Implementing and Automating Critical Control 19: Secure Network Engineering for
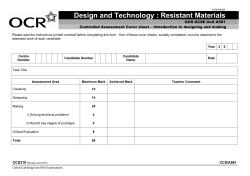
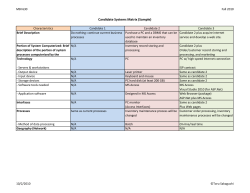
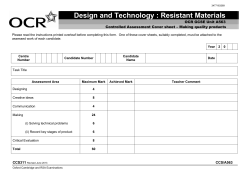
Implementing and Automating Critical Control 19: Secure Network Engineering for Next Generation Data Center Networks Aron Warren, George Khalil, Michael Hoehl February 2012 SANS Technology Institute - Candidate for Master of Science Degree Objectives • Introduction • Secure Network Engineering • Challenges for Next Generation Networks • Functional Requirements • Key Risk Considerations • High-Level Design and Build Approach • N-Tier Application and Infrastructure Control Checklist • Lessons Learned SANS Technology Institute - Candidate for Master of Science Degree Introduction • SANS 20 Critical Security Controls for Effective Cyber Defense • Security Control 19 “Secure Network Engineering” • Technical approaches to advance this control • Scope is for Web/Mobile App and 40GbE SANS Technology Institute - Candidate for Master of Science Degree Secure Network Engineering • Document Gathering is First Step • Understand Data Flows • Log Events and Correlate • Apply Least Privileged Principles • Divide and Secure • Establish Trust and Validate Data Integrity • Test and Validate Routinely SANS Technology Institute - Candidate for Master of Science Degree Challenges for Next Generation Networks • 40GbE is still early in “hype” cycle for Enterprises • Throughput speed ≠ Wire speed • Uncertainty increases relative to speed • Limited forensic team experience with 40 GbE • Existing operations resource capacity SANS Technology Institute - Candidate for Master of Science Degree Functional Requirements 1. Documentation 9. Virtual and Blade Servers 2. Data Center Physical Controls 10. Vulnerability and Threat Mgt 3. Enclaves 11. Log Mgt 4. Firewalls and Security Apps 12. Asset Mgt 5. Internet Access 13. Access Mgt 6. DNS 14. Performance Mgt 7. Hardening 15. Forensic Mgt 8. Config and Change Mgt 16. Service Mgt SANS Technology Institute - Candidate for Master of Science Degree Key Risk Considerations • Mixing assets of different value • Integrating security and network controls • High event volume and Impact of false negatives • Understanding data flows and security policies • Performance impact of inspection • Protecting high authority access • Configuration errors and product defects SANS Technology Institute - Candidate for Master of Science Degree High-level Design and Build Approach SANS Technology Institute - Candidate for Master of Science Degree N-Tier Application Control Checklist Enclave for each app function Dedicated Internet Access Firewall Security Fabric Separate Infrastructure Firewall SSL Accelerator and Proxies Tiered DNS Virtualization and Blade Servers Netflow Network Address Translation Network Monitoring Switch Load Balancers SANS Technology Institute - Candidate for Master of Science Degree Infrastructure Control Checklist Enclave for each function No direct Internet access Infrastructure Firewall Dedicated Enterprise Firewall Customer Authentication Admin Authentication Jump Boxes Network Access Control (NAC) Business-to-Business (B2B) VPN System and Security Event Mgt SANS Technology Institute - Candidate for Master of Science Degree Lessons Learned Pitfalls Promising Solutions •Poor Documentation • Security Fabric •Too many ACLs and Flows • Firewall Policy Mgt •Netflow “meltdown” • Virtual Switch Replacement •4 x10 Port Aggregation • IEEE 802.1AE (MACsec) •Virtual Switch Overload •Poorly designed QoS •Forensic Teams SANS Technology Institute - Candidate for Master of Science Degree Benefits • Improved Security • Increased Design Credibility • Better Manageability • Lower Total Costs • Faster Response to Threats Ultimately, adopting these design recommendations will provide a solid foundation for safeguarding infrastructure and data at the highest speeds available today—and tomorrow. SANS Technology Institute - Candidate for Master of Science Degree
© Copyright 2026