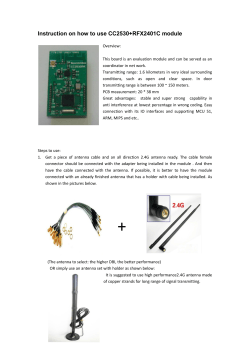
Lantronix How to add 802.11BG to your Embedded Device
Lantronix presents: How to add 802.11BG to your Embedded Device Gary Marrs Senior Field Application Engineer 06-26-09 1 @2004 Lantronix Corporation. All Rights Reserved. Confidential Agenda for Today Review of Basic RF concepts Wireless Security Implementing a WLAN embedded interface Troubleshooting a WLAN link Questions / Discussion 2 @2004 Lantronix Corporation. All Rights Reserved. Confidential About Lantronix Networking solutions for over 19 years (Founded: 1989) Sales, manufacturing, and support in Asia, Europe, USA Annual sales $56M+ Market and technology leader in device servers, console servers, and embedded Ethernet solutions Over 3,000,000 networkenabled devices and 20,000+ customers worldwide 3 @2004 Lantronix Corporation. All Rights Reserved. Confidential Lantronix Headquarters Irvine, California NASDAQ: LTRX What we Do… Lantronix Device Networking products provides complete solutions for complex networking integration. 4 Accelerated Time-to-Market: Lantronix Device Server’s are easy to integrate allowing any device to be enabled with network connectivity—in a few days using an external box and in a few weeks using an embedded unit. Reduced Design Risk: Lantronix products are already engineered, tested, and EMC-compliant, eliminating the R&D and investment risk inherent in any new design. Competitive Edge: Network enabling a device provides functionality with quantifiable benefits. Through pre-emptive notification and remote diagnostics, service costs will drop while responsiveness increases, simultaneously improving both revenue and customer satisfaction. @2004 Lantronix Corporation. All Rights Reserved. Confidential (Wireless Design) is a hard rocky path fraught with pitfalls for the naive and uninitiated Patrick Mannion – Senior Editor EE Times 5 @2004 Lantronix Corporation. All Rights Reserved. Confidential Implementing 802.11BG into an Embedded System… …Comes a reality of challenges: ● Difficulty of integrating chipsets and drivers ● Understanding of RF and TCP/IP networking ● FCC (Federal Communications Commission) and Worldwide certifications ● Wireless Security 6 @2004 Lantronix Corporation. All Rights Reserved. Confidential Which Wireless Technology is Right for Your Application? 7 RF technology Range Data Rate Power Security Zigbee 10-40 m Low Low Medium Bluetooth 10 / 100m Medium / High Medium Medium 802.11BG 100m High High High 802.11A 50m High High High Proprietary Wireless design Up to 4 km Low to Medium Low to High Low to Medium @2004 Lantronix Corporation. All Rights Reserved. Confidential IEEE 802.11 Wireless 8 @2004 Lantronix Corporation. All Rights Reserved. Confidential IEEE 802.11 - Infrastructure Mode In infrastructure mode (also called Infrastructure BSS), there is a wireless "station", which is usually a PC equipped with a wireless network interface card (NIC), and an "access point" (AP), which acts as a bridge between the wireless and wired networks. 9 @2004 Lantronix Corporation. All Rights Reserved. Confidential IEEE 802.11 Modes – Ad hoc Mode Ad hoc mode (also called peer-to-peer mode or an Independent Basic Service Set, or IBSS) is simply a set of 802.11 wireless stations that communicate directly with one another without using an access point or any connection to a wired network. 10 @2004 Lantronix Corporation. All Rights Reserved. Confidential Wireless Configuration To communicate via Wireless, the computers must have the same Network Name. The Network name for wireless is called the SSID. To add security, you can configure the Network Authentication and the Data Encryption. WEP, WPA and WPA2 are the standards for data encryption. To configure an Access Point – you can enable or disable SSID broadcast. An enabled SSID broadcast will allow anyone to find and connect to the access point. It is a good idea to change the default password on your AP or Wireless router. 11 @2004 Lantronix Corporation. All Rights Reserved. Confidential Basic RF Concepts 12 @2004 Lantronix Corporation. All Rights Reserved. Confidential Signal Strength There are 4 units of measurement used to represent RF signal strength. mW – (milliwatts) dBm – (dB-milliwatts) Received Signal Strength Indicator (RSSI) A percentage measurement Measuring RF energy in mW is not always convenient. Signal strength does not fade in a linear manner. Due to free space loss, RF energy fades inversely to the square of the distance. Example – measure the signal at 20m away from the AP. Then move to 40m away (double the distance), the signal power decrease by a factor of 4. 13 The dBm is a logarithmic function and mathematically represents this relationship very well. @2004 Lantronix Corporation. All Rights Reserved. Confidential Signal Power in Decibels The power of RF signal levels is commonly measured in Decibels (dB). dBm stands for a dB above one milliWatt To convert between watts and dBs use this formula: dB = 10 x log10 (power output / power input) To find dBm – simply use 1 mW for the input power dBm = 10 x log10 (power output / .001) ie.. 100 mW = 20 dBm mW values less than 1mW are represented by negative dBm values. Every 3 dB increase is a doubling of power 14 @2004 Lantronix Corporation. All Rights Reserved. Confidential Power in Decibels 15 Power (in watts) Power (in dBm) 0.000000000001 -90 = ,001 pW 0.00000000001 -80 = .01 pW 0.0000000001 -70 = .1pW 0.000000001 -60 = 1 pW 0.00000001 -50 = 10 pW 0.0000001 -40 = 100 pW 0.000001 -30 = 1 nW 0.00001 -20 = 10 nW 0.0001 -10 = 100 nW 0.001 0 = 1 mW 0.01 10 = 10 mW 0.1 20 = 100 mW 1 30 = 1W 10 40 = 10 W 100 50 = 100 W 1000 60 = 1000 W @2004 Lantronix Corporation. All Rights Reserved. Confidential Power (in watts) Received Signal Strength Indicator (RSSI) RSSI is generic radio receiver technology metric. IEEE 802.11 defines RSSI as a relative received signal strength in a WLAN environment, in arbitrary units. RSSI provides a way for the circuitry on a WLAN NIC to measure and represent RF energy. RSSI measurements are unit less and in the range 0 to 255. The maximum value, RSSI_Max, is vendor dependent. Every chipset vendor scales the RSSI differently. The 802.11 standard does not define any relationship between RSSI value and power level in mW or dBm. Key Point – you can not compare the RSSI readings from different WLAN chipset vendors. 16 @2004 Lantronix Corporation. All Rights Reserved. Confidential Percentage Signal Strength The percentage represents the RSSI for a received packet. The RSSI value is divided by RSSI_Max and multipled by 100. Provides a good way to circumvent the complexities of RSSI readings. If all vendors used percentage, then percentage would provide a good cross vendor metric for comparing signal strength. 17 @2004 Lantronix Corporation. All Rights Reserved. Confidential Antennas An antenna is a device that is made to efficiently radiate and receive radiated electromagnetic waves. There are several important antenna characteristics that should be considered when choosing an antenna for your application as follows: Antenna radiation patterns Power Gain Directivity Polarization 18 @2004 Lantronix Corporation. All Rights Reserved. Confidential Antenna Radiation Patterns An antenna radiation pattern is a 3-D plot of its radiation far from the source. Antenna radiation patterns usually take two forms, the elevation pattern and the azimuth pattern. Angle The elevation pattern is a graph of the energy radiated from the antenna looking at it from the side. Sometimes referred to as the vertical view. 19 @2004 Lantronix Corporation. All Rights Reserved. Confidential Sin2 Angle Antenna Radiation Patterns The azimuth pattern is a graph of the energy radiated from the antenna as if you were looking at it from directly above the antenna as illustrated. Sometimes referred to as the Horizontal view. 20 @2004 Lantronix Corporation. All Rights Reserved. Confidential Y Angle X Rubber Duck Omni Antenna 21 @2004 Lantronix Corporation. All Rights Reserved. Confidential Reflector Grid WLAN Antenna 22 @2004 Lantronix Corporation. All Rights Reserved. Confidential Antennas – Power Gain The perfect antenna is known as an Isotropic radiator – generates a perfect sphere of energy like light emitted from a light bulb. Isotropic radiators only exists in theory The Gain of an antenna is a ratio of the power input to the antenna to the radiated power output. The simplest antenna is a dipole antenna. Consists of 2 equal length pieces of wire that are at a length that is resonant to the desired frequency. Dipole antennas exhibit 2.1 dB of gain!!! The gain of an antenna is specified in dBi or dBd. dBi is the gain referenced to an isotrope. dBd is the gain referenced to a dipole. 23 @2004 Lantronix Corporation. All Rights Reserved. Confidential Antennas - Polarization Polarization is the orientation of electromagnetic waves far from the source. For Example - a simple dipole antenna produces a signal polarized in the same plane as the antenna. A vertically mounted dipole produces a vertically polarized signal. Ideally, the receiving antenna should be co-polarized with the transmitting antenna. A cross-polarized receiving antenna offers significant rejection of the transmitted signal. 24 @2004 Lantronix Corporation. All Rights Reserved. Confidential Types of Antennas Dipoles and Isotropes are common omnidirectional antennas. This means they generate a field 360 degrees around them. Yagi – is a common high gain directional antenna. Patch or panel – useful for their slim profile Dish or Parabolic – very high gain directional antenna 25 @2004 Lantronix Corporation. All Rights Reserved. Confidential Signal to Noise Ratio - SNR Defined as the ratio of a signal power to the noise power corrupting the signal 802.11 environments use this term slightly different. There it is used as “ the ratio of the power of the data signal to the power level of the noise floor”. In this case, noise refers to the background RF radiation present in the receiver's environment. Every environment has some noise; sources of interference, like cordless phones and Bluetooth, increase noise. Signal-to-Noise Ratio (SNR) compares peak signal strength to noise. An SNR of 22 dB or more is workable. The higher the SNR, the more stable and usable the WLAN network is. 26 @2004 Lantronix Corporation. All Rights Reserved. Confidential RF Interference - Multipath Multipath interference – occurs when the desired signal reaches the receiving antenna via multiple paths, each of which has a different propagation delay and path loss. Each of the received signals are summed at the receiving antenna Caused by reflections off objects in the environment or atmosphere. 27 @2004 Lantronix Corporation. All Rights Reserved. Confidential RF Interference - Fade Signal Fading is interference related to a time-varying change in the path loss of a link. The movement of objects in the radio path causes reflections which result in random variations in amplitude and the frequency of the received signal. Examples are – leaves blowing in the wind, rain and someone closing a door. Fade Margin – this is the amount of power in excess of what is needed to maintain a connection. Or, the amount by which a received signal level may be reduced without causing system performance to fall below a specified threshold value. The greater the fade margin, the more reliable the system will be under adverse propagation conditions. 28 @2004 Lantronix Corporation. All Rights Reserved. Confidential Antenna or Spatial Diversity Antenna diversity - a receiving station obtains two observations of the same signal sent from a transmitting station. The receiver will switch reception to the antenna currently receiving the stronger signal. For best results, the antennas are usually placed one wavelength apart. Only useful for receiving data. The use of antenna diversity can augment the wireless connection and minimize the effects of multipath interference. The Diversity Gain is the ratio of the signal field strength obtained by diversity to the signal strength obtained by a single path. Diversity gain is usually expressed in dB. 29 @2004 Lantronix Corporation. All Rights Reserved. Confidential Free Space Loss (FSL) Radio waves get weaker with distance The attenuation associated with distance in an unobstructed path is called Free Space Loss. FSL (in dB) is calculated by using the following formula: (20Log10 x freq. in Mhz) + (20Log10 x dist. in miles) + 36.6 For example - at 2.4 Ghz for 2 miles FSL = 20Log10 x 2,400 + 20Log10 x 2 + 36.6 = 110 dB The higher the frequency, the more attenuation will occur over a given distance. A 6 dB power change will double or halve the total distance. 30 @2004 Lantronix Corporation. All Rights Reserved. Confidential Free Space Loss at 2.4 Ghz FSL in dB 31 3 100 .6 201 .2 402 .3 804 .7 1 .6 km 3 .2 km 8 .0 5k 16. m 1k 40. m 25 80. km 5k m 50. 1 25. 2 12. 6 .1 3 .0 1 .5 Free Space Loss (FSL) 40 50 60 70 80 90 100 110 120 130 140 150 @2004 Lantronix Corporation. All Rights Reserved. Confidential Receiver Sensitivity Receiver Sensitivity is the lowest power level at which the receiver can detect an RF signal and demodulate data. Sensitivity is purely a receiver specification and is independent of the transmitter. Improving the sensitivity on the receiver (making it more negative) will allow the radio to detect weaker signals, and can increase the transmission range. Receiver Sensitivity is dependent upon transmission speeds! 32 @2004 Lantronix Corporation. All Rights Reserved. Confidential A Link Budget How many dBs of radio path loss can my Wireless link handle before communications deteriorates ? We can easily answer this once we have the following pieces of information: Radio transmit power (Ptx) Transmit antenna gain (Gtx) Receiver antenna gain (Grx) Diversity Gain (Gdv) Receiver Sensitivity (Srx) Fading Margin (M) Using the Formula: LB = Ptx + Gtx + Grx + Gdv – Srx - M 33 @2004 Lantronix Corporation. All Rights Reserved. Confidential A Link Budget Example - Downlink For example, suppose we have the following link. We are transmitting from a Orinocco AP-700 Access Point to a Lantronix WiPort at 11 Mbps. Here is the data: Transmit power = 24 dB Transmit antenna gain = 2.1 dBi Receiver antenna gain = 2.1 dBi Diversity Gain (Gdv) = 0 dBi Receiver Sensitivity = -82 dBm (of the WiPort) Fading Margin (M) = 20 dBm LB = 24 + 2 + 2 + 0 – (-82) – 20 = 90 dBm This means that the radio link can overcome 90 dB of attenuation and still work correctly 34 @2004 Lantronix Corporation. All Rights Reserved. Confidential A Link Budget Example - Uplink The next example, we have the return link (called the uplink). We are transmitting from a Lantronix WiPort to a Orinocco Access point at 11 Mbps. Here is the data: Transmit power = 14 dB Transmit antenna gain = 2.1 dBi Receiver antenna gain = 2.1 dBi Receiver Sensitivity = -84 dBm Diversity Gain (Gdv) = 2 dBm Fading Margin (M) = 20 dBm LB = 14 + 2 + 2 + 2 – (-84) – 20 = 84 dBm This means that the radio link can overcome 84 dB of attenuation and still work correctly. However, it is 6 dBm worse than the downlink and will only have a range of half as far. 35 @2004 Lantronix Corporation. All Rights Reserved. Confidential Analysis of Link Example This formula provides an estimate of performance. It allows you to compare competing solutions and estimate service coverage. This formula does not account for cable or connector losses. These can be significant and should be considered for real applications. You must calculate the link in both directions. Typically, an access point will have higher gain than a remote station adapter. The weaker link of the two, will be the limiting factor. In clear free space, the Down link example is good for around 314 meters. However, the uplink is good for only 157 meters. Which is what we should have expected – half the distance. These examples assume that there are no obstructions. If obstructions or interference exist (which is very likely), then the link margin will be less. 36 @2004 Lantronix Corporation. All Rights Reserved. Confidential Link Adjustments What can you do to get more link (or fade) margin? Since the IEEE- 802.11 and the FCC regulate the spectrum, you can not increase power output! You can shorten the distance or minimize interference / obstructions. Not Practical !!! You can use an antenna with more gain. This is a reasonable choice but it does require some paper work (and possible testing) with the FCC. The most practical solution is to increase Receiver sensitivity by selecting a slower transmission speed. Simpler modulation schemes provide better receiver sensitivity. 37 @2004 Lantronix Corporation. All Rights Reserved. Confidential Wireless Security 38 @2004 Lantronix Corporation. All Rights Reserved. Confidential Wireless Security Wireless security presents a challenge because anyone in ear shot range can potentially receive your data. There are 2 pieces to a secure WLAN connection. Encryption and Authentication = A Secure Environment Encryption is the scrambling of data prior to transmission Authentication determines if client radio is authorized to connect to the wireless network Both require additional processing power that can tax an embedded system Built-in security is a good option Large enterprise environments need a better way to handle Key management. 39 @2004 Lantronix Corporation. All Rights Reserved. Confidential Wired Equivalent Privacy - WEP Most WLANs in use today use WEP. WEP is vulnerable to attack for a number of reasons. WEP uses RC4 algorithm for encryption with a 40 bit or 104 bit key. The initialization vector (IV) is 24-bit. For authentication there is Open or Shared Key. Open is essentially no Authentication. With Shared Key, WEP is used for authentication. A four-way challenge-response handshake is used. It is possible to derive the keystream used for the handshake by capturing the challenge frames in Shared Key authentication. Both Authentication mechanisms are weak. In August 2001, Fluhrer, Mantin and Shamir published a cryptanalysis of WEP that explained how to recover the RC4 key after eavesdropping on the network in as little as one minute. 40 @2004 Lantronix Corporation. All Rights Reserved. Confidential WiFi Protected Access - WPA WPA was created in response to several serious weaknesses researchers had found in WEP. Intermediate solution until 802.11i was finalized. WPA supports 2 modes. A less secure "pre-shared key" (PSK) mode. Also supports an enterprise authentication mode that is designed for use with an 802.1x authentication server. Data is encrypted using the RC4 stream cipher, with a 128-bit key and a 48-bit initialization vector (IV). One major improvement in WPA over WEP is the Temporal Key Integrity Protocol (TKIP), which dynamically changes keys as the system is used. When combined with the much larger IV, this defeats the well-known key recovery attacks on WEP. By increasing the size of the keys and IVs, reducing the number of packets sent with related keys, and adding a secure message verification system, WPA makes breaking into a Wireless LAN far more difficult. 41 @2004 Lantronix Corporation. All Rights Reserved. Confidential IEEE802.11i / WPA2 Security WPA2 is the approved Wi-Fi Alliance interoperable implementation of 802.11i. WPA2 makes use of the Advanced Encryption Standard (AES) block cipher (referred to as CCMP); WEP and WPA use the RC4 stream cipher. Like WPA, WPA2 supports 2 modes. A pre-shared key mode (PSK), also known as personal mode and 802.1X for enterprise authentication. PSK mode is used in small networks that don’t require the complexity of an 802.1x authentication server. The key can be entered as 64 hex digits or as a pass phrase of 8 to 63 ASCII characters. PSK mode provides authentication via a pre-shared key, or password. 42 @2004 Lantronix Corporation. All Rights Reserved. Confidential IEEE802.11i / WPA2 Security Enterprise authentication mode uses the Extensible Authentication Protocol (EAP) and typically requires a RADIUS or other authentication server for strong authentication. 802.1X includes several different types of EAP protocols for enterprise security. EAP-TLS EAP-TTLS/MSCHAPv2 PEAPv0/EAP-MSCHAPv2 PEAPv1/EAP-GTC EAP-SIM LEAP is a Cisco protocol used in hospitals and other large enterprise applications. LEAP has exposed weaknesses and is not part of the 802.11i specification. 43 @2004 Lantronix Corporation. All Rights Reserved. Confidential Implementing a Wireless LAN Solution for an embedded device 44 @2004 Lantronix Corporation. All Rights Reserved. Confidential Implementing an 802.11B WLAN There are 3 options for implementing a WLAN interface for an embedded application. 1. The first option is to buy a chip set (usually 2 or more chips) and integrate the hardware and software into your existing application and uP. 2. The second option is to integrate a PCMCIA (PC Card) or a Compact Flash (CF) card with your existing uP and operating system. 3. The third option is to buy an off-the-shelf solution that is designed to integrate directly with your existing controller. 45 @2004 Lantronix Corporation. All Rights Reserved. Confidential Tradeoffs for the Chip set solution Advantages Can provide a cost effective solution for high volume applications Allows the most customizations of the network and radio Interface. Disadvantages Requires RF technical expertise to complete the hardware design Requires extensive software integration to interface to the existing uP. Requires complete FCC testing and approval before product can be released Time to Market – 14 to 18 months minimum. 46 @2004 Lantronix Corporation. All Rights Reserved. Confidential Implementing a CF or PC card design Must support the full CF or PC card interface here. 32 bit MicroController TCP/IP Stack CF or PC Card SW Driver +3.3 V and gnd 47 @2004 Lantronix Corporation. All Rights Reserved. Confidential CF or PC WLAN Card Tradeoffs for the PC Card / Compact Flash (CF) solution Advantages Makes sense if you are going to implement an OS that already supports that particular card Some cards offer higher output power Disadvantages Requires a fair amount of storage and processing on the host CPU. The embedded CPU must support a full TCP/IP stack. Requires software integration to interface to the existing Driver. In some cases the driver is hard to get. Can require extensive FCC testing and approval before product can be released Some or all of the encryption or key generation will be relegated to the host CPU Time to Market – 10 to 12 months minimum. 48 @2004 Lantronix Corporation. All Rights Reserved. Confidential Tradeoffs for the off-the-shelf solution Advantages Can easily integrate with existing uP firmware. Does not require any changes to existing firmware code if you are already using a serial interface. Design can be completed in 4 to 8 weeks (quick time to market). Does not require highly skilled RF HW and SW engineers on staff to implement. The OEMs FCC compliance can be leveraged to gain approval. In most cases it is only a paper work project if the design uses a 3 dBi antenna or less. Disadvantages Limited options to customize RF interface. 49 @2004 Lantronix Corporation. All Rights Reserved. Confidential Implementing an off-the-shelf solution 50 @2004 Lantronix Corporation. All Rights Reserved. Confidential Lantronix WLAN Modules - Advantages • MatchPort BG, MatchPort BG Pro & WiPort • Fast time to market. Wireless connectivity in as little as 60 days. Reduces project risk • Eliminates the need for RF & networking expertise • Frees up resources to focus on your application solution • Built-in WEP, WPA & WPA2 security. Support for PSK or full enterprise security. • Both Wire and Wireless in one module. POE options for wired Ethernet • Supports serial to WLAN or Ethernet bridging to WLAN. • Compact form factor • Future proof technology allows us to easily productize new Wireless devices 51 @2004 Lantronix Corporation. All Rights Reserved. Confidential WiPort Wireless Embedded Device Server • IEEE 802.11BG wireless radio • Capable of Wired or Wireless communications Serial to 802.11BG Serial to 10/100 Mbps Wired Ethernet Bridge 10/100 Mbps to 802.11BG • Built-in WEB Server. 1800 KB Flash Memory available for OEM WEB pages WPA & WEP & 802.11i PSK security • 2 High Speed Serial Ports (920 Kbps) • Up to 11 digital I/O Pins ModBus ASCII/TCP or RTU/TCP (optional) RS485 support included • Power 3.3 VDC @ 460 mA max • Operating Temperature of -40 to +70 C • FCC CFR47 part 15 Compliant 52 @2004 Lantronix Corporation. All Rights Reserved. Confidential WiBox – External Wireless Device Server External Wireless Device Server • IEEE 802.11bg wireless radio • Adhoc or Infrastructure modes • Supports bridging • 1800 KB Flash Memory available for OEM WEB pages • 2 High Speed Serial Ports (920 Kbps) • Port 1 – RS232 • Port 2 – RS232, RS422 or RS485 • Power 9 to 30 Vdc (2W max) • Operating Temperature of 0 to +60 C 53 @2004 Lantronix Corporation. All Rights Reserved. Confidential MatchPort BG Optimized 802.11 b/g Radio module • Capable of Wired or Wireless communications WEP, WPA & WPA2 PSK built-in security Serial to 802.11BG Serial to 10/100 Mbps Wired Ethernet Bridge 10/100 Mbps to 802.11BG Exclusive AES end-to-end encryption option 2 Serial ports - 921 Kbps Data Rate 802.11 Power Saving Radio Sleep Mode Options Web Server with Java Applet Support Operating Temperature of -40 to +70 C • FCC CFR47 part 15 Compliant Compact: 45mm x 45mm with 40-pin 2 mm Header 54 @2004 Lantronix Corporation. All Rights Reserved. Confidential MatchPort BG Pro Optimized 802.11 b/g Radio module • Capable of Wired or Wireless communications Serial to 802.11BG Serial to 10/100 Mbps Wired Ethernet Bridge 10/100 Mbps to 802.11BG WPA, WEP & 802.11i (AES-CCMP encryption) PSK WPA2 Enterprise/EAP Protocols • 2 Serial Ports (230 Kbps) • Up to 5 GPIO digital I/O Pins • Power 3.3 VDC @ 460 mA max • Operating Temperature of -40 to +70 C • FCC CFR47 part 15 Compliant On-board U.FL antenna cable connector Variety of available cables to meet customer needs Pin Compatible with all MatchPort 55 @2004 Lantronix Corporation. All Rights Reserved. Confidential Trouble shooting WLAN NetStumbler – a useful tool for pinpointing details of a wireless network, helping you configure, secure, optimize and discover. http://www.netstumbler.com/ Ethereal/Wireshark – Very useful for troubleshooting Ethernet and 802.11bg networks. http://www.wireshark.org/ Airsnort - a wireless LAN (WLAN) tool which recovers encryption keys. Passively monitors transmissions, computing the encryption key when enough packets have been gathered. Fluke – hand-held tools for WLAN analysis. 56 @2004 Lantronix Corporation. All Rights Reserved. Confidential Network Diagnostic Utilities IPCONFIG – Shows the entire TCP/IP configuration present in a host computer Type in: C:\IPCONFIG PING – Test connectivity across the network and confirm that an IP address is reachable Type in: C:\PING <ip address> ARP (ARP.EXE) – Used to display the ARP cache which holds the IP to MAC address translation Type in: C:\ARP –a to see ARP cache 57 @2004 Lantronix Corporation. All Rights Reserved. Confidential References for Wireless Networking Implementing 802.11, 802.16 and 802.20 Wireless Networks, Ron Olexa. Elsevier Communications Engineering Series 802.11 Wireless LAN Fundamentals, Pejman Roshan, Jonathon Leary. Cisco Press. 802.11 Wireless Networks – The definitive Guide. Matthew S. Gast. O’Reilly “You believe you understand what you think I said…” Joshua Bardell 58 @2004 Lantronix Corporation. All Rights Reserved. Confidential Thank you… Questions?? @2004 Lantronix Corporation. All Rights Reserved. Confidential
© Copyright 2026