UNIVERSITY OF WATERLOO Cheriton School of Computer Science CS 458/658
UNIVERSITY OF WATERLOO
Cheriton School of Computer Science
CS 458/658
Computer Security and Privacy
Douglas Stinson and Tariq Elahi
ASSIGNMENT 2
Assignment due date: Friday, October 31, 2014, 3:00 pm
Written Response Questions TA: Nabiha Asghar
Programming Questions TA: Frank Song
Total marks: 68
Written Response Question [28 marks]
Note: For written questions, please be sure to use complete, grammatically-correct sentences. You
will be marked on the presentation and clarity of your answers as well as the content.
1. [Total: 6 marks]
Identification/Authentication Protocols
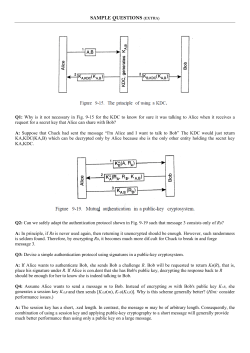
(a) [4 marks] In class you were taught that challenge-response protocols can be used for
authentication purposes. Consider a scenario involving two friends, Alice and Bob,
who often communicate with each other on an online chatting software. Each of them
possesses a ‘key’ K, a secret mutual password (known only to Alice and Bob), which
they shared with each other offline. In addition, they have access to a publicly known
function f , whoses inverse function f −1 is extremely hard to compute. Bob initiates
the following interactive protocol for two-way authentication with Alice at the start of
each chat session:
i. Bob sends a random string r1 to Alice.
ii. Alice chooses a random string r2 , computes x = f (“Alice”, K, r1 ) and sends r2
and x to Bob.
iii. Bob computes y = f (“Alice”, K, r1 ). If x 6= y, he aborts the chat session,
claiming that the person on the other end is not Alice. If x = y, Bob computes
z = f (“Bob”, K, r2 ) and sends z to Alice.
iv. Alice computes z ∗ = f (“Bob”, K, r2 ). If If z ∗ 6= z, she aborts the chat session,
claiming that the person on the other end is not Bob. If z ∗ = z, she continues the
chat session with Bob.
Note: “Alice” and “Bob” are strings that are padded to a fixed length.
We will make the following assumptions:
1
• Eve knows the protocol procedure but not the value of K,
• Eve can read all the messages exchanged between Alice and Bob (i.e. she can see
r1 , r2 , x and z),
• Eve can compute f but not its inverse f −1 , and
• Eve can initiate as many chat sessions as she wants, with any user.
• Eve can intercept and modify messages sent between Alice and Bob (i.e., she can
carry out man-in-the-middle attacks).
It turns out that this authentication protocol is insecure and susceptible to a man-in-themiddle attack. Explain how Eve, an adversary, can fool Alice and successfully pose as
Bob. That is, describe how Eve can impersonate Bob in a chat with Alice in such a way
that Alice thinks she is communicating with Bob.
(b) [2 marks] Alice and Bob eventually, realize that their protocol is insecure, so they
decide to modify as follows:
i. Bob sends a random string r1 to Alice.
ii. Alice chooses a random string r2 , computes x = f (“Alice”, K, r1 , r2 ) and sends
r2 and x to Bob.
iii. Bob computes y = f (“Alice”, K, r1 , r2 ). If x 6= y, he aborts the chat session,
claiming that the person on the other end is not Alice. If x = y, Bob computes
z = f (“Bob”, K, r2 ) and sends z to Alice.
iv. Alice computes z ∗ = f (“Bob”, K, r2 ). If If z ∗ 6= z, she aborts the chat session,
claiming that the person on the other end is not Bob. If z ∗ = z, she continues the
chat session with Bob.
Explain how this modified protocol is secure against the man-in-the-middle attack you
described in (a). Assume that Eve knows the new protocol, and has the same capabilities as before.
2. [Total: 6 marks] Intrusion Detection
An e-trading company called TradeWhiz notices anomalous traffic patterns on its servers and
decides to use an Intrusion Detection System (IDS) which labels a legitimate connection as
an attack (false positive) with probability 0.04, and labels an attack as a legitimate connection
(false negative) with probability 0.07.
(a) [3 marks] Given that 2% of all connection attempts are attacks, what is the probability
that when the IDS labels something as an attack, it is actually an attack?
(b) [3 marks] Given that 94% of all connection attempts are legitimate, what is the probability that when the IDS labels something as a legitimate connection, it is actually a
legitimate connection?
Note: You should use Bayes’ Rule for conditional probabilities to solve this question:
http://en.wikipedia.org/wiki/Bayes’_theorem
2
3. [Total: 16 marks]
Lattices
(a) [4 marks] Give the lattice representation of the positive factors of 120 (i.e., draw a
diagram). State how the G.L.B. and L.U.B. of two elements x and y are defined in this
lattice.
(b) [4 marks] A set S partially ordered by a binary relation is a lattice if, for all elements
x, y ∈ S, a unique greater lower bound (G.L.B) of x and y exists, and a unique least
upper bound (L.U.B) of x and y exists. Is the set {1, 2, 3, 4, 5, 6, 10, 12, 15, 18, 20, 30},
when it is partially ordered by divisibility, a lattice? Prove or disprove. (Note: to
disprove that something is a lattice, it suffices to present a counterexample, i.e., values
x and y in the lattice for which the G.L.B. or L.U.B. does not exist.)
(c) [2 marks] A set S partially ordered by a binary relation is a meet-semilattice if, for all
elements x, y ∈ S, a unique G.L.B of x and y exists. Is the set {1, 2, 3, 4, 12, 16}, when
it is partially ordered by divisibility, a meet-semilattice? Prove or disprove.
(d) [2 marks] A set S partially ordered by a binary relation is a join-semilattice if, for all
elements x, y ∈ S, a unique L.U.B of x and y exists. Is the set {1, 2, 3, 12, 18, 36},
when it is partially ordered by divisibility, a join-semilattice? Prove or disprove.
(e) [4 marks] Let S be a finite set. The power set of S, denoted P(S), consists of all the
subsets of S. Given X, Y ∈ P(S), suppose we define X ≥ Y iff X ⊇ Y . Give a
complete proof that this defines a lattice.
Programming Question [40 marks]
Background
You are a hacker specializing in network-related attacks. You are monitoring the network traffic
of one potential victim. The victim is not very careful and all her network traffic is in plain text,
which make your attacks much easier. You want to write some tools to analyze this traffic to gain
information about this victim. You also want to be able to modify the client’s taffic (packets) to
hide your tracks. For this assignment, you only consider HTTP traffic and IPv4.
Tool Descriptions
You have access to a great network sniffing tool called tcpdump which can take inputted network
traffic and output it in several formats. tcpdump is a program on Unix-like operating systems. It
can parse network packets and output human-readable representations. The exact commands used
to generate packet information are
3
tcpdump -X -n -l
tcpdump -A -n -l
These commands print verbose information about packets, along with their contents, and does not
convert IP addresses and ports into names. The first command’s output is in both hex and ascii
formats and it only contains contents of IP packets (i.e not including the link layer header). The
second command’s output is in ascii format and also only contains contents of IP packets.
Testing environment
For each tool, a sample input and output file has been providedi which you can download from the
course page. To test your tools, you can write the contents of the sample file to the standard input
of your program using the following command (be sure to replace sample-file with the actual name
of the sample file):
tool < sample-file
Each of the sample files comes along with the expected output for your script. To ensure that your
output is the expected one for the problem, you can compare the attacks that your program detected
against the expected attacks using diff:
tool < sample-file | diff - expected-output-file
If your tools are working properly, the output from this command should be empty. However,
you should ensure that you are using the requested methodology (e.g., hard-coding output for
the sample files is not a valid solution). Upon submission, your program will be tested using
additional input files.
[10 marks] Tool 1 : Steal Cookie
As we know, a cookie is a small piece of data sent from a website to the client and stored in the
client side when the user is browsing that website. Every time the user accesses that website again,
the browser will send the cookie back to the server so that the server can get some information
about the users previous activity. For example, the server will recognize if one user has logged in
or not with a cookie. If the information contained in a cookie is learned by a hacker (you), she may
gain access to the users data or access to the users account on the website. As a hacker, you want
to extract cookies from clients network traffic. The network traffic is obtained from tcpdump (with
-A option) and saved to one file. You need to write a program which can parse this output and then
4
output the cookies that may be present in the traffic (one packet may contain at most one cookie).
In summary, your program should work like this
cookieExtract < sample-file
and output every cookie one by one (see sample output for exact format).
[10 marks] Tool 2 : Compare Cookie
After step 1, you should be able to extract cookies from the network traffic. From cookies of two
HTTP requests, we can guess if these two requests are from the same user by checking if the two
cookies have a common key-value pair (see note below). You need to write a tool which can read
a file which contains two cookies and tells you if the two cookies have the same key-value pair. If
they do, your tool will output “Found” and output “Not found” otherwise. Your program should
work like this:
sameUser < sample-file
(Note: If we find a common key-value pair, we only know it is possible for these two packets belong
to the same user. However, we are not sure. For example, if one website uses ”isLogged=true” in
the cookie, even two different users’ cookies for this website can have a common key-value pair.)
[10 marks] Tool 3 : Extract URLs Accessed by Cookies
After step 2, you should be able to check if two cookies have a common key-value pair. Now, you
are able collect a lot of information about one specific user! You need to write a tool that takes two
inputs. The first is a file containing a number of cookies of a user. The second is a file containing
captured network traffic. The tool should extract the URLs from packets that belong to the user
whose cookies we have provided. Your program should work like this:
accessedURLs sample-cookies < sample-file
[10 marks] Tool 4 : Hide Modifications on Traffic
The Transmission Control Protocol(TCP) is designed to provide reliable data transfer between a
pair of devices on an IP internetwork. It uses packet checksums to detect transmission errors. You
are now ready to attack the client with the information you have learned from their cookies. To
5
do this you need to be able to modify the client’s traffic. In order to do this without tipping off
the client and the network administrator, you need to re-calculate the packet’s checksum since you
have manipulated it. Write a tool that verifies packet(s) checksums are correct. Your tool should
be able to take a number of packets from a file and tell you if each is correct or not. Your program
should work like this:
checkCheckSum < sample-file
For every packet, print out “Correct” if the checksum is correct, or “Wrong” otherwise. You may
find this link useful :
• TCP wikipedia page
Notice that the packet obtained from tcpdump is an IP packet.
Testing on the Ugster Machines
Once you are confident that your tools are working correctly for the sample files, you can optionally
use the ugster machines to perform several real-world tests. Using the same account credentials
that you used for assignment 1, log into your designated ugster machine. Once you have logged
into your ugster account, run uml to launch the virtual Linux environment for assignment 2. Recall
that you should log in as user to interact with the machine, and halt when you want to halt the
virtual environment.
For testing, you can launch your program using
tcpdump -A -n -l ’tcp dst port 80’ | cookieExtract
for tool 1,
tcpdump -A -n -l ’tcp dst port 80’ | accessedURLs cookies
for tool 3 and
tcpdump -X -n -l ’tcp dst port 80’ | checkCheckSum
for tool 4. For testing tool 2, you need to generate a file which contains two HTTP requests just
like the provided sample input file.
6
Evaluation
• For marking, we will compile and execute your tools in the /share directory in a virtual
machine.
• Your tools will be executed inside a virtual machine with standard input in same format with
tcpdump and sample input. You can assume that your program will be executed from the
current working directory.
• All relevant packets will follow the formats observed in the sample input files. If your
program encounters a packet with an unknown format, it should be gracefully ignored.
Programming Languages
We have installed several of the most popular programming languages within the virtual machine.
You may choose any language supported by the virtual machine to use for your tools implementation. The following list enumerates the supported languages and, for interpreted languages, the
shebang (the line starting with #!) that you should include as the first line of your source file:
C: gcc version 4.4.5
C++: g++ version 4.4.5
JavaScript (node.js 0.6.8): use #!/usr/bin/node
Perl 5.10.1: use #!/usr/bin/perl
PHP 5.3.3: use #!/usr/bin/php
PLT Scheme 4.2.1: use #!/usr/bin/mzscheme
Python 2.6.6: use #!/usr/bin/python
Ruby 1.8.7: use #!/usr/bin/ruby
What to hand in
All assignment submission takes place on the linux.student.cs machines (not ugster or
the virtual environments), using the submit facility. In particular, log in to the Linux student
environment (linux.student.cs.uwaterloo.ca), go to the directory that contains your
7
solution, and submit using the following command: submit cs458 2 . (dot included). CS
658 students should also use this command and ignore the warning message.
By the a2 deadline, you are required to hand in:
a2.pdf: A PDF file containing your answers for the written-response questions.
src.tar: Your source files for your tools, in your supported language of choice, inside a tarball. To
create the tarball, cd to the directory containing your code, and run the command
tar cvf src.tar .
(including the .). You should make sure that you have four executable files(cookieExtract,
sameUser, accessedURLs, checkCheckSum) in this tarball. If you use compiled
languages, you should also include source code and a makefile whose default target is
building these four tools.
a2.pdf must contain, at the top of the first page, your name, UW userid, and student number. -3
marks if it doesn’t! Be sure to “embed all fonts” into your PDF files. Some students’ files were
unreadable in the past; if we can’t read it, we can’t mark it. We also strongly encourage you to test
your tools in a clean /share directory.
The 24 hour late policy, as described in the course syllabus, applies to the assignment due date. If
you submit after deadline but within the 24 hours, you will get a 25% penalty. Remember to
add the “-t” option if you are late or you will fail to submit.
The Ugster Course Computing Environment
To access this system, you will need to use ssh to log into your account on one of the ugster
environment: ugsterXX.student.cs.uwaterloo.ca. There are a number of ugster machines, and each student will have an account for one of these machines. You should use the same
ugster machine that you used for assignment 1. When logged into your ugster account, you can
run “uml” to start the user-mode linux to boot up a virtual machine.
Any changes that you make in the uml environment are lost when you exit (or upon a crash of
user-mode linux). Lost Forever. Anything you want to keep must be put in /share in the virtual
machine. This directory maps to ∼/uml/share on the ugster machines, which is how you can copy
files in and out of the virtual machine. It is wisest to ssh twice into ugster. In one shell, start
user-mode linux, and compile and test your tools. In the other account, log into ugster and edit
your files directly in ∼/uml/share/, so as to ensure you do not lose any work. The ugster machines
are not backed up. You should copy all your work over to your student.cs account regularly.
8
When you want to exit the virtual machine, use exit. Then at the login prompt, login as user “halt”
and no password to halt the machine.
Any questions about your ugster environment should be directed towards the Programming Question TA.
9
© Copyright 2026