How to Get to Single Sign-On Gregg Kreizman Neil Wynne Twitter: @neilwynne
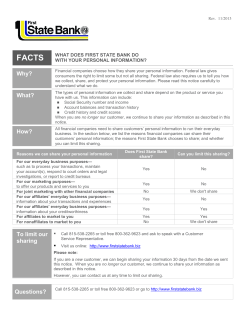
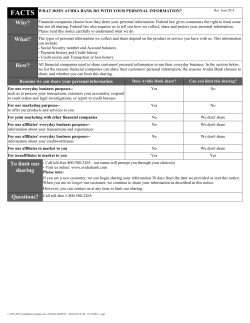
How to Get to Single Sign-On Gregg Kreizman Neil Wynne Twitter: @neilwynne © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. If you are authorized to access this publication, your use of it is subject to the Usage Guidelines for Gartner Services posted on gartner.com. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner's research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner's Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see "Guiding Principles on Independence and Objectivity." SSO Is Often About Treating the Symptoms, Not the Disease vs. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Key Issues 1. What are the forces driving enterprises to require SSO? 2. How should organizations plan for and choose SSO approaches and tools? 3. What are the market solutions, and which vendors and open source solutions can support different SSO needs? © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Key Issues 1. What are the forces driving enterprises to require SSO? 2. How should organizations plan for and choose SSO approaches and tools? 3. What are the market solutions, and which vendors and open source solutions can support different SSO needs? © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. How Did We Get Here? Internal Systems Mainframe Application Servers Portals Lotus Notes ERP SaaS Java Windows "Thick" Client Web Terminal Emulators SAP GUI Mac Users here… Notes Client User Interfaces and Devices © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Users there … users, users, everywhere! The Other Projects Are Hard. IAM Project Type and Complexity Business Strategic Identity & Access Governance Externalized Authorization IAM Project Type Federation Web Access Mgmt. User Authentication Limited Scope ESSO SSO Password Directory Mgmt. Services Identity Analytics User Administration/ Provisioning PAM Tactical IT Simple $ © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. IAM Project Complexity/Cost $$ Complex $$ $ Emerging Trends Trends: - SaaS application needs are reinvigorating the IAM market and are disrupting legacy IAM programs. - Mobile resident apps and BYOD are adding to the disruption. - Social network identity-based authentication is a first step in a trend toward the use of external identities. Implications: - Enterprise IAM managers must implement a cohesive strategy that accounts for enterprise and cloud apps with access from traditional and mobile endpoints. - Social login and registration reduce friction and provide convenience, but will often require stepped up controls. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Key Issues 1. What are the forces driving enterprises to require SSO? 2. How should organizations plan for and choose SSO approaches and tools? 3. What are the market solutions, and which vendors and open source solutions can support different SSO needs? © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Identify Use Cases and Relevant Target Systems Examples: • Employees inside the (logical) enterprise accessing Web-architected applications, or a mix of Web and legacy-architected systems. • Employees accessing SaaS applications. • Consumers accessing your external-facing Web applications. • Partners accessing your external-facing Web applications. • Access from smartphones and tablets; native app clients. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Inventory and Assess Application Architectures and Lifetimes Application name Current and Application other Application client user supported server interface Identity authentication architecture architecture repository methods Finance WebSphere/ Java Thick client DB2 Employee intranet IIS Web browser Active on desktops Directory and mobile devices SaaS Web browser SaaS on desktops vendor's and mobile repository applications User population and use cases Estimated application lifetime One-time password tokens Password X.509 One-time password tokens Employees on-premises and remote Employees and contractors on-premises and remote Replace in 2 years Password Employees Greater than 3 years Greater than 5 years • • • CRM © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Can You Reduce the Problems Without Buying Anything New? • Retire or replace applications soon? • Integrate apps with Active Directory via Kerberos Active Directory • Integrate apps with an LDAP accessible directory (RSO) Kerberos • Synchronize identities and passwords (RSO) © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Virtual Directory Kerberos App App Apps LDAP • Point apps at a virtual directory (RSO/SSO) Sync. Key Issues 1. What are the forces driving enterprises to require SSO? 2. How should organizations plan for and choose SSO approaches and tools? 3. What are the market solutions, and which vendors and open source solutions can support different SSO needs? © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. When Is Active Directory a Part of the Cure? SaaS SharePoint farm ADFS Trust Unix, AD/bridge © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. App with direct AD integration Type of Integration SSO or RSO App integrated directly Kerberos with Windows/Active SSO Directory. AD resource forest Kerberos and 1-way trust for SSO integrated apps. Users in multiple AD forests. Unix, Linux integration Kerberos with AD/bridge. SSO/LDAP App uses LDAP. RSO Apps in the cloud-ADFS. SSO/RSO Internal Web-based Applications, Internal and/or External Users (Software Wanted) External Internal • Best Solution: Web access management (WAM) • Mobile Support: Browser access — good; native apps — variable • Example Vendors: CA Technologies, RSA (EMC), Entrust, Evidian, IBM, NetIQ,, Oracle, Ping Identity, SecureAuth, Open Source — ForgeRock, CAS, OpenIAM © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Web Access Management MarketScoope Strong Caution Promising Positive Negative x CA Technologies Entrust x x Evidian ForgeRock x IBM x Ilex x i-Sprint Innovations x NetIQ x Oracle x Ping Identity RSA, The Security Division of EMC x SecureAuth x As of 13 November 2013 © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. x Strong Positive Web Access Among Partners, Internal IAM Islands, to SaaS/BPO, Product Wanted Service Provider Identity Provider SaaS • Best Solution: Federation • Mobile Support: Browser access — good; native apps — variable • Example Vendors: WAM vendors, Microsoft, Open Source — Shibboleth, OpenIAM, ForgeRock • Options: Virtual directories and networking products extended with federation © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Internal Access to Windows, Web, Java, Mainframe, Notes, SAPGUI, Applications Mainframe Application Servers Portals Lotus Notes ERP Windows "Thick" Client Terminal Emulators SaaS Java Web Mac Employees • Best Solution: ESSO • Mobile Support: Poor SAP GUI Notes Client • Limited to Windows Clients with exception of Web apps for some products • Example Vendors: ActivIdentity, Avencis, CA Technologies, Citrix, Evidian, IBM, Ilex Computing, Imprivata, i-Sprint Innovations, NetIQ, Oracle, Caradigm (Formerly Microsoft/GE Healthcare) © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. ESSO Rarely Needed • Inexorable shift to Web-architected apps • SSO or RSO for legacy apps by integrating with AD, LDAP, or password synchronization • Gartner client demand is for SSO to support use cases for employee-to-SaaS and login to consumer-facing enterprise applications • Few ESSO vendors are making gains • Healthcare is the only bright spot in the market © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Client Demand for ESSO 2008 2010 2012 2014 Web Access, Internal-to-SaaS/BPO, or SaaS/BPO Provider-to-many Customers, Outsourced Solution Wanted Bridge SaaS • Best Solution: IDaaS • Mobile Support: Browser access — good; native apps — variable • Example Vendors: CA Technologies, McAfee (Intel), Okta, OneLogin, Ping Identity, RSA (EMC), Symplified, Symantec … and many others © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Cross Platform — Enterprise Mobile App Access Options Your App VPN Client VPN Your App Web Kit Your App SDK Web Access Manager Your App OAuth OIDC Your App A Your App B Container/Wrapper © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. API Gateway MDM/MAM Access Gateway Application Server Mobile Apps From Third Parties: The West Gets Wilder Application resources SaaS What must the SaaS vendor provide? Your Organization Browser Native app What goes here? What goes here? Administration Access management Authentication methods Your Mobile Users © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Users administered and authenticated here Mobile Apps From Third Parties: The West Gets Wilder — Part 2 Application resources SP initiated federation SaaS Provisioning API Your Organization Browser Native app SDK, Webkit, SSO app Authentication methods Your Mobile Users © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Function: Federation IdP Provisioning connector Administration Access management Users administered and authenticated here "We Want to Accept Social Login for Access to Our Applications" Use Available Authentication Data and Context Use On-hand Data Databases Protected Resources View healthcare data Transfer funds Portal Access Manager Initiate benefits change Minor profile updates Policies Identity Proofing © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Initial registration Marketing Nonsensitive information Action Plan for CISOs and Data Center Managers Monday Morning: - Identify the most used target systems, and those generating the most help desk calls for authentication-related events. - Align these target systems with the common use cases discussed in this presentation, and prioritize these first for simplification. Your Next 90 Days: - Calculate the number and cost of calls related to password management and authentication failures. - Determine whether any targets will be out of scope within one to two years, and would thus reduce the problem space. - Evaluate the need for, and potentially identify solutions — most of which were highlighted in this presentation — to apply to these use cases. - If the outcome is positive, present the business case for moving forward, and establish the project. Your Next 12 Months: - Evaluate, select, and implement solutions; include communication and training. - Identify and highlight post-implementation benefits relative to costs. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved. Recommended Gartner Research How to Get to Single Sign-On Gregg Kreizman (G00247863) Choosing Among Federated Identity Management Options Gregg Kreizman (G00239178) Are You and the IDaaS Market Ready for Each Other? Gregg Kreizman (G00247865) Resolving Mobile Device Challenges to Single Sign-On Gregg Kreizman, Dionisio Zumerle, and John Girard(G00247868) For more information, stop by Gartner Research Zone. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved.
© Copyright 2026