Guidelines on How to Use Web 2.0 Use Case
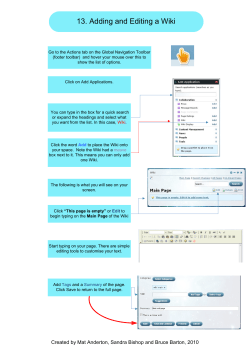
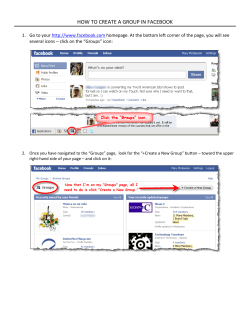
Guidelines on How to Use Web 2.0 – for Public Administration Staff Use Case Civil Service 2.0 Version 1.0.0 Results of the PG Short description Basic principles for access and use of Internet services with special emphasis on social networks Employees working for government offices and organisations are increasingly having to distinguish between private and official use of Web 2.0 applications. Web 2.0 applications are operated interactively on the Internet, handling contents primarily made available by their users. The present documentation was drawn up as a general guideline for users and may serve as a draft structure for individual organisations preparing their own guidelines. It does not include any rules concerning their web presence in Web 2.0 media. Authors: Contributions by: Daniel Medimorec (Federal Project team / Working group Chancellery) Civil Service Web 2.0 Peter Parycek (Danube University Krems) Peter Pfläging (City of Vienna) Andreas Gold (Federal Ministry for European and International Affairs) Thomas Jöchler (City of Vienna) Stephan Lauringer (Federal Chancellery) Robert Lender (Federal Ministry of Economy, Family and Youth) Ralph Osner (Federal Ministry of the Interior) Michael Rederer (City of Vienna) Thomas Skerlan-Schuhböck (City of Vienna) Andreas Unterberger (Federal Ministry of Economy, Family and Youth) Version … : 06-10-2010 rejected by: Deadline: DD.MM.YYYY (indicate name of rejecting province) Subversion … : DD.MM.YYYY Deadline: DD.MM.YYYY (indicate name of rejecting province) Detailed version … : DD.MM.YYYY Released: DD.MM.YYYY (details on release) Civil Service 2.0-1.0.0 1 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff Contents 1 2 3 4 5 Web 2.0 Guidelines for Public Administration Staff ......................................................... 3 1.1 Web-2.0 Services – aspects of use ............................................................................... 5 I. Identification ................................................................................................................... 6 II. Content........................................................................................................................... 6 III. Role/Function ............................................................................................................... 6 IV. Platform ........................................................................................................................ 6 V. Time and Place .............................................................................................................. 7 Web 2.0 Scenarios .............................................................................................................. 7 2.1 Scenario I: “private only“............................................................................................. 8 2.2 Scenario II: “official only“ ........................................................................................... 9 2.3 Scenario III: “private with official content“............................................................... 10 2.4 Scenario IV: “official publication without legitimisation“ ........................................ 11 Useful Hints for Using Web 2.0 ....................................................................................... 12 3.1 Web 2.0 for private use .............................................................................................. 12 3.2 Web 2.0 for official use .............................................................................................. 13 Glossary............................................................................................................................ 15 Diagram as a template for individual use ......................................................................... 18 Civil Service 2.0l-1.0.0 2 / 18 20/08/2012 WG: Civil Service/ Web 2.0 1 Web 2.0 Guidelines for Administration Staff Web 2.0 Guidelines for Public Administration Staff The present Guidelines were prepared to assist public administration staff with official and private use of Web 2.0 applications. They are based on the position paper “basic outlines for access and use of various Internet services (e.g. social networks on the internet)“ which provides a first general description 1. “Web 2.0“ as a keyword comprises a number of different World Wide Web (WWW) services designed to assist users in creating and managing their websites without specific web design or programming knowledge. Communities like Facebook or XING in particular are gaining in popularity. Quite evidently this is not a short-lived trend but a social development of overriding significance. Unlike in the traditional Web where a minority of active authors create sites for the majority of passive readers, in Web 2.0 everyone can become their own author. This opens up a wealth of new opportunities for cooperating, informing, communicating and linking with one another. It is nevertheless important that those who avail themselves of these opportunities are aware of the responsibility entailed. Now more than ever a distinction must be made between the fleeting spoken word and the written one. Much of what used to be treated flippantly in passing and in private is now increasingly spread through digital networks, granting it wider reach and lastingness. Thorough removal of data in Internet services and from the caches of search engine providers is virtually impossible – “The Internet remembers relentlessly“. As with all Internet utilisation it is important to draw a line between official and private utilisation. Official utilisation is subject to specific framework conditions. At the federal level these are specified in the “IKT-Nutzungsverordnung“ (ICT utilisation regulations) in the version of March 17, 2010. Reference is made to the decree “Internet und elektronische Kommunikation“ (Internet and electronic communication) issued by the City of Vienna in the version of February 20, 2009 to exemplify regulations at provincial level. When using the Internet and Web 2.0 services the following aspects should be taken into consideration: • • • Private Internet utilisation in principle is permitted to a “limited extent“ and/or “where absolutely essential“ only, Official secrecy and data protection must be respected, especially when passing on and storing data. Media spokespersons or persons in charge of public relations only are entitled to publish official information. All other administration staff, as in the case of the City of 1 Sources: „Wien spricht anders …auch im Internet“ (Vienna speaks a different language – on the Internet too), MA 53- Press and Information Services for the City of Vienna. Erlass „Internet und elektronische Kommunikation“ (decree “internet and electronic communication) http://dvs.wienkav.at/md/client/dv_detail.asp?ID_DV=2345 (internal link) Federal government regulation on government employees’ private utilisation of government information and communications technology infrastructure (IKT-utilisation regulation – IKT-NV) in the version of March 17, 2010 http://www.ris.bka.gv.at/ Civil Service 2.0l-1.0.0 3 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff Vienna amongst others, may contribute posts in external electronic discussion forums, guest books or similar sites only in the course of their official duties, stating their name and function. Administration staff using their private Internet access to participate in a community must also bear in mind that in their role as public service employees they act on behalf of the Austrian administration: • Once a profile makes reference to an official agency that person’s activities are no longer considered private. • No harm must be done to the official agency’s reputation. Civil Service 2.0l-1.0.0 4 / 18 20/08/2012 WG: Civil Service/ Web 2.0 1.1 Web 2.0 Guidelines for Administration Staff Web-2.0 Services – aspects of use As mentioned in the introduction above activities on social platforms are subject to specific ground rules. Users must take into account the role they are in when accessing the Internet. The following diagram illustrates how public service employees using Web 2.0 platforms I. II. III. IV. V. Identify in different ways, Publish private or official content, Assume different roles and functions, Use different platforms, Log in at different times in different places. The closer to the centre the relevant descriptions in any single category the more employees need to realize their actions are no longer private but official. Civil Service 2.0l-1.0.0 5 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff The following scenarios are intended as guidance only and do not provide a final assessment, as the dimensions and levels do not allow for clear distinctions and also because individual organisations have different legal frameworks and organisational cultures all of which need to be taken into account for final assessment. I. Identification The environment “identification” defines how users want to be recognized by others in Web 2.0. There is a range of different ways to identify: 1. anonymous, i.e. without indication of identification whatsoever, 2. anonymous account, e.g. using a nickname, 3. personalised user, e.g. using a personal account stating one’s own name, 4. official user, linked to an official account and the relevant department. II. Content This defines the content made available by users in Web 2.0. Content may be anything from purely private to fully official: 1. private content without official context, e.g. cooking recipes; 2. private content with official context, e.g. personal opinion on department’s decisions; 3. official content; 4. official content with binding character, e.g. created by an official agency’s bodies. III. Role/Function The third environment defines a user’s role and function in Web 2.0. Again there is a wide range of functions from private to official: 1. private; 2. private in an organisation, e.g. as a member of an association; 3. as a person in official service, maintaining and updating “fan sites“ e.g. on Facebook; 4. in an official function, publishing binding content in that role. IV. Platform “Platform“ refers to the channel of access users choose for Web 2.0 services. It is important to understand that published content may also be used as content by other platforms. Multiple use of content is one of the Web’s distinguishing features, a fact which makes it difficult to distinguish clearly between individual platforms. Content created by a person may be spread on other Internet sites without that person knowing. This is true in particular for social networks like Facebook or Xing where content may be passed on by “friends” despite Civil Service 2.0l-1.0.0 6 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff restricted privacy settings. Status messages related to employers or superiors are frequently cited as examples. Platforms are accessed through: 1. private sites (private blogs, forums, blog commentaries …), 2. networks (e.g. Facebook, Twitter …), 3. business networks (e.g. LinkedIn, XING …), 4. official sites (e.g. Intranets, BKA-Wiki, “reference servers“ www.ref.gv.at, etc.) V. Time and Place This environment identifies where and when Web 2.0 services are used, distinguishing between private and official IT equipment employed for the purpose. To better understand Web 2.0 it is important to note that “time and place” in principle are irrelevant. The Internet allows access any time any place. Public administration staff roughly speaking may choose among the following constellations: 1. at home using private equipment, 2. at home using official equipment, 3. at place of employment in off duty time, 4. at place of employment in the service. Some Internet sites save their users’ IP addresses which enables them to associate a person with the department they are employed at. Members of staff using official equipment should therefore be careful which websites they access, especially with regard to websites prohibited under criminal law or websites otherwise unlawful due to their pornographic or racist content. Sites obligating the employer to make payments or likely to contain malware are also potentially risky. The above environments occur in various patterns depending on the level of administration. The scenarios listed below may be assessed in different ways by individual organisations. Their aim is not to provide a final assessment but to show up the risks members of staff are potentially exposed to. 2 Web 2.0 Scenarios The environments described provide a basis for illustrating potential scenarios. Their purpose is to show members of staff what they need to look out for when accessing Web 2.0 services by raising their awareness and understanding of the subject matter. Civil Service 2.0l-1.0.0 7 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff The lightening symbol in the diagrams was used to point out the critical levels in scenarios III. and IV. 2.1 Scenario I: “private only“ Here is an example of entirely unproblematic private use: a person acting in private from their home, using private equipment and a personal account to access a network, such as eBay, and state their own opinion. Civil Service 2.0l-1.0.0 8 / 18 20/08/2012 WG: Civil Service/ Web 2.0 2.2 Web 2.0 Guidelines for Administration Staff Scenario II: “official only“ The following pattern illustrates unproblematic official use: a person acts in an official function, at their place of employment in the service, using official equipment to access an authority site, such as BKA-Wiki, for the purpose of working on a document with official content. Civil Service 2.0l-1.0.0 9 / 18 20/08/2012 WG: Civil Service/ Web 2.0 2.3 Web 2.0 Guidelines for Administration Staff Scenario III: “private with official content“ The following scenario, because it involves social networks like Facebook or Xing, is a mix of private and official spheres. A member of IT staff in her private time, albeit in the office, with her personal user account accesses a social network where she is linked with or friends with systems house XY members of staff. The content is private (e.g. personal opinion of software products) yet has official connotations (e.g. whether or not these products are also used in the workplace). Several months previously the user had added systems house XY to her profile by clicking the “like it“ function available on Facebook . The scenario thus created, in particular the “like it“ function, may turn into a problem in connection with a public tender which the relevant authority has launched and which systems house XY has also joined as a bidder. Should systems house XY be awarded the contract competitors might suspect a close relationship between the member of IT staff and systems house XY. Members of staff using Web 2.0 services must bear in mind that contents made available are difficult to remove if at all. The new networks, unlike traditional business contacts, highlight such contents and any relevant communication. No precedents have been set so far. Civil Service 2.0l-1.0.0 10 / 18 20/08/2012 WG: Civil Service/ Web 2.0 2.4 Web 2.0 Guidelines for Administration Staff Scenario IV: “official publication without legitimisation“ The scenario described below should be avoided at all costs: in this case a member of staff is using their official account in the service and in their place of employment to publish officially binding contents in a business network without having been authorized to do so. This is unacceptable by the general legal framework, including distribution of tasks, licences, or the regulations and decrees pertaining to ICT. Problem areas existing independently of communication media are only aggravated by ICT. Clearly in this case a diagram alone would not provide sufficient assessment. Civil Service 2.0l-1.0.0 11 / 18 20/08/2012 WG: Civil Service/ Web 2.0 3 Web 2.0 Guidelines for Administration Staff Useful Hints for Using Web 2.0 As the previous chapter aptly describes activities in Web 2.0, in social media and in social networks (Internet forums, mailing lists, Blogs, Vlogs, Podcasting, Wikis, Social Communities, etc.) feature as “private” or “official” or somewhere in between, depending on role, function, content, context, time, place and the equipment used. There are many different ways of making content, such as texts, photographs, audio and video files available in the web. The use of social networks like Facebook or Xing has virtually exploded in the past two years. These changes in the use of Internet services are challenging administrations and administration staff concerned with issues of use and with the difficulties of distinguishing between private and official activities. The following hints are to provide a basis for private and official use of social media and networks. 3.1 Web 2.0 for private use Social media and networks permit companies, colleagues, customers and citizens in general to exchange information on a wide scale. As a rule it is important that you draw a line between Internet activities you perform as a private person and those of an official nature. Below is a list of useful hints to bear in mind when you use social media as a private person: 1. Make a note of who has access to your social media and networks (Internet forums, mailing lists, Weblogs, Podcasting, Vlogs, Wikis, Social Communities, etc.) and bear in mind that electronic content is easily passed on to other platforms. Choose the information you want to disclose and the language you avail yourself of accordingly. Be mindful of your own reputation. 2. Design your postings as you see fit for the content. Make it clear, where necessary, that you are posting your own personal views and thoughts only and that you are not writing on behalf of your authority. This is particularly important when using business networks (XING, LinkedIn, etc.). 3. Never use private blogs, Wikis, virtual worlds, social networks and others to discuss content related to your authority or to communicate with work colleagues. Resort to means of communication created for that purpose inside your authority. 4. Do not post differences of opinion with your work colleagues in public media. 5. Respect the privacy of others. Ask for permission if you want to publish other people’s photographs or conversations. Never publish confidential information. 6. Respect copyrights, etc. When making a reference create a link to the source if you can or use content explicitly permitted for use. Civil Service 2.0l-1.0.0 12 / 18 20/08/2012 WG: Civil Service/ Web 2.0 3.2 Web 2.0 Guidelines for Administration Staff Web 2.0 for official use Listed below are a number of useful hints for using social media and networks in official environments, including, amongst others, the guidelines “Wien spricht anders …auch im Internet“ 2 prepared by the City of Vienna. In any event attention must be paid to the relevant authority’s terms of use and to the federal and provincial decrees regulating private and official Internet use as well as the use of IT infrastructure. As a public service employee you are vested with valuable professional competences you draw on in the context of social media and networks to comprehensibly convey pertinent information to the public. Social media and networks also allow you to exchange information with colleagues and establish useful contacts. Before you venture forth into this communication realm we recommend you pay heed to the following: 1. Participate in Internet activities only which your employer has granted permission for. Make sure you only publish information within your sphere of competence or which you are authorized to publish. 2. Remember to maintain official secrecy before creating or publishing information. 3. Use your brain and not your guts when creating your profile. 4. Never make your official profile too personal. Respect your own privacy and that of others (who may be in your photographs, etc.). Do not disclose personal details about yourself or your colleagues beyond what is absolutely necessary. 5. Using social media and networks is public relations work to some extent, which means that you as a member of staff act as a “press office” for communicating your department’s information. 6. Make sure you have understood the rules users must comply with for some Web 2.0 applications before getting started. 7. “Less is more“ – always consider your information’s usefulness before making it public. 8. When posting comments always state your professional position and the department you represent. 9. Make sure that any comments you make on behalf of your authority concerning that authority’s activities are appropriate, politically correct and in keeping with your role and function in that authority. 10. Bear in mind that postings on the Internet are permanently available and may be copied by other media. Respect your privacy in your blogs etc.: once published they will remain in the web for a long time. Be clear about how much personal detail you want to disclose. 2 Sources: „Wien spricht anders …auch im Internet“ (Vienna communicates clearly and efficiently – on the Internet too), MA 53 – Press and Information Services for the City of Vienna. These include recommendations on optimising online communication. Civil Service 2.0l-1.0.0 13 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff 11. In consultation with the relevant authorities correct any inaccuracies or incorrect information, hard facts such as spelling mistakes or closed-down departments, which you come across in your work in Web 2.0. 12. Try to answer any questions users may have concerning your authority’s work or published information within your sphere of competence. 13. When handling questions or discussions and where possible and practical make a reference to your authority’s/authorities’ official information site/s. 14. Respect copyrights, etc. When making a reference create a link to the source if you can or use content explicitly permitted for use. 15. Consider licensing the material you have processed through Creative Commons (CC) 3 to simplify further use and exchange. 4 16. Try to use content explicitly permitted for use, e.g. look out for CC licensed photographs on Flickr 5; there is no guarantee, however, that the provider is also the author. 17. Keep an eye on future developments, their technical aspects as well as their social consequences. Maintain a healthy dose of scepticism – you don’t have to use each and every technical innovation. 3 http://www.creativecommons.at/ (29.09.2010). Source: “Social Media Guidance for Agencies and Staff – Guidance for staff using social media official use” from the Commissioner for Public Sector Employment - Office for Ethical Standards and Professional Integrity. Government of South Australia, Department of the Premier and Cabinet: http://www.espi.sa.gov.au/socialmedia-guidelines.php?id=8 (29.09.2010). 5 http://www.flickr.com/ (30.09.2010). 4 Civil Service 2.0l-1.0.0 14 / 18 20/08/2012 WG: Civil Service/ Web 2.0 4 Web 2.0 Guidelines for Administration Staff Glossary Account (also user account) : “A user account grants authorization to access restricted IT systems. To log in, a user is typically required to authenticate themselves with a user name and password. Depending on the task user accounts may have various privileges, such as access rights, attached to them“. Source: http://en.wikipedia.org/wiki/User_account (10.02.2010) Blog : (short for: Weblogs) These predecessors of “Web 2.0“ as a rule do not arrange texts by hierarchy but consist of individual articles listed in reverse chronological order, the most recent post always appearing first. As a further asset blogs allow for numerous ways of connecting, either among individual blogs or with other websites. Many blogs function as “diaries“; others provide commentary on a particular subject (hobbies, politics, technology, philosophy, events, etc.). Source: BLSG “Position Paper on E-Democracy and E-Participation in Austria“; http://reference.e-government.gv.at/uploads/media/EDEM-1-0-0-20080525.pdf (10.02.2010). Cache: in computer engineering refers to a method for reducing the average time to access data that has been previously requested. Caches are buffer memories designed to store (or cache) duplicates temporarily. (…) Their purpose is to reduce access time and the number of visits to the memory to be cached. Source: http://de.wikipedia.org/wiki/Cache (04.10.2010) Collaboration tools: a collaboration tool is something that helps users collaborate and cooperate. The term is often used to mean “Collaborative Software“. Everything that helps to solve a predefined task more easily in a group is an effective collaboration tool. Wiki is among the most widely known. Source: http://en.wikipedia.org/wiki/Collaboration_tool (19.03.2010). Creative Com m ons is a movement of creators the world over. All creative works being automatically protected it wants to motivate as many creators as possible to share their works with others. Existing content is to be used more easily while providing a basis for new content. The Creative Commons licensing system wants to assist authors and bloggers, musicians and composers, filmmakers and camera people, photographers, designers and graphic designers, teachers and students in managing rights of use intelligently and without red tape. Source: http://www.creativecommons.at/ (29.09.2010). Term inal equipm ent: Terminal equipment in information technology (IT) and telecommunications (TC) refers to equipment (e.g. PC, telephone or answering machine) connected to the network termination of a public or private data or telecommunications network. The connection may be a direct electrical/optical one, as with a plug-in connector, or a radio connection, as with mobile telephones. Source: http://de.wikipedia.org/wiki/Endger%C3%A4t (10.02.2010). Good Practices: positive case studies; also known as “best method “ or “best practice“. Source: http://de.wikipedia.org/wiki/Good_Practice (10.02.2010). Civil Service 2.0l-1.0.0 15 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff IP address: is a label used in computer networks which, like the Internet, are based on an Internet protocol. Labels are assigned to devices participating in the net, making them addressable and accessible. IP addresses may refer to a single receiver or a larger receiver population (Multicast, Broadcast). On the other hand, one computer may have several IP addresses assigned to it. IP addresses are used to transport data packages from a sender to a specified receiver. Similar to postal addresses on envelopes IP addresses on data packages clearly identify the receiver. Yet unlike postal addresses IP addresses are not tied to a particular location. Source: http://de.wikipedia.org/wiki/IP-Adresse (10.02.2010). Short m essages: there are different ways of sending short messages: Short Message Service (SMS) is a method used on mobile telephones. Source: http://de.wikipedia.org/wiki/Kurzmitteilung (10.02.2010). M edia hype: Media hype refers to mostly short-lived news dramatised or exaggerated by the media and used for the purpose of advertising specific ideas and products. Source: http://de.wikipedia.org/wiki/Medienhype (10.02.2010). M edia platform s: Flickr, YouTube, Vimeo, … M icroblog: Microblogs allow users to exchange small elements of content similar to SMS texts. The messages tend to be no more than 200 characters. Postings are either private or publicly accessible and as with traditional blogging are listed in chronological order. To create or subscribe to messages different channels may be used including SMS, e-mail, instant messaging or the Web. Microvideoblogging is a more sophisticated form of microblogging allowing users to record short videos (without sound) and post these on the website. Status messages on the video application may be further expanded and published on Facebook, Twitter and Co. Twitter is the most widely known microblogging service to date. Source: http://de.wikipedia.org/wiki/Microblog (10.02.2010). Nicknam e: The terms user name and nickname (also nick) these days are understood to refer to the name you are identified with on the Internet. As a rule it is short and intended for long-term use. Source: http://de.wikipedia.org/wiki/Nickname (10.02.2010). Online services: Customers of commercial and non-profit online services are given the option of dialling a computer network (either the services’ own network or an open one) to access content in that network. Source: http://de.wikipedia.org/wiki/Onlinedienst (10.02.2010). Sm artphone: A smartphone is a mobile telephone equipped with a high-capacity processor. Most smartphones are slim and their handling is similar to that of regular mobile phones. Smartphones may be upgraded with additional programmes (so-called Apps) and functions to suit the individual user’s purposes. Popular examples include Android smartphones by HTC, the Apple iPhone or Samsung smartphones. Source: http://de.wikipedia.org/wiki/Smartphone (04.10.2010). Social netw orks: Social networks in informatics are online communities or web applications hosting such communities. Networks including user-generated content are also referred to as social media. Colloquially the term social networks is used to describe online communities Civil Service 2.0l-1.0.0 16 / 18 20/08/2012 WG: Civil Service/ Web 2.0 Web 2.0 Guidelines for Administration Staff hosted by Web-2.0 applications or portals. Facebook is a popular example of a social network. Source: http://de.wikipedia.org/wiki/Soziales_Netzwerk_(Internet) (10.02.2010). W eb search engine: A web search engine is designed to search for documents stored on a server or computer network such as the World Wide Web. When a user enters a query the search engine provides a listing of references to potentially relevant documents, usually with a short summary containing the document’s title and parts of the text. Different search methods may be applied in the process. Source: http://de.wikipedia.org/wiki/Suchmaschinen (10.02.2010). Tw itter: is an online social networking service and publically accessible diary (microblog) administrated and updated worldwide via website, mobile telephone, desktop applications, widget or web browser plug-in. it enables registered users to send and read text-based posts of up to 140 characters. The author of a post is pictured on the service’s website with an Avatar and is fully accountable for its content (…) Twitter is thus a useful tool for exchanging information, thoughts and experiences, as well as for communicating with others. Writing on Twitter is referred to as “twittering”. Posts on Twitter are known as “tweets“ or “updates“. Reposting a message from another user, e.g. to pass on urgent information more quickly, requires the “retweet“ function. The social network revolves around the principle of following other users’ messages. Authors are called “twitterers“, or, less frequently, “tweeps“, readers following an author’s messages are “followers“. The tweets followed appear on the follower’s main Twitter page in reverse chronological order. Senders can restrict message delivery to just their group of friends or make them publicly visible. Source: http://de.wikipedia.org/wiki/Twitter (10.02.2010). W eb 2.0: is a generic term used to describe a series of new interactive web techniques and services, the WWW in particular, based on a new understanding of the Internet. What is new essentially is the fact that users are increasingly allowed to interact and collaborate as creators of content, to (freely) recombine existing content and to avail themselves of “social software“ – systems supporting the structuring and maintenance of social networks largely through self-organisation. Source: BLSG “Position paper on e-democracy and e-participation in Austria“; http://reference.e-government.gv.at/uploads/media/EDEM-1-0-0-20080525.pdf (10.02.2010). Civil Service 2.0l-1.0.0 17 / 18 20/08/2012 WG: Civil Service/ Web 2.0 5 Web 2.0 Guidelines for Administration Staff Diagram as a template for individual use Civil Service 2.0l-1.0.0 18 / 18 20/08/2012
© Copyright 2026