How to the knowledge of legal, security, and privacy experts:
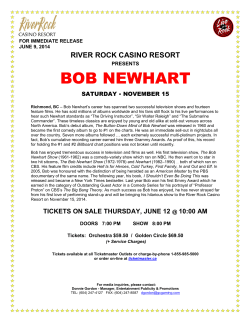
Università degli Studi di Trento How to capture, model, and verify the knowledge of legal, security, and privacy experts: a pattern-based approach L. Compagna, P. El Khoury F. Massacci, N. Zannone R. Thomas Security Research SAP Dept. Informatics and TLC Univ of Trento Dept. of Law Univ. of Leuven www.massacci.org www.tropos-project.org www.serenity-project.org Università degli Studi di Trento Outline • What is the Problem? – Address Regulatory Compliance Demands – Organizational Patterns • Which is the Solution? – Graphical requirements Engineer Methodology • Smart Items For Health Care – An Example of a Pattern • Conclusion & Future Work Università degli Studi di Trento What’s the Problem? • Emerging trends in Security Enginering – Security solutions can longer be best effort – Must show verifiable evidence with …. • Regulatory Compliance – SOX/Basel II/EU Privacy Directive • Industry Compliance – ISO 17799, ITIL Security Management.. • Usage of SOA Mandatory – WS-Security, WS-Trust, WS-Federations • Audit/Certification – CC formal models, verification of the model Università degli Studi di Trento What’s the Solution? • Security & Privacy Patterns for Organisation – Security patterns are security best practices presented in template format – Validated by Experts – Patterns can provide implementations • From rule of procedures to running code • Concept widely used in Software Patterns – Large repositories are available – Model-Based Transformatioon available for different languages Università degli Studi di Trento So what is the problem? Ask a toad what beauty is, the to kalon? He will answer you that it is his toad wife with two great round eyes issuing from her little head, a wide, flat mouth, a yellow belly, a brown back. . . . Interrogate the devil; he will tell you that beauty is a pair of horns, four claws and a tail. Voltaire, Philosophical Dictionary (1764) Università degli Studi di Trento To Design a Security Pattern • Ask a lawyer 17(4)1 For the purposes of keeping proof, the parts of the contract or the legal act relating to data protection and the requirements relating to the measures referred to in paragraph 17(1) shall be in writing or in another equivalent form. • Ask a computer engineer <SignedInfo> <CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/> <SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/> <Transforms> <Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/> </Transforms> <DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/> <DigestValue> FLuQTa/LqDIZ5F2JSaMRHSRuaiQ= </DigestValue> </SignedInfo> • Ask a formal methods expert Fail_NonRepudiation(A,B,S) :- del_exec(A,B,S), not entrust_exec(A,B,S) entrust_exec (A,B,S) :- trust(A,B,S). entrust_exec (A,B,S) :- prove_fulfillment(A, B, S, TP) prove_fulfillment(A, B,S, TP) :- provides(B, PoF), proof_of_fulfillment(PoF, S), entrust_exec(TP, B, PoF), entrust_exec(A, TP, PoF) Università degli Studi di Trento Lingua Franca… • Software Patterns work because they essentially are by toads only – The difference between C++, Java, C#, Eiffel, Perl, Python etc is negligible compared to the ones just made • Security Patterns needs integration of different “languages” • Idea: a picture is worth a thousand words – Provided you are able to get the picture from the words and the words back from the picture Università degli Studi di Trento Bob feels giddy Smart Items For Health Care smart e-health T-shirt terminal ERC MERC Faintness alert (1) Request for medicine delivery (4) Send e-prescription (3) Deliver the medicine (7) Request (2) Steps: 2. Bob feels giddy and sends via his e-health terminal a request for assistance to MERC. 3. MERC receives the request and, since Bob’s doctor is in vacation, redirects it to Charlie. 4. Charlie analyses Bob’s medical data and history and sends to Bob an e-prescription. Request (5) Charlie’s ehealth terminal 5. Bob requests MERC for a medicine delivery. 6. MERC selects Alison to execute this task, sends a message to her to which she promptly acknowledge receiving then back the data for accomplishing this activity. 7. Alison goes to the pharmacy and after a successful credentials exchange, she gets the medicine from the pharmacist. Pharmacist's computer Get medicine (6) Alison e-health terminal 8. Alison delivers the medicine to Bob. Notes: this Charlie Bob as the the credentials request last feels others retrieves step weak would involves Alison exchange and Bob’s have instead isan equipped medical been exchange iswith between ofsent driving data with toofand Bob’s Alison’s an to electronic e-health the history doctor, pharmacy e-health credential by terminal but using terminal he to get his is that between ine-health the she vacation and medicine, uses the Bob terminal pharmacist’s and to and communicate he thus Alison. prefers to e-health aquery doctor Their computer. toERC. be with discovery e-health supported the The Besides others eThis request is completed Bob’s medical data automatically retrieved by his terminal by prescription by health the terminals process the validity ERC actors. of for isused the In sent this the e-prescription, from task. data In this the Charlie’s she purpose. group receives Alison of e-health doctors from authorization terminal ERC able to there’ll to substitute toBob’s get be,the e-health properly Bob’s medicine doctor, terminal. protected, in behalf Charlie the ofe-prescription isBob theneeds first totoanswer. done be checked. for means ofisare aactivated. query toat his smart T-shirt Bob. Università degli Studi di Trento Goal-Based Req. Engineering • Graphical Requirement Language SI* – Agents, Roles, Relations among them – Execution, Delegation of Permissions • Legal text – (semi) automatic extraction of graphical model from Natural Language description • Logical Formulae – Experts provide general axioms and property descriptions – Instances added automatically from graphical model • Executable Business Process – (Semi) automatic BPEL generation from graphical model Università degli Studi di Trento Pattern Design and Validation Semantics Template Lawyer describes patterns NL2SI* transformation Security Engineer Modifies Patterns Graphical SI* Model Graphical CAiSE Tool Formal Logic Automated Reasoning Tool Axioms and Rules Software Engineer Refine Patterns BPEL Editing Tool BPEL Skeleton SI* Interpretation of Logical Result Università degli Studi di Trento Non repudiation requirement presented in SI* The Employer (MERC) shall have evidence that the Executor (Alison) cannot repudiate her commitment. MERC Request Delivery of medicine to Bob Alison e-health terminal Università degli Studi di Trento What is an organizative security pattern? Security Requirements NOT fulfilled Initial organizational structure • Agents • Resources • Tasks • Relations: delegation, trust… Fulfilled Security Pattern Revised organizational structure • Add/Remove Agents • Add/Remove Resources • Add/Remove Tasks • Add/Remove Relations Context Solution SI* MODELS 12 Università degli Studi di Trento Non repudiation pattern [Context and Requirement] Non repudiation pattern [Context, Requirement and Solution] Context: The Employer requests the achievement of a commitment and delegates its execution to the Executor. Requirement: the former has no warranties that the latter takes the responsibility of achieving the commitment Solution: The Employer refines the commitment into two sub parts. 3. Check the evidence about responsibilities taken by the Executor. 4. Represents the actual desire of fulfilling the commitment. Università degli Studi di Trento Conclusion & Future Work • System designers are usually neither security nor legal experts – Graphical RE notation useful common ground • Idea: a picture is worth a thousand words – Provided you are able to get the picture from the words and the words back from the picture • Future Work – Improving model construction from NL – Reasoning capability only detect failed properties, should also suggest what is missing to satusfy them – Apply to other domains • Ack – Supported by the EU through the EU-IST-IP SERENITY
© Copyright 2026