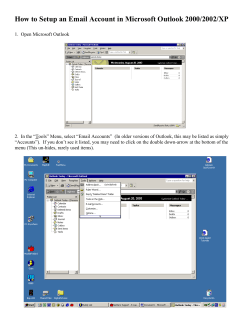
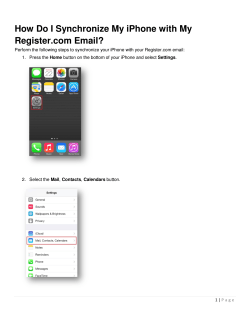
What is Information Technology?
What is Information Technology? Information Technology (IT) consists of computers, networks, and the applications they support such as electronic mail and the World Wide Web. These technologies are critical to the AUC mission, a mission that includes teaching, research and public service. What is IT contd. IT increases communication opportunities and affects the way we conduct business as a university in the following: Examples of how IT is connected All students, faculty, and staff may have an e-mail account. All members of AUC may obtain computer user privileges. Students frequently submit assignments using e-mail. Committee reports or presentations may appear in Web form only. Communication is increasingly done through the e-mail system. Responsibilities in IT. While information technology helps us function, it also requires responsible use from each user. Your actions on this campus can affect people throughout the world. These technologies require responsible use with respect for others. Responsibilities of IT contd. Information technology is provided to support the essential mission of AUC campus. Your use of information technology is governed by campus policies, and regulations. If an action is against the law it is against campus Policy – whether specifically spelled out or not! Responsibilities of IT contd. You are requested to use information technology with courtesy, respect and integrity. Things to expect As a user of ITS at this facility and in AUC, there are certain things you can expect: I- What can I expect? II- What are my responsibilities? III- Can I …... IV- What can happen? V- What is not against L-A-W OR POLICY? VI- Reporting an incident? I- What can I expect? Is my e-mail private? Are my files private? What are my First Amendment rights? What can I do about being harassed? What happens if someone complains about me? Is my e-mail private? E-mail stored on University-operated mail servers requires a password for access and is therefore protected on the mail server, based upon the security strength of that password. E-mail is thought of as a postcard, where privacy is supposed to be observed, but in cases when needed to remedy problems with an e-mail system, the systems administrators may become aware of the contents of some messages. Are my files private? The university respects the contents of your files and does not review file content. However, system administrators may become aware of the content while dealing with some system problems. What are my First Amendment rights? As an Academic institution, we place great value on freedom of thought and expression. All students associated with the university should exercise their freedoms in a mature, responsible, and respectful manner What can I do about being harassed? Unfortunately, rudeness is not harassment and neither are other boorish behaviors. If you feel you are harassed, it should be reported to the Dean for Student Affairs II- What are my responsibilities? a- Protecting Resources from Physical Access b- Protecting Resources from Electronic Access c- Responsible Use of E-mail d- Responsible and Efficient Use of Limited Resources a- Protecting Resources from Physical Access You are responsible for the use of your computer account and the activities performed under the current. - You must keep your account secure by preventing others from getting access to your personal computer, desktops, laptops, notebooks, etc. Important: Remember that you are responsible for all e-mail or other communications sent from your computer or access port. - b- Protecting Resources from Electronic Access You are responsible for protecting your account and its resources from unauthorized electronic access by using effective passwords and by safeguarding those passwords. University Information Technology serves a diverse group of users and are selectively opened to make access and operation easy for users, and the responsibility for protecting the access falls on you – the user. In a nutshell, if something is done in your name then its yours. c- Responsible Use of E-mail - - Students are encouraged to use electronic mail for university related material and to facilitate the efficient exchange of useful information. Access and use of mail has certain responsibilities. Users of e-mail are expected to be ethical and responsible in their use, following general guidelines (found in the UNS department in the Hill House 3rd floor room 301) based on common sense, common decency, and civility applied to the networked computing environment. C- Responsible Use of E-mail, contd. - - Messages sent as electronic mail shall meet the same standards for distribution or display as if they were tangible documents. Identify yourself clearly and accurately in all electronic communications. Concealing or misrepresenting your name or affiliation to dissociate yourself from responsibility for your actions is never appropriate. C-Responsible Use of E-mail, contd. - All electronic mail files belong to somebody. They should be assumed to be private and confidential unless the owner has explicitly made them available to others. d- Responsible and Efficient Use of Limited Resources You are expected to promote and practice efficient use of network resources, consistent with the instructional, research, public service, and administrative goals of the University. Show consideration for others and refrain from engaging in any use that would interfere with their work or disrupt the intended use of network resources. III- Can I … …share my computer account? …give other people an account on my multiuser computer that is connected to the campus network? …tell others about a “Make Money Fast” scheme? …play a joke on my friend by deleting his/her files? …get even with some jerk by sending him a flood of e-mail messages? … copy some vendors software for my friends? Can I share my computer account? No. The university provides your computer account for your exclusive use. IT resources should only be used for approved purposes. Don’t give your password to anyone else, even people you trust, such as your friends or relatives or even someone who has offered to help you fix a problem. Assume your user ID is the equivalent of your signature! Can I share my computer account ? Contd. You are responsible for all charges accrued using the ID number/password or computing resource assigned to you, even if a friend using your password without your permission runs up the charges. You will also be held responsible for destructive or illegal activity done by someone to whom you gave access. Can you give other people an account on my multi-user computer that is connected to the campus network? No. This activity gives those other people access to university computer resources, which is against IT policy. Can I tell others about a “Make Money Fast” scheme? No. These are called “chain letters” and are explicitly illegal. Can I play a joke on my friend by deleting his/her files? No. Such activities are illegal, and you are not exempted from the law because you are “just a student” or are underage or it was “my friend” even if you were “just playing around.” Can I get even with some jerk by sending him a flood of e-mail messages? No. This is called a “mail bomb” and is inappropriate use of resources. Can I copy some vendors software for my friends? No. It is a violation of university policy and federal law to participate in copyright infringement. Copyrighted materials include, but are not limited to, computer software, audio and video recordings, photographs, and written material. Violators are subject to University discipline, as well as legal liability, generally – even if the work does not contain a written copyright notice. IV- What can happen? What are the repercussions for violating the rules as listed in section III of Can I…? Punishment for infractions include but is not necessarily limited to: 1- Verbal warnings 2- Revocation of computing privileges 3- Disciplinary probation 4- Suspension and/or expulsion from university 5- Civil liability 6- Criminal prosecution V- What is not against L-A-W OR POLICY? Before you report what you believe is an incident of misuse make sure you are on the right track. First Amendment rights: In general, expressions of opinion by members of the university community that do not violate the law or university rules are protected as “free speech.” We encourage all those associated with the University to exercise their constitutional rights and freedoms responsibility. V- What is not against L-A-W OR POLICY? Contd. AUC does not punish its students for expressing views that may be unpopular or offensive, but who break no laws or University rules while doing so. “Spam” Mail “Spam,” unsolicited and unwanted email, and other junk mail from a source outside this university. Many people are annoyed by junk mail such as “spam” and other kinds unsolicited or unwanted e-mail. It is not unusual, for junk mail to originate from a source outside the University. In most such cases, the University has little control. In most cases, the University has little control. “Spam” Mail contd. However, as a recipient you have a great deal of control: 1- You can ignore or delete the junk mail. 2- You can filter your email so the offending mail is filed unread in a junk mail file, allowing you to delete it at your leisure. Breaches of “Netiquette” Disagreements between people, even heated arguments, unless threatening or otherwise unlawful, are not considered violations. We do however, strongly encourage all users to be polite. A well-known problem with email, newsgroups, and chat groups is that it’s easy to fire off a quick, angry response that you’ll later wish you hadn’t sent. Breaches of “Netiquette” contd. In doing so, should you cross the line beyond merely being rude or stating an unpopular, offensive view, you may run the risk of violating criminal laws. “Counting to ten” before saying something you may later regret applies in cyberspace too. VI- Reporting an incident? For reporting problems with mail, you may want to notify the University Network Services, Help Desk extensions: 5343,5625, 5624 located at the Hill House Building – 3rd Floor room 302. Your problem will then be handled either by one of the Help Desk personnel or you will be referred to the appropriate entity.
© Copyright 2026