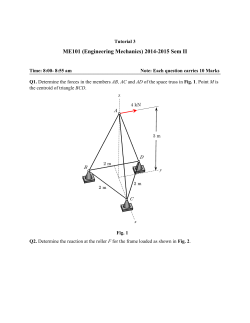
a Linux-based Platform for Achieving the Attack to Security Protocol
8th OAPS Working Paper Series
Website: http://www.oaps.hk/
Paper No. 2011-010
NMI - a Linux-based Platform for Achieving the Attack to
一
Security Protocol Semi-automatically
Shibo Luo1, Jing Fu2
1 UM-SJTU Joint Institute
2 School of Electronic, Information and Electrical Engineering
ABSTRACT
Security protocol is the special communication protocol which is used for strengthening the security
of communication process and confirming the privacy of message, the authenticity of subject’s identity
and the completeness of data by using cryptographic technique. It is widely used in Internet bank, online
shopping, Email and other network application. But security protocols are not as safe as their designer
thought, they can often be attacked through various bug. In the absence of a universal instrument to
construct attack by attacker’s own requirement, we developed NMI (Network Message Interceptor)
Platform, which is used for achieving the attack to Security Protocol semi-automatically.
The paper has introduced the runtime environment, structure, and implementation of NMI-Platform.
Then it used several application cases to demonstrate NMI-Platform’s function, if we have idea, we can
construct the idea into practical attack immediately. At last, it showed how to extend NMI-Platform’s
application range to wireless network protocol. NMI-Platform will bring convenient to the research fellow
who has interest on security protocol.
KEY WORDS
WORDS: Information Security, Security Protocol, NMI platform
1 Introduction
1.1 Security Protocol’s Application Status
Since informatization becomes more and more universal in government, military and
E-business, information security has become a common requirement in the whole society.
For achieving the object of sharing network resource in security, we often use security
protocol. Security protocol is a mutual communication protocol based on the cryptographic
mechanism. It is realized by two or more participants to take the promissory ways to
exchange messages. And it takes a sort of cryptographic algorithm to encrypt the whole or
part of exchange messages to achieve the preconcerted security objectives [1]~[2]. (Such as
authentification, assigning the key or confirming the message’s privacy)
Security protocol is also widely used in our daily life. It has various applications to
Emails, online shopping, internet bank and other network applications that need to guarantee
一
本论文受“上海交通大学本科生研究计划(PRP)”项目(T03017006)资助
上海交通大学 SJTU
1
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
the secrecy of users’ account, the non-repudiation and the fairness of transaction or the
completeness of messages.
Fig.1-1 the SSL Protocol Used in SJTU’s JAccount
1.2 Research Contents and Significance
Though security protocol has undertook the task of guaranteeing information security
and most security protocols was designed carefully, security protocol’s design is a complex
and subtle process, many security protocols are not as safe as their designer thought. For
example, one of the most famous early security protocols—“Needham-Schroeder
authentication protocol” [3], which is published in 1978 has being used until someone found
the bug after 17 years [4].
And even if a security protocol’s theoretical model is unassailable, there exists “the
realization of protocol’s code”, “the internet environment that protocol is applied” and other
secure factor, the security protocol can still have security risks. Hence analyze and check
whether a security protocol is secure is a troublesome problem. Sometimes, constructing an
attack to check whether a security protocol can be captured is a good way for finding the
bugs.
In the absence of an instrument which allowed attackers to construct attacks as their
own requirement, we developed NMI-platform. It is a universal instrument which has high
freedom and can be used conveniently. With NMI-platform’s help, attackers don’t need to
control the router or study the router’s structure and related knowledge any more. Attackers
also can save many time and energy which they spend on many complex works (such as
modify the operating system’s code and write great amount of code) before. When they have
idea about how to construct an attack, they can construct an attack immediately and check
the idea’s feasibility.
2
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
1.3 Some Explanation and Clarification
The NMI-Platform is not an instrument provided for hackers to break the internet
security and steal user’s information. It is designed for academic research and help
researcher to find the bugs of security protocol. Actually, it’s hard for hackers to use this
instrument do harm to internet public safety. The paper will explicate it in Chapter 3.2.
2 Security Protocol’s Attack Method
2.1 Dolev-Yao Model
Dolev-Yao Model [5] is a model which describes the internet environment. It is widely
used in protocol’s analysis.
In this model, we assume attackers won’t know any secret information before the
protocol begins, but attackers can control the whole internet any time. Attackers can wiretap,
intercept, modify and store all the information that transmits in internet. Attackers can be
legal participant to run the protocol. And we assume attackers have a great store of
knowledge and strong ability such as being familiar with various kinds of crypto-operation
to construct an attack.
At the same time, the model assumes the cryptographic algorithm which being used in
security protocol is perfect. This assumption mainly includes two aspects. On the one hand,
we must use the corresponding decryption key to decrypt the ciphertext. On the other hand,
the cryptosystem has enough redundancy, if someone wants to produce a ciphertext, he must
use corresponding plaintext and encryption key [6].
In sum, Dolev-Yao model is mainly concentrate on Security Protocol’s structure but not
cryptographic algorithm. It can be used to check whether a protocol can run regularly in the
worst internet environment.
2.2 Basic Symbols Representation for Security Protocol
This paper takes the basic symbol representation in Dolev-Yao model [5]. This
representation separates the security protocol from its specific cryptosystem. It is based on
the precondition that the specific cryptosystem is perfect in the given security definition. The
one line represents a message send step. The regular representation is below:
Message 2: A → B: {m}k
Message 2 shows this message is the second message in the protocol. A → B: {m}k
shows the participator A sends the message “{m}k” to the participator B ({m}k means use
key k to encrypt m). In addition, use I(A) or I(B) to represents the attacker “I” forged the
protocol’s participator A or B to send or receive the messages.
2.3 An Example of an Attack to Security Protocol
This section will introduce the theoretical model of a protocol which is designed by
Needham and Schroeder
上海交通大学 SJTU
[7]
. This protocol’s security objectives are changing key and do ID
3
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
authentication between two communicating parties. And the protocol realizes its security
objective with the help of a third-party notary S. The protocol’s process is below (the words
below each message is the explanation of the message):
Message 1: A → S: {A,B,Ra}Ks
At first, A encrypts “A”, “B” (represents the usernames of A and B) and “Ra” (the
random number produced by A) with S’s public key and send the encrypted packet to S.
Message 2: S → A: {B, Kab ,Ra}Ka ,{Kab,A}Kb
S decrypts the packet and produces a symmetric key Kab for A and B to communicate.
Then S encrypts “Kab”, “B” and “Ra” with A’s public key and encrypts “Kab” and “A” with
B’s public key. Then S sends these two encrypted packets to A.
Message 3: A → B: {Kab,A}Kb
A decrypts the received packet which is encrypted with A’s public key to get symmetric
key Kab and check the Ra decrypted from packet with the Ra produced by himself. Then A
sends the packet which is encrypted by B’s public key to B.
Message 4: B → A: {Rb}Kab
B decrypts the received packets and get Kab, then B produces a random number Rb and
encrypts it with Kab and sends the packets to A.
Message 5: A → B: {Rb-1}Kab
A decrypts the received packet and calculate Rb-1, then encrypt Rb-1 and sends the
packet to B. B decrypts the received packet to check Rb-1, if Rb-1 is right, he can confirm the
man who talk to him is A.
The protocol is over. This protocol is not perfect, it can be captured by the way below:
Message 1: A → S:
{A,B,Ra}Ks
Message 2: S → A:
{B, Kab ,Ra}Ka ,{Kab,A}Kb
Message 3: I(A) → B: {Kib,A}Kb
Message 4: B → I(A): {Rb}Kib
Message 5: I(A) → B: {Rb-1}Kib
As we can see, attacker “I” intercepts the packet which A sends to B (the Message 3 in
origin protocol). Then “I” encrypts the forged symmetric key “Kib” and “A” with B’s public
4
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
key and pretends A to send the packet to B. B will not know that “I” is pretending A to
communicate with him, then he will believe that Kib is the symmetric key for A and B’s
communication and the man who talk to him is A. The protocol is captured completely.
We will show how to use NMI-Platform to realize this attack in Chapter 4.
3 NMI-Platform
In the process of researching about security protocol’s attack method, we found that
construct attacks to attack security protocol is an effective way to check whether the security
protocol is secure. Then we developed NMI-Platform.
NMI (Network Message Interceptor) Platform is an instrument that developed by us
complete independently. It sets up in the internet router and has the competence of
intercepting, modifying and stealing the data packet that transmitting in internet.
In traditional way, when a researcher wants to construct an attack, he must control the
router and be familiar with the knowledge related to router. Or he will spend much time on
modifying the operating system’s code and writing great amount of code. And he must have
enough knowledge about how operating system run, how data packet transmit in internet,
and the structure of operating system’s kernel. And for different protocol, he may need to
write different program. But with the help of NMI-Platform, attackers can convert his ideal
into attack directly.
3.1 The Runtime Environment of NMI-Platform
Since NMI-Platform is designed for research fellows to find the bug for security protocol,
it uses the simulated router instead of practical router. We use a laptop with the operating
system of Ubuntu to connect the internet by cable (we call this laptop root computer). Then
we use this computer to establish a Wireless LAN, and let other terminal computer
(laboratory instrument computer) connect internet by this Wireless LAN. Then the terminal
computer and root computer constitute an Intranet, all data packet that other terminal
computers send to internet should pass through the root computer. And setting up
NMI-Platform in root computer, the root computer can become a simulated router.
Fig.3-1 the Practical Way of Users Connect to Server
上海交通大学 SJTU
5
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
Fig.3-2 the NMI-Platform’s Runtime Environment
As we can see, on the one hand, NMI-Platform can simulate the router and construct an
intranet completely. And on another hand, it can only intercept, steal or modify the data
packet from terminal computer, but doesn’t do harm to internet public security. And if
somebody wants to set up NMI-Platform in a practical internet router to hurt public security,
he may meet two big problems: At first, the practical router is usually placed on the private
room, it is not easy for somebody to touch, control, and install something on the practical
router. Second, most routers’ operating systems are not Ubuntu but other dedicated systems.
3.2 The Structure and Implementation of NMI-Platform
NMI-Platform is composed of three parts: Filter, Modifier and Transmitter.
Fig.3-3 the Construction of NMI-Platform
3.2.1 Filter
Filter’s main function is capturing the specified data packet according to user’s
requirement (such as the data packet from given IP, given Mac, or particular type of
protocol), then sends the captured packet to Modifier to do farther operation. The Filter is
based on the linux’s firewall (netfilter), and assist port---/proc file system. These settings
bring great convenience to the communication between man and computers and the data
communication between different processes. The Filter treats all data packets that pass
through the root computer as input, and then capture the packet which satisfied the
requirement.
6
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
Fig.3-4 the Analyzing Method of Filter
The method of Filter to capture the specified data packets is analyzing the bytes in the
packet (Fig.3-4). We extract the information from the specific location of the packet (such as
message heading), then we compare the information to the user’s requirement. If they are the
same, then we capture the packet.
3.2.2 Modifier
The function of Modifier is to do operation to the captured packets according to users’
requirements. For example, Modifier can modify the contents of the packets and disguise the
packets as legal packets then sends them into send buffer to wait for farther operation.
Modifier can also just get some information from the captured data and then throw it away.
Except the self-defined modification from users, Modifier also will do the modification as a
normal router needs to do. (Fig.3-5)
Fig.3-5 the Position of Modifier in Runtime Environment
Modifier modifies or extracts the data according to the rules about packet’s format of
security protocol. And Modifier disguises the packets as legal packets according to the
calculation method of various protocols. Modifier also uses assist port---/proc file system as
the buffer port between the process of Transmitter and the process of Modifier itself.
Fig. 3-6 Transporting Process of Data in Modifier
上海交通大学 SJTU
7
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
The arrow in Fig.3-6 shows the transporting process of data in Modifier. Preliminary
Modify includes the modification that routers should do, such as adjust the source address to
the root computer and subtract TTL by 1. Attack Modify will be set by users such as replace
the packets’ data as attackers’ own data. Disguise Modify disguises the modified packets as
legal packets then sends it into transmitter’s buffer to wait for farther operation.
For a root computer that loaded NMI-Platform as a router in internet, when the terminal
computer sends message to server in Internet, the data packet captured by the Intranet port
usually needs to do some modification before sends to internet. It requires very painstaking
modification. The detailed work process is below (use IPv4 as example).
a: change the destination MAC address to root computer’s former router’s mac address.
And change the source IP and source MAC address to the root computer’s IP and MAC
address.
b: subtracts TTL by 1
c: Attack Modify (it is mainly self-defined by users)
d: according to the algorithm strictly to calculate the checksums in all level, confirming
the correctness and timeliness
e: Recording of the packet. While the server responses the current router (root computer),
the router cannot identify the packet whether it is for the router itself or terminal
computer, because all packets caught by Filter has changed its source IP and MAC
address to root computer’s IP and MAC address (we have mentioned on a). Thus, there
is something necessary to be done to record the transforming operations.(In fact, the
router broadcasts the received packets throughout the inner net is also right, as that
packets with wrong IP will be abandoned).
f: sends the produced packet into Transmitter’s buffer.
Fig. 3-7 The Regular Process of Modifier
NMI-Platform has great freedom, the process above is the regular process. Actually, for
different requirements, we can throw out the captured packet directly or produce the packet
without any input.
The biggest trouble in the process is re-producing the checksum. For UDP and IP, we
can use the existed function in linux, but for TCP, we can only calculate the checksum by
ourselves. Re-calculate the checksum needs a certain amount of time, but many servers have
limitation about the time of receiving data. Since if the packets only have modification on
small number of bytes, we can get the result by calculate the difference value, it can save a
8
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
lot of time. NMI-Platform provides both two ways for users to choose accordingly. It can
satisfy most web-server.
Why don’t we use the existed router function on the operation system (linux) but
construct this part by ourselves?
If we use the router function of the operation system directly, we have to modify the
code of the operating system and catch the packet which is being processed, then do
operation to it and put it back. But this method has several unavoidable troubles:
� It will take a great amount of time to modify the operating system’s kernel code,
but this is not the key. The most serious problem is that an instrument implement by
modifying the operating system’s kernel code has no portability between the different
computers. But the instrument we construct is based on linux firewall (netfilter), it is a
module and can be set up on any computer with operating system of Ubuntu.
� Even if we can extract the data, modify it and put it back (as Fig.3-8), it is
obviously that when we process the data, we must suspend the process of the operating
system for some time. It’s practically impossible.
Fig.3-8 the Model of Extracting Data from System
3.2.3 Transmitter
The Filter and Modifier belong to the same process, but Transmitter belongs to another
process. Transmitter reads the packets in the buffer continuously until the buffer become
empty. The inputting information of the packet is accurately checked down to Link-Layer, so
there is no need to repack it and just sends it according to the MAC address.
All communications between different processes are using /proc file system.
Fig.3-9 Work Process of Transmitter
Filter and Modifier are at the same process, the same kernel process. Transmitter is
another user process. Transmitter will be blocked when buffer contains nothing. The
no-protocol sending model means we send a packet into the internet with source and
destination MAC and no process for protocol. (Fig.3-9)
上海交通大学 SJTU
9
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
The reason why using /proc file system as transmit buffer is considering about
NMI-Platform’s efficiency. There are three ways to establish communication of large data
blocks between different processes:
a.
Named Pipe: it has limitation of data’s size and can’t afford all packets
transmitting task.
b. Global Variable: it is applying to the processes of the same level, but not
suitable for a kernel-mode module and a user-mode process.
c.
/proc File System: it suits to exchange data between kernel-mode and
user-mode. Though it is not as fast as processing memory directly, it can confirm the
correctness and completeness of the exchanging data.
3.3 The GUI of NMI-Platform
We use GTK to do the GUI of NMI-Platform. Fig.3-11 is the welcome interface of
NMI-Platform. In Fig.3-12, user is inputting the source IP and MAC address of the packet
which he wants to capture.
Fig.3-10 The Logo of NMI-Platform
Fig.3-11 The Welcome Interface
Fig. 3-12 The Setting Input Interface
4 Application Cases of NMI-Platform
In this chapter, we will introduce several application cases to demonstrate NMI-Platform’s
function. The cases will show if you have idea of how to attack a security protocol, you can
convert your idea to practical attack immediately to check whether your idea has feasibility
with the help of NMI-Platform.
4.1 The Realization of an Attack to the Protocol Introduced in Section 2.3
Since the protocol we introduced in Chapter 2.3 is very old, we can hardly find it being
use in Internet. Therefore, we construct this protocol by ourselves,
10
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
We use the No.13 computer and the No.21 computer as protocol participants A and B.
The communication is between these two computers. We use RSA encryption algorithm as
the asymmetric cryptographic algorithm and we use DES encryption algorithm as the
symmetric cryptographic algorithm. And all keys are showed in table 4-1. (Since we have
mentioned in previous chapter, in protocol analysis, we don’t concentrate on the complexity
of key and cryptographic algorithm. Hence the keys we use is simple).
Table 4-1 The Key of All Participants and Notary
Public key
Private key
A
asl
soc
B
er1
o6u
S
rw3
i68
Below is the protocol’s process we have run:
a. A (No.13 computer) produces random number Ra =771, then encrypts “No.13”,
“No.21”,”771” with S’s public key “rw3” , and sends the packets to S.(Fig.4-1)
Fig.4-1
b. S decrypts the received packet and produces the symmetric key Kab=“pwu”. Then sends
{A, Kab ,Ra}Ka and {Kab,B}Kb to A. (Fig.4-2)
Fig.4-2
c. A decrypts {A, Kab ,Ra}Ka and gets Kab=”pwu”, and checks Ra=771. Then sends
{Kab,A}Kb to B (No.21 computer). (Fig.4-3)
Fig.4-3
d. B gets the Kab=”pwu” from decrypting the received packet. Then B produces a random
number Rb=1490 and uses Kab to encrypt it and sends the packet to A. (Fig.4-4)
上海交通大学 SJTU
11
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
Fig.4-4
e. A decrypts the received packet with Kab=”pwu”, then get Rb=1490, and encrypt
Rb-1=1489 with Kab=”pwu” (Fig.4-9), then sends the packet to B. (Fig.4-5)
Fig.4-5
f. As Fig.4-6 shows (the string seems like unrecognizable code in Fig.4-6 is the packet we
received on No.21 computer (B)), B decrypts the received packet with Kab, and get
Rb-1=1489. After check it with the Rb he produced. He will know the man who talk to
him is A and the Kab=”pwu”. And we run this protocol successfully.
Fig.4-6
Then we will show the process of using NMI-Platform to capture this protocol with the
method we have introduced in Section 2.3.
Since all message’s transmitting will pass through the root computer (router), attacker “I”
first intercept the message {Kab,A}Kb that A has sends to B in Step c by using the Filter of
NMI-Platform in root computer (In Dolev-Yao model, he can control root computer) . Then
he forged Kib=”lzd”, and encrypts it with B’s public key, then send the packet to B by using
the Modifier and Transmitter of NMI-Platform in root computer. (Fig.4-7)
12
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
Fig.4-7
B doesn’t know that the man talk to him is “I”, and believe that Kib=”lzd” (he decrypts
from received packet) is the symmetric key Kab, then he produces the random number
Rb=2711, and do as Step e. (Fig.4-8) Attacker “I” intercepts the message in root computer
(Fig.4-9 shows the packet that intercepted by NMI-Platform), decrypts it and get Rb
(Fig.4-10).
Fig.4-8
Fig.4-9
Fig.4-10
Then I encrypt Rb-1 with Kib=”lzd”, and sends the packet to B. B decrypts the received
packet, after check, he will consider the man talk to him is A, and Kib=”lzd” is the symmetric
key that S produces for A and B’s communication. Therefore, attacker “I” captured this
protocol. (Fig.4-11)
上海交通大学 SJTU
13
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
Fig.4-11
The result shows the attack method we have introduced in Section 2.3 is feasible and
valid.
4.2 Other Case We Have Constructed
In many websites, when user log-in, he or she can choose log-in automatically in the
same computer next time for convenience. This function is realized by Cookie. Server
returns a Cookie value to user and user’s browser saves it in the computer (The Cookie value
is different for different users). When user visits the website again, user’s browser will send
the Cookie value to the server. Then the server will check whether the Cookie value can
match to the user, if can, the server will allow user to log-in directly.
In mail163, it also uses Cookie to bring convenient to user (Fig.4-12). Therefore, we
think though mail163 has used SSL protocol to protect user’s information (Fig.4-12), we can
still use Cookie deceive to pretend others to log-in.
Fig.4-12 The SSL and Cookie of Mail163
We assume the Cookie value produced by mail163 is related to user’s IP address. We
think that mail163 has a function to calculate the Cookie value, and the variable for the
function is the IP address, when mail163’s server checks whether the Cookie value can
14
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
match to the user, the server will calculate the Cookie value again by using user’s IP address.
If the result is as same as the result that received form user’s browser, then server think it is
matching.
Since the computers in the same intranet showed the same IP address to the internet, we
came up with an idea: user A and user B are in the same intranet, when user A visits mail163,
user B uses NMI-Platform to identity, extract and save the Cookie value (only save and not
obstruct user A’s visit). Then user B connects to mail163, and uses NMI-Platform to
substitute the Cookie value in data packet into the Cookie value he extracted before
(Fig.4-13) .Then server will accept the Cookie value and allow user B to log-in with user A’s
account directly .
Fig.4-13
Unfortunately, we failed to cheat mail163. The server told us that the Cookie value did’t
match to user B. But it doesn’t mean what we have doone has no meaning. The result told us
that our idea is wrong, the design procedure of 163mail’s Cookie function is not only related
to user’s IP address. Now, we are finding other factors that may related to the production of
mail163’s Cookie value.
Anyway, NMI-Platform has finished its task in this case, we have uses it converting our
idea into practical attack sucsessfully.
5 Extension of the NMI-Platform’s Application Range to Wireless
Protocol
The original NMI-Platform can only catch the Ethernet protocol and the protocol above
Ethernet. The data packet of IEEE is being ignored. Therefore, it can only catch the protocol
that applied on cable network. Then we set the number of Netfilter (linux firewall)’s hook as
NF_IP_PRE_ROUTING (the initial data), and do some procession about 802.11MAC, and
modify some setting of Ubuntu. Then NMI-Platform is able to catch the protocol of IEEE
802.11 and do operation to wireless protocol.
上海交通大学 SJTU
15
Shibo Luo, Jing Fu
School of Electronical Information and Electrical Engineering
Fig.5-1 The Level of Data Packet
6 Further Work
Since our NMI-Platform still has some shortcomings, its GUI is still not friendly enough
and the flexibility of its operation need be strengthened.
And we have dabbled with the communication protocols of cellphone before but didn’t
research it profoundly. To extend NMI-Platform be adequate for checking the bugs of the
protocols which is applied on cellphone’s communication may be the further work we can
do.
7 Conclusion
The paper has introduced an instrument developed by us—NMI-Platform. It is based on
the linux for achieving the attack to security protocol semi-automatically. It can help
research fellows to find the bug of security protocol. And then, the paper introduced
NMI-Platform’s several application cases and extended function (processing the wireless
protocols). We believe this platform will bring convenient to research fellow who has
interest on security protocol.
Reference
[1] W. Mao. “Modern Cryptography Protocol: Theory and Practice”. English reprint by PEARSON
EDUCATION NORTH ASIA LIMITED and Publishing House of Electronic Industry, 2004.
[2] R.A. DeMillo, G.L. Davida, D. P. Dobkin, M.A.Harrison and R.J. Lipton. “Applied Cryptology,
Cryptographic Protocols, and Computer Security Models”. Proceedings of symposia in Applied
Mathematics, 29: 174, 1983.
[3] R.M. Needham and M.D.Schroeder. “Using Encryption for Authentication in Large Network of
Computers”. Communication of the ACM, vol. 21(12): 993-999, 1978.
[4] G. Lowe. “An Attack on the Needham-Schroeder Public Key Authentication Protocol”. Information
Processing Letters, 56(3): 131- 133, 1995.
[5] D.Dolev and A.C.Yao. “On the Security of Public Key Protocols”, IEEE Transactions on Information
Theory, 29(2): 198- 208, 1983.
16
上海交通大学 SJTU
8th OAPS Working Paper Series
NMI - a Linux-based Platform for Achieving theAttack to Security Protocol Semi-automatically
[6] Ling Dong, “Cryptographic Protocol Engineering Principles and Protocol Security Based on Trusted
Freshness”, [Doctoral Dissertation], ShangHai: Shanghai Jiao Tong University Department of
Computer Science and Engineering, 2008. (In Chinese)
[7] Mingyu Fan, Guangwei Wang, “Security Protocol’s Theorem and Technique”, Beijing, The Tsinghua
University Press, 2009. (In Chinese)
上海交通大学 SJTU
17
© Copyright 2026