CIO, New York Power Authority P20 IoT, by Jonathan Carter, Arxan. 18 Analysis Strike back on payment HE WILL GET IN. security, by Stephen Orfei, GM, PCI SSC. 19 Letters From the online mailbag. 49 Calendar A guide to upcoming IT security shows and courses. 50 Last word Avoid a network stampede, by Timothy Eades, CEO, vArmour. YOUR FATE WILL BE DETERMINED BY YOUR SPEED OF DETECTION AND RESPONSE. 20 Make it stop! Sharing lessons learned with managers and staff is key to halting breaches, says Lena Smart, CIO, New York Power Authority. 24 Taming the third-party threat The challenge for security practitioners is to make the mobile ecosystem more trustable. 28 Zone of protection To what extent is state-sponsored cybercrime extending the protection for hackers who operate outside U.S. borders? That’s where we come in. LogRhythm’s next-generation security intelligence platform identifies high-impact threats and neutralizes them before they can result in a material breach. It uniquely unifies SIEM and log 32 Fit for a queen: Case study management with network and endpoint forensics and advanced security analytics to provide comprehensive threat life cycle management and the ideal foundation for today’s cyber security operations. Jen Andre P12 IMPROVE YOUR SECURITY INTELLIGENCE POSTURE AT LOGRHYTHM.COM/SIMM FEATURES Alex Stamos P16 Queens College found a solution to monitor activity and manage devices on its network. Cover photo by Susan Woog Wagner Photography SecureAuth P45 Bromium P48 SC Magazine™ (ISSN No. 1096-7974) is published monthly, 10 times a year, with combined December/January and July/ August issues, by Haymarket Media Inc., 114 West 26th Street, 4th Floor, New York, NY 10001 U.S.A.; phone 646-638-6000; fax 646-638-6110. Periodicals postage paid at New York, NY 10001 and additional mailing offices. POSTMASTER: Send address changes to SC Magazine, P.O. Box 316, Congers, NY 10920-0316. © 2015 by Haymarket Media Inc. All rights reserved. Annual subscription rates: United States: $98; Canada and Mexico: $110; other foreign distribution: $208 (air service). Two-year subscription: United States: $175; Canada and Mexico: $195; other foreign distribution: $375 (air service). Single copy price: United States: $20; Canada, Mexico, other foreign: $30. Website: www.scmagazine.com. Haymarket Media uses only U.S. printing plants and U.S. paper mills in the production of its magazines, journals and digests which have earned Chain of Custody certification from FSC® (Forest Stewardship Council®), SFI (Sustainable Forestry Initiative) and from PEFC (Programme for the Endorsement of Forest Certification Schemes), all of which are third party certified forest sustainability standards. www.facebook.com/SCMag www.scmagazine.com/linkedin www.twitter.com/scmagazine Editorial Giving IT security pros some love I n last month’s edition I discussed the conflicting opinions about information security needs that often pervade organizations and how these can negatively impact budget and resources to effectively address these requirements. But even nimble practitioners can only be so crafty when the majority of CEOs and boards of directors don’t really want to hear about the fast-growing intensity of cyber threats. According to the recently released survey, “2015 Global Megatrends in Cybersecurity,” conducted by Ponemon Institute, 78 percent of senior IT leaders responding say they hadn’t briefed their boards on corporate IT security strategies in the last year. Meanwhile, threats loom heavily on the minds of those charged with keeping critical data safe from bad actors. Zero-days and attacks on critical infrastructure are top of mind for respondents to the survey. And, the survey results indicate, the problems confronting CISOs don’t stop there. Another is the shortage of competent IT security pros. About 66 percent of those responding to the survey, which was commissioned by Raytheon, say they need more “knowledgeable and experienced cybersecurity practitioners.” Yet the necessity to find more pros armed with both business and IT security acumen is hitting at the same time that most in the IT security arena are acknowledging a soon-to-be desperate shortage of pros to hire, a fact also pointed out by this month’s cover subject, Lena Smart, CIO of the New York Power Authority. Combine this with a consistently high turnover rate of qualified pros and this challenge to build more solid and expert teams becomes even more complex. SC Awards U.S., happening this month at the RSA Conference, strives to help here by acknowledging the indefatigable efforts of IT security practitioners, as well as the rookie and long-standing product and service providers that support risk management plans and everyday endeavors by calling out outstanding achievements. In June, the SC Awards U.K. will be doing the same for organizations and IT security leaders in Great Britain and Europe. It’s a small contribution we’ve been making to the industry for a number of years that enables us to draw attention to IT security and its leading players. If you’ve never attended (or entered any of our categories), please do consider it. Meantime, this month’s SC Awards gala in California and the other fast-approaching in the U.K. will show IT security pros like you some love. Survey results show y’all could use some. Meantime, I welcome your suggestions on other categories we can consider adding to our SC Awards programs. Illena Armstrong is VP, editorial of SC Magazine. [It’s a] necessity to find more pros armed with both business and IT security acumen...” 4 SC • April 2015 • www.scmagazine.com SC CONGRESS 24/7 SC Magazine has created a free virtual environment that is open year-round. Each month we host online events focused on subjects that you – as an IT security professional – face on a regular basis. THIS MONTH April 9 eSymposium: Mobile security Use of mobile devices in the has forced those 9 enterprise in charge of maintaining the integrity of business networks to consider new security strategies and new tools. All the old assumptions about how to protect endpoints have been under challenge and the threat picture continues to only grow. We examine the most recent developments in the area of mobility and find out some programs that are showing some positive inroads. April 30 eSymposium: Cyberespionage Even members of the U.S. Congress can agree that cyberespionage is a major problem for both the country’s private companies and government agencies. From direct attacks to backdoors, the methods to conduct cyberespionage attacks run the gamut. We take a look at the threat and find out what the U.S. government, private organizations and others are doing to address the problem. FOR MORE INFO For information on SCWC 24/7 events, please contact Jourdan Davis: [email protected] or 646-638-6176. For sponsorship opportunities, email Mike Alessie at mike.alessie@ haymarketmedia.com or phone him at (646) 638-6002. Or visit scmagazine. com/sc-congress-247-whats-new/ section/1223/. SC MAGAZINE EDITORIAL ADVISORY BOARD 2015 Rich Baich, chief information security officer, Wells Fargo & Co. Greg Bell, global information protection and security lead partner, KPMG Christopher Burgess, CEO/president, Prevendra Jaime Chanaga, global consultant and adviser; formerly managing director, CSO Board Consulting Rufus Connell, research director, information technology, Frost & Sullivan Dave Cullinane, CEO, Security Starfish; former chief information security officer, eBay Mary Ann Davidson, chief security officer, Oracle Dennis Devlin, chief information security officer, chief privacy officer and senior vice president of privacy practice, SAVANTURE Gerhard Eschelbeck, vice president security engineering, Google Gene Fredriksen, global information security officer, PSCU * emeritus WHO’S WHO AT SC MAGAZINE EDITORIAL U.S. SALES VP, EDITORIAL Illena Armstrong [email protected] VP, SALES David Steifman (646) 638-6008 [email protected] ASSOCIATE EDITOR Teri Robinson [email protected] EAST COAST SALES DIRECTOR Mike Shemesh (646) 638-6016 [email protected] MANAGING EDITOR Greg Masters [email protected] WEST COAST SALES DIRECTOR Matthew Allington ONLINE EDITOR Marcos Colón [email protected] EVENT SALES DIRECTOR Mike Alessie (646) 638-6002 [email protected] SENIOR REPORTER Danielle Walker [email protected] ACCOUNT EXECUTIVE Ife Banner (646) 638-6021 [email protected] REPORTER Adam Greenberg [email protected] ACCOUNT EXECUTIVE Gabby Brown 646-638-6101 [email protected] ACCOUNT EXECUTIVE Jessica Andreozzi 646-638-6174 [email protected] SALES ASSISTANT Kelli Trapnell 646-638-6104 [email protected] MARKETING DIRECTOR Karen Koza [email protected] EDITORIAL ASSISTANT Ashley Carman (646) 638-6183 [email protected] SC LAB TECHNOLOGY EDITOR Peter Stephenson [email protected] SC LAB MANAGER John Aitken [email protected] LEAD REVIEWER Jim Hanlon [email protected] PROGRAM MANAGER Judy Traub [email protected] REGULAR CONTRIBUTORS James Hale, Karen Epper Hoffman, Stephen Lawton, Jim Romeo (415) 346-6460 [email protected] MARKETING MANAGER Rochelle Turner [email protected] LEAD GENERATION CAMPAIGN MANAGER Jennifer Brous [email protected] SC MAGAZINE LIST RENTAL REACH MARKETING VP, MARKETING SOLUTIONS Wayne Nagrowski (845) 201-5318 [email protected] DESIGN AND PRODUCTION CIRCULATION ART DIRECTOR Michael Strong [email protected] AUDIENCE DEVELOPMENT MANAGER Richard Scalise (646) 638-6190 [email protected] PRODUCTION MANAGER Krassi Varbanov [email protected] SC EVENTS PROGRAM DIRECTOR, SC CONGRESS Eric Green [email protected] EVENTS DIRECTOR Adele Durham [email protected] EVENTS MANAGER Maggie Keller [email protected] ASSOCIATE VIRTUAL EVENTS MANAGER Jourdan Davis [email protected] VIRTUAL EVENTS COORDINATOR Anna Jurgowski [email protected] 6 SC • April 2015 • www.scmagazine.com Maurice Hampton, director, field operations, Qualys Paul Kurtz, partner and chief operating officer, Good Harbor Consulting Kris Lovejoy, general manager, IBM Security Services Tim Mather, CISO, Cadence Design Systems Stephen Northcutt, director - academic advising, SANS Technology Institute Randy Sanovic, owner RNS Consulting; former general director, information security, General Motors * Howard Schmidt, partner, Ridge-Schmidt Cyber Ariel Silverstone, chief security officer adviser, GNN; former chief information security officer, Expedia Justin Somaini, chief trust officer, Box; former chief information security officer, Yahoo Craig Spiezle, executive director and president, Online Trust Alliance; former director, online safety technologies, Microsoft Amit Yoran, president, RSA, the security division of EMC SENIOR MARKETING MANAGER Edelyn Sellitto (646) 638-6107 [email protected] SUBSCRIPTION INQUIRIES CUSTOMER SERVICE: (800) 558-1703 EMAIL: [email protected] WEB: www.scmagazine.com/subscribe MANAGEMENT CEO, HAYMARKET MEDIA Lee Maniscalco COO John Crewe CFO Donna Santarpia DataBank ThreatReport Cybercriminal activity across the globe, plus a roundup of security-related news. Colored dots on the map show levels of spam delivered via compromised computers (spam zombies). Activity is based on the frequency with which spam messaging corresponding with IP addresses is received by Symantec’s network of two million probes with a statistical reach of more than 300 million mailboxes worldwide. MEDIUM-LEVEL ACTIVITIES LOW-LEVEL ACTIVITIES RUSSIA – The U.S. Department of State’s Transna- CANADA – Canadian Bitcoin exchange CAVIRTEX is shutting down following a database compromise. The company stated that it has reason to believe that an older version of its database, which includes two-factor authentication secrets and hashed passwords, may have been compromised. The company believes its reputation has been damaged and it can no longer operate successfully. HIGH-LEVEL ACTIVITIES ONTARIO – The Ontario government inadvertently disclosed the personal information of 720 individuals to third parties. The information included the social insurance numbers of welfare and disability support program recipients, as well as the amount of assistance they received last year. The issue was software related and involved misdirected T5 forms. NETHERLANDS – An international effort by Europol and private companies, including Microsoft, has resulted in the takedown of command-and-control servers for the Ramnit botnet. Additionally, the takedown team redirected 300 internet domain addresses used by botnet operators. Since its emergence, Ramnit has infected an estimated 3.2 million computers worldwide. tional Organized Crime Rewards Program has put a $3 million bounty on Russian hacker Evgeniy Mikhailovich Bogachev for crimes he allegedly committed using Zeus malware. Bogachev – who is said to have used Zeus to steal banking information and empty compromised accounts – is believed to be living in Russia. U.K. – A backdoor into a database MIDLOTHIAN, ILL. – The police department in a Chicago suburb paid an unknown hacker $500 in Bitcoin to regain access to data on a police computer infected with ransomware. An IT vendor that works with the town indicated that only one computer and specific files located on it were impacted, and not the entire department’s system. NEW YORK CITY – A 16-year-old student was able to change his grades after getting through the password barrier and other security on his school’s computer system. The high school junior was charged as an adult with forgery, computer trespass, unauthorized use of a computer, computer tampering and criminal possession of forgery devices. belonging to PaymyPCN.net, which is linked to the Driver and Vehicle Licensing Agency database, allowed the public to access data on nearly 10,000 motorists. The information included names, addresses, emails appealing penalty charges, and photographs taken by law enforcement of motorists and their vehicles. INDIA – A researcher, Laxman Muthiyah, earned $12,500 from Facebook after he identified a vulnerability that allowed him to delete any photo album on the social media website. Muthiyah reported the issue to Facebook, and the social media company applied a fix in less than two hours. Russia top producer of zombie IP addresses For the period reported, the EMEA region (Europe, Middle East, Africa) was the leading source of all zombie IP addresses. Of the countries making up the EMEA, Russia was the top producing country. For the other regions, the top producers were Brazil in South America, the United States in North America and Vietnam in the Asia-Pacific region. Source: Symantec 8 SC • April 2015 • www.scmagazine.com www.scmagazine.com • April 2015 • SC 9 DataBank ThreatStats Zombie IPs Global distribution 1,091,866 5. @MAIL.RU 912,807 12,500 6. Road Runner 780,703 7. American Express почта 706,291 8. Telstra 697,354 Names, Social Security numbers and birthdates of 12,000 Florida residents on a family services waiting list were inadvertently exposed via a PowerPoint email attachment sent as part of a measure for transparency. India 9. Microsoft 686,761 10. LinkedIn 587,161 815,842,526 07/14 08/14 09/14 10/14 11/14 12/14 01/15 02/15 The index queries information security industry professionals monthly to gauge their perceived risk to the corporate, industrial and governmental information infrastructure from a spectrum of cyber security threats. A higher index value indicates a perception of increasing risk, while a lower index value indicates the opposite. Source: ICS, www.cybersecurityindex.com 10 SC • April 2015 • www.scmagazine.com China Russia Taiwan Argentina 5. Zeus trojan Top 5 attacked countries Russian Federation 1.93% United States 11.74% Kazakhstan 1.90% Ukraine 10.38% Qatar 1.76% Russian Federation 6.14% Ukraine 1.71% China 5.31% Algeria 1.68% Spain 4.74% 7.0 6.5 6.0 5.5 5.0 4.5 4.0 3.5 3.0 2.5 2.0 1.5 1.0 06/14 Vietnam Top 5 sources of spam (as of March 10) Rate of change (continuously compounded) 05/14 Iran There were 3,530,44 attacks in the United States last month, primarily originating from Columbus, Ohio; Provo, Utah; New York; Atlanta; and Los Angeles. There were 28,034,962 foreign attacks last month, primarily originating from Amsterdam; Berlin; Bucharest, Romania; Lisbon, Portugal; and Stuttgart, Germany. Source: Dell SecureWorks Source: Privacy Rights Clearinghouse (data from a service provided by DataLossDB.org, hosted by the Open Security Foundation) Index value 03/14 04/14 3. Glupteba trojan Zombie IP addresses are recorded in CYREN’s database as having sent spam in the past 24 hours. These are infected computers (zombies) that are unknowingly sending spam. Based on the IP address, the company can determine the country of the spam-zombie and then sums up the spamzombies per country. Source: CYREN Index of cybersecurity Perceived risk 2,650 2,550 2,450 2,350 2,250 2,150 2,050 1,950 1,850 1,750 1,650 1,550 1,450 2. Gozi trojan 4. Nymaim trojan TOTAL number of records containing sensitive personal information involved in breaches in the U.S. since January 2005: Source: Kaspersky 1. ZeroAccess trojan 2.9% 4. CNBC Top 5 attacks used by foreign hackers 2.9% 2,309,984 5. ZeroAccess trojan 3.8% 3. Google 4. Downloader trojan 4.6% 80 million 9.8% 2,730,784 The second largest health insurance company was infiltrated by a Chinese hacker group known as “Deep Panda,” according to journalist Brian Krebs. He reports the hacking began as early as April 2014. 3. Gozi trojan 7.0%. 2. mail.com Anthem Indianapolis 11.3% 10.7% Type of breach 9.0% Name The Office of Jeb Bush Tallahassee, Fla. 5.0% Number of records 3,635,524 1. Upatre downloader trojan 2. CryptoWall trojan 5.5% 6.2% 1. Facebook Top breaches in February Data loss 8.7% Top 10 names used by phishing websites 9.3% There were 3.5 million attacks in the U.S. last month. Top 5 attacks used by U.S. hackers Jan. Feb. 0 5% 10% 15% 20% 25% 30% 0 1% 2% Source: Kaspersky 3% Source: Kaspersky Internet dangers Top 10 threats Name Movement First observed Type Last month Months on list 1 Upatre.aa p 05/09/14 downloader 0 0 2 Upatre p 12/11/13 downloader 0 0 3 Simbot.gen p 06/29/11 backdoor 0 0 4 Soltern.l p 01/08/11 worm 13 7 5 Tugspay.a Same 07/07/14 downloader 6 5 6 Ogimant.gen!c 09/17/14 downloader 3 2 7 Eggnog.a p 01/15/14 worm 0 0 8 Berbew p 01/31/11 backdoor 0 0 9 Ramnit.i 12/03/10 virus 11 1 10 Ramnit.a 01/05/11 virus 0 0 p Source: Motive Security Labs www.scmagazine.com • April 2015 • SC 11 Update 2 minutes on... An answer to ransomware? P14 Me and my job Finding out what the bad guys are up to next P15 NEWS BRIEFS Web application security pros are needed P15 Equation quake »Researchers disclosed a new SSL/TLS vulnerability, dubbed “FREAK,” which enables attackers to intercept HTTPS connections between vulnerable clients and servers and forces the use of “export-grade” cryptography that can more easily be decrypted. In early March, analysts shared that vulnerable clients include “many Google and Apple devices” that use unpatched OpenSSL, as well as a “large number” of embedded systems and other software products using TLS “behind the scenes without disabling the vulnerable cryptographic suites.” Skills in demand The “Equation” group targeted governments, financial institutions and militaries in more than 30 countries, reports Kaspersky Lab. Kaspersky Lab uncovered what it believes to be the most advanced threat actor the research team has ever seen. The “Equation” group targeted institutions in more than 30 countries dating back to 1996. Early reports suggested that the group and the NSA were closely linked, if not one and the same, and Kaspersky noted that the gang’s most impressive malicious technique was infecting hard drive firmware. »An Arlington, Va.-based security firm uncovered connections between a Chinese cyberespionage group, called Axiom, and the cyber attack against health insurer Anthem. The Anthem breach, which surfaced in early February, exposed the personal information of 78.8 million consumers, including Anthem and Blue Cross Blue Shield (BCBS) members. Threat intelligence firm ThreatConnect found that malware used in a 2013 attack against BCBS was signed with the same digital signature used to spread other Chinese APT malware. Suspicious domains which appeared to mimic Anthem’s infrastructure were also linked to the distribution of a backdoor program used by the APT attackers, ThreatConnect found. THE QUOTE Dyranges [an infostealer]... first appeared in June 2014 and its use has skyrocketed since.” – “The State of Financial Trojans 2014,” Symantec, March 2015 »A hacker group stole as much as $1 billion from 100 banks in 30 countries by distributing a 12 SC • April 2015 • www.scmagazine.com remote backdoor via spear phishing emails targeting bank employees, Kaspersky Lab revealed in February. The group, called Carbanak, is believed to be the same gang that breached Staples last fall. Based on information gathered from its own research in addition to info from law enforcement agencies, including INTERPOL and Europol, Kaspersky Lab said that losses ranged from up to $10 million per bank. Rather than aiming their attacks at accounts belonging to customers, the miscreants went after central sources, such as e-payment systems and banks primarily in Russia, but also in the U.S., Germany and China. »Computer maker Lenovo came under fire for shipping adwareladen laptops to consumers. Furthermore, data security experts with knowledge of the preinstalled adware, called Superfish, revealed that the software leaves users vulnerable to manin-the-middle (MitM) attacks that break HTTPS security. After facing backlash in February, Lenovo apologized for the security blunder and told customers that it had stopped preloading the adware on its laptops. The incident prompted the Electronic Frontier Foundation (EFF) to publish a how-to on uninstalling Superfish and removing the certificate, as the adware installs its own root CA certificate in Windows systems. »Erratum: In last month’s Two Minutes On column, we reported that, according to Gartner, IT security spending would reach the $76.9 million mark in 2015. That figure should, of course, be $76.9 billion. Debate» Your money is safe online. If you make electronic transactions in any form, your money is already online. It doesn’t matter if you never enter a credit into an e-tailer and only shop brick-and-mortar. No business operates without connectivity to the internet. The point-ofJen Andre chief scientist, sales breaches at Target and Threat Stack Home Depot deeply illustrate this. Such breaches are not going to stop happening, and nearly every retailer (online or not) will be vulnerable to them in some way. Given that reality, consumers have some onus to be savvy in choosing who they do business with – and how – to protect their own finances. Fortunately, technology is making advances to help us. Text messages and mobile apps make it easy to monitor your bank and credit card statements, and get alerts instantly when something is suspicious. With the increase of computing power and the rise of machine learning and Big Data, fraud detection is getting faster and better. New payment technologies are reducing the attack surface for potential credit card thieves and ensuring all transactions are safer. FOR THREAT OF THE MONTH AGAINST Unless you have protections, digital awareness and training, consumers expose themselves to risks while banking or purchasing products online. Consumers must learn to choose passwords wisely, change them Cameron Camp frequently and limit their security researcher, exposure. They must also keep ESET sensitive personal information, bank account numbers and passwords in unencrypted form off their phone. On the institutional side, memory scraping on point-of-sale and other related technologies will remain a scourge to payment card participants. Financial institutions view theft in terms of “risk management,” not specifically stopping theft because it’s bad. That is, they assign a value to fund loss and attempt to manage that relative to security purchases. If that equation is at an acceptable level, they feel a measure of success and proceed to other issues. Consumers, on the other hand, think an acceptable level of “loss” would be zero. Lack of full disclosure on breaches, and/or delayed reporting weaken security and trust across the landscape in the interest of brand protection. THE SC MAGAZINE POLL When naming malware, should there be an industry standard when sharing threat information? THE STATS 16% growth in mobile malware in third quarter of 2014. No 5% Yes 95% 76% year-over-year growth in overall malware samples. Komodia libraries What is it? Komodia Redirector and SSL Digestor libraries provide a way for software to intercept HTTPS traffic. This is a feature commonly used by various security products. However, the Komodia libraries contain a flaw, allowing an attacker to spoof the identity of a web server or disclose and manipulate HTTPS traffic through man-in-themiddle attacks. How does it work? The Komodia libraries do not properly validate selfsigned X.509 certificates. Should I be worried? Third-party libraries are used more and more to speed up the software development process and reduce cost. Unfortunately, software vendors rarely secure audit libraries before using them. A number of privacy and parental control software has been confirmed to bundle the vulnerable library. How can I prevent it? Some products have removed the feature or issued fixes. Apply fixes if available or delete the offending program as well as the installed root CA certificate. – Carsten Eiram, chief research officer, Risk Based Security To take our latest weekly poll, visit www.scmagazine.com Source: McAfee Labs www.scmagazine.com • April 2015 • SC 13 Update 2 MINUTES ON... An answer to ransomware? I n recent years we’ve seen increasing numbers of companies fall victim to ransomware that encrypts a compromised computer’s files, threatening to delete them all if a Bitcoin ransom isn’t paid to the attacker. Even police departments have been strong-armed by cyber bullies into shelling out ransom payments. While coughing up the money may encourage attackers to continue their campaigns, it’s tough to blame organizations for either not wanting to lose their data or receive negative press on their security posture. New variants of ransomware keep popping up, skirting anti-virus systems and haunting security pros. Briefs A recent study conducted by Malwarebytes indicates that this is a primary cause for concern. Of the 685 IT decision-makers surveyed, 38 percent indicated that ransomware had the most severe impact on their organization, moreso than advanced persistent threats. The same report also indicates that 84 percent of respondents believe that traditional AV lacks in addressing modern threats. So, is there an answer to this proven threat? For TK Keanini, CTO at security firm Lancope, there’s a logical one: Back up your data. If organizations treated ransomware as “just a drive failure” they’d be better off, he says. “When you look at the economics, it is most of the time cheaper to have a cloud backup system on a yearly subscription than to pay the ransom, and with the backup, you get all the other added benefits,” Keanini says. It may seem like a onesize-fits-all solution, but a recent alert issued by The Internet Crime Complaint Center shed light on a new attack that uses ransomware 84% of respondents say traditional AV is insufficient today. Source: Malwarebytes to drop trojans and keyloggers, thus adding a new layer to this already disruptive threat. Thanks to that attack, miscreants netted more than $179 million from victims in the U.S. and 45 other countries. While it’s essential to ensure enterprises are equipped to handle malware threats, Christopher Budd, threat communication manager at Trend Micro, believes that so long as ransomware’s brutal efficiency and effectiveness surrounding its “data destructive qualities” continues, this threat will likely proliferate in various forms. “Ransomware has shown time and again that it’s more than willing to ‘pull the trigger’ and cause permanent harm and heartache if the criminals don’t get what they want – and sometimes even when they do,” Budd says. – Marcos Colón JOBS MARKET Me and my job Johannes Ullrich dean of research for the SANS Technology Institute How do you describe your job to average people? I am helping an amazing group of volunteers to try to find out what the bad guys are up to next and how we can protect ourselves. Why did you get into IT security? I started out in physics, but ended up doing a lot of “computer work.” Of course, originally security wasn’t really something I thought about too much until my home system was compromised. The more I learned about security and networks, the more I found the dynamic of it more and more interesting. What was one of your biggest challenges? My biggest challenge is to figure out what to focus on. Decisions have to be made quickly. It is always difficult to find the right point to publish findings. If you wait too long, it doesn’t matter anymore. But if you publish too early, you may give people bad advice. What keeps you up at night? I am always worried about the security of my own systems. Offering services and data to the public in the form of dynamic and complex web applications is a challenge that is at times exhilarating and also frightening. The more you know, the more you worry. What makes you most proud? The persistent and longtime positive impact the Internet Storm Center has had on internet security. I am proud to be able to work with an amazing group of volunteers. How would you use a magic IT security wand? The internet-wide implementation of BCP 38 (antispoofing) and, if I had some powers left, the same for RFC 3514, which is just about as likely to happen. Skills in demand With so many visiting the web for social-networking, shopping, banking and paying bills, it’s imperative that companies ensure their web facing applications are secure and free from vulnerabilities. What it takes Mid- to senior-level experience enforcing web application security in all phases of SDLC with the ability to identify, interpret and remediate vulnerabilities found within web applications. Knowledge of the OWASP Top 10, web vulnerability scanning tools and previous web app development skills. Compensation Johannes Ullrich is responsible for the SANS Internet Storm Center (ISC) and the GIAC Gold program. He founded DShield.org in 2000, which is now the data collection engine behind the ISC. Full-time salaries generally range from $90,000 to $135,000 (higher in certain regions and for contractors). Source: Wils Bell, president, SecurityHeadhunter.com Company news »Kurt Takahashi has joined AMAG Technology, a Torrance,Calif.-based endto-end security management solutions provider, as its senior vice president of sales. Takahashi leads the field sales team and helps implement strategies to drive growth and extend customer service. He will report to President Matt Barnette. He most recently worked at Quantum Secure as a vice president of global sales and marketing. While there, he changed the company’s sales » Kurt Takahashi, senior vice president of sales, AMAG Technology approach through purchasing agreements and by increasing customers’ pipeline and account activity. 14 SC • April 2015 • www.scmagazine.com Christopher Bolin has joined Absolute Software, a Vancouver, BC, Canada-based endpoint security and management solutions provider, as chief product officer. Bolin will be responsible for Absolute’s overall global strategy, and the company’s product development and product management teams will report directly to him. Bolin, who has worked in information security for more than 20 years, was previously executive vice president of worldwide product operations and CTO at McAfee. During his time there, he grew security specific product revenues to more than $2 billion from under $500 million. »Emailage, a Phoenix-based fraud prevention provider, has received $3.8 million in funding led by Felicis Ventures. Double M Partners and Much Capital also joined the Series A funding round. Emailage has tripled the number of transactions analyzed over the past year and flagged more than two million transactions as “risky.” » Chenxi Wang has joined cloud platform and transition it to a services-based software model. CipherCloud as vice president of cloud security and strategy. Prior, Wang was at Intel, McAfee and Forrester Research. » » Sean Molloy has joined Tenable Network Security, a continuous networking monitoring company, as vice president of cloud services. Molloy will oversee the operations, deployment, design and architecture of Tenable’s cloud product lineup. Molloy previously worked as the direc- Chenxi Wang, VP of cloud security and strategy, CipherCloud tor of software engineering at Qualys until he was promoted to chief architect. While in that role, he helped deploy the company’s Sydney Carey has joined Zscaler, a San Jose, Calif.-based internet security company, as the company’s CFO. Carey will report to the company’s founder and CEO Jay Chaudhry. She will be responsible for the company’s global financial operations. Carey was named a Bay Area CFO of the Year in 2012 and most recently worked as the CFO of MongoDB. Previous to that, she spent nine year at TIBCO. » PayPal has acquired Israelbased CyActive, which claims its offering – based on an algorithm sourced from biology – is able to foresee and forestall potential cyberthreats. CyActive was incubated by Jerusalem Venture Partners. It also received investment from Siemens. Follow us on Facebook, LinkedIn and Twitter www.scmagazine.com • April 2015 • SC 15 Opinion From the CSO’s desk The failure of the security industry I CISO, Yahoo t is a truth universally acknowledged that a CSO with budget must be in want of a thousand dedicated point solutions. Like many security executives, my email, snail-mail slot, LinkedIn profile and cell phone field a constant barrage of offers from wellmeaning but insanely aggressive account representatives. They arrive in waves from companies big and small. They offer solutions to my data analysis problems, zeroday malware and “advanced APTs.” Any demonstration of reluctance on my part is parried with a quick “Ok, I’ll circle back later.” In my dreams, I squint up at the flock of sales cybervultures, “circling back” until I lose my will to resist their entreaties, or perhaps to live. The problem is not only that these companies build beautiful websites that refuse to explain what they sell and instead wax poetic on their “solutions,” or that their slide decks lecture me on what – The explosion of security needs means the median security engineer in 2015 is less experienced than her counterpart in 2005. Security companies need to recognize that most of their addressable market cannot properly consume their products and that user experience is a bigger priority than getting more checkmarks in a Gartner report. Accept asynchronicity – That’s not an album from The Police, but a mantra that needs to be embraced to provide security services on modern networks. Big Data, cloud and container technologies mean that most enterprises will be deploying 100GbE inside of the datacenter and corporate campus this year. At those speeds, security products have about 6.7 nanoseconds to decide whether an Ethernet frame is malicious or not. Evolve or die, that is the reality facing the security vendors, lest the cybervultures feast. threats I face (“BYOD really means Bring Your Own Malware!”). The problem is that almost none of these products work in a real environment. For the most part, the security vendors I meet believe that IT departments want to run another agent on their Windows laptops, that production engineers are willing to put a cheap Lintel 1U security device in their critical path, and that every company’s security team is staffed like a Top-5 bank. These assumptions are not true. Some ways we can adapt: Build platforms – The activation energy to qualify, purchase and deploy a security solution is not widely variable and for most enterprises the opportunity cost of choosing a product that solves a very small problem outweighs the price. The security industry needs to build reusable platforms with pluggable use cases. Focus on user experience 30seconds on... » Don’t be the next headline Companies are waking up to the fact that their security posture is insufficient to fend off today’s threats, says Stamos. We can no longer build products like it’s 2005. » Hadoop to the rescue Why would I keep many copies of my syslogs in proprietary databases when one standard storage mechanism could be queried by security products from competing companies? 16 SC • April 2015 • www.scmagazine.com » Build solid platforms Why should five separate security agents hook the Windows kernel (and introduce instability) when one collector process could feed intelligence to five products? »Modern service These days, network security has to be pushed into the end nodes, and decisions need to be made at a much slower pace than packets arrive and remediations performed out-of-band. CEO, Caspida I Bad guys are inside t is an assumption for many enterprises operating today that they may already have been compromised. Hackers and bad guys are likely already inside their network. With the increasing sophistication of hackers, organized criminals and cyberhack-focused countries, it is safe to presume that the networks of many enterprises are already breached. Therefore, perimeter-only protection practices are no longer sufficient and firewalls and malware-detection products – while necessary – are no longer sufficient. Today’s enterprise is filled with security tools for which the underlying technology and principles are likely 10-plus years old. These might include firewalls and intrusion detection systems, which operate on known signatures; rule-based detection; malware detection tools using sandboxing techniques; and DLP systems, which look for specific content in the form of keywords within documents leaving the enterprise. Another challenge is that current security products rely on known attacks, standard rules and correlations techniques. This approach is generating millions of alerts and too many false positives. It is unsustainable to go through millions of alerts while relying on manual incident response with large SOC teams. Naturally, this methodology increases time to detection to weeks/months. Worse, these alerts are not actionable. Because security analysts and incident response teams get a flood of alerts from many security products within an enterprise, this creates a phenomenon called “analyst fatigue.” Most of the alerts are not actionable and security professionals have to spend a lot of time reviewing these alerts and developing required supporting evidence. Most recent high-profile breaches involved the continuous use of current-generation security products, yet the attackers were able to infiltrate and exfiltrate data unhindered. There needs to be advanced, deep data, science-driven and machinelearning security technology within the network that detects advanced hack attacks and malware. It is imperative to detect malware that has already penetrated your corporate network. Mobile interfacing with IoT T Photo by J.M. Eddins Jr. Photography Alex Stamos Muddu Sudhakar Jonathan Carter technical director, Arxan Technologies ...avoiding doing sensitive things via mobile devices is not possible...” he security community is abuzz about the risks of reverse engineering code. The overall belief is that it’s a bad thing that can lead to cloning, repackaging, IP theft and other types of attacks. Most professionals believe there really isn’t much that can be done about preventing an attacker from reverse engineering their code. There are many excellent tools on the market that make the task easy and affordable to the adversary. However, there are things that can be done to make reverse engineering a lot more difficult to execute. You can significantly raise the bar for hackers without a lot of effort. Most software engineers and security professionals don’t have the technical background to understand or apply basic obfuscation techniques that make reverse engineering much more difficult for hackers. I suspect that “solution bias” is driving technical communities to avoid addressing the risks of reverse engineering as it relates to the IoT devices and their mobile interfaces. Traditional security advice always recommends avoiding doing anything sensitive on a mobile device. This is wise advice and should be followed if possible. But, avoiding doing sensitive things via mobile devices is not possible when IoT devices are doing sensitive things and exposing that functionality (and associated information assets) via mobile interfaces. In this increasingly common business use-case, we are seeing IoT devices that allow users to see/do things via corresponding mobile interfaces: collect and process medical data, unlock doors, start cars, etc. Hence, the issue of reverse engineering and code tampering of IoT devices and their associated mobile app interfaces must be addressed one way or another. But, let’s be realistic. IoT and mobile are happening because of the business case. Regardless of what people may fear, it’s coming and we’ll have to reckon with reverse code engineering now or it will bite us later. www.scmagazine.com • April 2015 • SC 17 Letters Analysis Strike back on payment security Annual compliance assessments are merely the start of a vigilant security program, says PCI SSC’s Stephen Orfei. M ake no mistake, we are in a battle. Cybercriminals are raiding our financial system. Armed with malware and hacking expertise, they are sneaking by breakdowns in security protocol. Many of these attacks are preventable. The key is grasping how they do it and knowing how to strike back. The common attack pattern – as outlined in Verizon’s “2014 Data Breach Investigations Report” – is hacking into a vulnerable back office PC to implant malware. This paves the way to compromising connected point-of-sale (POS) devices and systems, collecting magnetic-stripe data from live transactions, exfiltrating the stolen data – and cashing in. Many of the breaches so far reported in 2015 have continued using this tactic. So how do you strike back? The PCI Council recommends three tactics: Ongoing vigilance, proactive security and solid preparation. Malware is typically installed because missing or lapsed controls allow access into systems attached to the cardholder data environment (CDE). In many of the recent breaches, attackers exploited remote access methods to implant malware on vulnerable back office systems that typically ran an unpatched older operating system. This is an easily preventable breach of security protocol! Vigilant risk mitigation means your controls must ensure that: Software is frequently patched and up-to-date; configuration settings do not expose devices and systems to exploitation; monitoring includes internal and third-party access to systems in the CDE; and access security includes strong authentication and strong passwords. Ongoing vigilance means you are continually monitoring controls as “business as usual.” These controls are your lifeline for they will identify suspicious activity 18 SC • April 2015 • www.scmagazine.com that may indicate a potential breach – and let you react quickly to remediate vulnerabilities. To ensure strong POS security, your organization should use PCI-approved point-of-interaction devices that encrypt data where it’s captured. This prevents exposure of plaintext cardholder data in these attacks. Also, consult your POS device vendors and IT partners to understand options for strengthening security with point-to-point encryption and tokenization throughout the cardholder data environment. These technologies have the potential to make cardholder data unusable and worthless if stolen. Finally, 2015 is a big year of transition as merchants in the U.S. implement EMV [Europay, MasterCard and Visa] chip cards to There is no silver bullet to security or preventing breaches.” reduce fraud in card-present transactions. Used together with PCI standards, these technologies provide a layered approach to payment security that makes theft of cardholder data a non-event. Often an organization’s approach to PCI security is to focus on passing the annual compliance assessment. But this is just the start of a vigilant, proactive security program. Organizations also need to anticipate and assess new risks in order to get ahead of emerging threats. Ongoing threat assessments and gap analyses will help to identify vulnerabilities and risks – and opportunities to improve security with technologies such as encryption and tokenization. There is no silver bullet to security or preventing breaches. Yet, with a multi-layered approach that includes vigilance in monitoring and managing access, proactively strengthening security at the point-ofsale and actively preparing to meet new threats, your organization can significantly reduce the types of risks that have enabled recent breaches. Take action now and strike back with confidence to ensure the safety of cardholder data. Got something to say? Send your comments, praise or criticisms to [email protected]. We reserve the right to edit letters. From the online mailbag In response to February’s Last Word, The security model is broken, by Craig Shumard, principal of Shumard and Associates: Craig is correct, a new security paradigm is needed to address the realities of the world we live in today. Even using the term “breach” these days is misguided. Today’s enterprise networks are porous. There are so many ingress and egress points that there is really no way to keep the bad guys out. Ask any IT or security worker if he/she can still access the network of the company they worked for previous to their current job. Don’t be surprised that the answer is “yes.” Floating credentials are not uncommon, and as long as that is the case and we are not requiring two-factor authentication then these breaches will continue. This is not about the cost associated with securing sensitive data, it is more about the will to do so and understanding how to get the job done. Ted Heiman This is an interesting argument. Craig Shumard is correct that we need to rethink the security paradigm, but to imply that an influx of spending, technology deployments and regulations with teeth will make a difference is a bit overreaching. We have security in many physical environments and still have security breaches. Banks still get robbed. Cars still get stolen. When you have facilities and systems that either must be open to public access or access public resources, you’re exposed to risk. The goal is always mitigation or risk exposure and diminishing the probability of security incidents. Elimination of security risk exposure and incidents is a practical impossibility. Larry Walsh In response to a feature article in the March issue, Closing the gate: Good article. It’s not enough to monitor for known threats or to rely on stale security products that provide an inaccurate view of the environment. Organizations must focus on detecting data breaches in real-time and respond appropriately. To minimize potential harm, it’s crucial to place controls around sensitive data with DLP tools which can accurately alert and prevent, in real-time, unsanctioned sensitive data extraction thus enabling incident response teams to disrupt, respond and contain a possible APT/ malware attack. Wendy Cohen, CIO/CISO, GTB Technologies Stephen Orfei is general manager of the PCI Security Standards Council. www.scmagazine.com • April 2015 • SC 19 Data breaches MAKE IT Sharing lessons learned with managers and staff is key to halting breaches, says Lena Smart, CIO, New York Power Authority. Steve Zurier reports. M oving into 2015, there’s a general sense of uneasiness in the IT security community. While the Ponemon Institute dubbed 2014 the year of mega breaches, there’s no indication that this year is going to be any better. Dave Frymier, CISO, Unisys John Kindervag, analyst, Forrester Kevin Mandia, SVP and COO, FireEye Donald “Andy” Purdy, chief security officer, Huawei USA Lena Smart, VP and CIO, New York Power Authority Nathan Smolenski, CISO, Zurich North America 20 SC • April 2015 • www.scmagazine.com Lena Smart, VP/CIO, New York Power Authority Photo by Susan Woog Wagner Photography OUR EXPERTS: Intelligence sharing If anything, IT security workers may feel that whatever new risk management program they roll out or security product they deploy, the bar constantly moves higher. Many fear privately that the hackers are winning, and that it’s impossible to stop nation-states, organized crime gangs and amateur hackers out to prove they can access Defense Department systems or Wall Street bank accounts. Anyone and everyone can be hacked – and it often happens without the IT staff even knowing about it. Even the harsh 20-year federal prison sentences handed out to TJ Maxx hacker Albert Gonzalez and credit card scammer David Ray Camez haven’t really proved an effective deterrent. However bleak it may appear, though, the tide started to turn with the Target hack in late 2013. In fact, the Ponemon Institute reports that, following the Target breach, survey respondents said the percentage of senior management who considered data breaches an “extremely high” concern rose to 55 percent – up from just 13 percent. It also didn’t hurt that heads started to roll from the corner offices. Without question, CEOs woke up when they read last year that 35-year company veteran Gregg Steinhafel was forced to resign at Target, and CIO Beth Jacob also lost her five-year-old position. And if Target was a wake-up call, the Sony hack late last year pushed cybersecurity into the mainstream as President Obama weighed in on the issue and even Entertainment Tonight reporters gushed cybersecurity news www.scmagazine.com • April 2015 • SC 21 Data breaches when Amy Pascal, former co-chair of Sony Pictures Entertainment, was forced to resign over revelations about embarrassing emails that were stolen by the hackers. High-profile data breaches have certainly attracted the attention of C-suites, says Nathan Smolenski, CISO for Zurich North America, a global insurance company. He says these incursions have changed the game in terms of exposing the capabilities of nation-state-type threat actors and provided a view into the collateral damage that can occur as part of a large-scale breach with the public release of HR data and emails. “But C-suite awareness has actually been growing over the past five years,” he explains. “They are seeing the importance of increased focus and targeted communication and bringing all key stakeholders to the table, including risk management, privacy, legal and supply chain teams. “The nature of the threat is ever-evolving,” Smolenski says. “Our mission is ultimately to continuously improve our visibility into the assets we protect, increase the cost to our adversary – time, complexity, risk of being caught, etc. – as well as measuring, reporting and effectively eliminating residual risk.” For many, all of these requirements can be confusing and hard to sort out. Cynics may point out that JPMorgan Chase spent tens of millions in IT security and employed 300 people focused on security and it still was hacked. On the other hand, while it was hacked, it had the personnel to remediate the issue and sense to admit that there was a problem, 55% After the Target incident Before the Target incident Source: Ponemon Institute 13% which ultimately changes how his security team delivers awareness and targeted information throughout its business units – such as providing awareness to executives about wi-fi attacks to ensure that individuals traveling to high-risk location are outfitted with the proper equipment. 23% 3 or 4 8% 1 or 2 28% 26% 22 SC • April 2015 • www.scmagazine.com – Kevin Mandia, SVP and COO, FireEye The Target breach in November 2013 served as a wakeup call for senior management. Level of concern runs from 1 = none to 10 = significant concern. 9% SOURCE: Ponemon Institute, “2014: A Year of Mega Breaches,” January 2015 Know what matters most and protect it.” Senior management’s data breach concern 5% eBay: 145 million people affected JPMorgan Chase: 76 million households and 7 million small businesses Home Depot: 56 million cards CHS Community Health Systems: 4.5 million people Michaels Stores: 2.6 million people Nieman Marcus: 1.1 million people At stake “Risk management is our business,” says Smolenski at Zurich North America. “Top management makes it their business to understand what is at stake. Management is made aware of the types of vulnerabilities, their probability and the implications of an incident.” Key executives at Zurich, he says, are informed of the latest threat activities, 11% THE YEAR THAT WAS: 2014 mega breaches hundreds of millions of endpoints for hackers to attack. Finally, Frymier says there’s a general rush by software makers to bring products to market too quickly. “Companies push product out the door as fast as they can with the lowest cost,” he says. “The result is that a lot of software is full of vulnerabilities.” In the long run, he says, all of these issues will have to be addressed in order for the industry to make progress on breaches. 22% Only the serious need apply Much of this publicity and the focus by the press on the next “9-11 event” that will affect the security industry troubles Lena Smart, vice president and CIO of the New York Power Authority (NYPA). “I really don’t respond well when people compare these hacking attacks to 9-11,” she says. While it’s regrettable that personal information and credit card data was stolen in these recent incursions, there was no loss of life, she says. Smart, who worked for more than 11 three steps to protect their organizations: years as NYPA’s CISO before assuming discover and classify their data; gain the CIO position, knows what she’s visibility into the company’s internal talking about. Along with her role network; and deploy data encryption and at NYPA, Smart serves as the power tokenization. industry sector chief for the New York “I really wish that more people State chapter of InfraGard, understood that there are a partnership between real consequences to not the FBI and the private doing anything,” Kindervag sector, where she receives says. “But people don’t briefings on cybersecurity put alarm systems in events from the FBI and their homes until they get shares lessons learned with burglarized.” other IT managers and FBI Meanwhile, Dave officials. Frymier, CISO at Unisys, She says following the an information technology Sony hack, she met with company based in Blue top management at NYPA Tom Smedinghoff, partner, Bell, Penn., says while it’s Edwards Wildman Palmer and explained to them important to encrypt data that the FBI believed the hack was tied and deploy two-factor authentication, to North Korea and how her security companies also need to support their IT program at NYPA puts the organization departments. “What Target did was like in a strong position to withstand an attack. planting a vegetable garden with a shovel, “I told them we use a combination of rake and hoe, but not have anyone to tend data encryption, complex passwords and the garden,” he says. “They bought some identity and access management tools tools, but they made no investment in that weren’t necessarily applied to the human resources to learn how to manage same extent at Sony,” Smart says. IT security.” NYPA also has an aggressive security Better and more universally applied education program. Anyone who enters crypto can help, but Frymier points to the organization, whether it’s their first three main factors that have led to the day on the job or are there as a visitor rise of data breaches. First, he says when or contractor, is trained in IT security. the internet was first developed it ran Further, Smart will run unannounced on unauthenticated and unencrypted phishing attacks throughout the year packets. A packet is authenticated when to raise awareness so staff understands its origin is known and verified. Packets better what to look for. She also does can be authenticated by sending a digital “brown bag” lunches with the rank-andsignature (generated with a digital file staff where she offers tips on how certificate unique to the sender) along to spot a suspicious email that may be a with it. phishing attack or contain malware. “In the early days of electricity, “We do videos of these sessions houses were routinely outfitted with and people who may have missed the bare wire,” he says. “As you can imagine, presentation are encouraged to watch many burned down. Fifty years from and learn what’s going on,” she says. now, the notion that we are sending around unauthenticated and unencryptA focus on crypto ed packets will seem as absurd as wiring The techniques that Smart uses at NYPA houses with bare metal.” Second, he says standardization are accepted best practices that most has been a double-edged sword. For experts recommend. John Kindervag, example, Microsoft Office is universal a Forrester analyst who focuses on IT at most corporations, but it also created security, says companies need to take 5 or 6 7 or 8 9 or 10 and then move on. Kevin Mandia, SVP and COO at FireEye, a Milpitas, Calif.-based network security company that has often been the “go-to” vendor for remediation following high-profile hacks, says what really needs to change is the idea that the victims have done something wrong. “Organizations are compromised all the time, often without them knowing it,” he says. “When you’re talking about a nation-state hacking into an educational institution or a media or financial company, it’s really an unfair fight.” Above all, Mandia says companies need to prioritize which information and data is most valuable. “Know what matters most and protect it,” he says. There are many components to protect data, adds Smolenski. “While encryption, password complexity and the management of identity are important, they certainly are only a few pieces to the puzzle.” Having the capability to proactively understand the motive, intent and capabilities of adversaries, being aware of vulnerable conditions, and maintaining continued discipline in all of the security and technical operation activities can go a long way in appropriately managing risk, he says. With all these latest developments, consequently, there are jobs aplenty in the security field. It’s just a matter of finding the right people to fill the posts. “As for security becoming the hot career, while the industry needs people, what we really need are people who are ready to roll up their sleeves and do the hard work. I’m still finding it hard to find qualified people,” Smart says. CISOs and CIOs may not be able to make the hacks stop completely. But they can certainly apply the best possible tools and work with top management to identify the data and intellectual property that matters most to the organization. Short of an incident in which there’s a loss of life, the primary concern may not be about what was lost or stolen, but more about how the organization responds. n www.scmagazine.com • April 2015 • SC 23 Application security TAMING THE THIRD-PARTY THREAT T hey are ubiquitous. Apps, the new short-form word, describes the thousands of software applications designed to run on mobile Android or Apple devices. From kids to corporate CEOs, everyone with mobile technology has come to depend on apps to perform tasks that range from basic to arcane. Given that most are either inexpensive or free, they have been a temptation that is simply too hard to resist. But all is not well in this Garden of Eden. Security professionals have long fretted over their lack of insight into the source of apps or their sometimes nefarious nature. On top of this formidable challenge, social media, a nearby element in the mobile technology spectrum, is also problematic. Last year, for example, a security researcher discovered a vulnerability in Twitter, since repaired, that allowed applications to access users’ direct messages without their knowledge. The vulnerability exploited users who signed into third-party applications using their Twitter credentials, a common authentication capability offered by many web and mobile apps. In fact, many apps use Twitter handles or other social media identities for sign-on – both on PCs and on mobile devices. Everyone is worried, or so it seems. According to “Advanced Malware Detection and Prevention Trends,” a report by Enterprise Strategy Group, an IT research, analysis and strategy firm based in Milford, Mass., mobile security monitoring weaknesses and application security are the top concerns of those surveyed. So, just how risky are apps? A 2014 study from Symantec reported that vulnerabilities discovered within an operating system (OS) are not the main focus of attacks. Rather, it is the top layer of the security stack – the application layer – that is the primary point of risk within a mobile device. Another study of app vulnerabilities comes from the folks at Appthority. Its researchers studied the activities of the top 400 mobile apps – including the top 100 free apps and 100 paid apps for both of the most popular mobile platforms, iOS and Android. Among other things, the report found that the popular perception that iOS devices 24 SC • April 2015 • www.scmagazine.com The challenge for security practitioners is to make the mobile ecosystem more trustable, reports Alan Earls. are a “safer” choice was not supported when it came to relevant app activity. In fact, Appthority saw consistent risky app behaviors across both platforms. The company also found the top risky app behaviors for both operating systems most often fall into one of two categories: sensitive data being captured and sensitive data being shared. Significantly, it’s not just personal data but also corporate data that may be at risk. In general, the company concluded that free apps are the most problematic, generating the most risky behaviors. Perhaps not surprisingly, Appthority also found that free apps aren’t really “free” to consumers in that developers often earn compensation by routing user data to third parties, such as advertising networks and analytics companies. In fact, the authors noted that app developers, in an effort to expand their customer base, often transmit the contacts or even the full address book located on the device. Of course, if a device is connected to a corporate desktop, it could potentially be permitted to sync with contacts from Outlook, many of whom are contacts actually owned by the organization. In short, mobile apps are the quintessential Pandora’s box, chock full of woes for the unwary. Jon Oltsik, an analyst with the Enterprise Strategy Group, sees the challenges in the explosive growth of applications used on mobile devices and he says organizations have to formulate responses for both consumer applications and business applications. He says organizations are addressing this growth in several ways. Some segregate devices and networks between consumer and corporate use. “In the best case, nothing from the consumer side ever touches the corporate side,” says Oltsik. They also do things like application reputation checking to assess the riskiness of consumer applications. “Based upon this knowledge, organizations may force users to uninstall applications or disallow their use on the corporate network,” he says. Overall, the key issue is whether business or consumer applications have or should have access to sensitive data. “This could be contact lists or it could be regulated data,” Oltsik explains. “The first thing you have to do is understand what data the application wants access to.” Once you know this, he says admins can build in controls, like VPNs and data encryption, and then monitor activity to detect anomalous or suspicious behavior. When it comes to app security, authorization is where a lot of the problems start, according to Tyler Shields, a senior analyst at research and advisory firm Forrester. When authorization occurs through a common social platform, such as Facebook or Twitter, there is a clear tradeoff between user experience and security. “The most secure option would be to have high-strength, two-factor authorization that is specific to each property,” says Shields. But user experience is horrible when you do that, he adds. Therefore, at some point admins must be willing to centralize and federate identity in exchange for ease of use. “That is what consumers are saying. They don’t want to deal with 20 passwords. They want one, or a password safe that remembers them, or they want to use Facebook or Google.” McAfee, for one, offers personal password managers that aim to provide the convenience of single sign-on but with a lot more Application security security built in, notes Gary Davis, chief consumer security evangelist at security technology company McAfee. Further, many businesses are adopting a similar approach by offering enterprise identity, with one log-in that is federated across the enterprise. Forrester’s Shields says federated enterprise sign-on is growing more popular. For example, users can now federate one’s ID into the cloud and let a provider, such as Ping Identity or Okta Identity Management, handle it. Conceptually, notes Shields, this should be even better than consumer-grade federation because it will be designed for situations where there is fiduciary responsibility. However, he adds, “they are going to be better, but they are still a single point of failure.” Although those corporate approaches could be configured to also include access to popular consumer apps and sites, as a rule, notes Shields, they are reserved for enterprise functions. Where are the vulnerabilities? Shields says there are two types of app issues: security flaws and privacy problems. The security flaws are not that different from traditional PC code or web code flaws. Those problems could lead to a single issue or a mass compromise. However, there are two components to worry about in mobile apps: the client side and the server side. Servers will be using JSON [JavaScript Object Notation, a lightweight data-interchange format] or some other API so the client can request data, Shields explains. Naturally, a flaw on the client side is less serious than a flaw on the server side. The privacy pieces are completely different because they stem more from the client side than the server side, he says. For example, an app could try to get information from all the sensors on a mobile device – like GPS, RFI and Wi-Fi connection – as well as contacts, calendar information, health and payment capabilities. “An app can then try to send out the information to an advertising group or a library or even a malicious hacking entity.” they can’t secure it. “However, you need Of course, the builder of the phone or app to do this in an automated fashion,” says also may access this information in ways Shields. “Without that you can’t possibly that the user probably didn’t explicitly keep up with the pace of change.” approve, Shields says. To that end, he advises admins Or did they? In most cases, Shields to inventory every app in their says, users mark a check box or two environment. “Once you know, you when they acquire an app, indicating can build out profiles of acceptable their agreement with terms and risk for specific apps and for specific conditions. But these end-user license user segments.” For agreements (EULAs) example, executives are flawed at their may be allowed to do core in Shields’ view. certain things – or not. Few users read or Admins, he points out, understand them. might not want location Many simply don’t care. data to be available Thus, when a consumer for CEOs. Or perhaps installs an app, they are location data for people frequently giving a wide involved in delivering range of permissions. packages might be “In some cases, the deemed too sensitive. app developers may not Each group will have even know how this a risk threshold which works or what might Jon Oltsik, Enterprise Strategy Group must be mapped to the happen to the data,” privacy impact of each app. It is typically says Shields. And there may not be any a complex and time-consuming activity simple technical fix as long as most users that demands automation. either ignore the EULA or simply agree. Fortunately, he notes, there are lots of That may make app vulnerabilities, off-the-shelf offerings, such as a mobile whether caused by poor engineering or by onerous EULA agreements, a real device management (MDM) system, public policy problem. “I don’t feel which can provide a good overview developers are incentivized enough to of one’s environment. Some can be write secure code because the negative integrated with reputation systems, such repercussions of unsecure code are as Veracode and Appthority, so that the minimal,” says Shields. “And for users, a application and its risk rating can be lot of it depends on individual sensitivity contained within the MDM. “If you are to privacy. So, developers don’t feel their going to allow apps into the highest risk code needs to be submarine tight.” segments, you will want to do a security Instead, they prioritize getting to assessment, too. For example, a static market fast, before someone else gets analysis of the code,” notes Shields. there. “I’m afraid better app security At this point, he says most organizamight have to come down to litigation tions lack maturity. Many are just or regulation,” says Shields, citing the starting to figure out policies on BYOD planned addition of chips to credit cards and MDM, just starting to understand in the U.S. in order to improve security, security at the application layer, and which is a government mandate rather just starting to grasp their application than something demanded in the market. count and the types of applications For enterprises, the first step is in their environment. Few have done knowing what is there. That is achieved by user segmentation and risk threshold implementing an inventory of all the apps assessment. And fewer still have created in the enterprise’s environment –because policies, procedures and full automation. if the admin doesn’t know what is there, “All that takes time,” Shields says. 26 SC • April 2015 • www.scmagazine.com An alternative can be to try to simply keep devices out of the organization or sharply limit their use. This can be done, but in most companies with a lot of younger employees, this can damage morale and probably lose people, says Shields. Because of that, some enterprises have just given up and gone “open.” But that’s not a good response for the security practitioner. “The answer is to think through the challenges and match the risk threshold to user expectations,” says Shields. “It is a long process and you can’t flip it on in a day.” The people problem With so many users and devices, a big challenge is people. “Consumers do not have the same level of security controls and security technology as the enterprise,” says Mike Spanbauer, managing director of research at NSS Labs, a security research and advisory firm with headquarters in Austin, Texas. As a consequence, he says, these devices should never be allowed directly on the trusted network. “There is always a risk of compromise to the user when utilizing commercial applications for identity management. Consumers must practice security awareness for their personal safety,” he says. And complicating the user experience is the issue of email. “There are emails people receive on a mobile device, where they are typically rushed and not careful,” says Gordon MacKay, EVP/CTO for Digital Defense (DDI), a San Antonio, Texas-based provider of managed security risk assessment solutions. There is no silver bullet, he points out. Rather, in this scenario, users are particularly vulnerable to phishing or instances where people, especially using single sign-on, may inadvertently convey permissions, he says. McAfee’s Davis recommends engaging employees in the effort. For example, people often download apps that they never or rarely use. Asking them to reduce their app count or at least reduce those that share a common or “social” sign-on can cut risk significantly. Businesses need to allow the use of personal devices, but...” – Mike Spanbauer, NSS Labs Adam Ely, COO and co-founder of of business applications and information Bluebox Security, a San Francisco-based from personal applications and mobile solutions firm, says many security information,” Spanbauer says. teams overlook social media apps because Ely recommends that companies work they are personal in nature. “Since there with employees to understand their needs has always been a risk of employees and adopt the technologies that make over-sharing information via email and them more productive. Furthermore, any forums, teams tend to treat this problem app with company data has to be thought as an existing issue and don’t focus on of as a business enabler and a potential it too much.” However, he says a lot risk, and the company must determine if of organizations are drifting to social the risk is real and acceptable or not. messaging apps for internal communicaIt comes down to distinguishing tions since they are easier to use, everyone identities. “The dynamics of cybersecuhas them and they are outside of the rity have changed and identity is company’s data archiving and monitoring. becoming the new perimeter,” says Then there are the efforts to make the Ken Ammon, chief strategy officer ecosystem more trustable. It may not of Xceedium, a Herndon, Va.-based prevent all problems, network security but it provides a software company. “The baseline mechanism idea that there is an for imposing order. inside and an outside In that vein, there to a system has broken are industry efforts, down,” he explains. such as the FIDO “It is really a mesh (Fast IDentity Online) of interconnectivity Alliance, formed in 2012 whereby people use to address the lack of mobile devices to access interoperability among corporate data and go to strong authentication Facebook.” devices. The group is Moving forward, working to develop Ammon says the Mike Spanbauer, NSS Labs specifications that define underlying effort needs an open, scalable, interoperable set of to be to separate identity, authentication mechanisms that reduce the reliance on and authorization so that users get what passwords. they need. “I am encouraged to see what However, the fundamental problem is Apple is doing with payments,” he says, reliance on the consumer to understand referring to the company’s new Apple how authentication and access works Pay mobile-payment system. “It seems in an open environment and who owns like we are finally moving in the right what information. Rogue apps exploit direction at the consumer level. But the this lack of awareness to bypass a rate of adoption will have to catch up,” system’s security controls. he says. n “Businesses need to allow the use of personal devices, but they should do so A more extensive version of this article is in a manner that provides for separation available on our website. www.scmagazine.com • April 2015 • SC 27 Hacker havens ZONE OF PROTECTION To what extent is statesponsored cybercrime extending protection for hackers operating outside the U.S.? Karen Epper Hoffman investigates. W hen considering the impact of globalization, organizations nowadays must not only think about reaching out to people in other parts of the world, but also who is reaching back. Increasingly, cybercrime is not just being perpetrated by hackers and syndicates within U.S. borders, but those that operate outside them. And, many of the countries where these online attackers operate are either actively supporting them, or at the very least, allowing them to thrive and perpetuate their crime. “Russians, for example, turn a blind eye to a lot of crime, they have a more permissive attitude toward organized crime,” says Gary McGraw, chief technology officer at Cigital, a software security firm based in Dulles, Va. “The government looks the other way.” Russia and a number of countries in Eastern Europe initially emerged as hacker havens – areas of the globe where cybercriminals could ply their trade without worrying that the government or state law enforcement would crack down on their work, or 28 SC • April 2015 • www.scmagazine.com ...intrusions are...the state’s global strategy...” expend much effort to extradite them to the United States or other countries that would penalize or jail them. Why here? Eastern Europe has been a haven for cybercriminals since the internet – Andrea Little Limbago, Endgame began, according to Rick Howard, chief security officer at Palo Alto Networks, a network security company based technology officer and SVP of Blue ties – are creating more of these hacker in Santa Clara, Calif. “Many of these Coat Systems, a Sunnyvale, Calif.-based hotspots throughout the globe. “It countries have excellent engineering provider of security and networking really comes down to there being a schools [and] when the wall came down solutions. The whole discipline is climate that’s conducive to the proliferain 1989, there was no work for these becoming more professionalized in tion of cybercrime,” says Casey Ellis, brilliant engineers,” he says. “Some of these countries that support it, he says, CEO and co-founder of Bugcrowd, them went into cybercrime in order to pointing up the improved quality of a San Francisco-based vulnerability make a living. Some organized crime phishing emails with fewer misspellings assessment company. “Of course, not factions scooped these technicians up to or tell-tale signs of their point of origin. everyone with cybersecurity chops in add cybercrime to the portfolio.” Criminals based in these hacker havens, these parts of the world are malicious, Johannes Ullrich, dean of research for he says, are getting far more sophisticatbut this does somewhat explain the the SANS Technology ed about writing in the local language of concentration of gifted Institute (STI), which the countries where they are perpetrathackers in those parts educates managers ing their exploits. As well, they and of the world.” and engineers in putting in false clues, making it harder Kevin Epstein, vice information security president of advanced practices and security and governance techniques, and for Proofpoint, a OUR EXPERTS: chief technology Sunnyvale, Calif.-based Border patrol officer of the provider of SaaS and SANS Internet on-premises solutions, Casey Ellis, CEO and co-founder, Storm Center, agrees. “Any city or Bugcrowd a division of geographic region that Kevin Epstein, vice president of STI which hosts smart people with advanced security and governance, keeps track access to computing Proofpoint Hugh Thompson, CTO, Blue Coat Systems of malicious technology will breed Rick Howard, chief security officer, activity on hackers,” he says. Palo Alto Networks the internet, agrees that “Whether those hackers choose gainful Rodney Joffe, SVP, senior Russian and eastern legal employment or a life of crime technologist and fellow, Neustar European cybercrimidepends on the same factors that would Andrea Little Limbago, principal nals often work influence residents to pursue legal or social scientist, Endgame together, creating illegal activities in the physical world. As Marc Maiffret, chief technology “a strong criminal has been proven over centuries, a poor officer, BeyondTrust infrastructure… economy and minimal law enforcement Gary McGraw, chief technology with a good range of technically savvy presence can push even honest citizens officer, Cigital individuals.” into committing criminal acts.” Vikram Phatak, CEO, NSS Labs But the threat is no longer isolated Hugh Thompson, chief technology to a single region, or even a single class State sponsorship officer and SVP, Blue Coat Systems of nefarious groups. In countries like In some countries, particularly Iran and Peter Tran, senior director for the China, Ukraine and Iran, and some China, the offensive capability can be a advanced cyber defense practice, RSA countries within the Pacific Rim, South direct result of sponsorship by the states Johannes Ullrich, dean of research, America and Africa, a tolerance for themselves, Ellis adds. Increasingly, SANS Technology Institute; chief fraudulent activity combined with the malware distribution is “controlled by technology officer, SANS Internet emergence of more skilled engineers – the nation-state and the highest bidder,” Storm Center who may lack for legitimate opportuniaccording to Hugh Thompson, chief www.scmagazine.com • April 2015 • SC 29 Hacker havens for companies and law enforcement to trace malicious code back to the source. As a result, we will see two distinct kinds of havens for internet-based criminal activity, says Andrea Little Limbago, principal social scientist at Endgame, an Arlington, Va.-based vulnerability research firm, and co-author of a whitepaper, “Operational Cyber Intelligence,” for the Intelligence and National Security Alliance (INSA). She believes countries like Ukraine and Belarus are havens for non-state criminal networks, whereas Iran, China and Russia are havens for state-sponsored espionage. The low barriers to entry and weak economies make criminal behavior on the internet a relatively easy, low-risk, high-reward alternative to traditional crime in places like Eastern Europe, where criminals are motivated by opportunity, she says. Conversely, groups in Iran, China, and Russia are usually either state-sponsored or motivated by nationalism. These groups have emerged to lead cyber-espionage efforts on behalf of their states’ economic or military interests. Attacks emanating from these hacker havens are not only growing in number and sophistication, but are increasingly becoming more high-profile, more adversary, they must instead make it extremely difficult for them to operate. Specifically, he recommends deploying security controls at each point in the kill chain; configuring and adapting each security control to function properly; regularly capturing metrics for each t is hard enough to combat the existing cybercrime threat on our deployed security control so that the security department can conown home turf – with the weight of local and federal law weighfirm that it is doing what it is originally designed to do; and reviewing ing in support. But how can organizations hope to limit the efinitial design considerations and making the appropriate changes. fect of malicious hackers who operate far from the reach of U.S. law While organizations have no control over these malicious attacks, and under the protection of their own sympathetic governments? managing their own vulnerabilities and response is key, says Casey Many experts say that the first step is understanding that it Ellis, CEO and co-founder of Bugcrowd. “Identify your assets and might not be a matter of if, but when, these foreign hackers will prioritize their protection. Determine where your vulnerabilities are come calling. – in your code, your networks and your processes – and run through “I believe that these days there isn’t a single company in the scenarios within your company to determine how you’d react and United States with more than 50 employees that hasn’t already what would happen if a breach were to occur,” he says. been compromised in some way,” says Rodney However, companies will likely need the Joffe, senior vice president, senior technologist support of the U.S. federal government and law and fellow for Neustar, a Sterling, Va.-based firm enforcement if they want to slow the forward that provides real-time information and analytprogress of activities at the source. “Companies, ics. “Unfortunately, a lot of companies refuse to industries and governments must find a way to believe that.” adjust the cost-benefit calculus using tools of Government protection, or even support, has cyber, diplomatic, legal and economic statecraft,” boosted these adversaries to the point that typisays Andrea Little Limbago, principal social cal counter-measures simply will not do, accordscientist, Endgame. Currently, there are ecoing to Peter Tran, senior director for the advanced nomic sanctions against Russia, Iran and North cyber defense practice at RSA. These criminal Korea – three of the leading countries involved in elements have an unprecedented business model state-sponsorship of digital economic and intelthat legitimate businesses can’t keep up. “Comlectual property theft against the United States, panies, industries and governments have used she points out. Additionally, the FBI just placed a Rodney Joffe, senior vice president, traditional approaches to cyberdefense that have senior technologist and fellow, Neustar $3 million bounty on Evginy Bogachev, a Russian been reactive as opposed to intelligence-driven,” hacker and the world’s most wanted cybercrimihe says. nal, and Senator Mark Warner (D-Va.) recently called for increased And, as the Internet of Things seeps into more areas, the attack efforts to combat cybercriminals in Ukraine as a condition for a surface for foreign hackers will only increase, says Hugh Thompson, military aid package to that country, says Limbago. chief technology officer of Blue Coat Systems. “Integrating cybersecurity cooperation into other forms of coopA lot of the advice offered by experts is just for organizations to erative agreements can impact governments harboring non-state operate solid, standard cybersecurity hygiene and protocol. Rick sponsored criminal groups as well,” Limbago says. “All of these Howard, chief security officer at Palo Alto Networks, says that tactics – both sticks and carrots – must be thoughtfully employed since organizations will never be able to keep out every advanced to impact the risk calculus of adversaries.” – KEH FIGHTING THE HIDDEN FOE: Integrating cybersecurity I 30 SC • April 2015 • www.scmagazine.com damaging and harder to root out. Ellis points up the widely publicized, and highly embarrassing, hack on Sony’s internal systems, which has been attributed to North Korea, as well as Operation Aurora, a series of information security attacks against Google tracing back to 2009, which reportedly came from groups in China. Since many of these emerging hacker havens have poor relations with the United States, or have a wide base of citizens that dislike U.S. policies, there is a ripe climate for these attacks to be directed toward U.S. companies, government agencies and private citizens. Global strategy In countries like Iran, China and Russia, governments employ digital statecraft externally as part of espionage campaigns, but also internally as part of propaganda or information suppression campaigns, Limbago says. “Computer intrusions against adversaries are not only condoned, but are also supported and perceived as a legitimate aspect of the state’s global strategy,” she adds. Russia condones the global bank breaches with ties to Russian-based groups, while also hampering law enforcement efforts. Particularly in the former Soviet bloc countries, Limbago says that states will often turn a blind eye to criminal activity, even if they aren’t necessarily protecting the transnational groups perpetrating the crime. The government of Ukraine, for example, was recently linked to $1 billion in global banking heists executed by individuals hiding out there. Chinese hackers have been implicated in cyberattacks on the U.S. Office of Personnel Management, the U.S. Postal Service and National Weather Service, and the theft of F-35 jet fighter blueprints from Lockheed Martin and its contractors, as well as exploits against steel industry companies such as Alcoa, U.S. Steel and Westinghouse. Indeed, Howard says that China has Identify your assets and prioritize their protection.” – Casey Ellis, Bugcrowd been famous for cyberespionage ever since TITAN RAIN, the code name that the U.S. Department of Defense used to label cyberespionage activities from the Chinese government, became public in the early 2000s. Meanwhile, system breaches of the White House and U.S. State Department unclassified networks, Neiman Marcus and J.P. Morgan Chase & Co. have been traced back to groups in Russia. Similarly, the cyberattacks on Home Depot and Target, as well as the pernicious Zeus malware can be linked to groups or individuals in Eastern Europe. Groups in Iran were implicated in a series of denial of service attacks on U.S. banks in 2012. There are examples of hackers in Ukraine, Russia and the United States, says Marc Maiffret, chief technology officer for BeyondTrust, a a global cyber security company based in Phoenix. “And, of course, no day goes past where an attack isn’t linked to China.” It’s not just a matter of sophisticated state-sponsored hacking mixed with everyday cybercrime, according to Maiffret, but also that foreign intelligence agencies will do things like hacking or leveraging existing cybercrime networks or botnets in order to piggyback these systems and better blend in with the noise. Vikram Phatak, CEO of NSS Labs, an information security research and advisory company based in Austin, Texas, is increasingly seeing a blending where cybercriminals are “reservists” for their governments. Pakistan and Syria are just the latest hacker hotspots that Phatak has seen emerge. And, this widespread protection is also paving the way to more sophisticated exploits. State-sponsored hacking does not necessarily create centers for protection, but what they do is create a resource-rich environment to support globalized attacker anonymity or obfuscation, says Peter Tran, senior director for the advanced cyber defense practice at RSA, a Bedford, Mass.-based computer and network security company. “It achieves this by creating economic ecosystems for cybercriminals and nation-state hackers to collaborate, partner or use a globalized channel over the internet to monetize malware as a commodity.” Enabling criminal behavior Industry observers say that these hacker havens will continue to evolve and flourish. Mideast warriors ISIS (the Islamic state of Iraq and Syria) is gaining traction with its digital activities, and given the established nexus between criminal groups and terrorist organizations, it seems likely that they will explore digital theft and espionage as well, according to Limbago. Similarly, Latin American drug gangs, such as Los Zetas and the Sinaloa cartel, have a similar organizational structure to groups in Eastern Europe and have demonstrated criminal activities in the cyber domain. There also are signs of Russian organized crime syndicates in places like Peru that could transfer their knowledge to local groups, exploiting some of the under-governed spaces and government corruption, she says. “Many of these countries are particularly susceptible,” Limbago adds, “because they have an IT infrastructure that is mature enough to enable cybercriminal behavior coupled with weak rule of law and preexisting criminal networks.” n www.scmagazine.com • April 2015 • SC 31 Case study FIT FOR A QUEEN Queens College found a solution to monitor activity and manage devices on its network, reports Greg Masters. T he list of its alumni who rose from humble beginnings to prominence stretches from Robert Moog, the inventor of the Moog synthesizer, to musicians Carole King and Paul Simon and comedians Joy Behar, Roy Romano and Jerry Seinfeld. But none of these distinguished figures ever had to contend with the challenges Morris Altman, director of network services and internet security officer at Queens College, faces on a daily basis: malware. Queens College is located in Flushing, Queens, the easternmost and largest in area of the five boroughs that make up New York City. Perhaps most readily identified as the home of LaGuardia Airport and Mets ballpark, CitiField, the borough is also home to a diverse population – of its 2.3 million residents, half are foreign born. The college is one of nearly 20 schools spread throughout New York City comprising the City University of New Before searching for a network security solution, his team had no way to effectively estimate the number of devices, including desktops and laptops, that were connecting to the Queens College networks. Therefore, he says, being able to identify and classify these endpoints was imperative while at the same time he looked to improve the school’s network security posture. “More so, we had to securely manage users, students and faculty and their personal mobile ForeScout CounterACT benefits span across the IT team at Queens College. devices connecting to our computing resources.” and faculty population. Another issue that prompted his team “So we needed a solution that would to search for a new network security not only let us better manage and platform was the increasing incidence of organize corporate assets, but also more sophisticated threats – including provide continuous monitoring of our zero-day and propagating worms. It network, and ultimately comprehensive was not uncommon, he explains, for visibility and policy-based control over hundreds of computers on the network devices accessing or on our network,” to be regularly infected – leading to says Altman. York (CUNY) system. With 20,000 students and 5,000 faculty and staff, Queens College faced the modern-day plague of network attacks. And Altman, along with about 40 full-time and 100 part-time personnel on his IT security staff, were challenged with preventing computers from becoming infected and adversely affecting network performance of both the student 32 SC • April 2015 • www.scmagazine.com the spreading of malware to other machines. These threats even consumed enough bandwidth to take the college network services offline on a number of occasions. The network group – specifically the CIO – began the search for a solution. A number of offerings either failed evaluation or could have potentially created future limitations, such as bandwidth limits of in-line network security solutions, says Altman. “We initially turned to ForeScout CounterACT to help protect us against advanced threats and propagating worms, which, in the past, would have infected hundreds of computers, literally bringing the network to a crawl.” Eliminating infections Once the college had CounterACT in place, the first time a new worm broke out, Altman’s team only saw three computers become infected. Those three were immediately isolated from the network and the infection was contained. Additionally, those three users were automatically notified of the problem and were instructed to call the help desk so the IT team could rectify the situation. “Instead of weeks, problems were solved in less than a day and had minimal impact on our students, faculty or staff,” Altman says. After such a positive experience with the initial implementation, the IT team expanded its use of ForeScout CounterACT to enhance visibility and control over who and what types of devices were connecting to the networks. “Prior to CounterACT, we were forced to conduct manual investiga- OUR EXPERTS: Preventing malware Morris Altman, director of network services and internet security officer, Queens College Jack Marsal, director of solution marketing, ForeScout We needed a solution to reduce the risk of security breaches.” – Morris Altman, Queens College tions – even going through firewall logs to identify infected devices and one by one disabling their network ports,” says Altman. At that time, the user and help desk didn’t know why their network ports went down, he adds, which required more resources to determine the source and scope of problems and could take weeks to resolve. As a result, both the network group and the help desk shouldered a huge workload. “ForeScout CounterACT works with a majority of existing networks, both wired and wireless, and integrates with the existing switch, identity and access infrastructure,” says Jack Marsal, director of solution marketing at ForeScout, a Campbell, Calif.-based network security company. “ForeScout CounterACT automatically identifies, classifies and applies security policy to all network devices,” he says. “Unlike first-generation network access control systems, CounterACT continuously monitors devices on the network to ensure that they remain compliant with the organization’s security policies.” The tool ships with numerous policies out-of-the-box and offers customers a great deal of flexibility in terms of designing custom policies that are tailored to their environment, Marsal says. “For example, CounterACT can inform users if they are running prohibited kinds of software. This allows users to take corrective action. If corrective action is not taken, CounterACT can block the user’s device from the network.” The offering also includes the ability to identify when malware is trying to spread through a network and it blocks the propagation, Marsal says. This is done without any need for signatures or signature updates, so the management overhead is very low compared to traditional IPS systems. “We needed a solution like ForeScout CounterACT to help us reduce the risk of security breaches and threats to our students’ computing resources,” says Queens College’s Altman. Prior to implementing the appliance, the college had a significant number of network outages that cost Altman’s team time and money and severely disrupted the experience of students and staff. “We needed a solution that could protect our network while providing us with ROI. Plus, in higher education, the students are your organization’s customers, and if they are inconvenienced or unhappy, it affects the business.” The solution is easy to operate, says Altman. And, he adds, “It has done a great job for us for many years. We’ve maintained our CounterACT appliance as updates have been released, and we are currently using the CounterACT Enterprise Manager, which has centralized administration of our four CounterACT 4000s.” Improved network uptime Altman and his IT team also use CounterACT to automate help desk alerts. Prior, individuals with a networking, system or security issue would have to call the help desk on their own. Now, he says, with the ForeScout solution, the help desk knows of the issue – often before the user does – and calls them first to resolve the issue quickly and conveniently. “CounterACT benefits span across the entire IT team at Queens College,” says Altman. “Asset management uses it for visibility into the network. For example, the endpoint team is monitoring device posture, the help desk is examining www.scmagazine.com • April 2015 • SC 33 Case study ...monitoring for network anomalies is no longer good enough.” what’s going on with the device when an issue is reported, and the network and security teams are constantly monitoring for risks and exposures.” Further, he adds, students and staff can even use – Morris Altman, Queens College CounterACT desktop support for personal patches. that have become part of a botnet. The return on investment from your existing The implementation improved FireEye appliance is integrated with the systems, and you shorten the window network uptime. Whereas prior in the ForeScout network, which alerts the end of time that an attacker has to gain a early 2000s, the school would have user and the Queens College help desk, security incident-related network outages foothold in your network.” and then blocks internet access until the At Queens College, this means that at least two or three times per year, endpoint is remediated. unauthorized applications are blocked now it no longer has outages and enjoys “Being vigilant with regard to from running on the network and nearly constant uptime. CounterACT allows the IT updating signatures and reputation lists, Another benefit, the or monitoring for network anomalies, is teams to notify students tool allows Queens no longer good enough,” says Altman. and faculty when their College to comply with “With FireEye and ForeScout, we know machines are lacking copyrights as it is able the details, security posture and activity up-to-date software. This to limit P2P software, of all devices on our network, and we feature also supports the says Altman. “We’re can automatically isolate violations, Family Educational Rights using CounterACT to malware and affected systems before and Privacy Act (FERPA) – block unauthorized and anything gets out of hand.” a federal law that protects noncompliant users.” Altman says there is no resting on the privacy of student That’s an added benefit laurels, however. His team has seen education records – by because, like all colleges a huge increase in phishing over the keeping all endpoints and universities, the years in the college environment. He up-to-date. school must comply with Jack Marsal, ForeScout also needs to make sure systems are The tool itself does such regulations as the up-to-date and have active defenses. not require constant updates. Thus, Digital Rights Millennium Copyright “Until we had CounterACT, we really it requires very little in terms of Act, which makes it illegal to produce didn’t have an idea of management overhead, and disseminate technology, devices how many devices were Marsal points out. “If or services aimed at getting around on our networks, or if CounterACT discovers DRM measures that regulate access they were compliant and that an endpoint computer to copyrighted works. The ForeScout up-to-date.” is running old software, it solution assists IT in resolving The tool, he says, allows can trigger the endpoint to take-down notices for music and his team to “discover all fetch an update, or it can movies with copyright violations being sorts of things. We now automatically run a script downloaded from peer-to-peer software. know that there are about on the endpoint to install 6,000 wireless and 5,000 the updated software.” Easy installation wired endpoints at any The offering is deployed In many situations, CounterACT does on all parts of the Queens not require any agents to be installed on given time.” College wired and wireless the endpoint, ForeScout’s Marsal points This detailed insight on Morris Altman, Queens College network. Some other out. “This makes CounterACT much network endpoints allows CUNY colleges have easier to install and maintain than other his team to understand adopted ForeScout following success at NAC products that require agents.” the diversity of devices and prioritize the the Queens campus. The gadget integrates with many devices or operating systems it supports And, Altman says his team will different types of security systems, he when new applications are released, he continue to add appliances to support adds. “The goal is to share information says. For example, if only 10 users have additional users. For example, they and automate actions. By coordinating Windows phones and thousands have recently added FireEye to the edge of its security intelligence and automating Android and iPhone devices, the priority network to act as a sensor for computers security responses, you obtain a higher shifts, he explains. n 34 SC • April 2015 • www.scmagazine.com Product Section Deepnet PistolStar The multifactor authentication pros need P38 For that first step into dual-factor authentication P43 Let’s get authentic R eviews this month addressed authentication. It used to be that we knew exactly what we meant by authentication. It was part of the access control function: identify, authenticate, authorize. It’s not quite so simple today. Today, the perimeter is porous and we sort of let strangers into parts of our systems – think online banking, for example. The notion of strong authentication used to mean multifactor and, to some extent, it still does. But now we have some special use cases that call for strong authentication, but do not necessarily require multifactor. An example is that awful tool, CAPTCHA. This has to be the most user-unfriendly contrivance in the history of computing. However, it is just that which makes it useful. It is, in its own way, an authentication device. It authenticates the user as a human rather than a bot. There is no multifactor, but it changes with each use, so it is not predictable. In short, it is rather like a one-time pad in encryption. At the other end of the spectrum we have biometrics. Now, if we combine with a PIN or password for multifactor, we have pretty much the strongest authentication around. Unless you are very clever. Fans of Sherlock Holmes may recall “The Adventure of the Norwood Builder.” In that story, Holmes discovers that a fingerprint on the wall was fashioned by making a rubber mold of a fingerprint and using it rather like a stamp. Fantasy? Not really. At the annual scientific meetings of the American Academy of Forensic Sciences this year, a project was shown that demonstrated that the Holmes story works just fine: a latex facsimile can be used to unlock a mobile phone. However, in this month’s parade of products we tried no such subversion. Our testing was very straightforward. For each product, we created its own test bed and put it through its paces. Everything tested worked well and the result was a crop of first-rate products – some spectacular. The name of the authentication game this year seems to be price/ease of use. Now, the average person can use strong authentication easily, and the tools are inexpensive. Hats off this month to the reviews team of Sal Picheria, Ben Jones and James Verderico. Now, on to the products. – Peter Stephenson, technology editor RSA Has features not found anywhere else P44 How we test and score the products Our testing team includes SC Labs staff, as well as external experts who are respected industry-wide. In our Group Tests, we look at several products around a common theme based on a predetermined set of SC Labs standards (Performance, Ease of use, Features, Documentation, Support, and Value for money). There are roughly 50 individual criteria in the general test process. These criteria were developed by the lab in cooperation with the Center for Regional and National Security at Eastern Michigan University. We developed the second set of standards specifically for the group under test and use the Common Criteria (ISO 1548) as a basis for the test plan. Group Test reviews focus on operational characteristics and are considered at evaluation assurance level (EAL) 1 (functionally tested) or, in some cases, EAL 2 (structurally tested) in Common Criteria-speak. Our final conclusions and ratings are subject to the judgment and interpretation of the tester and are validated by the technology editor. All reviews are vetted for consistency, correctness and completeness by the technology editor prior to being submitted for publication. Prices quoted are in American dollars. What the stars mean Our star ratings, which may include fractions, indicate how well the product has performed against our test criteria. ★★★★★ Outstanding. An “A” on the product’s report card. ★★★★ Carries out all basic functions very well. A “B” on the product’s report card. ★★★ Carries out all basic functions to a satisfactory level. A “C” on the product’s report card. ★★ Fails to complete certain basic functions. A “D” on the product’s report card. ★ Seriously deficient. An “F” on the product’s report card. LAB APPROVED What the recognition means Best Buy goes to products the SC Lab rates as outstanding. Recommended means the product has shone in a specific area. Lab Approved is awarded to extraordinary standouts that fit into the SC Labs environment, and which will be used subsequently in our test bench for the coming year. www.scmagazine.com • April 2015 • SC 35 PRODUCT SECTION GROUP TEST Authentication Authentication Specifications for authentication tools It now is feasible for organizations of just about any size to support everyone in the organization with strong authentication, says Peter Stephenson. Deepnet Entrust SafeNet Imation LoginTC PistolStar RSA Auth Swivel Secure Vasco Supports Yubikey? ● ○ ● ○ ○ ● ○ ● ○ ○ Supports physical token? ● ● ● ● ○ ● ● ● ● ● Supports software authenticator? ● ● ● ○ ○ ● ● ● ● ● Offers self-service password reset? ● ● ● ● ○ ● ● ● ● ● Offers API for custom products ● ● ● ○ ● ● ● ○ ● ● Offers biometric support ● ● ○ ● ○ ○ ● ○ ○ ○ Offers RADIUS support ● ● ● ○ ● ● ● ○ ● ● Offers Active Directory support ● ● ● ● ● ● ● ● ● ● Offers VPN support ● ● ● ○ ● ● ● ● ● ● Offers SMS authentication ● ● ● ○ ○ ● ● ● ● ● Offers Bluetooth authentication ● ● ○ ○ ○ ○ ● ○ ● ○ Gemalto Vendor PICK OF THE LITTER PistolStar PortalGuard is one of the most full-featured products we’ve tested this time around, with great value per user, ease of use, impressive customer support and support for a wide range of products and services for multifactor authentication integration. We picked this as our Best Buy. RSA Authentication Manager is more expensive than other alternatives, but it also comes with several features not found anywhere else. This combined with its tight integration with popular business applications make it a great choice for organizations of all sizes. Our pick for Recommended. T his month we look at authentication. Most years we begin this review section with a basic chat about the access control process. This year, let’s have a look at how that process has changed. The big news is price and ease of use. While there still are a few pricey solutions to the authentication challenge, the trend – absolutely – is to make it fiscally practical to move from passwords to strong authentication. Authentication is a component of the access control process. That includes identification, authentication and authorization. More and more organizations are realizing that access to sensitive systems is way too easy. The cry to “encrypt everything” has met with resistance, both due to cost and to the weakness of encryption as a confidentiality solution. If you can compromise the admin account, you can get in. The encryption is pretty useless in that situation. That, of course, is not an admonition to scrap encryption entirely. It does have its place. But wholesale encryption of entire hard disks probably – by itself – won’t solve the confidentiality issue. So, we’re back to the real gatekeeper: strong authentication. Today, as always, that probably means multifactor authentication in most cases. Traditionally, multifactor has been expensive. And, as you will see, there still are some 36 SC • April 2015 • www.scmagazine.com pricey products. Those, however, need to be taken in context with how many users they are intended to support. Looked at that way, the price starts looking much more reasonable. The other issue that has pushed strong authentication out of the reach of many organizations is ease of use. While it probably is reasonable for system administrators to have the technical chops to use just about any authentication tool, it is not as reasonable to expect that of the average business user. And, why should it be? The average business user should address computing as a tool to get his or her job done, not an end in itself. Such things as email encryption and data classification – very cumbersome at one time – now almost are automatic. Strong authentication should be as well. And, many vendors of strong authentication have addressed that, as we saw this year. So, where does strong authentication fit in the confidentiality scheme of most organizations? It depends on when you ask. In years past, the answer was “for high risk accounts.” That meant that the system administrators or any other person who had access to sensitive data got the hardware tokens. Today, though, that is not necessarily the best solution. Certainly you might want to keep the hardware tokens for the high-risk accounts – although they are nowhere near as expensive as they once were – but there are other schemes that are cheap and will work for the average user. Also, mixing products is viable and integration into existing systems is pretty simple. This is a sea change from the past. Part of why this is possible – and practical – is the pervasive use of cloud computing. Sitting the heavy lifting on a big server farm readily accessible from the internet makes a lot of sense. It also has the economy of scale that puts the cost of the service well within the reach of most organizations. Given these changes, how do you build out a strong replacement for passwords? Carefully! First, evaluate, evaluate and then evaluate some more. When you get down to a couple of products that you like, run a small pilot. Most vendors will gladly help you do that. Now, look at deployment. If you are a big organization spread all over the country or the world, you might want to consider something that can be self-deployed by your users. Self-service systems are becoming much more common, especially for cloud-based vendors, and that could ease your support pains significantly. The bottom line is that it now is feasible for organizations of just about any size to support everyone in the organization with strong authentication. It is cost-effective and easy to use in most cases. As the old TV commercial said, “Try it…you’ll like it!” ●=yes ○=no Secure- www.scmagazine.com • April 2015 • SC 37 GROUP TEST Authentication Deepnet Security Entrust DualShield v5.8.1 IdentityGuard D DETAILS Vendor Deepnet Security Price $649. Contact deepnetsecurity.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Simple setup, wide variety of deployment for security strategies. Weaknesses None found. Verdict Given the great price and the simple integration into one’s infrastructure, the product is exactly what security professionals are looking for to provide multifactor authentication. GROUP TEST Authentication ualShield is an enterprise-grade, unified, multifactor authentication platform that protects all commonly used business applications with a large selection of multifactor authentication methods. This product provides an advanced level of security when identifying and authenticating users. DualShield works in conjunction with other OATH-compliant, one-time password (OTP) hardware tokens, mobile apps, grid cards, as well as Google Authenticator, RSA SecurID, VASCO DigiPass Go tokens and YubiKey. Deepnet’s product was shipped to us with a setup CD and a SafeID OATH token. With the provided documentation, the setup was a breeze. We followed the installer wizard found on the CD and were able to choose between a back-end, front-end or complete installation. The installation type depends on what machine one wants to install the appropriate functionality. By default, a MySQL server and database are installed once the native software is finished downloading. Additional security functionality can be implemented during installation. The device was very simple to use. Once installation was complete, to test the authentication capabilities it was necessary to create the identity source, link it to Active Directory, create a domain for the identity source and create a basic Windows logon procedure to test user authentication. Using the installed Self Service module enables administrators to 38 SC • April 2015 • www.scmagazine.com manage end-users, request replacement tokens or even request an emergency login code. Unlike most other two-factor authentication products that commonly provide only one or a few authentication methods, DualShield provides more than 10 authentication methods including token-less on-demand password delivered by SMS, email and voice; tokenbased mobile app, key fobs, display cards and grid cards; device-based device fingerprinting; biometrics voice, face and keystroke recognition; and PKI certificates and smartcards. The documentation provided by Deepnet is found on the setup CD, which also gives users links to access further materials. The documentation is clear-cut and well put together and allowed us to easily follow along or find help for procedures to get everything running. Throughout, images aid the user during both installation and setup. Deepnet provides its clients with both basic no-cost and fee-based support options. Basic no-cost support includes assistance by email, phone and WebEx. Overall, DualShield is a complete solution for strong user authentication that is extremely user-friendly, cost-effective and easy to integrate into a customer’s existing IT infrastructure. For the price point, functionality provided and security management capabilities of this product, it is a great option for a multifactor authentication solution on one’s network. E ntrust IdentityGuard is a dual-factor authentication server, app, smart card manager, biometrics server and general jack-of-all-trades when it comes to dual-factor authentication. It has a large volume of features and supported factors. It is part of the Entrust IdentityGuard Software Authentication Platform and, along with other products in the suite, covers just about authentication task you can imagine. Setup could have been easier – the administrator interface is nearly overwhelming at first. Although IdentityGuard has a level of granularity in settings that goes unmatched, setup on the administrator side is a little complicated to match. The user setup is much easier. It has an easy-to-use web interface, particularly on the smartphone application, with a level of cleanliness and intuitiveness that we expect from a big name like Entrust. Entrust IdentityGuard has security questions; GRID/eGRID (basically a matrix); an app for both iPhone and Android, with mobile device certificates to match; one-timepassword authentication; SMS authentication as well as soft tokens. Soft tokens are software-based authentication methods that reside on the device to authenticate the device itself. IdentityGuard also includes a Bluetooth authentication method in the form of a fingerprint scanner that ties in with the app, smart cards, USB tokens and biometrics. The app is an easy-to-use self-service for employees, and enlists a method of authentication through either one-time-password generation or through Bluetooth. The documentation includes setup guides for each of the protocols and supported services, as well as self-service-oriented videos that could be used as teaching materials for employees learning how to use the app. We were quite pleased with the documentation. The site is exactly what you would expect from a name such as Entrust. Product sales documentation is plentiful as are technical brochures that discuss how IdentityGuard fits into compliance and standards. Entrust IdentityGuard has three support tiers: TrustedCare Platinum, Gold and Silver. TrustedCare Platinum costs 22 percent of total software investment annually with 24/7 support. TrustedCare Gold costs 20 percent of total software investment annually with 24 hours a day, Monday to Friday support. TrustedCare Silver costs 18 percent of total software investment annually, with aid 8 a.m. to 8 p.m., Monday to Friday. IdentityGuard is a feature-packed tool that surpasses our expectations, with support for every protocol on our matrix and at the same time the most options for different forms factor types. It also has an extra bit of security and ease of use by being a certificate authority manager. It provides a great value per user and will make a contribution to your authentication across every service in your network. DETAILS Vendor Entrust Price $8 per user, $3.75 per user above 25,000. Contact entrust.com Features ★★★★★ Ease of use ★★★★ Performance ★★★★½ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★½ Strengths Sheer volume of features. Weaknesses Administrator learning curve. Verdict A solid product for a great price, one of the most comprehensive platforms we’ve seen. www.scmagazine.com • April 2015 • SC 39 GROUP TEST Authentication DETAILS Vendor Gemalto Price $1 per user/per month for 2,500 token configuration. Contact safenet-inc.com Features ★★★★★ Ease of use ★★★★½ Performance ★★★★★ Documentation ★★★★★ Support ★★★★½ Value for money ★★★★½ OVERALL RATING ★★★★¾ Strengths Wide range of supported products. Weaknesses No serious liabilities found. Verdict Full of features and solid on performance, well worth looking at. GROUP TEST Authentication Gemalto Imation IronKey SafeNet Authentication Service F200 Flash Drive S T afeNet Authentication Service is a cloud-based authentication service that uses a wide range of tokens and custom agents to support multifactor authentication to include one-time passwords generated by a phone app, SMS, a hardware token or email. Setup, as with many cloud-based solutions, is a breeze. The MP-1 software token is a onetime password that expires every 60 seconds and generates a new one. This is as simple as install and activate. Simply follow the email link and copy-paste an activation code. SMS authentication is as simple as inputting a cell phone number. One of SafeNet’s big selling points is its API, and consequently, Safenet can be integrated into just about any application one may be working on. It has many agents for a long list of already existing applications, services and servers, including Microsoft Active Directory and RADIUS. SafeNet also allows SAML services, like Google Apps and Salesforce. The tool has granular logging and reporting and a self-service portal, both of which greatly reduce the amount of management time required while keeping both the user and the administrator more informed. Documentation is extensive and complete. The agents themselves each have a spot on their website that is easy to find and the diagrams are clear in describing what is happening every step of the way. However, they may 40 SC • April 2015 • www.scmagazine.com have overdone themselves here as there is so much documentation it can be challenging to find what you might be looking for. For some applications, it seems like a great deal of reading is needed to get one’s feet off the ground. One interesting part of the SafeNet web site is the sction on software monetization. Departing from the traditional sales pitch for strong authentication, this part of the site discusses how to apply SafeNet to your software product to make more money. Also departing from the traditional use of hardware tokens for copyright protection, this part of the product allows enforcement of copyright through the cloud. SafeNet’s Extended Support is included in the subscription cost and includes online and telephone assistance during regional business hours with an eight-hour response time. SafeNet’s Plus Support costs 10 percent of the subscription price and includes 24/7/365 online and telephone aid with a one-hour support time. If you are a global operation this type of support probably makes sense for you. SafeNet has one of the broadest ranges of agents we have ever seen. There is a small, easy to set up agent for seemingly every service we can shake a stick at. The interface feels intuitive and clean and presents logging information at the fingertips of the administrators. Overall, this is a very nice piece of work – easy to deploy, easy to use and a lot of functionality. he Imation IronKey F200 Flash Drive is a simple, easy to set up and extremely secure device for users who need to transport confidential data between computers. Because of its non-involved setup, users who are not necessarily tech savvy can suddenly equip themselves with top-tier protection. It is available in 8, 16, 32 and 64 gigabyte variations, which allows organizations to purchase the F200 based on the storage needs of individual users. For extra security and manageability, the enterprise version of the management software can be purchased. This allows organizations to centrally manage and provision secure flash drives across the enterprise. For our tests, we received the 8GB model in a small package. After unpacking the device, we were greeted with what appears externally to be no more than a very sturdy flash drive. After removing the sleek metal cover, it is immediately obvious that this tool means business. The sturdiness aspect is further exemplified by the internal device construction and the biometric sensor lies in an ergonomic groove for easy swiping. We plugged it into one of our lab machines, which automatically opened the Imation Access software – the gateway to the device. Once it is connected, two drives automatically install on the system. The first appears as a virtual CDROM drive, where the system files live. The second appears as a removable disk named LOCKED. We followed the software through the GUI wizard, which was where we configured the device. Here, we were prompted to create an administrator password. After we did that, it prompted us for the number of users we wanted to create. As far as security is concerned, the Imation IronKey F200 is an excellent choice. By default, the device operates in biometric-only mode, but users who opt to go through the advanced options in the setup are afforded several more options. One feature we really liked is the ease of mounting it read only. When logging into the device, the user is prompted to enable the device as read only. This provides an extra layer of security for users transporting very sensitive documents or users connecting to devices they suspect may contain malware. Because the F200 uses hardware encryption, once it has been set up it is supported by virtually every device that accepts USB disks. The only drawback we could find was its speed. Read speeds were average, but writing large files took a long time. Because of its advanced security, we find this solution to be useful with a reasonable price tag. The granularity aspect of purchasing makes it affordable for organizations of all sizes. As the enterprise grows, the centralized management software can be added, which increases the value of the device as a longterm investment. DETAILS Vendor IronKey by Imation Price $189 per unit. Contact ironkey.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★½ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Very secure with the ability to add central manageability at any time. Weaknesses It’s not a big issue for most users, but the lack of USB 3.0 support will slightly slow power users or individuals moving large files. Verdict Great price point and advanced security. www.scmagazine.com • April 2015 • SC 41 GROUP TEST Authentication Cyphercor PistolStar LoginTC PortalGuard L DETAILS Vendor Cyphercor Price $16.80 per user per year, or $15 per user per year over 1,000 users. Contact logintc.com Features ★★★½ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★½ Support ★★★★★ Value for money ★★★★½ OVERALL RATING ★★★★½ Strengths Ease of use and beautiful interface. Weaknesses Limited feature set. Verdict A great solution that can be up in no time at all. GROUP TEST Authentication oginTC from Cyphercor is a cloudbased solution that uses a mobile device or a desktop for authentication. It has easy-to-use iOS, Android and Chrome desktop applications to approve logins to a variety of products. Their big selling points are reliability of the cloud, ease of use and cost. Because Cyphercor uses a mobile device it is far less likely that the user will lose the device than it is if the user has a traditional hardware token. According to Cyphercor users check their mobile devices every five minutes on average. Setup is as easy as it gets. RADIUS, VPN, WordPress, Drupal and Joomla connectors all simply work off the bat. Documentation provides a simple, step-by-step guide to starting up all of these connectors. There is a User Sync Tool to synchronize users (in one direction) to any LDAP server, including Active Directory and OpenLDAP. On the user end, it gets even easier. Downloading an app is something everyone knows how to do by now. One then types in an activation code and is done. The Chrome app is no different: follow the link in an email upon registration, or look them up on the Chrome app store, input activation code and one is done. LoginTC supports RADIUS, Cisco ASA, OpenVPN, PHP web-based, Unix SSH, Drupal, WordPress and Joomla, as well as a REST API. The interface itself is beautifully 42 SC • April 2015 • www.scmagazine.com simple and intuitive, the Google Chrome app takes advantage of the browser’s push notifications, which makes this one of the simplest and most intuitive software-based tokens we’ve used. The documentation is some of the best we’ve seen. It’s easy to get to on the top of the website. The category view makes sense. Complicated concepts are expressed in simple and easy to understand diagrams. It made the setup step a whole new level of easy. There are three support packages that are all free, but depend on the number of users: Starter support is for less than 10 users and is via email 8 a.m. to 8 p.m. EST; Professional support is available for less than 1,000 users and has phone support 8 a.m. to 8 p.m. EST and email support 24/7; Enterprise support is 24/7 phone and email aid. LoginTC’s API sets it apart from many other products. LoginTC does exactly what it says it does very well, arguably the best for its feature set. LoginTC being cloud-based takes out much of the work, but also restricts some of the use cases. LoginTC is a great product that deserves your consideration, especially if you do much of your work on the web. This is one of those tools that brings strong authentication to the average user in a cost-effective (up to ten users are free), easy to use package that works in the user’s familiar environment. P ortalGuard is a multifactor authentication, web-based single sign-on (SSO) through internet information services (IIS) and self-service password reset server and application rolled into one. The install is guided by a PistolStar engineer who has either developed or tested PortalGuard through screen sharing and VoIP, included with every purchase. This is a nice touch. The PortalGuard server application is easy to install, no doubt because the engineer guiding us through the install knew the product inside and out. This almost doubled as a training session, as during the install we were able to ask questions and learn how the product worked. This saved us a tremendous amount of time in setup and reduced the gap between setup and actually having something useful to work with. PortalGuard has support for RADIUS servers; SSL VPNs; single sign-on (SSO) web servers and Active Directory servers; Sharepoint, Exchange and Outlook Web App, federation websites, like Google Apps, Microsoft Office 365; and many more. The offering does exactly what one would expect it to – as a dual-factor authentication server and then some. The different authentication methods include a mobile authenticator (like Google Authenticator), phone call, SMS, email, RSA SecurID, Yubico Yubikey, and/or a number of personal challenge answers to be set up by the users when they configure their preferred methods of authentication. Many of these are taken care of on first startup. However, if one has the user’s email or phone number already in an Active Directory field, PortalGuard can optionally look for some of that information. PortalGuard also supports extra logging functionality and tying this extra data into a SIEM. The aspects that really set PortalGuard apart are its granularity of controls, ease of use and contextual-based authentication. The tool allows every detail to be different between user groups, or even individual users, all from an easy-to-use GUI application that sits on the server. With the configurable contextual-based authentication, if a user logs in consistently from a certain IP at the same time every day and doesn’t get their password wrong, PortalGuard does not need to ask for another factor. If a user is logged into a local network inside the building, the policy could be set to be a little more relaxed than if the user was logging in through a VPN while on vacation. PistolStar PortalGuard is one of the most full-featured products we’ve tested with great value per user, ease of use and impressive customer assistance, as well as support for a wide range of products and services for multifactor authentication integration. For the combination of these assets – in combination with no real downsides – we picked this as our Best Buy. DETAILS Vendor PistolStar Price $10,000 (initial purchase); $2,500 (yearly renewal). Contact pistolstar.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Does everything expected and then some – with ease of use and unlimited users. Weaknesses None. Verdict Excellent product for that first step into dual-factor authentication. We select it as our Best Buy. www.scmagazine.com • April 2015 • SC 43 GROUP TEST Authentication DETAILS Vendor RSA, the security division of EMC Price $46 per user. Contact emc.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Scalable, made for large environments, integration with many applications. Weaknesses None found. Verdict It’s clear why this is one of the most popular dual-factor authentication products. Recommended. GROUP TEST Authentication RSA SecureAuth Authentication Manager IdP T S he RSA Authentication Manager is a dual-factor authentication system designed from the ground up for enterprise deployment. It is one of the most widely deployed systems out there and is available in many different configurations to fit the needs of any business. In the backend, RSA Authentication manager can run as a VM or preconfigured hardware appliance. RSA has preconfigured VMs available for Hyper-V and VMware virtualization platforms. End-users can then select from a credit card-sized token, the traditional dongle token, the more advanced USB dongle token, the software token or the mobile device authenticator. Mobile device authenticator apps are available for iOS, Windows Phone, Android and BlackBerry. For larger organizations, individual RSA Authentication Manager Instances can be set up in a pool for load balancing capabilities. Also available is a self-service component, where users can reset their PINs or create requests for new tokens. We received RSA Authentication Manager as a preconfigured virtual appliance for VMware. In addition to the software kit, we received 25 SecurID dongles, 25 SecurID 800 dongles and 25 software token licenses. After we removed everything from the box, we logged into our VMware ESX server and inserted the provided CD containing the VM. In VMware, we opened the CD and dis- 44 SC • April 2015 • www.scmagazine.com covered an OVA file with the VM in it. After opening the OVA, we accepted the license agreement and VMware did the rest. After it was done copying files, we powered on the VM to complete the VM equivalent of hardware setup. After booting, the Authentication Manager VM automatically started a Linux shell script which ran us through the network configuration. Here, we set up our network settings by following the wizard. Once the network settings were configured, the VM then continued starting up and eventually stopped at a screen which provided us with a quick setup code and prompted us to complete configuration in our web browser. We went to the webpage to upload our license, set the passwords for various accounts and set up the time. Overall, setup was very easy and, for the most part, entirely automated. RSA Authentication Manager is more expensive that other alternatives, but it also comes with several features not found anywhere else. RSA is built from the ground up to be used in an enterprise environment and it is clear when using the tool. Its scalability means that users can set up only on Authentication Manager in smaller environments and then add more as load increases or the business grows. This combined with its tight integration with popular business applications makes it a great choice for organizations of all sizes. Our pick for Recommended. ecureAuth IdP is an identity provider – with a unique approach to securing user access control. With control of the device, applications and even the infrastructure moving out of the data center, IdP is the perfect solution to maintain secure control of user access to resources and data, whether on premise, in the cloud, on the web, via a mobile device or through VPN. SecureAuth IdP can be purchased as a standalone subscription service, a preconfigured virtual server, a standard physical server or a high availability physical server. The product is an on-premise or cloudbased solution that allows single sign-on (SSO) and two-factor authentication for many enterprise environments, such as legacy web applications, VPNs/gateways, cloud resources or Windows Logon. This product also offers the security authentication concepts of “something you have,” as well as the traditional “something you know.” The SecureAuth IdP was extremely easy to set up. We were sent the download link for the preconfigured virtual server, downloaded it and logged in with the provided credentials. Upon initial login to the account, the native install wizard began installation and we followed the documentation to finish integration into our network. Once installation was complete, we accessed the SecureAuth SSO portal and were able to easily manage various user accounts and credentials. All configuration and management for the server itself is done through the web-based management console that is implemented during installation. Users are easily added to the business environment and the admin can easily customize authentication methods for the users’ portable devices. For documentation we were given the link to a website. The documentation is clear and thorough providing the user with an appliance setup and administrator guide as well as guides for certain network and application integrations. The website provides clients with access to an immense knowledge database to answer most questions and a plethora of other resources. SecureAuth IdP provides its clients with a basic no-cost support option. If the user has a valid license, they are given all the following: The no-cost support provides licensed users 24/7 coverage support, ranging from 24/7/365 phone assistance as well as an email support staff. The response times range from as short as 30 minutes to up to one business day depending on the severity of the ticket. This is an interesting approach to aid and is definitely a cost-effective solution compared to other options. Overall, SecureAuth IdP is the perfect solution for maintaining secure control of user access to resources and data, whether on premise, in the cloud, on the web, via a mobile device or through VPN. The product is easily setup and integrated into the network, has a great price point and offers great support. DETAILS Vendor SecureAuth Price $19.50 per user/per year (price drops as users are added). Contact secureauth.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Provides users with a variety of authentication methods and an easy-to-use management console. Weaknesses None found. Verdict With a diverse set of functionality for authentication methods and support offered for licensed users, this product is definitely worth every penny. www.scmagazine.com • April 2015 • SC 45 GROUP TEST Authentication Swivel Secure VASCO Swivel Appliance DIGIPASS 760 and DIGIPASS for Mobile T DETAILS Vendor Swivel Secure Price $3,047.04 for virtual appliance (prices go up for hardware appliances). Contact swivelsecure.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★ OVERALL RATING ★★★★★ Strengths The Swivel appliance can be seamlessly integrated into an infrastructure with little to no downtime. Weaknesses Steep price. Verdict The easy-to-use management console allows for seamless integration of authentication for new users with few steps. GROUP TEST Authentication he Swivel Appliance is a competitive solution for two-factor authentication methods for clients searching for a secure product. The product uses a variety of authentication methods from its own patented OTC extraction protocol, called PINsafe, to PINs via OATH tokens, and one-time as well as password-based. The product is also capable of providing a user with authentication using the PINsafe protocol over SMS, a mobile app, telephony or in-browser imagery. Swivel is easily implemented and can integrate into an IT infrastructure with minimal downtime. This solution also provides users with the satisfaction of knowing that their authentication methods are reliable, safe and secure. It was easily set up. We were given the links to download a virtual appliance, downloaded it and began setup almost immediately. Also provided was a converter application, which converts the Windows-based physical machine into a VMware virtual machine image. This tool was extremely useful because it made integration into VMware much easier. The virtual appliance is managed through Webmin, a web-based management console. Webmin allowed for the initial configuration into our network to be extremely simple and the GUI was clean. The setup, configuration and integration process is easily followed through provided documentation and offers ease of mind during this process. With its streamlined setup process, the 46 SC • April 2015 • www.scmagazine.com appliance can be easily integrated into one’s current IT infrastructure. When authentication occurs, seeing as the OTC code is not generated by the server, it makes interception by an unauthorized user nearly impossible. This can provide a great sense of security when integrating Swivel into a network or with the many types of devices supported. The product comes packed with compatibility to leading SSL VPN technologies, such as Juniper, F5, Sonic Wall, Citrix, Palo Alto, Cisco and more. Swivel also supports a wide variety of remote access and web platforms, such as Microsoft Sharepoint, Exchange, OWA and IIS via an ISAPI filter, as well as a wide range of cloud services, such as Microsoft Office 365, Huddle, Google Apps and Salesforce.com. The full list of integration supported can easily be found on the website or from documentation. Overall, the Swivel Secure Swivel Appliance is a great product – but for a steep price. The easy-to-install functionality of this program is a great plus; however, the product is tailored toward those with extra money seeking an absolute top-of-the line product. The appliance provides exactly that and offers its clients a simple and intuitive management console to easily customize authentication methods for its users. For those who want a permanent solution to authentication security and have the extra cash, the Swivel Secure Swivel Appliance is definitely your product. D IGIPASS 760 is a trusted hardware device for visual transaction-signing that creates a secure optical communication channel between the end-user (client) and the organization (server). This product makes use of QR reader functionality where a unique code is generated as a token for the transaction. The DIGIPASS 760 is then used to read the QR code and give the user the unique one-time code generated for the transaction. The device can be used in conjunction with a custom application in order to create a secure two-factor authentication transaction. It can also work with mobile platforms to ensure secure communication between user and the server. VASCO’s product was very easy to set up. We removed the DIGIPASS 760 hardware device from the package, powered on and connected to the demo website created for testing. The hardware device is the size of a small wallet and is used to decrypt the information displayed in the cyrptogram for verification. Once powered on and using its built-in camera, we connected to the VASCO authentication web address and decrypted the cryptogram. The cryptogram provided us with the activation license that we validated with company’s website. At this point, the basic setup was complete and the DIGIPASS 760 device was ready. The device is easy to use, seeing as we simply pointed the device at the cryptogram and received the code on the screen. The other component was the setup of IDENTIKEY and DIGIPASS gateway on our backend server. IDENTIKEY is the access-management software installed in order to validate user login on web-hosted applications. The entire security package gives users the ability to integrate security with the development of both mobile- and cloud-based applications. But most importantly it can give users an ease of mind when implemented for transaction security. The DIGIPASS 760 is used to validate the user with the generation of a unique signature. A very important aspect to this service is that no sensitive data, including account or cardholder information, is stored as part of any transaction, which alleviates the burden from the organization and further protects user data. Both the DIGIPASS 760 and DIGIPASS for Mobile provide clients with basic no-cost or fee-based support options. The fee-based option offers 5/10 and 24/7 support that varies depending on the initial amount of licenses purchased. Levels of support vary from standard to a remote assistance package. Overall, both the DIGIPASS 760 and DIGIPASS for Mobile security packages can provide users with an ease of mind for security. Whether for secure transactions, secure communication or mobile and cloud app security, these VASCO products are well worth checking for users with security on their minds. DETAILS Vendor VASCO Price DIGIPASS 760: $4,030.60; DIGIPASS for Mobile: $905.75, with $226.44 maintenance fee. Contact vasco.com Features ★★★★★ Ease of use ★★★★★ Performance ★★★★★ Documentation ★★★★★ Support ★★★★★ Value for money ★★★★★ OVERALL RATING ★★★★★ Strengths Limitless options of integration with custom applications. Weaknesses None found. Verdict With an excellent price point and the security provided to its users, this product is a must-see. www.scmagazine.com • April 2015 • SC 47 FIRST LOOK Events Seminars APRIL »INTERPOL World 2015 Bromium vSentry AT A GLANCE Product vSentry Company Bromium Price $150 list price (volumebased discounts available). What it does Creates micro-VMs to encapsulate running processes and protect them from malware. What we liked This is the most creative use of virtualization we’ve seen to date and certainly the best anti-malware protection around. We also loved its forensic capabilities. The bottom line Absolutely rock-solid malware protection and forensic diagnostic tool for endpoints, arguably the most vulnerable part of the enterprise. W e hear that anti-malware tools just are not effective anymore. Malware is way too sophisticated for the types of protection that we have relied upon traditionally. So what is the answer? A company called Bromium may have solved this one. The answer is not what it seems on the surface, though. A sandbox, by the company’s definition, is a layer between the malware you are dissecting – or protecting against – and the operating environment. I agree. I would not trust a sandbox that could be bypassed any number of ways by a really smart bit of code. Locking malware in (or out) is exactly what vSentry does. vSentry contains anything that needs protection inside a virtual environment and that environment uses a bare metal hypervisor – which they call a Microvisor – just as does our big VMware virtual cluster at the Center for Advanced Computing. By placing all vulnerable tasks in the Windows environment inside micro-VMs that are tied to the hardware, there is no way for malware to work through a sandbox layer and attack the operating environment. Each process gets its own micro-VM, and that VM is dissolved when the process stops, taking any malware with it. There are two issues that need to be addressed to ensure isolation. First, processes cannot be allowed to write to a “golden 48 SC • April 2015 • www.scmagazine.com image” that has been installed on the computer. When one of those golden images executes – in memory, of course – vSentry makes a copy and writes to the copy. Bromium calls this process “Copy on Write.” Windows sees the micro-VM as the executing task and the micro-VM isolates everything to its own Microvisor. The second issue is that malware often will try to infect anything it can see. In vSentry, the Microvisor restricts the micro-VM from seeing anything that it does not need to see in order to run. Think of this as a sort of “virtual machine need to know.” If the particular process caged in the micro-VM needs a resource, it can see it. If it doesn’t, it can’t. Finally, vSentry limits a process’s access to the Windows Registry. This prevents malware from modifying Registry entries, a favorite malware trick. But what we liked – perhaps even more than vSentry itself – was its Live Analysis and Visualization (LAVA). With LAVA you can see the behavior of otherwise undetectable malware, including watching execution and capturing destinations – helpful in finding commandand-control servers – and seeing how the malware attempts to hook processes and modify the Registry. Overall, this is a first-rate tool and as a way of isolating a system from malware it is about the best we’ve seen. April 14-16 INTERPOL World is a new international security event that will showcase innovation, and achievements among the public and private sectors in the security arena. It will address the rising demand for technology to meet real global security challenges. It will focus on cybersecurity, border management, safe cities and supply chain security. Venue: Singapore Contact: cloudsecurityalliance. org/events/#_industry »CSA Summit 2015 April 20 Cloud computing is now a mission-critical part of the enterprise. Join CSA to discover lessons learned from enterprise experts in securing their clouds and achieving compliance objectives. A global list of industry experts will share their experiences and discuss the key security challenges of tomorrow. Get the big picture view of the future of IT and CSA’s mandate to revolutionize security at this traditional Monday kickoff to the RSA Conference. Venue: San Francisco Contact: cloudsecurityalliance. org/events/csa-summit-2015/ » RSA Conference April 20-24 This year’s gathering is dedicated to leading-edge information security topics, including data breaches, threats, compliance, social engineering, cloud, risk management, applications, mobile, governance, data, legislation, policy, law, cryptography and identity management. More than 400 speakers will be presenting, including General Keith Alexander, former director, NSA; Michael Assante, director of ICS, SANS Institute; Gene Fredriksen, CISO, PSCU; and Johannes Ullrich, dean of research, SANS Technology Institute. Venue: San Francisco Contact: rsaconference.com MAY »SANS Security West 2015 May 4-12 SANS Security West 2015 will focus on emerging trends and feature evening talks and an interactive panel discussion on the future of cybersecurity. Attendees can take courses from top SANS instructors and real-world practitioners who can ensure you not only learn the material, but that you can apply it immediately when you return to the office. Venue: San Diego Contact: sans.org/info/171472 JUNE »Infosecurity Europe 2015 June 2-4 Infosecurity Europe addresses the latest challenges in information security to provide attendees with businesscritical insight, best practice and practical case studies. Speakers include information security thought-leaders from public and private sector end-users, policy-makers and government analysts, industry experts, as well as service providers and vendors. More than 345 exhibitors will be on the expo floor and more than 100 hours of free education offered. Venue: London Contact: infosec.co.uk Start here for a calendar of events. To have your event included, contact [email protected] Venue: São Paulo Contact: gartner.com/ technology/summits/la/ business-intelligence-brasil »SC Congress Toronto June 10-11 SC Congress Toronto returns for another exciting two-day program. We’re bringing together leaders in the information security industry in both the public and private domains, particularly based in Canada. You will have a chance to walk our expo floor exploring the latest trends and products best suited for your company, as well as sit in on keynote and breakout sessions. Don’t miss this opportunity to earn nine CPE credits, network with other information security professionals, and better equip yourself to stay ahead of the pack. Venue: Toronto Contact: congress.scmagazine.com/page.cfm/link=10 » Portland SecureWorld June 17 This gathering offers a full day of cybersecurity education. Attendees can earn up to eight CPE credits, network with industry peers, partake in any of 30-plus educational elements. Venue: Portland, Ore. Contact: secureworldexpo.com/ portland/home » » Gartner Business Intelligence & Information Management Summit June 23-24 This year’s agenda explores how to apply new technologies and information management practices, analytics and business intelligence to improve performance management, generate new revenue and drive progress toward business goals. SANS Rocky Mountain 2015 June 22-27 Attendees will see the SANS promise in action: what one learns in the classroom will be applicable to use immediately upon returning to the office. Venue: Denver Contact: sans.org/u/PJ JULY » SANS Capital City 2015 July 6-11 Choose from an outstanding offering of courses. SANS knows that training and travel budgets are tight, so it is offering courses at the Capital Hilton. Venue: Washington, D.C. Contact: sans.org/u/PO ADVERTISER INDEX Company Page URL CyberSponse 19 cybersponse.com Dell 5 software.dell.com LogRhythm SANS SC Awards 2015 SC Congress Toronto Inside Front Cover 7 logrhythm.com sans.org Inside Back Cover awards.scmagazine.com Back Cover sccongress.com/toronto www.scmagazine.com • April 2015 • SC 49 LastWord Avoid a network stampede IoT will require a new approach to security, says vArmour CEO Timothy Eades. B oth enterprises and the consumer anxiously await the convenient future promised by the Internet of Things. The predictions place IoT at the precipice of opportunity, but for users and companies to fully tap its potential, they must first remove obstacles preventing a completely connected and secure network. People are plugging into a virtual stream of data, which offers great promise, productivity and an improved way of life. But, simultaneously, it creates gateways for attackers to penetrate. Every device and login is a potential access point for attack, making protecting against every intrusion impractical. Already, found vulner- abilities and reported hacks suggest a foreboding future in which hackers can spy on our homes or use a cool new office gadget to make their way to sensitive information. Data’s new nature – coupled with poor process management and the rapid evolution of the malware landscape – will mean unprecedented and potentially disastrous modes of attack, unless users implement software-based security to accommodate the changing landscape. To make IoT safe, users and companies must devise a way to visualize networks and understand their traffic at a lateral level – from device to device. Moreover, security processes need to improve between C-level execs, gatekeepers and users to align them in a world of increasing information and connectivity. It is already difficult to view laterally moving data traffic in existing data centers. In 2015, it can be expected that the expanding IoT space, with its growing number of interconnected devices serving as data hubs, will fall victim to the same issue to obscure data moving behind a perimeter. The current opaque nature of networked infrastructures has already made east/west traffic practically invisible, creating a virtual playground for would-be cybercriminals. In the future, perimeter defenses will amount to little more than chain-link fences weakened by the expanding thicket of interconnected devices. Companies will need to focus on understanding traffic flows to strategically stop attacks and impede exfiltration. Additionally, they will require systems that map hacker movement through files. Visualization of the network will also allow C-suite executives to understand security and enact better policies. Until the recent barrage of breaches, the C-suite was not as aware of security concerns as they should have been. But hackers aren’t slowing, and cloud-based information infrastructures are far from safe, especially considering how administrative control is ...the management of personal and enterprise devices will need to be managed...” often managed. Further, internal monitoring of admin controls will uptrend as more attacks gain momentum and enterprises will be more stringent on gatekeepers and top-down permissions. But the management of personal and enterprise devices will also need to be managed as systems become automated and new devices are introduced into company infrastructures. The face of data infrastructure and function has dramatically changed as the enterprise has progressed down the path of cloud, app and mobility. What is needed is the ability to place security controls closest to the asset wherever it resides. In this way, enterprises will have a distributed and consistent layer of visibility, control and threat defense across all of their assets – physical, virtual or cloud. With new devices computing at unprecedented levels, a smart watch or appliance will have the computing power your laptop or phone now has. Security needs to be addressed and built into the networks and IoT devices or it will open doors for an attack – and even the botnets of the future. A new, software-based, distributed approach is needed in order for IoT to realize its full potential. I hope we are ready. 2015 SC Awards Tuesday, April 21, 2015 InterContinental San Francisco Visit awards.scmagazine.com to view the finalists and book tickets. 50 SC • April 2015 • www.scmagazine.com You only have a few WEEKS LEFT! Register TODAY for SC Congress Toronto June 10 - 11, 2015 8:15 a.m. - 6:00 p.m. Metro Toronto Convention Centre SC Magazine subscribers can register today for $595. At SC Congress Toronto you will: • Gain insights from leading industry insiders convened only for SC Congress Toronto • Experience firsthand the latest cybersecurity solutions in our newly enhanced Exhibition Hall • Network with information security luminaries and peers over two days • Earn up to 14 CPE credits Kindly visit our new website at www.scongress.com and register today. Through April 15, please use Discount Code EARLYBIRDPRINT to receive $700 off the Full Conference Rate of $1,295. Visit SCMagazine.com for the latest in cybersecurity and to sign up for our newsletters and more.
© Copyright 2026